Professional Documents
Culture Documents
Blow Fish
Uploaded by
mohammedfarhan.noorani23dse0 ratings0% found this document useful (0 votes)
1 views11 pagesCSS
Original Title
BlowFish
Copyright
© © All Rights Reserved
Available Formats
PPT, PDF, TXT or read online from Scribd
Share this document
Did you find this document useful?
Is this content inappropriate?
Report this DocumentCSS
Copyright:
© All Rights Reserved
Available Formats
Download as PPT, PDF, TXT or read online from Scribd
0 ratings0% found this document useful (0 votes)
1 views11 pagesBlow Fish
Uploaded by
mohammedfarhan.noorani23dseCSS
Copyright:
© All Rights Reserved
Available Formats
Download as PPT, PDF, TXT or read online from Scribd
You are on page 1of 11
Blowfish is an encryption technique
designed by Bruce Schneier in 1993 as an
alternative to DES Encryption Technique.
It is significantly faster than DES and
provides a good encryption rate with no
effective cryptanalysis technique found to
date.
It is one of the first, secure block cyphers
not subject to any patents and hence
freely available for anyone to use.
blockSize: 64-bits
keySize: 32-bits to 448-bits variable size
number of subkeys: 18 [P-array]
number of rounds: 16
number of substitution boxes: 4
[each having 256 entries of 32-bits each]
Two parts:
Expansion of the key.
Encryption of the data.
Expansion of the key:
Break the original key into a set of subkeys.
Key of no more than 448 bits is separated into
4168 bytes.
P-array and four 32-bit S-boxes.
P-array contains 18 32-bit subkeys.
Each S-box contains 256 entries.
The encryption of the data:
64-bit input is denoted with an x
P-array is denoted with a Pi (where i is the
iteration).
Each line - 32 bits.
Algorithm keeps two
sub-key arrays:
The 18-entry P-array
Four 256-entry S-boxes.
S-boxes accept 8-bit
input
Produce 32-bit output.
One entry of P-array is
used every round.
After final round, each
half of data block is
XORed with one of the
two remaining unused
P-entries.
Now each of the subkey is changed with
respect to the input key as:
P[0] = P[0] xor 1st 32-bits of input key
P[1] = P[1] xor 2nd 32-bits of input key . . .
P[i] = P[i] xor (i+1)th 32-bits of input key
(roll over to 1st 32-bits depending on the key
length) . . . P[17] = P[17] xor 18th 32-bits of
input key (roll over to 1st 32-bits depending
on key length)
Step2: initialise Substitution Boxes:
4 Substitution boxes(S-boxes) are
needed{S[0]…S[4]} in both encryption aswell
as decryption process with each S-box having
256 entries{S[i][0]…S[i][255], 0&lei&le4}
where each entry is 32-bit.
It is initialized with the digits of pi(?) after
initializing the P-array.
Step3: Encryption:
The encryption function consists of two parts:
a. Rounds: The encryption consists of 16 rounds
with each round(Ri) taking inputs the
plainText(P.T.) from previous round and
corresponding subkey(Pi). The description of
each round is as follows:
Blowfish's F-function.
Splits the 32-bit input into four eight-bit
quarters, and uses the quarters as input to the S-
boxes.
Outputs are added modulo 232 and XOR to
produce the final 32-bit output.
Blowfish is a Feistel network, it can be inverted
simply by XORing P17 and P18 to the ciphertext
block, then using the P-entries in reverse order.
