Professional Documents
Culture Documents
Design & Implementation of An Encryption Algorithm For Use in RFID System
Uploaded by
SPAM rohitOriginal Title
Copyright
Available Formats
Share this document
Did you find this document useful?
Is this content inappropriate?
Report this DocumentCopyright:
Available Formats
Design & Implementation of An Encryption Algorithm For Use in RFID System
Uploaded by
SPAM rohitCopyright:
Available Formats
International Journal of RFID Security and Cryptography (IJRFIDSC), Volume 1, Issues 1/2, March/June 2012
Design & Implementation of an Encryption Algorithm for use in RFID
System
M. B. Abdelhalim M. El-Mahallawy , A. Elhennawy
AASTMT Cairo, Egypt M. Ayyad ASU Cairo, Egypt
mbakr@ieee.org AASTMT Cairo, Egypt a.hennawy@hotmail.com
mahallawy@ieee.org;
mayyad@ieee.org
Abstract authentication and strong authentication schemes
such as those based on a challenge and response
The Tiny Encryption Algorithm (TEA) is a concept. Many RFID authentication protocols use
suitable lightweight cryptographic algorithm used in cryptographic techniques to protect messages
medium security systems such as RFID systems. The exchanged over a radio frequency interface from
TEA is a fiestel structure used to satisfy the eavesdropping. Compared to asymmetric or public
confusion and the diffusion properties to hide the key alternatives, a symmetric key is generally less
statistical characteristics of the plaintext. However, complicated, requires less number of operations, and
TEA has few weaknesses, most notably from can have the same security strength as its asymmetric
equivalent keys and related-key attacks. So, a equivalence using a key of smaller size. These facts
Modified TEA algorithm (MTEA) is proposed which make the symmetric key approach more suitable for
uses the Linear Feedback Shift Register (LFSR) to limited resource RFID systems [2].
overcome the security weakness of the TEA RFID tags have limited processing power and
algorithm against attacks. In this paper an storage because of tight tag cost requirements.
implementation of MTEA algorithm is presented and Symmetric cryptographic schemes, such as hash
benchmarked with the standard TEA algorithm functions and symmetric encryption algorithms, are
considering the area and power consumption. commonly used. As a result, authentication protocols
for RFID systems should not only be designed to
1. Introduction address privacy and security threats, but should also
take into account the limited capabilities of RFID
Radio Frequency IDentification (RFID) is an tags.
automatic identification technology which consists of Tiny Encryption Algorithm (TEA) is a
two main parts (Reader and tag for object) that uses lightweight cryptographic algorithm which makes it
radio waves to identify objects. The main benefits of suitable for embedded systems that require high
RFID systems are that they can provide automated performance; ease of implementation, high speed,
contactless identification of a range of physical low power consumption and low cost beside security
entities, and can be used to track valuable objects. [3]. All these requirements need a simple
From the way in which RFID tags operate via a cryptographic algorithm such as TEA. TEA can meet
wireless radio communications channel, there is a these requirements and has a resistance towards
concern about privacy and security, including the differential cryptanalysis; however, it has a simple
possibility of eavesdropping, snooping, cloning, key schedule which makes it weak against the related
counterfeiting and tracking of end users since key attacks [4].
information stored in tags can easily be retrieved by A modification in the standard TEA (MTEA) is
hidden readers, eventually leading to violation of proposed to improve the security strength of the TEA
user privacy and tracking of individuals by the tags against attacks by using a Pseudo Random Number
they carry [1]. Generator (PRNG) such as Linear Feedback Shift
One of the best ways to provide security and Register (LFSR) where the MTEAs key is
privacy measures is through an authentication frequently changed in each round instead of using
process. Authentication is an assurance of the one key only for all rounds in the standard TEA [5].
identity of an entity at the other end of TEA and MTEA is a fiestel structure network
communication channel. There are various which depends on the confusion & diffusion
authentication schemes or protocols such as properties as a substitution & permutation properties
password protection which is an example of a weak respectively. In [5], these properties are tested using
completeness & avalanche effect properties which
Copyright 2012, Infonomics Society 51
International Journal of RFID Security and Cryptography (IJRFIDSC), Volume 1, Issues 1/2, March/June 2012
result in good performance for MTEA rather than Some ciphers use arithmetic operations as a
TEA algorithm. diffusion and confusion technique, but this can
In this paper, the proposed MTEA is implemented significantly increase the area and power
and we will point to several issues that need to be consumption. On the other hand, bit permutations in
taken care of when implementing the design such as hardware can be realized with wires and no
limitation of silicon area and power consumption in transistors are involved. They are therefore a very
RFID systems. efficient component [7].
This paper is organized as follows: Sections 2
present an introduction of the fiestel cipher. Sections 3. Tiny Encryption Algorithm
3 and 4 provide brief introductions to TEA and
MTEA block cipher, respectively. Section 5 TEA is a block cipher with block length of 64 bits
evaluates MTEA implementation compared to the and key lengths of 128 bits. It is a Feistel type cipher
standard TEA implementation. Finally, in section 6 as shown in Figure 2 which uses operations from
we conclude the paper and draws guidelines for mixed (orthogonal) algebraic groups. A dual shift
future enhancements. causes all bits of the data and key to be mixed
repeatedly. The key schedule algorithm is simple; the
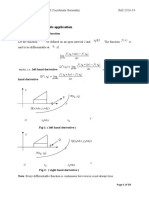
2. The Fiestel cipher: 128-bit key K is split into four 32-bit blocks (K[0],
K[1], K[2], K[3]) and the 64-bit plaintext is split into
The Fiestel cipher structure is proposed to hide two 32-bit blocks (Yi and Zi).
the statistical characteristic of the plaintext by using
an alternative of substitution & permutation. This
idea first proposed by Claude Shannon to develop
the block cipher that alternates confusion & diffusion
[6]. Shannon was concern about cryptanalysis
depend on the statistical analysis of the plaintext that
some messages in different languages have the
frequency distribution such as letters, words or
phrases which may be transferred to the ciphertext at
the same frequency distribution. If the attacker has
some knowledge about these statistics, maybe he can
get the encryption key used to encrypt the plaintext.
