Professional Documents
Culture Documents
A Study On Detecton and Prevention of SQL Injection
Uploaded by
a kOriginal Title
Copyright
Available Formats
Share this document
Did you find this document useful?
Is this content inappropriate?
Report this DocumentCopyright:
Available Formats
A Study On Detecton and Prevention of SQL Injection
Uploaded by
a kCopyright:
Available Formats
A STUDY ON DETECTON AND PREVENTION
OF SQL INJECTION
05/28/21 SINHGAD COLLEGE OF ENGINEERING, DEPARTMENT OF COMP. ENGINEERING, STCL 2015-16. 1
Introduction
• Structured Query Language (SQL) is a text language that allows
manipulating the data stored in the database through the commands
such as INSERT, UPDATE and DELETE etc.
• Code injection technique in which hacker manipulates the logic of
SQL command to obtain access on the database and other sensitive
information.
05/28/21 SINHGAD COLLEGE OF ENGINEERING, DEPARTMENT OF COMP. ENGINEERING, STCL 2015-16.
2
Problem Statement
• SQL injection attack belongs to one of the means of study of
database security attack.
• SQL injection attacks allow attackers to spoof identitiy,change
existing data,cause repudiation issues such as destroy data or make
it otherwise unavailable and become administrators of the database
server.
05/28/21 SINHGAD COLLEGE OF ENGINEERING, DEPARTMENT OF COMP. ENGINEERING, STCL 2015-16.
2
Motivation
• Determining Database Schema
• Extracting Data
• Identifying SQL Injection vulnerability
05/28/21 SINHGAD COLLEGE OF ENGINEERING, DEPARTMENT OF COMP. ENGINEERING, STCL 2015-16.
2
SQL INJECTION
The ability to inject SQL commands into the database engine through
an existing application.
Types of SQL Injection attack
• Tautologies
• Illegal/Logically Incorrect Queries
05/28/21 SINHGAD COLLEGE OF ENGINEERING, DEPARTMENT OF COMP. ENGINEERING, STCL 2015-16. 5
Tautologies
• Inject code in one or more conditional statement so that they
always evalute to true
• Example
SELECT name FROM user_details WHERE username = ‘abc’ and
password = or1 = 1.
05/28/21 SINHGAD COLLEGE OF ENGINEERING, DEPARTMENT OF COMP. ENGINEERING, STCL 2015-16. 6
Illegal/Logically Incorrect Queries
• Inject statement that cause a syntax,type conversion,or logical error
into database.
•Example
SELECT accounts FROM users WHERE login = “AND pass=”
A ND pin=convert(int,(select name from sysobjects where
xtype = ‘u’))
05/28/21 SINHGAD COLLEGE OF ENGINEERING, DEPARTMENT OF COMP. ENGINEERING, STCL 2015-16. 7
Prevention Of SQLIAs
• The root cause of SQL injection vulnerabilities is insufficient input
validation
• Solution:
-Defensive coding practices
-Detection & Prevention techniques
05/28/21 SINHGAD COLLEGE OF ENGINEERING, DEPARTMENT OF COMP. ENGINEERING, STCL 2015-16. 8
Defensive coding practices
• Input type checking
• Encoding of inputs
• Positive pattern matching
• Identification of all input sources
05/28/21 SINHGAD COLLEGE OF ENGINEERING, DEPARTMENT OF COMP. ENGINEERING, STCL 2015-16. 9
Detection & Prevention Techniques
AMNESIA
• Analysis and Monitoring for Neutralizing SQL Injection Attack
• Uses a combination of static analysis and runtime monitoring.
05/28/21 SINHGAD COLLEGE OF ENGINEERING, DEPARTMENT OF COMP. ENGINEERING, STCL 2015-16. 10
SQLRand
• Extends the application of Instruction-set Randomization to the
SQL:appending a random integers to SQL standard keyword.
