Professional Documents
Culture Documents
Fidonet: Technology, Tools, and History: Topology
Uploaded by
Sebas EscalanteOriginal Title
Copyright
Available Formats
Share this document
Did you find this document useful?
Is this content inappropriate?
Report this DocumentCopyright:
Available Formats
Fidonet: Technology, Tools, and History: Topology
Uploaded by
Sebas EscalanteCopyright:
Available Formats
FIDONET: TECHNOLOGY,
TOOLS, AND HISTORY
sparse); and node is the particular Within a local network (e.g., city),
host within the local network. T h e nodes usually exchange email di-
addressing scheme may be e x t e n d e d rectly with one another. In those cit-
to accommodate points which are ies where p h o n e tariff zones divide
power users who reduce their con- the city, local hubs are used to con-
he public FidoNet consists o f nect time by using private (i.e., un- centrate intracity traffic to reduce
T
over 20,000 nodes which listed) nodes to exchange email and costs.
move email and enews over enews with public nodes. Thus, the Each local network has one node
the public telephone net- e x t e n d e d addressing scheme is with an alias o f node 0 (i.e., zone:neff
work using a unique proto- zone:net/node, point. 0) which is known as the inbound host.
col and data format. As the T h e FidoNet nodelist, a list o f all By default, all mail from outside the
initial implementations were written nodes in the public FidoNet network, local net is delivered to the i n b o u n d
for MS-DOS, DOS-based hosts are is automatically u p d a t e d and distrib- host to be distributed within the local
still the vast majority o f the network. uted weekly. This list contains the network. Thus, a node in New York
But semiformal specifications for the actual data telephone n u m b e r o f may deliver all mail to San Francisco
data formats and protocols have fa- each host, as well as the geographic with a single telephone call, as op-
cilitated implementations for Unix, location and name o f the system op- posed to a call for every SF node for
Apples from t h e / / t o the Macintosh, erator (sysop). Every city's local net- which it has mail. While each node is
CP/M, MVS, the T a n d y CoCo, and work maintains its local data and responsible for sending its own mail
many other platforms. sends those data to a regional coordi- (as FidoNet is financed by users),
As FidoNet is almost entirely fi- nator who, in turn, sends the region's some local networks cooperate suffi-
nanced by private individuals, mini- aggregated data to a continental co- ciently to provide an outbound host to
mization o f m o d e m / t e l e p h o n e time ordinator. T h e continental coordina- concentrate all mail destined for out-
has been the principal driving force tors exchange their data, and create a side the city.
behind any design o f the data trans- list o f differences between the cur- Each o f the present six zones (con-
fer protocols. T h e original imple- rent week's data and that o f the pre- tinents) has a unique host which pro-
mentations used an inefficient vious week. This nodediff is then dis- vides interzone email routing. These
x m o d e m - b a s e d transport, a nonwin- tributed back down the hierarchy all zonegates have alias addresses o f the
dowed A C K / N A K protocol with 128- the way to each individual node in form orig-zone:orig-zone/dest-zone. For
byte packets. Although rarely used in the network. example, the gate from North Amer-
practice today, this protocol remains As all m o d e m p h o n e numbers are ica (zone 1) to Oceania (zone 3) has
codified as the minimal basic stan- published in the nodelist, point-to- an addressing alias o f the form 1 : 1/3.
d a r d implementation, since it is triv- point transfers are always possible. Hence, a node in North America
ial to code. Almost all current imple- But, as store-and-forward capabili- may save the cost o f an interconti-
mentations offer an optional suite o f ties are specified in the basic stan- nental call to Australia by sending
quite efficient zmodem-based dards, email tends to be routed the message to 1:1/3, which will in
streaming transport protocols which t h r o u g h a worldwide hierarchic to- turn send it to 3:3/1, which will see
are ACK-less, only N A K i n g in case o f pology and enews via a worldwide ad that it is delivered within Australia.
error. It is interesting to contrast this hoc, but generally geographically hi- Since November 1991, an experi-
push for efficiency with uucp's prof- erarchic, acyclic graph. mental system has been using the
ligate G protocol and the Internet's Internet to transport mail and enews
SMTP and N N T P protocols. TOpology between E u r o p e and N o r t h America.