Shannon suggests two strategies to hide the
statistical characteristics of the plaintext: diffusion &
confusion.
- Diffusion: its target to make the statistical
analysis relationship between the plaintext &
ciphertext as complex as possible to thwart any
attempts from attacker to notice the key. Figure 1. Feistel encryption network.
- Confusion: its target to make the statistical
analysis relationship between the ciphertext & the The TEA operations rely on the alternate use of
encryption key as complex as possible to thwart any XOR and ADD to provide nonlinearity. Addition and
attempts from attacker to find the key. subtraction are used as the reversible operators for
In the Fiestel Cipher Structure: the concept of encryption and decryption rather than XOR. A dual
confusion & diffusion done by using substitution & shift causes all bits of the key and data to be mixed
permutation in the Fiestel Cipher Structure repeatedly. The number of rounds can be 16 cycles
sometimes called Fiestel Network as shown in (32-iterations) or 32 cycles (64-iterations). The key
Figure 1. is set at 128 bits as this is enough to prevent simple
- Substitution: is done on the left half of the search techniques from finding the key [4].
plaintext after the function F is applied to the right
half then; the output of it is XORed with the left half. The constant number, delta, is derived from the
The function F is the same structure in each round. golden number ratio [4]:
- Permutation: is done by interchanging the two
halves of the plaintext every round. ( 5 1) * 231 = 9E3779B9h
Decryption process is the same as the encryption delta = (1)
process except that the sub key used with the
function F is in the reverse order. The Feistel cipher delta[i] = (i +1) * delta, i = 0,1,2,,31 (2)
structure is used in many symmetric block ciphers
such as Data Encryption Standard (DES) & Tiny
Encryption Algorithm (TEA).
Copyright 2012, Infonomics Society 52
International Journal of RFID Security and Cryptography (IJRFIDSC), Volume 1, Issues 1/2, March/June 2012
where delta is used to ensure that the sub keys are
distinct and its precise value has no cryptographic
significance.
1 2 3 128 LFSR
128 bit key
Yi (0:31) Zi (32:63)
K[0]
1:32
<<4
TEA Deltaj
algorithm
>>5
33:64
( 5 1 )* 2 31
K[1]
The constant delta
( 5 1 )* 2 31
9E3779B9h K[2]
65:96
<<4
Deltaj
32-cycle
>>5
64-round
97:128
K[3]
C (0:31) P : 64-bit (2 x 32-bit) C (32:63)
Key : 128-bit (4 x 32-bit)
Figure 2. Tiny Encryption Algorithm block diagram
In Figure 4, using the input "Mohammad" which Figure 3. Modified Tiny Encryption Algorithm
ASCII code is "4D 6F 68 61- 4D 4D 61 64" and the (MTEA) block diagram
key "AbdallahOmarAyad" which ASCII code is "41
62 64 61 - 6C 6C 61 68 - 4F 4D 61 72 - 41 79 61 An n-bit LFSR can be in one of 2n - 1 internal
64"; the encrypted data is "43 64 A8 4A - 1E 55 9C state. This means that it can, in theory, generate a 2n
48" which will be used in the decryption side to 1 bit-long pseudo-random sequence before
recover the original plaintext "Mohammad"as sown repeating. It is 2n - 1 and not 2n because a shift
in Figure 5. register filled with zeros will cause the LFSR to
output a never ending stream of zerosthis is not
4. The proposed modified TEA algorithm particularly useful. Only LFSRs with certain tap
sequences will cycle through all 2n - 1 internal states;
In order to increase the TEA security against these are the maximal-period LFSRs. The resulting
cryptanalysis, a PRNG is used to generate a new key output sequence is called an m-sequence[8]
every round. We propose to use LFSR as a PRNG as The characteristic polynomial of an LFSR
shown in Figure 3 for its ease of implementation generating a maximum-length sequence is a
using a software or hardware [5]. primitive polynomial where:
A feedback shift register is made up of two parts:
a shift register and a feedback function. The shift number of 1s = number of 0s + 1
register is a sequence of bits [8], the length of a shift same number of runs of consecutive 0s and
register is figured in bits; if it is n bits long, it is 1s
called an n-bit shift register. Each time a bit is fed to 1/2 of the runs have length 1
LFSR, all of the bits in the shift register are shifted 1/4 of the runs have length 2
one bit to the right. The new left-most bit is It is proved that LFSRs achieve best performances
computed as a function of the other bits in the by using one of the following polynomials [8-10]:
register. The output of the shift register is one bit,
often the least significant bit. The period of a shift P1(X) = 1+X64+X78+X123+X128 (3)
register is the length of the output sequence before it P2(X) = 1+X +X + X +X +X 32 47 58 121 128
(4)
starts repeating.
2 7 128
The simplest kind of feedback shift register is a P3(X) = 1+X+X +X +X (5)
linear feedback shift register. The feedback function One of the mentioned polynomials is used to
is simply the XOR of certain bits in the register; the generate 128-bit key in each round, so we have 32 *
list of these bits is called a tap sequence. 128 bits keys for each block.