Diagram of Blowfish's F function
You might also like
- List of Parts Singer 31-15 and 31-20Document296 pagesList of Parts Singer 31-15 and 31-20Just4Him89% (9)
- Implementation of Des AlgorithmDocument12 pagesImplementation of Des Algorithmambrish_pandey_1No ratings yet
- Cultural Anthropology: Appreciating Cultural Diversity by Conrad Kottak - 15e, TEST BANK 0078035007Document16 pagesCultural Anthropology: Appreciating Cultural Diversity by Conrad Kottak - 15e, TEST BANK 0078035007jksmtnNo ratings yet
- 32 TMSS 01Document35 pages32 TMSS 01Mohammed Madi67% (3)
- Megger Test Form-NewDocument2 pagesMegger Test Form-NewShahadad PNNo ratings yet
- Checklist of Mandatory Documentation Required by ISO 45001 enDocument12 pagesChecklist of Mandatory Documentation Required by ISO 45001 enashraf91% (11)
- Camshaft Adjustment, FunctionDocument2 pagesCamshaft Adjustment, FunctionPawluch100% (1)
- Blow FishDocument11 pagesBlow FishhfnunezNo ratings yet
- Blowfish AlgorithmDocument4 pagesBlowfish AlgorithmInternational Organization of Scientific Research (IOSR)100% (3)
- Blowfish AlgorithmDocument11 pagesBlowfish AlgorithmMomtaj Hossain MowNo ratings yet
- Network SecurityDocument12 pagesNetwork SecurityDivjot SinghNo ratings yet
- Unit - Ii: Information Security 1Document29 pagesUnit - Ii: Information Security 1Santhi PriyaNo ratings yet
- Cryptography-Symmetric - Modern - DeCDocument41 pagesCryptography-Symmetric - Modern - DeCLam CaoNo ratings yet
- DesDocument19 pagesDesmanju287No ratings yet
- Blow Fish Two Fish ArunDocument20 pagesBlow Fish Two Fish ArunSohan KumarNo ratings yet
- Chapter ThreeDocument30 pagesChapter ThreeMstafa MhamadNo ratings yet
- BlowfishDocument62 pagesBlowfishDhaval DoshiNo ratings yet
- BlowfishDocument21 pagesBlowfishoovoo90No ratings yet
- Unit2: Data Encryption StandardDocument78 pagesUnit2: Data Encryption StandardAbhishek RaoNo ratings yet
- Cryptography and Network Security Unit - 2 Chapter 3 - Block Ciphers and The Data Encryption StandardDocument86 pagesCryptography and Network Security Unit - 2 Chapter 3 - Block Ciphers and The Data Encryption StandardAkshit PrajapatiNo ratings yet
- Uni 2 (IDEA)Document14 pagesUni 2 (IDEA)hrishita.bhandaryNo ratings yet
- Data Encryption StandardDocument44 pagesData Encryption StandardAnkur AgrawalNo ratings yet
- NTC Project ReportDocument7 pagesNTC Project ReportDhivya KarthikeyanNo ratings yet
- Is DesDocument53 pagesIs Desbcsm-s21-005No ratings yet
- Unit 2Document49 pagesUnit 2Mansi AgrawalNo ratings yet
- SboxDocument7 pagesSboxZeco Neco100% (1)
- Enhancement of DES Algorithm With Multi State LogicDocument5 pagesEnhancement of DES Algorithm With Multi State LogicWhite Globe Publications (IJORCS)No ratings yet
- DesDocument58 pagesDesHarneet Singh ChuggaNo ratings yet
- Q. 162 What Are The Various Types of DES? What Are The Types of Operations Performed in DES?Document8 pagesQ. 162 What Are The Various Types of DES? What Are The Types of Operations Performed in DES?Pratik NagoriNo ratings yet
- IDEA and Blowfish NotesDocument10 pagesIDEA and Blowfish NotesMukesh100% (2)
- NSC Assignment RajeshDocument17 pagesNSC Assignment RajeshRAJESH KUMARNo ratings yet
