Professional Documents
Culture Documents
Depicted at The Centre of This Map.: Course, in All Domains of Learning in Terms
Uploaded by
ashaOriginal Title
Copyright
Available Formats
Share this document
Did you find this document useful?
Is this content inappropriate?
Report this DocumentCopyright:
Available Formats
Depicted at The Centre of This Map.: Course, in All Domains of Learning in Terms
Uploaded by
ashaCopyright:
Available Formats
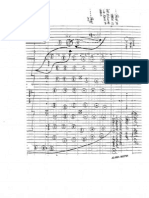
Network and Information Security Course Code: 22620
course, in all domains of learning in terms of the industry/employer identified competency
depicted at the centre of this map.
Topic 5.3 Email”
Security
14,16-Trace the origin
of Email using any tool
feo FmuilTrarerPmy at
PrO 12- Install
Firewall on any
i ? *s,| oneratine svstem
a < \
t
ji a
' a Bees *y
\ ‘
\ a
\
!‘
'
:t
‘
i‘
i
\
‘ ‘
. \
‘
f ‘ ‘ \ ‘ ‘
!
5 ! ;t _ Compet
& ency ‘1 . ’' 1'
1 Maintain Computer and y 1 '
t \ : Network Securityofan : ! t
1 1 oreanizatian
‘ ‘ \ t 1 1
i; ’ , r 1
# ' A
‘ » S _ : !
\ » +" pO 5: Write
HH \ program to ;
\\ \. 4 implement Caesar a
’
\ ‘
Cioher ‘.
PrO 1- Install &
we" “5 Pro 4: Apply security
- to file
Sonefigure antivirus
{folder or application using «,,Softvare.on system): 4
access permissions and verify ” LsTypes
of Attacks
>
Topic 3.5 Symmetric Topic 2.1
and Asymmetric Identification and
" Cryptography » Authentication | 441”
PrO through Practical yo ‘Topic
Figure 1 - Course Map
The practicals in this section are PrOs (i.e. sub-components of the COs) to be developed and
assessed in the student for the attainment of the competency.
., Approx.
: Practical Outcomes (PrOs) Unit Hrs.
No. No. -
Required
a. Install and configure Antivirus software on system (any).
1 I 2
b. Set s U
2 Perform B and Restore of the s I 2
3 Setu — asswords to and cations II 2
4 Apply security to file folder or application using access U 2
ssions and
5 Write a to Caesar Ci ll 2
6 Write a toim ement Vernam Ci III 2
7 Create and Hash Code for messa Il
8 Write a to ement Rail fence techni ue
9 Write a program to implement Simple Columnar Transposition
technique
MSBTE — Final Copy Dt. 24.09.2019 Page 2 of8
You might also like
- Donald Walker - Walker's Manly ExercisesDocument409 pagesDonald Walker - Walker's Manly ExercisesMadalinaNo ratings yet
- Discovery Free SampleDocument136 pagesDiscovery Free Samplefelipe pretelNo ratings yet
- LP Die Zauberflote The Magic Flute Wolfgang Amadeus Mozart Hilde Guden WilDocument30 pagesLP Die Zauberflote The Magic Flute Wolfgang Amadeus Mozart Hilde Guden WilSebastián Rodríguez GonzálezNo ratings yet
- 2018 Ibc Seaoc SSDM Vol4Document335 pages2018 Ibc Seaoc SSDM Vol4Albert Farag100% (2)
- l'1IJ'j' - : 4 PK Variety Onesies-Girl Ref#OP213727EKDocument20 pagesl'1IJ'j' - : 4 PK Variety Onesies-Girl Ref#OP213727EKMartha LandazuryNo ratings yet
- ME145 - Conventional Symbol-Exp 4 - Part 1Document4 pagesME145 - Conventional Symbol-Exp 4 - Part 1neha1685No ratings yet
- 002 Discharge ValveDocument2 pages002 Discharge Valvehanco17858No ratings yet
- D&D Subreddit - Monster A Day CompendiumDocument232 pagesD&D Subreddit - Monster A Day CompendiumAnonymous Rk95Bj95% (21)
- Glenn JDocument1 pageGlenn Japi-528969291No ratings yet
- 3603 M342-51571 - REV5 - Sheet - 0007Document1 page3603 M342-51571 - REV5 - Sheet - 0007Batsha PonnusamyNo ratings yet