Copyright 2012, Infonomics Society 53
International Journal of RFID Security and Cryptography (IJRFIDSC), Volume 1, Issues 1/2, March/June 2012
It is worthy to mention that the key of the final Moreover, it was proven that the performance
round will be used as the key of the first round in the degradation of MTEA could be neglected when the
decryption process; hence this is the key that will be algorithm is implemented using MATLAB tool [5].
given to the users. This feature adds another The remaining metric that shows the superiority of
advantage to the proposed technique as the keys MTEA over standard TEA is actual Hardware
given to the users, i. e. decryption keys, are different
compared to the original algorithm where the same Table 2. Avalanche Effect Test Evaluation
key is used in the encryption and decryption
processes; hence the key secrecy is highly preserved. M TEA M TEA MTEA
Block
In [5], the security strength of the proposed #
TEA
(P1) (P2) (P3)
modified encryption algorithm (MTEA) is tested
using two important security analysis criteria for 1 42.18 51.56 53.12 48.43
block cipher; Completeness and avalanche effect 2 45.31 48.43 48.43 65.62
tests. These tests are evaluated, compared to that of 3 46.87 62.5 42.18 43.75
the standard TEA algorithm and proved that MTEA
provides better strength as shown in table 1 and table 4 56.25 62.5 48.43 50
2. 5 46.87 37.5 45.31 53.12
Completeness test was done by using matrix of 6 46.87 50 54.68 50
(64 x 64) elements with 65 plaintexts of length 64
7 57.81 56.25 53.12 50
bits, the difference between each plaintext and the
next one is only one bit. Each plaintext is encrypted 8 50 54.68 53.12 64.06
and its output ciphertext is XORed with the 9 48.43 54.68 53.12 48.43
previous output from the previous plaintext. Finally, 10 48.43 50 50 57.81
these results are written in the matrix until the matrix
11 45.31 54.68 57.81 62.5
is completed. The number of ones in this matrix is
added and then the percentage average value of this 12 57.81 65.62 48.43 42.18
matrix is taken, this percentage determine how an 13 48.43 48.43 45.31 48.43
algorithm can achieve the percentage of 14 56.25 57.81 46.87 46.8
completeness effect that each bit of the ciphertext
needs to depend on many bits on the plaintext [11]. 15 50 51.56 40.62 57.81
This test is performed for the standard TEA as well 16 42.18 48.43 54.68 46.8
as MTEA which uses 3 different polynomials P1, P2 17 37.5 57.81 54.68 51.56
and P3 in equations (3), (4) and (5). The results are
18 56.25 62.5 48.43 50
shown in table 1.
19 50 51.56 57.81 56.25
Table 1. Completeness effect test evaluation 20 39.06 50 50 37.5
Ave. 31.1 34.45 32.2 33
Modified TEA Modified TEA Modified TEA
TEA
(P1) (P2) (P3) 5. Hardware implementation of MTEA
0.4836 0.5046 0.4968 0.4885
Implementing cryptographic functionality on
Avalanche effect test is done by encrypting 20 RFID tags is limited not only by the available silicon
plaintexts that results in 20 ciphertexts; after that, the area, but also by the available power for computing
same 20 plaintexts are encrypted again but with only cryptographic operations. Transponders basically
one bit difference in the key that is used in the operate as active or passive devices. The
previous test. Each two ciphertexts resulted from the functionality of both types is similar; the main
same plaintext using the key & its one bit different difference is the increased performance in view of
version are XORed together. The number of ones communication distance and computation
from this XORing is calculated and then the capabilities of the active vs. the lower cost of the
percentage average of each result (number of ones / passive transponders. The integrated battery
64- bit) is obtained. Finally, the percentage average increases the cost of the transponder, limits the tags
for all 20 results is calculated for evaluating the life time, causes environmental issues over disposal,
avalanche effect for an algorithm when an input/key and limits the form factor and thickness of the tag.
is changed slightly, the output changes significantly Most relevant for implementing cryptographic
[11]. This test is done for the standard TEA and circuits are HF systems working on 13.56MHz and
MTEA which uses 3 different polynomials P1, P2 UHF systems operating at 900 MHz [12]. Both
and P3 in equations (3), (4) and (5). The results are systems have in common that only a small fraction of
shown in table 2. the energy emitted at the interrogators antenna is
Copyright 2012, Infonomics Society 54
International Journal of RFID Security and Cryptography (IJRFIDSC), Volume 1, Issues 1/2, March/June 2012
received by the RFID tag. Both systems induce a Therefore we compared the two algorithms using
voltage in the antenna of the RFID tag. The pre-layout implementation.
characteristics of HF and UHF fields define the The power measurements shown in Table 3, with
constraints for energy and power consumption of 3.3V supply [14], are for 51.2 kbps throughput,
RFID tags. When implementing cryptographic which is the requirement for 2.5-milli-second process
circuits on RFID tags it is desired that the time.
cryptographic functionality does not limit the Table 3 shows that the area increase of MTEA
operating range. Thus, the tags have to satisfy with over standard TEA is not significant, the maximum
the limited power and energy budget. Before clock speed for the two algorithms is so close due to
discussing these limits it is necessary to clarify the fact that the added LFSR, in MTEA, runs in
whether power consumption or energy consumption parallel and will not affect the critical path delay.
is more important for passive RFID tags [13]. Throughputs of the two algorithms are similar as
Hardware specifications of an encryption core for MTEA is build upon the parallel architecture of the
low-cost RFID tag are: standard TEA; therefore they have the same number
of clock cycles per iteration.