05/28/21 SINHGAD COLLEGE OF ENGINEERING, DEPARTMENT OF COMP. ENGINEERING, STCL 2015-16. 11
Web Application SQL Injection Preventer(WASP)
• Allow only developer-trusted strings to form parts of a query
05/28/21 SINHGAD COLLEGE OF ENGINEERING, DEPARTMENT OF COMP. ENGINEERING, STCL 2015-16. 12
Algorithm:Static Pattern Matching Algorithm
1. Procedure SPMA(Query,SPL[])
INPUT:QUERY<-user Generated Query
SPL<-Static Pattern with an Anomaly
Pattern
2. For j=1 to m do
3. If(AC(Query,StringLength(Query),SPL[J][0]==∅)
Then
4. Anomalyscore = Matchingvalue(Query,SPL[J] *100
StringLength(SPL[J])
5. If(Anomalyscore >==Thresholdvalue)
05/28/21 SINHGAD COLLEGE OF ENGINEERING, DEPARTMENT OF COMP. ENGINEERING, STCL 2015-16. 13
6. Then
7. Return Alarm->Administrator
8. Else
9. Return Query->Accepted
10. End If
11. Else
12. Return Query->Rejected
13. End for
End Procedure
05/28/21 SINHGAD COLLEGE OF ENGINEERING, DEPARTMENT OF COMP. ENGINEERING, STCL 2015-16. 14
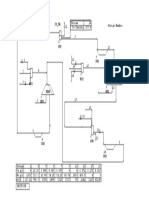
Architecture used for Detecting SQLIA
05/28/21 SINHGAD COLLEGE OF ENGINEERING, DEPARTMENT OF COMP. ENGINEERING, STCL 2015-16. 15
Defence Against SQL Injection
• Comprehensive data sanitization
• Limit database priviliges by context.
• Avoid constructing SQL queries with user input
05/28/21 SINHGAD COLLEGE OF ENGINEERING, DEPARTMENT OF COMP. ENGINEERING, STCL 2015-16. 16
Advantages
• SQL allows you to select and output data from database.
•It take advantage of security vulnerabilities in website and
application.
•SQL also allow yot to alter data in database and add new data.
05/28/21 SINHGAD COLLEGE OF ENGINEERING, DEPARTMENT OF COMP. ENGINEERING, STCL 2015-16. 17
Applications
• Attacker can use SQL injection vulnerabilities to bypass application
security measures.
• They can go around authntication and authorization of web
application to retrieve content of database.
• They can also use SQL injection to add,modify,and delete records in
database
05/28/21 SINHGAD COLLEGE OF ENGINEERING, DEPARTMENT OF COMP. ENGINEERING, STCL 2015-16. 18
Conclusion
• SQL injection is technique for utlizing applications that use
ralational database as their back end.
• Application compose SQL statements and send to database.
• All the database can be target of SQL injection and all are
vulnerable to this technique.
05/28/21 SINHGAD COLLEGE OF ENGINEERING, DEPARTMENT OF COMP. ENGINEERING, STCL 2015-16. 19
References
1.Mohd Amin Bin,Mohd Yunus,Nazri Mohd Nawi,”Review of SQL
Injection : Problems and Prevention”, VOL 2 (2018) NO 3 – 2.
2.Limei Ma,Yijun Gao,Dongmei Zhao,Chen Zhao,” Research on SQL
Injection Attack and Prevention Technology Based On Web”, 2019
International Conference on Computer Network, Electronic and
Automation (ICCNEA).
05/28/21 SINHGAD COLLEGE OF ENGINEERING, DEPARTMENT OF COMP. ENGINEERING, STCL 2015-16. 13
Thank You!
Guided By Presented By
Prof. N.P.Bunge Anjali Kumkar
SCOE, Pune (305B033 )
05/28/21 SINHGAD COLLEGE OF ENGINEERING, DEPARTMENT OF COMP. ENGINEERING, STCL 2015-16. 14
You might also like
- The Bitcoins KeysDocument5 pagesThe Bitcoins KeysJohn Smith0% (3)
- IITD CV PackDocument271 pagesIITD CV PackGopika AroraNo ratings yet
- Ipc A 610standardinelectricandelectronicDocument9 pagesIpc A 610standardinelectricandelectronicDuy Tuấn ĐàoNo ratings yet
- Digital JewelleryDocument25 pagesDigital JewelleryIsha Bhatia100% (1)
- Study On SQL Injection Attacks: Mode, Detection and PreventionDocument7 pagesStudy On SQL Injection Attacks: Mode, Detection and PreventionssNo ratings yet
- SQL Injections Seminar ReportDocument33 pagesSQL Injections Seminar ReportDipak GiteNo ratings yet
- Pondicherry University: Project Phase - 1Document12 pagesPondicherry University: Project Phase - 1kpalanivel123No ratings yet
- SQL Injections Seminar ReportDocument33 pagesSQL Injections Seminar ReportPrateekChauhan0% (4)