- CSPC-307 Blow Fish and RC5 Stream Ciphers For B Tech CS August 2022Document37 pagesCSPC-307 Blow Fish and RC5 Stream Ciphers For B Tech CS August 2022NOOR ARORANo ratings yet
- CNS Unit 2Document119 pagesCNS Unit 2Mr.Ashok SNo ratings yet
- Chapter 3 - Block Ciphers and The Data Encryption StandardDocument15 pagesChapter 3 - Block Ciphers and The Data Encryption StandardrishabhdubeyNo ratings yet
- BlowFish (Cipher) 20161124Document14 pagesBlowFish (Cipher) 20161124Rami Khalil RouchdiNo ratings yet
- Aes and DesDocument11 pagesAes and Des20PCT19 THANISHKA SNo ratings yet
- Cryptography Block Ciphers and The Data Encryption Standard (DES)Document55 pagesCryptography Block Ciphers and The Data Encryption Standard (DES)sonyNo ratings yet
- Number Theory & CryptographyDocument18 pagesNumber Theory & CryptographyPrateek ParashariNo ratings yet
- DES (Data Encryption Standard)Document39 pagesDES (Data Encryption Standard)Anonymous LsxNp3rNRNo ratings yet
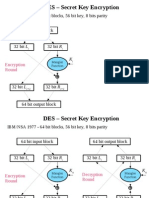
- DES - Secret Key Encryption: IBM/NSA 1977 - 64 Bit Blocks, 56 Bit Key, 8 Bits Parity 64 Bit Input BlockDocument14 pagesDES - Secret Key Encryption: IBM/NSA 1977 - 64 Bit Blocks, 56 Bit Key, 8 Bits Parity 64 Bit Input BlockRock GamerNo ratings yet
- CSS Lab ManualDocument32 pagesCSS Lab ManualQaif AmzNo ratings yet
- Blow Fish AlgorithmDocument5 pagesBlow Fish AlgorithmDil LipNo ratings yet
- IdeaDocument34 pagesIdeasukla.banerjee6427No ratings yet
- Lab 6Document35 pagesLab 6Ebtisam HamedNo ratings yet
- Data Encryption StandardDocument4 pagesData Encryption StandardLionel Bharath RazerNo ratings yet
- CNS UNIT-2 NotesDocument30 pagesCNS UNIT-2 Notespravallika100% (1)
- Des, Double Des AesDocument11 pagesDes, Double Des AesUttam KolekarNo ratings yet
- Chapter 3 Block CipherDocument18 pagesChapter 3 Block CipherFadhliEleeNo ratings yet
- Cryptography - Lecture3Document27 pagesCryptography - Lecture3AbhijeetNo ratings yet
- NSC Unit 2 Zoom Cls (15-04-2020)Document20 pagesNSC Unit 2 Zoom Cls (15-04-2020)yuvaraaj aletiNo ratings yet
- Practical No.5 DESDocument5 pagesPractical No.5 DESRahul PatelNo ratings yet
- Symmetric Cryptography: Block Ciphers Lecture 4 (May 7, 2012)Document58 pagesSymmetric Cryptography: Block Ciphers Lecture 4 (May 7, 2012)Agajan TorayevNo ratings yet
- Data Encryption StandardsDocument16 pagesData Encryption Standardssanthosh n prabhuNo ratings yet
- Security Enhancement: Combining Cryptography and SteganographyDocument4 pagesSecurity Enhancement: Combining Cryptography and Steganographyben_sundarNo ratings yet
- Conventional Encryption AlgorithmsDocument41 pagesConventional Encryption AlgorithmsSwapna DollyNo ratings yet
- Loki 97Document22 pagesLoki 97Diego Durán100% (1)
- Blow Fish EncryptionDocument7 pagesBlow Fish EncryptionramachandraNo ratings yet
- Serpent: A Proposal For The Advanced Encryption StandardDocument23 pagesSerpent: A Proposal For The Advanced Encryption StandardscribblenotesNo ratings yet
- BlowfishDocument9 pagesBlowfishukakkad2011No ratings yet
- Unit IiDocument60 pagesUnit Iitalatamhari2002No ratings yet
- Unit 2Document61 pagesUnit 2Bibhushan Jung SijapatiNo ratings yet