Area Less than 0.25 milli-meter square (or The throughput can be calculated from the
4,000 gates) equation (6) [2].
Power Less than 30 micro watt
Execution time 2.5 milli-second for Data size * max. clock speed (6)
encryption Throughput =
no. of clocks per cycle * no. of cycles
where data size is 64 bits, no. of clocks per cycle
For a typical 0.35-m CMOS technology, the is 1 and no. of cycles is 32 cycles.
maximum layout areas allowed translate to
Regarding the power consumption, Prime Time
equivalent numbers of gates from 2,000 to
tool from Synopsys Inc. is used to calculate the
4,000 gates [14].
The proposed design (MTEA) is implemented power as in [2]. The power consumption is divided
using VHDL description language and evaluated into two main components: internal power and net
with respect to the parallel architecture for the switching power. The authors of [2] did not mention
standard TEA in [2] as a suitable lightweight the nature of their power calculation; therefore we
cryptographic algorithm for passive RFIID tag. provided, in Table III, the total power as well as the
Figure 6 and Figure 7 show the encryption and net switching power. The Table shows that there is
decryption results for MTEA. an increase in the power consumption in MTEA over
In Figure 6, using the input "Mohammad" which the standard TEA. However, this increase is
ASCII code is "4D 6F 68 61- 4D 4D 61 64" and the acceptable as the power still within acceptable range.
key "AbdallahOmarAyad" which ASCII code is "41
62 64 61 - 6C 6C 61 68 - 4F 4D 61 72 - 41 79 61 Table 3. Pre-layout synthesis results comparison
64"; the encrypted data is "94 04 11 F8 - 2B 07 4A Original
4A". This output is provided to the decryption circuit TEA TEA MTEA MTEA
Algorithm TEA
ENC DEC ENC DEC
but with using the last key generated from the ENC [2]
encryption circuit, which is "D3 A2 6C 6A -20 B1 Pre-routed
area 0.207 0.262 0.3 0.337 0.346
32 30 - B6 36 30 B4 27 A6 B0 B9", and the (mm2)
decrypted output is similar to the original data as Maximum
shown in Figure 7. clock speed 53 66.8 69.1 67.1 64.3
We implemented MTEA and standard TEA using (MHz)
Maximum
0.35-m CMOS technology which is the same throughput 106 133.6 138.2 134.2 128.6
technology used for the standard TEA in [2] using rate (Mbps)
the same parallel architecture with the difference of Power (W)
adding LFSR in key generation. For the sake of fair at 51.2
7.37 546.1 519.9 903.6 969.8
(kbps) at
comparison, we used the same synthesis tool as in
100 (KHz)
[2], namely, Lenoardo Spectrum from Mentor Net
Graphics Inc. the output of the synthesis tool is a pre- switching - 119.5 102.8 68.69 116.4
layout implementation using library primitives. power (W)
Table 3 shows the comparison between MTEA Power (W)
at 51.2
and standard TEA with respect to area, performance, (kbps) at 1
- 650 626.7 1478 1072
throughput and power. The second column shows the (MHz)
results of the standard TEA implementation in [2]. Net
The results are for post-layout implementation where switching - 176.3 161.3 375.2 171.6
power (W)
no details are given for the post layout step.
Copyright 2012, Infonomics Society 55
International Journal of RFID Security and Cryptography (IJRFIDSC), Volume 1, Issues 1/2, March/June 2012
It is worthy to mention that all the results are [5] M. Elmahallawy, M. B. Abdelhalim, M. Ayyad, A.
Elhennawy. Security analysis for a lightweight modified
based on pre-layout implementations. We believe cryptographic TEA algorithm, 4th International
that better results would be obtained after performing Conference on Computer and Electrical Engineering
the layout step. ICCEE, Singapore, Malaysia, 2011.
[6] Shannon, C.E., Communication Theory of Secrecy
6. Conclusion and future work Systems . Bell System Technical Journal, v. 28, n. 4,
1949, p. 656715.
In this paper, a hardware implementation of the
Modified TEA algorithm (MTEA) is proposed which [7] C. Paar, A.Posshmann, and M.J.B. Robshaw, New
Design in Lightweight Symmetric Encryption, RFID
uses the Linear Feedback Shift Register (LFSR) to Security: Techniques, Protocols and System-On-Chip
overcome the security weakness of the standard TEA Design, Springer US, 2009.
algorithm against attacks. The implementation of
MTEA algorithm is benchmarked with the standard nd
[8] S. Bruce, Applied Cryptography. 2 edition, John
TEA algorithm considering the area, throughput and Wiley and Sons, Inc, 1996.
power consumption. The pre-layout synthesis results
show that there is no significant degradation in the [9] L. Cedric, From Hardware to Software Synthesis of
considered metrics due to using MTEA over standard Linear Feedback Shift Registers, IEEE Parallel and
Distributed Processing Symposium, Long Beach, CA,
TEA; hence MTEA is a good security candidate to USA, 2007, pp. 1-8.
be implemented in RFID systems.
In the future, we plan to perform the layout step [10]H. Martin, J. Thomas, M. Alexender, M. Willi, A
for the proposed MTEA design to meet the Stream Cipher Proposal: Grain-128, IEEE International
limitations for silicon area, throughput and power Symposium on Information Theory, Seattle, WA,
USA,2006, pp.1614-1618.
consumption for RFID system.