- An Efficient Technique For Detection and Prevention of SQL Injection Attack Using ASCII Based String MatchingDocument8 pagesAn Efficient Technique For Detection and Prevention of SQL Injection Attack Using ASCII Based String MatchingPramono PramonoNo ratings yet
- SQL Injection: Bachelor of TechnologyDocument17 pagesSQL Injection: Bachelor of TechnologyMuqheed ShaikNo ratings yet
- Combinatorial Approach to Prevent SQL InjectionDocument2 pagesCombinatorial Approach to Prevent SQL InjectionMoulika Sushma BuragaddaNo ratings yet
- Evaluating and Solving Canal Irrigation Problems with MLDocument39 pagesEvaluating and Solving Canal Irrigation Problems with MLTejal PatilNo ratings yet
- Esij Setsrw Mca Saec05Document4 pagesEsij Setsrw Mca Saec05ssNo ratings yet
- Effective Dynamic Detection of SQL Injection Attacks Without Source Code AccessDocument25 pagesEffective Dynamic Detection of SQL Injection Attacks Without Source Code AccessPramono PramonoNo ratings yet
- Implementation of Pattern Matching Algorithm To Defend SQLIADocument7 pagesImplementation of Pattern Matching Algorithm To Defend SQLIASiddesh S ANo ratings yet
- Wms 2.1Document10 pagesWms 2.1War LockNo ratings yet
- SSRN Id3141112Document6 pagesSSRN Id3141112anisharoysamantNo ratings yet
- Detection of SQL Injection Attacks Using Hidden Markov ModelDocument7 pagesDetection of SQL Injection Attacks Using Hidden Markov ModelPramono PramonoNo ratings yet
- Attendance Management System Project ReportDocument29 pagesAttendance Management System Project ReportanveshNo ratings yet
- SQL Injection Monitoring Security Vulnerabilities in Web ApplicationsDocument6 pagesSQL Injection Monitoring Security Vulnerabilities in Web ApplicationsInternational Journal of Application or Innovation in Engineering & ManagementNo ratings yet
- Vitae Dec 2010Document11 pagesVitae Dec 2010Andes PutraNo ratings yet
- Research_on_the_SCADA_system_constructing_methodolDocument6 pagesResearch_on_the_SCADA_system_constructing_methodoldarshan bsNo ratings yet
- Exp 08 MinorDocument2 pagesExp 08 MinorAshish MundhadaNo ratings yet
- Detection and Prevention of SQL Injectio PDFDocument5 pagesDetection and Prevention of SQL Injectio PDFPramono PramonoNo ratings yet
- Quiz Gaming System: Bachelor of Engineering IN Compuer Science and EngineeringDocument26 pagesQuiz Gaming System: Bachelor of Engineering IN Compuer Science and EngineeringKoveNo ratings yet
- Research Paper SQL InjectionDocument7 pagesResearch Paper SQL Injectioncjyjcyakf100% (1)
- Detection of SQL Injection-Katole2018Document6 pagesDetection of SQL Injection-Katole2018rafiNo ratings yet
- CV - Tanmoy - 1Document2 pagesCV - Tanmoy - 1Tanmoy BhowmikNo ratings yet
- DMS-Railway Management SystemDocument33 pagesDMS-Railway Management SystemSumit UshirNo ratings yet
- ETI Pro KomalDocument18 pagesETI Pro Komalmohit moreNo ratings yet
- Ellucian Internship API DevelopmentDocument23 pagesEllucian Internship API DevelopmentSanitha MichailNo ratings yet
- Internship Report Updated - 7th SemDocument37 pagesInternship Report Updated - 7th SemSatyam Kumar VermaNo ratings yet
- Alpin Ak Online Examination SystemDocument61 pagesAlpin Ak Online Examination SystemANDRU PRADHEEPNo ratings yet
- Transmission Line Protection in SimulinkDocument17 pagesTransmission Line Protection in SimulinkEE1029 Arushi JainNo ratings yet
- A Review On SQL Injection Prevention Technique: Navu - Verma@yahoo - inDocument6 pagesA Review On SQL Injection Prevention Technique: Navu - Verma@yahoo - inPankaj JindalNo ratings yet
- Iqbal Uzair 0625210 EResumeDocument4 pagesIqbal Uzair 0625210 EResumeuzair274No ratings yet
- D 5006Document2 pagesD 5006Sudhanshu BadolaNo ratings yet
- Shwetank CV New2Document3 pagesShwetank CV New2shwetank23No ratings yet