- Fema P-1078 PDFDocument1 pageFema P-1078 PDFeerrddeemmNo ratings yet
- Fema P-1078Document1 pageFema P-1078Ronny FortaNo ratings yet
- Central Intelligence Bull (15772430)Document18 pagesCentral Intelligence Bull (15772430)Oh my pluto Oh my plutoNo ratings yet
- Light Wave Interference - 0001Document6 pagesLight Wave Interference - 0001Damaris KaminzaNo ratings yet
- #5 The Discovery Approach To MathematicsDocument45 pages#5 The Discovery Approach To Mathematicsrichard dean rubricaNo ratings yet
- Ahiman Rezon 1778Document319 pagesAhiman Rezon 1778Leonardo BorgesNo ratings yet
- Simulasi 5 JwabanDocument3 pagesSimulasi 5 JwabanD KaNo ratings yet
- Take Home Mod 8 Coal SeamDocument1 pageTake Home Mod 8 Coal SeamChristian BudimanNo ratings yet
- How to optimize images for the webDocument1 pageHow to optimize images for the webanthony acuñaNo ratings yet
- ETI 1978-10 OctoberDocument132 pagesETI 1978-10 OctoberCarlos SoaresNo ratings yet
- Yves Saint Laurent - Forty Years of Creation - Saint Laurent, Yves International Festival of FashionDocument212 pagesYves Saint Laurent - Forty Years of Creation - Saint Laurent, Yves International Festival of Fashiondanabooks3No ratings yet
- Ebook PDF Understanding Learning and Learners Custom Edition 2e PDFDocument41 pagesEbook PDF Understanding Learning and Learners Custom Edition 2e PDFferne.bass217100% (32)
- 576d8v49yuy41 JPGDocument1 page576d8v49yuy41 JPGliliplayz123No ratings yet
- Spirituall Directory Fenner PDFDocument119 pagesSpirituall Directory Fenner PDFDavid MartinezNo ratings yet
- The Illustrated Encyclopedia of Woodworking Handtools - Graham Blackburn - Anna's ArchiveDocument244 pagesThe Illustrated Encyclopedia of Woodworking Handtools - Graham Blackburn - Anna's ArchiveTheo RenckNo ratings yet
- Indian Philosophy PDFDocument6 pagesIndian Philosophy PDFRock KrishnaNo ratings yet
- Anima PoetaeDocument298 pagesAnima PoetaeM GNo ratings yet
- Prelude BWV 1008, Transcription by Roger Allen CopeDocument2 pagesPrelude BWV 1008, Transcription by Roger Allen CopeRoger Allen CopeNo ratings yet
- 1985-12-01 Zimbabwe Foundation For Education With Production ZIMFEP - A Follow-Up Study - Education Division Documents No 29Document102 pages1985-12-01 Zimbabwe Foundation For Education With Production ZIMFEP - A Follow-Up Study - Education Division Documents No 29Vimbai ChinoonekaNo ratings yet
- ScarlettDocument42 pagesScarlettDeboraNo ratings yet
- Er Final WorksheetDocument4 pagesEr Final WorksheetdujalshahNo ratings yet
- Khách S N Tư NhânDocument13 pagesKhách S N Tư Nhânđạt nguyễnNo ratings yet
- Rerum Hungaricarum Sui Temporis CommentaDocument809 pagesRerum Hungaricarum Sui Temporis Commentamerlu123No ratings yet
- Lessons in Elocution, Or, A Selection of Pieces in Prose and Verse 1831Document357 pagesLessons in Elocution, Or, A Selection of Pieces in Prose and Verse 1831Thigpen FockspaceNo ratings yet
- Gupt GyanDocument22 pagesGupt GyansunnyNo ratings yet
- Trecho Chester GabrielDocument10 pagesTrecho Chester GabrielGabriel AndionNo ratings yet
- Math Kelas Viii Untitled Notebook 21Document3 pagesMath Kelas Viii Untitled Notebook 21xaveriusgaoNo ratings yet
- AC Circuits - 4Document25 pagesAC Circuits - 4Shivam AggarwalNo ratings yet
- ML20101Q417Document65 pagesML20101Q417muhamad.elhosiny21No ratings yet