[11]B. Kam, I. DAVIDA. Structured Design of
7. References Substitution-Permutation Encryption Network, IEEE
Transactions on Computers, vol. 28, no.10, 1979 , pp.747-
[1] D. Tassos, RFID Security and Privacy, RFID 753.
Security: Techniques, Protocols and System-On-Chip
Design, Springer US, 2009. [12] C. Paar, A. Poschmann, M.J.B. Robshaw, "New
Designs in Lightweight Symmetric Encryption", RFID
[2] P. Israsena, Design and Implementation of Low Security: Techniques, Protocols and System-On-Chip
Power Hardware Encryption for Low Cost Secure RFID Design. Springer US, 2009.
Using TEA, Fifth International Conference in
Information, Communications and Signal Processing, [13] S. E. Sarma, Towards the 5 /c Tag, Technical
Bangkok, Thailand, 2005. Report MIT-AUTOID-WH-006. MIT, Auto-ID Center,
2001.
[3] D. Issam, H. Samer, D. Hassan. Efficient Tiny [14] Austria Micro Systems, 0.35m CMOS Digital
Hardware Cipher Under Verilog, Proceedings of the 2008 Standard Cell Databook, 2003.
High Performance Computing and Simulation Conference,
Nicosia, Cyprus, 2008.
[4] A. V. Reddy, A Cryptanalysis of the Tiny Encryption
Algorithm, Master of Science, Department of Computer
Science in the Graduate School, The university of
Alabama, 2003.
Figure 4. TEA encryption results
Copyright 2012, Infonomics Society 56
International Journal of RFID Security and Cryptography (IJRFIDSC), Volume 1, Issues 1/2, March/June 2012
Figure 5. TEA decryption results
Figure 6. MTEA encryption results
Figure 7. MTEA decryption results
Figure 7. MTEA decryption results
Copyright 2012, Infonomics Society 57
You might also like
- A Study and Analysis On Symmetric Cryptography: Sourabh Chandra Siddhartha Bhattacharyya Smita Paira SK Safikul AlamDocument8 pagesA Study and Analysis On Symmetric Cryptography: Sourabh Chandra Siddhartha Bhattacharyya Smita Paira SK Safikul AlamSamuele TesfayeNo ratings yet
- JETIR2308519Document9 pagesJETIR2308519Hitesh TumsareNo ratings yet
- Study on Cryptanalysis of Tiny Encryption AlgorithmDocument4 pagesStudy on Cryptanalysis of Tiny Encryption Algorithmmiki_dudaulNo ratings yet
- A Review On RSA Encryption Algorithm: Shaina Garg, Dr. Mukesh Kumar RanaDocument4 pagesA Review On RSA Encryption Algorithm: Shaina Garg, Dr. Mukesh Kumar RanaPatient ZeroNo ratings yet
- Randomness Evaluation Framework of Cryptographic AlgorithmsDocument19 pagesRandomness Evaluation Framework of Cryptographic AlgorithmsijcisjournalNo ratings yet
- Implementation of Aes and Blowfish AlgorithmDocument4 pagesImplementation of Aes and Blowfish AlgorithmInternational Journal of Research in Engineering and TechnologyNo ratings yet
- VideoStegnography (Synopsis) @mumbai AcademicsDocument17 pagesVideoStegnography (Synopsis) @mumbai AcademicsMumbai AcademicsNo ratings yet
- Use of Cryptography and Signing For Network SecurityDocument6 pagesUse of Cryptography and Signing For Network SecurityIJRASETPublicationsNo ratings yet
- Encryption and Decryption Using AES in The Field of Network Communication Based On ConfidentialityDocument3 pagesEncryption and Decryption Using AES in The Field of Network Communication Based On ConfidentialityUjjwal KumarNo ratings yet
- Jecet: Journal of Electronics and Communication Engineering & Technology (JECET)Document13 pagesJecet: Journal of Electronics and Communication Engineering & Technology (JECET)IAEME PublicationNo ratings yet
- Peformance Analysis and Implementation of Scalable Encryption Algorithm On FpgaDocument6 pagesPeformance Analysis and Implementation of Scalable Encryption Algorithm On FpgaVijay KannamallaNo ratings yet
- DR Waseem PaperDocument21 pagesDR Waseem PaperAsadullah Tariq TariqNo ratings yet
- A New Symmetric Cryptosystem Using RandoDocument7 pagesA New Symmetric Cryptosystem Using RandoNget ThearithNo ratings yet
- CISSP CryptographyDocument1 pageCISSP CryptographyonlysubasNo ratings yet
- Irjet Image Encryption Techniques and CoDocument14 pagesIrjet Image Encryption Techniques and Cosnehpatel0308No ratings yet
- International Journal of Computer Engineering and ApplicationsDocument7 pagesInternational Journal of Computer Engineering and ApplicationsrishithaNo ratings yet
- Efficiency and Security of Data With Symmetric Encryption AlgorithmsDocument4 pagesEfficiency and Security of Data With Symmetric Encryption Algorithmsexpert 60No ratings yet
- Modified Rsa Encryption Algorithm Using Four Keys IJERTCONV3IS07021Document5 pagesModified Rsa Encryption Algorithm Using Four Keys IJERTCONV3IS07021Jeff HambreNo ratings yet
- Block Chain-Enabled Distributed Security Framework For Next Generation Iot: An Edge-Cloud and Software Defined Network Integrated ApproachDocument8 pagesBlock Chain-Enabled Distributed Security Framework For Next Generation Iot: An Edge-Cloud and Software Defined Network Integrated ApproachSachin KNo ratings yet