- Question BankDocument16 pagesQuestion BankvivekparasharNo ratings yet
- A Mini Project Report On (Size 16) Attendence Management SystemDocument35 pagesA Mini Project Report On (Size 16) Attendence Management SystemanveshNo ratings yet
- Using Positive Tainting and Syntax-Aware Evaluation To Counter SQL Injection AttacksDocument11 pagesUsing Positive Tainting and Syntax-Aware Evaluation To Counter SQL Injection AttacksKarthi KeyanNo ratings yet
- LarryGHankins - 2019 SDEInverterDsgnDocument1 pageLarryGHankins - 2019 SDEInverterDsgnGreg HankinsNo ratings yet
- Visvesvaraya Technological University: Traffic SignalDocument62 pagesVisvesvaraya Technological University: Traffic SignalMonisha AbNo ratings yet
- Integrated Circuit Design Summer Training ReportDocument61 pagesIntegrated Circuit Design Summer Training ReportRamesh Maurya MauryaNo ratings yet
- Fin Irjmets1686708368Document4 pagesFin Irjmets1686708368jahnavimaruru4No ratings yet
- Electrical Engineer ResumeDocument3 pagesElectrical Engineer ResumeDanish MohammedNo ratings yet
- MTS - 310: Proteus Design Suite for Microcontroller Based Systems LabDocument25 pagesMTS - 310: Proteus Design Suite for Microcontroller Based Systems LabHamza Nasir100% (1)
- AKM Seminar Report PDFDocument44 pagesAKM Seminar Report PDFASHOK KUMAR MUWALNo ratings yet
- Visvesvaraya Technological University, Belagavi: Submitted in The Partial Fulfilment of The 5 SEM of The Degree ofDocument28 pagesVisvesvaraya Technological University, Belagavi: Submitted in The Partial Fulfilment of The 5 SEM of The Degree ofsahanaNo ratings yet
- IPC-A-610 Standard in Electric and Electronic Laboratory For Engineering Students A Systematic Literature ReviewDocument9 pagesIPC-A-610 Standard in Electric and Electronic Laboratory For Engineering Students A Systematic Literature ReviewKarthik Mani0% (1)
- Auto Credit System DocumentationDocument47 pagesAuto Credit System Documentationcity cyberNo ratings yet
- Concept of "Finishing School For Engineering Students"Document4 pagesConcept of "Finishing School For Engineering Students"Amit Kumar SrivastavaNo ratings yet
- Prevention of SQL Injection Attacks by Using Service Oriented Authentication TechniqueDocument5 pagesPrevention of SQL Injection Attacks by Using Service Oriented Authentication TechniqueKarthik SNo ratings yet
- 2015 Ieee Ns2 Project TitlesDocument3 pages2015 Ieee Ns2 Project Titlesieee4mybusinessonlyNo ratings yet
- Fault Testing of CMOS Integrated Circuits Using Signature Analysis MethodDocument10 pagesFault Testing of CMOS Integrated Circuits Using Signature Analysis MethodInternational Journal of Application or Innovation in Engineering & ManagementNo ratings yet
- Obsolescence Risk and Lifecycle Prediction Using Gradient Boosting AlgorithmDocument36 pagesObsolescence Risk and Lifecycle Prediction Using Gradient Boosting AlgorithmAnusha RameshNo ratings yet
- Batch2csea FinalDocument36 pagesBatch2csea FinalAnusha RameshNo ratings yet
- Correct Front PageDocument9 pagesCorrect Front Pageaarthi_devNo ratings yet
- Database Management System: Course OutcomeDocument45 pagesDatabase Management System: Course OutcomeVishal TeslaNo ratings yet
- Buck Converter Full ProjectDocument38 pagesBuck Converter Full Project2k18-EE-243 Vethushan VinnayagamoorththiNo ratings yet
- FT Mini Alpha v1.0 Full-SizeDocument5 pagesFT Mini Alpha v1.0 Full-Sizea kNo ratings yet
- FT Explorer v1.0 AIODocument37 pagesFT Explorer v1.0 AIOMoises Garcia Durand100% (1)
- Identified Social ProblemDocument10 pagesIdentified Social Problema kNo ratings yet
- JLAKJDFLKKSJFDocument25 pagesJLAKJDFLKKSJFa kNo ratings yet
- JLAKJDFLKKSJFDocument25 pagesJLAKJDFLKKSJFa kNo ratings yet
- Seminar On Android: Submitted To: Submitted byDocument12 pagesSeminar On Android: Submitted To: Submitted bySaurabh SinghNo ratings yet