- A F R) Eeb) (TR) (O O86957Document3 pagesA F R) Eeb) (TR) (O O86957Jared OcampoNo ratings yet
- The Immortality of The Soul PDFDocument635 pagesThe Immortality of The Soul PDFCarlos100% (1)
- 9 - Bhattiacademy - Com - Chemistry - 5. Scholar Series (Obj)Document13 pages9 - Bhattiacademy - Com - Chemistry - 5. Scholar Series (Obj)Amir FarooqNo ratings yet
- Credit Book Aquino 2021Document525 pagesCredit Book Aquino 2021Sealtiel VillarealNo ratings yet
- Air Force Operation Stats (1944)Document70 pagesAir Force Operation Stats (1944)CAP History Library100% (2)
- Ency-education SEO-optimized document titleDocument2 pagesEncy-education SEO-optimized document titleGhiles OularbieNo ratings yet
- Movable Pattern 2: The MCfior TriadDocument1 pageMovable Pattern 2: The MCfior TriadAsun GombrekNo ratings yet
- Columbine Report Pgs 3701-3800Document100 pagesColumbine Report Pgs 3701-3800columbinefamilyrequestNo ratings yet
- Toyota Rav 4 1CDFTV 2005 Esquema Sensor Angulo de GiroDocument3 pagesToyota Rav 4 1CDFTV 2005 Esquema Sensor Angulo de GiroMarcos CubaNo ratings yet
- Drawing Mechanical SLM-167Document1 pageDrawing Mechanical SLM-167acexventuraNo ratings yet
- .... ::P S::JVT::L F - I.. L - ,-R-I - 1::::P::: : :J : .... :J:) - # t.LI LL-I+-2 - F+ - ( - L..:: - ::1-:i: - 1-. .-2 - IDocument1 page.... ::P S::JVT::L F - I.. L - ,-R-I - 1::::P::: : :J : .... :J:) - # t.LI LL-I+-2 - F+ - ( - L..:: - ::1-:i: - 1-. .-2 - IMohammed H SaeedNo ratings yet
- Effective CommunicationDocument4 pagesEffective Communicationroyakky262No ratings yet
- Supersonic,': (Turbulencei, in .. /), GAMMA-,R'AY .'.Document39 pagesSupersonic,': (Turbulencei, in .. /), GAMMA-,R'AY .'.janiklp1337No ratings yet
- TrumanlakeDocument1 pageTrumanlakeDaniel ThompsonNo ratings yet
- Green Ridge Lay Out ContactsDocument1 pageGreen Ridge Lay Out Contactsnithishkonda12345No ratings yet
- Linearment Map of NigeriaDocument1 pageLinearment Map of NigeriaAbiola BolarewajuNo ratings yet
- Join the Upsc Group online or via hard copyDocument99 pagesJoin the Upsc Group online or via hard copyPrashant KushwahaNo ratings yet
- Wireless World 1990 11Document100 pagesWireless World 1990 11Milton NastNo ratings yet
- Situation in Libya As of (15708344)Document2 pagesSituation in Libya As of (15708344)Mario Alberto Pineda CastilloNo ratings yet
- PT Coca Cola DD 10 Juli 2023Document5 pagesPT Coca Cola DD 10 Juli 2023evi zodriyahNo ratings yet
- Cryptography and Network SecurityDocument23 pagesCryptography and Network SecurityVivek VermaNo ratings yet
- A Review of Authentication MethodsDocument4 pagesA Review of Authentication MethodsashaNo ratings yet
- Electronic Mail Security: Henric Johnson Blekinge Institute of Technology, Sweden Henric - Johnson@bth - SeDocument26 pagesElectronic Mail Security: Henric Johnson Blekinge Institute of Technology, Sweden Henric - Johnson@bth - SeRishika ChowdaryNo ratings yet
- Public Key InfrastructureDocument52 pagesPublic Key Infrastructureapi-27431931No ratings yet
- Marathwada Mitra Mandal's Polytechnic Question BankDocument2 pagesMarathwada Mitra Mandal's Polytechnic Question Bankshruti gaware100% (1)
- Nis MCQ QB1Document34 pagesNis MCQ QB1Rakesh Mahajan100% (1)
- Cyber Crimes and Legal ImplicationsDocument3 pagesCyber Crimes and Legal ImplicationsashaNo ratings yet