- A Comprehensive Review of Cryptographic AlgorithmsDocument9 pagesA Comprehensive Review of Cryptographic AlgorithmsIJRASETPublicationsNo ratings yet
- Comparative Study of Symmetric Encryption Techniques For Mobile Data Caching in WMNDocument6 pagesComparative Study of Symmetric Encryption Techniques For Mobile Data Caching in WMNtheijesNo ratings yet
- Paper 41-A Survey On The Cryptographic Encryption AlgorithmsDocument12 pagesPaper 41-A Survey On The Cryptographic Encryption Algorithmsmcselles100% (1)
- Encrption: Keywords: Encryption, DES, Blowfish, RSA, AESDocument10 pagesEncrption: Keywords: Encryption, DES, Blowfish, RSA, AESabdul hadiNo ratings yet
- Basic Methods of CryptographyDocument12 pagesBasic Methods of Cryptographyedutakeo0% (1)
- RFID Authentication for IoT HealthcareDocument7 pagesRFID Authentication for IoT Healthcarerahul agarwalNo ratings yet
- Irjet V5i4919Document5 pagesIrjet V5i4919ghada sayedNo ratings yet
- IOSR JournalsDocument7 pagesIOSR JournalsInternational Organization of Scientific Research (IOSR)No ratings yet
- Tiny Encryption Algorithm For Rfid ApplicationsDocument2 pagesTiny Encryption Algorithm For Rfid ApplicationsAnkit DesaiNo ratings yet
- A Comparative Study of Symmetric Key Encryption Algorithms: Amit Jain, Divya BhatnagarDocument6 pagesA Comparative Study of Symmetric Key Encryption Algorithms: Amit Jain, Divya BhatnagarrebwarpcNo ratings yet
- Audio Encryption Optimization: Harsh Bijlani Dikshant Gupta Mayank LovanshiDocument5 pagesAudio Encryption Optimization: Harsh Bijlani Dikshant Gupta Mayank LovanshiAman Kumar TrivediNo ratings yet
- Comparative Study of Different Cryptographic Algorithms For Data Security in Cloud ComputingDocument7 pagesComparative Study of Different Cryptographic Algorithms For Data Security in Cloud ComputingPathan MehemudNo ratings yet
- An Integrated Encryption Scheme Used in Bluetooth Communication MechanismDocument4 pagesAn Integrated Encryption Scheme Used in Bluetooth Communication MechanismChaitanya KumarNo ratings yet
- CS707 FinalTerm Exam Paper Q ADocument9 pagesCS707 FinalTerm Exam Paper Q ASaeed SaeedNo ratings yet
- Burmester 2009Document27 pagesBurmester 2009alexanderfortis8628No ratings yet
- Ijaiem 2013 07 17 054Document3 pagesIjaiem 2013 07 17 054International Journal of Application or Innovation in Engineering & ManagementNo ratings yet
- Cybersecurity Essentials Chapter 4 Quiz Questions AnswersDocument5 pagesCybersecurity Essentials Chapter 4 Quiz Questions Answersheno ahNo ratings yet
- AES-128 Performance in Tinyos With CBC Algorithm (WSN) : Ankit Srivastava, Dr. N. Revathi VenkataramanDocument10 pagesAES-128 Performance in Tinyos With CBC Algorithm (WSN) : Ankit Srivastava, Dr. N. Revathi VenkataramanIJERDNo ratings yet
- Computer Crytography-Mit 5114-Take Away 2Document10 pagesComputer Crytography-Mit 5114-Take Away 2JoelNo ratings yet
- Data Encryption StandardDocument37 pagesData Encryption Standardchristian MacNo ratings yet
- 1 s2.0 S235291482100157X MainDocument7 pages1 s2.0 S235291482100157X Maindavid t. KleinNo ratings yet
- Security of Information Systems: Implementation of EncryptionDocument6 pagesSecurity of Information Systems: Implementation of EncryptionMohammed ErritaliNo ratings yet
- It 2352-CNSDocument21 pagesIt 2352-CNSlakshmigajendranNo ratings yet
- Comparison of Encryption Algorithms: AES, Blowfish and Twofish For Security of Wireless NetworksDocument5 pagesComparison of Encryption Algorithms: AES, Blowfish and Twofish For Security of Wireless NetworksPuji SetiadiNo ratings yet
- CyberDocument5 pagesCyberpranavNo ratings yet
- NSC Unit - 2 - 221218 - 100752Document25 pagesNSC Unit - 2 - 221218 - 100752SurenderNo ratings yet
- Designing of AES Algorithm Using VerilogDocument5 pagesDesigning of AES Algorithm Using VerilogAMIT VERMANo ratings yet
- Asko One GuyDocument7 pagesAsko One GuyHussaini ZubairuNo ratings yet
- Application of Classical Encryption Techniques For Securing Data - A Threaded ApproachDocument8 pagesApplication of Classical Encryption Techniques For Securing Data - A Threaded ApproachJames MorenoNo ratings yet
- No Network Is 100Document7 pagesNo Network Is 100AngelDayanaNo ratings yet
- Paper 2 - : February 2021Document22 pagesPaper 2 - : February 2021zubair nawazNo ratings yet
- Running Head: Lightweight CryptographyDocument8 pagesRunning Head: Lightweight CryptographyCarlos AlphonceNo ratings yet
- 9 Dr. Amit Sharma 1459672381 - 254VDocument6 pages9 Dr. Amit Sharma 1459672381 - 254VamittechnosoftNo ratings yet