- Reference Seminar ReportDocument28 pagesReference Seminar Reporta k0% (1)
- Data Mining and Sentiment Analysis: A Seminar Report OnDocument39 pagesData Mining and Sentiment Analysis: A Seminar Report Ona kNo ratings yet
- Data Mining and Sentiment Analysis: A Seminar Report OnDocument39 pagesData Mining and Sentiment Analysis: A Seminar Report Ona kNo ratings yet
- Reference Seminar ReportDocument28 pagesReference Seminar Reporta k0% (1)
- S A A A+A - B++ B Y: Name - Compiler Exam Fall 2007Document8 pagesS A A A+A - B++ B Y: Name - Compiler Exam Fall 2007Nishant MishraNo ratings yet
- Videoxpert Storage: Product SpecificationDocument2 pagesVideoxpert Storage: Product SpecificationoseguraNo ratings yet
- Offer ExtensionDocument10 pagesOffer ExtensionVikashJainNo ratings yet
- Fluidos User ManualDocument37 pagesFluidos User ManualSao KhonNo ratings yet
- TF4 WattenbachetalDocument21 pagesTF4 WattenbachetalIvaturiAnithaNo ratings yet
- Project On: Steady State Heat Conduction and Convection in An Isotropic Rectangular PlateDocument35 pagesProject On: Steady State Heat Conduction and Convection in An Isotropic Rectangular PlateRahul BajakNo ratings yet
- Jedox Database FilesDocument5 pagesJedox Database FilesHenriNo ratings yet
- More Efficient Service Deployment With Dell Active System ManagerDocument21 pagesMore Efficient Service Deployment With Dell Active System ManagerPrincipled TechnologiesNo ratings yet
- Engineer Resume SummaryDocument4 pagesEngineer Resume SummarydeveshNo ratings yet
- Metsim Print 2018Document1 pageMetsim Print 2018worquera2507No ratings yet
- Check Point Certified Security Expert - R80 Exam A QuestionsDocument45 pagesCheck Point Certified Security Expert - R80 Exam A QuestionsAFSungoNo ratings yet
- Como Map Network Drives With Group PolicyDocument20 pagesComo Map Network Drives With Group PolicyMg. Juan Carlos ZegarraNo ratings yet
- Behaviour of P, Pi & Pid Controller From Matlab SimulinkDocument30 pagesBehaviour of P, Pi & Pid Controller From Matlab SimulinkDineshNo ratings yet
- REF611 Appl 757456 ENaDocument128 pagesREF611 Appl 757456 ENaphelo1No ratings yet
- Set Analysis Functions and OperatorsDocument4 pagesSet Analysis Functions and OperatorsIvo LegonNo ratings yet
- INTRF - MAPPING BackgroundDocument12 pagesINTRF - MAPPING BackgroundShelton Tapiwanashe Ndindana100% (1)
- Designing With Ethernet MAC ControllersDocument1 pageDesigning With Ethernet MAC ControllersKarthikeyan KrishnamoorthyNo ratings yet
- Problems Using Latest Software With Kensington Universal Docking Station (Sd400v) - Page 3 - DisplayLink ForumDocument4 pagesProblems Using Latest Software With Kensington Universal Docking Station (Sd400v) - Page 3 - DisplayLink ForumpacoNo ratings yet
- DAY 1 Assessment 1Document12 pagesDAY 1 Assessment 1Ethiopian CodeNo ratings yet
- Captains Courageous by Kipling, Rudyard, 1865-1936Document118 pagesCaptains Courageous by Kipling, Rudyard, 1865-1936Gutenberg.orgNo ratings yet
- Price List: AN ASI Telespazio CompanyDocument34 pagesPrice List: AN ASI Telespazio CompanyAri SulistyoNo ratings yet
- Amar Resume 2023Document1 pageAmar Resume 2023Karan vhatkarNo ratings yet
- Cucm B Administration-Guide-1251Document192 pagesCucm B Administration-Guide-1251Serhat DundarNo ratings yet
- Cryptocurrency NewDocument55 pagesCryptocurrency NewManoj ManuNo ratings yet
- Work Around To Disable and Remove OGA Office Not Genuine Notifications (Uninstall KB949810)Document5 pagesWork Around To Disable and Remove OGA Office Not Genuine Notifications (Uninstall KB949810)Sudipta DasNo ratings yet
- Electronics Seminar TopicsDocument11 pagesElectronics Seminar TopicsSreedhar RamNo ratings yet
- F4 Final ReportDocument12 pagesF4 Final ReportSYAKIRAH IRDINA SHAHAROL NIZAM100% (1)
- Bisnis GlobalDocument96 pagesBisnis GlobalMisda RomisNo ratings yet