Addressing within FidoNet is Power users r u n points that may con- T h e data are moved directly between
numeric with a bit o f punctuation nect to only their respective host the zonegates via IP (i.e., not gated
and specifies a particular node in the nodes to receive and deliver their between data formats) courtesy o f
administrative hierarchy. Addresses email a n d enews. As they are not in RIPE and EUnet. This saves FidoNet
are o f the form zone:net~node where the public nodelist, points are not operators thousands o f dollars a
zone is one o f the six continents considered to be official nodes in the month. Since late in 1992, this tun-
(North America, Europe, Oceania, network and thus are not subject to neling o f the I n t e r n e t has been ex-
Asia, or Africa); net is the city (or constraints o f technology, national t e n d e d to Taiwan, Southern Africa,
larger area if the node density is mail hour, and so forth. Chile, and other areas. This is done
COMHUiIICATIOH|OFTHIIACM August 1993/Vo1.36, No.8 3S
th the explicit consent o f the IP local basis in many cities as FidoNet tion and possibly a small fee to com-
carriers involved, to whom FidoNet echomail. pletely open facilities allowing full
owes a considerable debt o f grati- Internetwork gateways have been use for the first-time caller.
tude. used extensively by nongovernmen- Although no formal measure-
tal organizations (NGOs) in Africa, as ments have been made, it has been
Gateways to the Other well as by an ingenious transport be- estimated that the average FidoNet
Networks tween the South African academic IP BBS has over 200 active users; half
T h e r e are gateways between FidoNet network (UNINET-ZA) and the use enews, and 5% use private email.
and the uucp network, and thereby Internet [4]. As not all FidoNet nodes have BBS
the Internet. FidoNet is addressable access, we can estimate that on the
from the Internet DNS universe via Users o r d e r of 2 million FidoNet users read
the DNS ~,one fidonet.org. A FidoNet FidoNet has currently over 20,000 or write enews, and approximately
node, for .example, 1:105/42, has the distinct nodes worldwide. Although 200,000 o f these use private email.
d o m a i n name f6.nlO5.zlfidonet.org. FidoNet started in North America,
Gating is done almost exclusively via by 1985 there were systems in Eu- History
the u u c p network. T h e IvlX forward- rope, very soon followed by systems In 1984, T o m Jennings wished to
ers for thefidonet.org zone are set up on the other continents. Currently, move messages from his MS-DOS-
so that there is default forwarding about 59% o f the publicly listed based Fido 1 BBS to that o f a friend,
for all FidoNet hosts should there be nodes are in N o r t h America, 30% in J o h n Madill. As J e n n i n g s was the
no gateway which is local to the tar- Europe, 4% in Australia and New a u t h o r of the Fido BBS, he was able
get host. Zealand (Oceania), and 7% in Asia, to quickly modify it to extract mes-
T h e correct RFC822 address for Latin America, and Africa. sages from a specially designated
a F i d o N e t power user at point FidoNet technology is also used local message base and queue them
zo:ne/no.po is user@PpoFno.Nne.Zzo. privately within large corporations, for sending to the r e m o t e BBS. As
FIDONET.ORG, for example, public institutions, and NGOs. While telephone rates are much lower in
the scale o f the private use o f the middle o f the night, he wrote a
randy.bush@pO.f42.n105 zl .fidonet.org
FidoNet is not known, it is estimated separate external p r o g r a m to r u n
And, as points are optional in to be at least as large as the public this email transfer for one desig-
FidoNet, J a n e User at the BBS user at network. It is known to be used in nated h o u r to exchange mail with the
node zone:net~node is user@Fnode. companies such as AT&T, Georgia other node.