- Information SecurityDocument21 pagesInformation SecurityashaNo ratings yet
- Public Key InfrastructureDocument52 pagesPublic Key Infrastructureapi-27431931No ratings yet
- 3 Computer Security (CSE 17514) Model Answer Practice TestDocument34 pages3 Computer Security (CSE 17514) Model Answer Practice TestashaNo ratings yet
- MD5Document13 pagesMD5bethlehem100% (1)
- Introduction To Public Key Infrastructure: Theo Gravity Viv LabsDocument35 pagesIntroduction To Public Key Infrastructure: Theo Gravity Viv LabsashaNo ratings yet
- 4.1 Firewall 4.2 Virtual Private Network (VPN) Kerberos Security Topology and DMZDocument94 pages4.1 Firewall 4.2 Virtual Private Network (VPN) Kerberos Security Topology and DMZashaNo ratings yet
- 1st Sem AllDocument53 pages1st Sem AllkirankumarNo ratings yet
- E Valuing Level' in 1° Year: ., Approx. - . Practical Outcomes (Pros) Unit HRSDocument1 pageE Valuing Level' in 1° Year: ., Approx. - . Practical Outcomes (Pros) Unit HRSashaNo ratings yet
- Information SecurityDocument16 pagesInformation SecurityashaNo ratings yet
- Course Outcomes (Cos) : Program Name: Computer Engineering Program Group Semester: SixthDocument1 pageCourse Outcomes (Cos) : Program Name: Computer Engineering Program Group Semester: SixthashaNo ratings yet
- Information and Network SecurityDocument10 pagesInformation and Network SecurityashaNo ratings yet
- Chapter 3. CryptographyDocument70 pagesChapter 3. CryptographyashaNo ratings yet
- Basic Electronics Subject Code 22225 NotesDocument6 pagesBasic Electronics Subject Code 22225 NotesashaNo ratings yet
- 2 Computer Security (CSE 17514) Model Answer Practice TestDocument33 pages2 Computer Security (CSE 17514) Model Answer Practice TestashaNo ratings yet
- Identification, Authentication and Operational SecurityDocument34 pagesIdentification, Authentication and Operational SecurityashaNo ratings yet
- 1 Computer Security (CSE 17514) Model Answer Practice TestDocument30 pages1 Computer Security (CSE 17514) Model Answer Practice TestashaNo ratings yet
- Unit - II User Authentication & Access ControlDocument11 pagesUnit - II User Authentication & Access ControlJayesh DeshmukhNo ratings yet
- K. K. Wagh Polytechnic, Nasik-3: Chapter 1: Introduction To Information SecurityDocument6 pagesK. K. Wagh Polytechnic, Nasik-3: Chapter 1: Introduction To Information SecurityashaNo ratings yet
- Unit - IDocument15 pagesUnit - IashaNo ratings yet
- Intruders: Detect Possible IntrusionsDocument11 pagesIntruders: Detect Possible IntrusionsashaNo ratings yet
- Chapter 1Document33 pagesChapter 1ashaNo ratings yet
- Intruders: Detect Possible IntrusionsDocument11 pagesIntruders: Detect Possible IntrusionsashaNo ratings yet
- Financial Shenanigans 3rd EditionDocument6 pagesFinancial Shenanigans 3rd Editionpwsicher100% (1)
- Pigovian Welfare Economics 3Document4 pagesPigovian Welfare Economics 3vikram inamdar100% (1)
- Summary National Policy Strategy For Infrastructure and Spatial PlanningDocument24 pagesSummary National Policy Strategy For Infrastructure and Spatial Planningandre turnerNo ratings yet
- Darwin Route10 Pocket Maps/TimetableDocument2 pagesDarwin Route10 Pocket Maps/TimetableLachlanNo ratings yet
- Incident Management & Service Level Agreement: An Optimistic ApproachDocument6 pagesIncident Management & Service Level Agreement: An Optimistic ApproachServiceNow UsersNo ratings yet