- UNIT-2 Stream Ciphers and Block Ciphers: Cryptography and Network Security (3161606)Document32 pagesUNIT-2 Stream Ciphers and Block Ciphers: Cryptography and Network Security (3161606)Ganesh GhutiyaNo ratings yet
- Blowfish (Cipher) - Wikipedia, The Free EncyclopediaDocument4 pagesBlowfish (Cipher) - Wikipedia, The Free EncyclopediaAndi WidiasmoroNo ratings yet
- Ata Ncryption Tandard: D E S DESDocument39 pagesAta Ncryption Tandard: D E S DESritesh sinhaNo ratings yet
- Ae Lab ManualDocument48 pagesAe Lab Manualसंकेत कलगुटकर100% (1)
- 10 Synp.2023Document9 pages10 Synp.2023jangahkmNo ratings yet
- Method Statement For InstallationDocument5 pagesMethod Statement For Installationsamsul maarifNo ratings yet
- Manual de Mantenimiento PERKINS Serie 2500Document84 pagesManual de Mantenimiento PERKINS Serie 2500DamarickPachecoNo ratings yet
- TA20 03 NBS Domestic SampleDocument17 pagesTA20 03 NBS Domestic SampleScott2771No ratings yet
- Drill HolesDocument304 pagesDrill HolesJorge Luis Zegarra OtoyaNo ratings yet
- Europass Curriculum Vitae: Personal InformationDocument2 pagesEuropass Curriculum Vitae: Personal InformationNatasa BudisinNo ratings yet
- Circulating Fluidized Bed BoilerDocument96 pagesCirculating Fluidized Bed BoilerMuhammad Talha Abid100% (1)
- Learning Outcomes RaDocument11 pagesLearning Outcomes Raapi-349210703No ratings yet
- C-4DS & C-4DL Electric Bed User Manual-Rev180810Document30 pagesC-4DS & C-4DL Electric Bed User Manual-Rev180810hector raffaNo ratings yet
- Conductímetro Sper Manual Del UsuarioDocument45 pagesConductímetro Sper Manual Del UsuarioEduardo Zunino100% (1)
- Solution Manual For Introductory Econometrics A Modern Approach 6Th Edition Wooldridge 130527010X 9781305270107 Full Chapter PDFDocument29 pagesSolution Manual For Introductory Econometrics A Modern Approach 6Th Edition Wooldridge 130527010X 9781305270107 Full Chapter PDFlois.payne328100% (18)
- Kumpulan 100 Soal TOEFL Written ExpressiDocument8 pagesKumpulan 100 Soal TOEFL Written ExpressiPuji AmbarNo ratings yet
- Fix Api: Developers GuideDocument36 pagesFix Api: Developers GuideAlex CurtoisNo ratings yet
- 70-270: MCSE Guide To Microsoft Windows XP Professional Second Edition, EnhancedDocument46 pages70-270: MCSE Guide To Microsoft Windows XP Professional Second Edition, EnhancedManish BansalNo ratings yet
- The Steps How To Use Theodolite For SurveyingDocument2 pagesThe Steps How To Use Theodolite For Surveyinglong bottomNo ratings yet
- 300+ TOP Automobile Engineering Multiple Choice Questions AnswersDocument27 pages300+ TOP Automobile Engineering Multiple Choice Questions Answerser9824925568100% (1)
- Hetron Fabrication Process PDFDocument57 pagesHetron Fabrication Process PDFDyah AyuNo ratings yet
- Esd Valve Actuator SizingDocument19 pagesEsd Valve Actuator Sizingshinojbaby4148No ratings yet
- Cuzn37 Industrial RolledDocument6 pagesCuzn37 Industrial RolledcvgfgNo ratings yet
- 15 Canteens and RestroomsDocument5 pages15 Canteens and RestroomsОлександра СеменкоNo ratings yet
- VadafoneDocument12 pagesVadafoneSantosh MirjeNo ratings yet
- Expose PolymerDocument7 pagesExpose PolymerKarfala KandeNo ratings yet
- PythonDocument2 pagesPythonVaibhaw ShiwarkarNo ratings yet