Nnet.Zzone.FIDONET.Ot'G, for ex- Pacific, and the Canadian Post Of- This soon grew to m o r e nodes,
ample, rice, a m o n g others. It is heavily used reaching 200 by early 1985. T h e
by NGOs in Africa. nodelist, a list o f all known active
lisa.gronke@f6.n105.zl ~donet.org
While hobbyists and public BBSs nodes, was d e v e l o p e d as a distributed
T h e U F G A T E package, which allows p r e d o m i n a t e the N o r t h American external file a n d was initially main-
an MS-DOS-based FidoNet node to FidoNet, p e r h a p s half o f the public tained by Jennings. T h e reserved
simulate a uucp host, gates both systems in E u r o p e are subsidized by mail transfer h o u r became enshrined
email and enews. This package m a d e small to medium-scale businesses. In as zone mail hour a n d is preserved
gating fairly p o p u l a r by 1987. More Africa, there is very serious use by today despite c u r r e n t technology
recently, other DOS packages have NGOs a n d poorly f u n d e d academic being capable o f intermixing mail
provided similar features. RFmail, a institutions. Within N o r t h America, transfer and BBS access.
complete F i d o N e t implementation there is growing use within the With the porting o f FidoNet to the
which runs on Unix SysV and Xenix, school systems thanks to the spread- DEC Rainbow, F i d o N e t BBSs be-
includes gateware to transform be- ing K12Net [5]. came quite p o p u l a r with the DEC
tween F i d o N e t message format and While the original FidoNet sys- Users G r o u p in St. Louis, Missouri.
that o f the uucp/Internet. tems were fully integrated within Ken Kaplan and Ben Baker were
Currently, there are approxi- bulletin b o a r d systems, FidoNet mail- particularly active and started the
mately one h u n d r e d gateway sys- only systems are now a noticeable first F i d o N e t newsletter. As the
tems, most o f them in N o r t h Amer- portion o f the public network. T h e s e nodelist a p p r o a c h e d 100 members,
ica. AsMe from tile expected provide the owner a facility similar to Kaplan and Baker took over from
internetwork email, there is consid- h a m radio or a fax machine, but pro- J e n n i n g s its organization a n d main-
erable gating o f Usenet news to and vide no public access via dial-up. tenance.
from F i d o N e t echomail conferences. A r o u n d the world, BBSs with As the nodelist passed the 200
A n u m b e r o f newsgroups are FidoNet capability provide the most mark, it became obvious that, for
shared globally by F i d o N e t and the publicly accessible and lowest-cost example, San Francisco had much
Usenet, e.g., FidoNet',; MODULA-2 email and enews service today. While daily traffic for St. Louis and vice
echomail conference is Usenet's most BBSs are only usable by a single versa, and dozens o f telephone calls
comp.lang.modula2, and FidoNet's dial-up caller at a time, others run were being placed to all the various
K12__Net conferences are the Usenet's multiline systems ranging from two
IThe Fido BBS was developed on a machine
k12.* hierarchy. Usenet newsgroups to 20 lines. Public access require- which was both slow and cumbersome, like the
are also m a d e available on a purely ments vary from formal user valida- dog n a m e d Fido, hence the name.
3• August 1993/Vo1.36, No.8 C O I m l P I U N I C A T I O N S OFTIIE ACN
nodes in each city. As calls within a began in 1986, with the publication (you may find this site generally use-
U.S. city are generally inexpensive, of FSC-0001 describing the then- ful for acquiring FidoNet supplies,
but calls between cities are not, it extant xmodem-based protocol suite
such as documentation, tools,
seemed obvious to concentrate the and the basic data formats [3]. This gateware).
intercity traffic into one call per was shortly followed by a description
FTS-0001 describes the original-
night. Tt/erefore, what had been a of the nodelist in FSC-0002 [1]. A
message data formats, session proto-
simple linear nodelist was broken FidoNet Standards Committee (now cols, and link layer protocols for
into a structure o f city segments FTSC) was formed in 1986 by the FidoNet as it was originally devel-
transforming the FidoNet address then-active software authors, chaired oped by Tom Jennings. The ability
notation from node to net/node. by a nonauthor. The FTSC collects for a node to obey this standard is
In late 1986, it became obvious and publishes documents called mandatory if it wishes to be listed
that an analogous problem existed FSCs, which are similar to the IETF's within the public FidoNet, although
between the continents. At the same RFCs. Those which are voted as for- the vast majority of connections now
time, the idea emerged of power mal standards are known as FTS use the far more efficient FTS-0006
users, or points, who could use documents. suite. Data transfer uses xmodem
FidoNet data formats and transport There are approximately 80 FSC and a variant called Telink, 128-byte
protocols (as opposed to BBS inter- documents at this time and five offi- block ACK/NAK protocols, neither
faces) to send and receive their mail cial FTS standards, Some of the most of which is streaming, bidirectional,
and enews. So, at a FidoNet Stan- interesting are depicted in Table 2. or windowing, and which discrimi-
dards Committee meeting in October The current document set is kept on nate between email and file transfer
1986, the nodelist was redesigned as many FidoNet nodes and is available at the session and data transfer level.