- Chapter One 1.1 Background of StudyDocument24 pagesChapter One 1.1 Background of StudyPeter OsasNo ratings yet
- What is Cryptography? ExplainedDocument9 pagesWhat is Cryptography? ExplainedSagar DixitNo ratings yet
- CS8792 CNS Two Marks Questions With AnswersDocument15 pagesCS8792 CNS Two Marks Questions With Answerslavanyaraju4985No ratings yet
- Doc-1. RtosDocument212 pagesDoc-1. RtosbaluNo ratings yet
- Performance Analysis of Blowfish, Idea and AES Encryption AlgorithmsDocument8 pagesPerformance Analysis of Blowfish, Idea and AES Encryption AlgorithmsEddy ManurungNo ratings yet
- Paper 59-Cryptography A Comparative Analysis For Modern TechniquesDocument7 pagesPaper 59-Cryptography A Comparative Analysis For Modern Techniquesadi putraNo ratings yet
- CNS Imp (Overview)Document23 pagesCNS Imp (Overview)elitepredator1916No ratings yet
- Mens Hostel Counselling 2017Document8 pagesMens Hostel Counselling 2017SPAM rohitNo ratings yet
- CSE1002 Problem Solving With Object Oriented Programming LO 1 AC39Document7 pagesCSE1002 Problem Solving With Object Oriented Programming LO 1 AC39SPAM rohitNo ratings yet
- CSE1002 Problem Solving With Object Oriented Programming LO 1 AC39Document7 pagesCSE1002 Problem Solving With Object Oriented Programming LO 1 AC39SPAM rohitNo ratings yet
- Water quality experiment results Rohit Vemparala 16BCE0766Document3 pagesWater quality experiment results Rohit Vemparala 16BCE0766SPAM rohitNo ratings yet
- Digital Asst. 2Document1 pageDigital Asst. 2SPAM rohitNo ratings yet
- DA1Document10 pagesDA1SPAM rohit100% (3)
- Lesson Plan On ForcesDocument3 pagesLesson Plan On Forcesapi-226755313No ratings yet
- Ref 9 PDFDocument10 pagesRef 9 PDFAli H. NumanNo ratings yet
- Anel Peralta Participation Activity 2Document7 pagesAnel Peralta Participation Activity 2Indira AlfonsoNo ratings yet
- Naive Bayes Classifier: Coin Toss and Fair Dice ExampleDocument16 pagesNaive Bayes Classifier: Coin Toss and Fair Dice ExampleRupali PatilNo ratings yet
- MIT Introduction To Deep Learning (6.S191) : Course InformationDocument6 pagesMIT Introduction To Deep Learning (6.S191) : Course InformationGokul SoundararajanNo ratings yet
- 03rec3 ExerciseDocument2 pages03rec3 Exercisejunaid1626No ratings yet
- Big Rip EssayDocument2 pagesBig Rip EssayBo BobNo ratings yet
- 01-Basics of AntennasDocument40 pages01-Basics of Antennaskomar33No ratings yet
- Three Point Flexural TestDocument3 pagesThree Point Flexural Testjerfmos100% (1)
- Grade 7 Math Practice Test 2013 2014Document44 pagesGrade 7 Math Practice Test 2013 2014Natalie MuslehNo ratings yet
- Christoph Reinhart: L12 Thermal Mass and Heat FlowDocument64 pagesChristoph Reinhart: L12 Thermal Mass and Heat FlowT N Roland BourgeNo ratings yet
- GuardSoft Cerberus Full Software Cracked Download (Pc-Mac) CrackDocument2 pagesGuardSoft Cerberus Full Software Cracked Download (Pc-Mac) CrackMegatoreNo ratings yet
- Presentation McqsDocument2 pagesPresentation McqsEngr Mujahid Iqbal100% (1)
- Mohr's Theorem and Corollaries PDFDocument8 pagesMohr's Theorem and Corollaries PDFEvaNo ratings yet
- Equated Yield RateDocument15 pagesEquated Yield RateAndr Ei100% (1)
- Chapter 2Document19 pagesChapter 2TearlëşşSufíåñNo ratings yet
- H2 MYE Revision Package Integration SolutionsDocument9 pagesH2 MYE Revision Package Integration SolutionsTimothy HandokoNo ratings yet
- V Foreword VI Preface VII Authors' Profiles VIII Convention Ix Abbreviations X List of Tables Xi List of Figures Xii 1 1Document152 pagesV Foreword VI Preface VII Authors' Profiles VIII Convention Ix Abbreviations X List of Tables Xi List of Figures Xii 1 1July Rodriguez100% (3)
- Systems of Inequalities Study GuideDocument2 pagesSystems of Inequalities Study Guideapi-470562131No ratings yet
- 50 Mathematical Puzzles and OdditiesDocument88 pages50 Mathematical Puzzles and OdditiesmatijahajekNo ratings yet
- ResponDocument4 pagesResponFelix PalanganNo ratings yet
- Philosophy of Mind - Mental States and Brain States (Leibniz and Kripke)Document6 pagesPhilosophy of Mind - Mental States and Brain States (Leibniz and Kripke)Victoria RoncoNo ratings yet
- PMT Paper Reference(sDocument3 pagesPMT Paper Reference(sSHEHAN NITESHNo ratings yet
- 1st Periodical TestDocument1 page1st Periodical TestbjnatsNo ratings yet
- Week 1 DLL - General MathematicsDocument5 pagesWeek 1 DLL - General Mathematicsanon_838476361No ratings yet
- Prog 3112 Week 11-19Document18 pagesProg 3112 Week 11-19Tanga KaNo ratings yet
- Physics Gutka - Allen's 2021 Side BookDocument192 pagesPhysics Gutka - Allen's 2021 Side BookDhyey PatelNo ratings yet
- Machine Learning With CaeDocument6 pagesMachine Learning With CaeHarsha KorlapatiNo ratings yet