- American Political Parties: Republicans vs. DemocratsDocument60 pagesAmerican Political Parties: Republicans vs. DemocratsSchmetterling TraurigNo ratings yet
- Sap Erp Integration of Business ProcessesDocument4 pagesSap Erp Integration of Business ProcessesShaik Shoeb AbdullahNo ratings yet
- Enhancing Role of SMEs in Indian Defence Industry1 PDFDocument84 pagesEnhancing Role of SMEs in Indian Defence Industry1 PDFINDIRA PALNINo ratings yet
- Lightcyber Behavioral AnalyticsDocument4 pagesLightcyber Behavioral AnalyticsasadaNo ratings yet
- Basic Microeconomics Semi Final Exam ReviewDocument3 pagesBasic Microeconomics Semi Final Exam ReviewEnergy Trading QUEZELCO 1No ratings yet
- Name: Yeison Adrián Vargas Suaza Grade: 11°A: Realización de Ejercicios PropuestosDocument4 pagesName: Yeison Adrián Vargas Suaza Grade: 11°A: Realización de Ejercicios Propuestosyeison adrian vargasNo ratings yet
- Microeconomics 20th Edition Mcconnell Test BankDocument25 pagesMicroeconomics 20th Edition Mcconnell Test BankMeganAguilarkpjrz100% (56)
- Paystub 2019 05 31 PDFDocument1 pagePaystub 2019 05 31 PDFAnonymous wkIlICXmQfNo ratings yet
- Ch1. Considering Materiality and RiskDocument47 pagesCh1. Considering Materiality and RiskAli AlbaqshiNo ratings yet
- SociologyDocument3 pagesSociologyMuxammil ArshNo ratings yet
- 2009-05-28Document40 pages2009-05-28Southern Maryland OnlineNo ratings yet
- 516 Application CarDocument2 pages516 Application Carazamkhan13No ratings yet
- Encashment of Bank Guarantee 2017-08-11Document4 pagesEncashment of Bank Guarantee 2017-08-11mc160403810 Usman AliNo ratings yet
- Three Generations Potters of San Juan de Oriente, Nicaragua - HTMLDocument2 pagesThree Generations Potters of San Juan de Oriente, Nicaragua - HTMLElefante Magico100% (1)
- Ed. Remington, Patrick L. - Chronic Disease Epidemiology, Prevention, and Control-American Public Health Association (2016)Document1,168 pagesEd. Remington, Patrick L. - Chronic Disease Epidemiology, Prevention, and Control-American Public Health Association (2016)Sebastián Ramírez RoldánNo ratings yet
- Letter Sa Mga Panel Inag FinalsDocument7 pagesLetter Sa Mga Panel Inag FinalsCHENNY BETAIZARNo ratings yet
- Italian Renaissance Theatre DevelopmentsDocument3 pagesItalian Renaissance Theatre DevelopmentsAndrewNathanVesselNo ratings yet
- Desperate HousewivesDocument15 pagesDesperate HousewivesIvanka ShtyfanenkoNo ratings yet
- Office Furniture Catalogue EnquiryDocument12 pagesOffice Furniture Catalogue EnquiryAdela MărgineanuNo ratings yet
- COMOROS 01 SynopsisDocument99 pagesCOMOROS 01 SynopsisJaswinder SohalNo ratings yet
- Submitted To: Jalal Ahmad Khan Name: Osama Yaqoob ID# 63125 Assignment# 3 Course: Managerial AccoutingDocument6 pagesSubmitted To: Jalal Ahmad Khan Name: Osama Yaqoob ID# 63125 Assignment# 3 Course: Managerial AccoutingOsama YaqoobNo ratings yet
- G.R. No. 148991 January 21, 2004 People of The Philippines, Appellee, Leonardo Nuguid Y Mayao, AppellantDocument21 pagesG.R. No. 148991 January 21, 2004 People of The Philippines, Appellee, Leonardo Nuguid Y Mayao, Appellantida_chua8023No ratings yet
- Airline Alliances Game TheoryDocument4 pagesAirline Alliances Game TheoryJ CNo ratings yet
- TWDocument16 pagesTWDrago DragicNo ratings yet
- PaperDocument4 pagesPaperAnne ChenNo ratings yet