- Reliability & Maintainability Exam Solutions 2012Document14 pagesReliability & Maintainability Exam Solutions 2012luchogilmourNo ratings yet
- Systems of Inequalities Solved(MathDocument25 pagesSystems of Inequalities Solved(MathEd VillNo ratings yet
- Python for Beginners: The 1 Day Crash Course For Python Programming In The Real WorldFrom EverandPython for Beginners: The 1 Day Crash Course For Python Programming In The Real WorldNo ratings yet
- So You Want to Start a Podcast: Finding Your Voice, Telling Your Story, and Building a Community that Will ListenFrom EverandSo You Want to Start a Podcast: Finding Your Voice, Telling Your Story, and Building a Community that Will ListenRating: 4.5 out of 5 stars4.5/5 (35)
- Defensive Cyber Mastery: Expert Strategies for Unbeatable Personal and Business SecurityFrom EverandDefensive Cyber Mastery: Expert Strategies for Unbeatable Personal and Business SecurityRating: 5 out of 5 stars5/5 (1)
- How to Be Fine: What We Learned by Living by the Rules of 50 Self-Help BooksFrom EverandHow to Be Fine: What We Learned by Living by the Rules of 50 Self-Help BooksRating: 4.5 out of 5 stars4.5/5 (48)
- How to Do Nothing: Resisting the Attention EconomyFrom EverandHow to Do Nothing: Resisting the Attention EconomyRating: 4 out of 5 stars4/5 (421)
- Nine Algorithms That Changed the Future: The Ingenious Ideas That Drive Today's ComputersFrom EverandNine Algorithms That Changed the Future: The Ingenious Ideas That Drive Today's ComputersRating: 5 out of 5 stars5/5 (7)
- The Digital Marketing Handbook: A Step-By-Step Guide to Creating Websites That SellFrom EverandThe Digital Marketing Handbook: A Step-By-Step Guide to Creating Websites That SellRating: 5 out of 5 stars5/5 (6)
- The Wires of War: Technology and the Global Struggle for PowerFrom EverandThe Wires of War: Technology and the Global Struggle for PowerRating: 4 out of 5 stars4/5 (34)
- Content Rules: How to Create Killer Blogs, Podcasts, Videos, Ebooks, Webinars (and More) That Engage Customers and Ignite Your BusinessFrom EverandContent Rules: How to Create Killer Blogs, Podcasts, Videos, Ebooks, Webinars (and More) That Engage Customers and Ignite Your BusinessRating: 4.5 out of 5 stars4.5/5 (42)
- Ultimate Guide to YouTube for BusinessFrom EverandUltimate Guide to YouTube for BusinessRating: 5 out of 5 stars5/5 (1)
- Ultimate Guide to LinkedIn for Business: Access more than 500 million people in 10 minutesFrom EverandUltimate Guide to LinkedIn for Business: Access more than 500 million people in 10 minutesRating: 5 out of 5 stars5/5 (5)
- The $1,000,000 Web Designer Guide: A Practical Guide for Wealth and Freedom as an Online FreelancerFrom EverandThe $1,000,000 Web Designer Guide: A Practical Guide for Wealth and Freedom as an Online FreelancerRating: 4.5 out of 5 stars4.5/5 (22)
- Monitored: Business and Surveillance in a Time of Big DataFrom EverandMonitored: Business and Surveillance in a Time of Big DataRating: 4 out of 5 stars4/5 (1)
- Facing Cyber Threats Head On: Protecting Yourself and Your BusinessFrom EverandFacing Cyber Threats Head On: Protecting Yourself and Your BusinessRating: 4.5 out of 5 stars4.5/5 (27)
- A Great Online Dating Profile: 30 Tips to Get Noticed and Get More ResponsesFrom EverandA Great Online Dating Profile: 30 Tips to Get Noticed and Get More ResponsesRating: 3.5 out of 5 stars3.5/5 (2)
- SEO: The Ultimate Guide to Optimize Your Website. Learn Effective Techniques to Reach the First Page and Finally Improve Your Organic Traffic.From EverandSEO: The Ultimate Guide to Optimize Your Website. Learn Effective Techniques to Reach the First Page and Finally Improve Your Organic Traffic.Rating: 5 out of 5 stars5/5 (5)
- SEO 2021: Learn search engine optimization with smart internet marketing strategiesFrom EverandSEO 2021: Learn search engine optimization with smart internet marketing strategiesRating: 5 out of 5 stars5/5 (6)
- Coding for Beginners and Kids Using Python: Python Basics for Beginners, High School Students and Teens Using Project Based LearningFrom EverandCoding for Beginners and Kids Using Python: Python Basics for Beginners, High School Students and Teens Using Project Based LearningRating: 3 out of 5 stars3/5 (1)
- The Ultimate LinkedIn Sales Guide: How to Use Digital and Social Selling to Turn LinkedIn into a Lead, Sales and Revenue Generating MachineFrom EverandThe Ultimate LinkedIn Sales Guide: How to Use Digital and Social Selling to Turn LinkedIn into a Lead, Sales and Revenue Generating MachineNo ratings yet
- Get Into UX: A foolproof guide to getting your first user experience jobFrom EverandGet Into UX: A foolproof guide to getting your first user experience jobRating: 4.5 out of 5 stars4.5/5 (5)