a four-level hierarchy o f zone (conti- via ftp on the internet as Midfile restart recovery is also ab-
nent), net, node, and point, with the sent.
address becoming zone:net/node.point, ftp.psg.com:~/publfidonetlstdsl*
The FTS-0006 session and link
as it remains today.
layer protocols [2] were developed by
The rate of growth of FidoNet Wynn Wagner and Vince Perriello in
seems typical o f electronic networks Table 1:
1987 to overcome the serious ineffi-
in the last decade. T h e approximate
ciency o f FTS-0001. T h e default data
number of nodes at the end of the link layer described uses zmodem, a
year is illustrated in Table 1. At pres-
very efficient streaming, windowing,
ent, the registered public FidoNet is 1984 100 and ACK-less (NAK only on failure)
considerably larger than Bitnet and
protocol designed by Chuck
has recently passed the estimated size
i Forsberg. It also provides midfile
of the registered part of the uucp
1986 1,400 restart recovery. The YooHoo/2U2
network.
session-level protocol provides for
In February, 1986, Jeff Rush de- exchange of identification and au-
veloped FidoNet's form of enews thorization data as well as allowing
called echomail. As very few FidoNet 1988 4,000
negotiation of the link layer protocol.
users were familiar with the Usenet,
they were quite surprised at the pop-
Common Software Components
ularity and rate o f growth of 1990 9,000 Like their uucp/Internet brethren,
echomail. Within two weeks, an in- ........ ............ ..........................................
FidoNet systems tend to have differ-
ternational echomail conference, ii!000 ent components to act as user,
MODULA-2, was propagated be- 1992 16,000 transfer/routing, and transport
tween Europe, Australia, and North
agents. While not all FidoNet imple-
America, and today the daily volume
mentations are composed identically,
of compressed echomail is over eight
on the whole the following concepts
megabytes (MB). T h e social effects,
both good and bad, of echomail on Tuble 2:
the network parallel those of the
Usenet.
Although primitive experiments
had been conducted earlier, in 1986
gateways between FidoNet and the
uucp network, and hence the Inter-
net, became sufficiently reliable for
production use.
TeChnical Standards
Technical standards development
COMMUNICATIOM| OF TIlil ACM August 1993/Vol.36, No.8 3 3
FidoNet has been owned and operatedprimarily by end users more
than computerprofessionals. Therefore, s o c i a l a n d
political issues arose in FidONet far
faster and more seriously than other
network cultures.
and nomenclature are u n d e r s t o o d A Mailer is the session and link vide minimal-cost public access to
t h r o u g h o u t FidoNet. level t r a n s p o r t layer which decides email. Two very basic features o f
A Bulletin Board Sys/.em (BBS) is when to make and accept FidoNet F i d o N e t encourage this. Every node
often available and provides a mail calls to/from o t h e r nodes and pro- is self-sufficient, n e e d i n g no s u p p o r t
and news user agent (M/NUA) to vides everything n e e d e d to t r a n s p o r t from o t h e r nodes to operate. But
dial-up callers o f the BBS, and it the email, enews, and files between more significant is that the nodelist
often provides a console interface for F i d o N e t nodes. Mailers know about contains the m o d e m telephone num-
the system o p e r a t o r as well. As BBS m o d e m s and how to control them, ber o f all nodes, allowing any node to
M/NUAs must be usable by dial-up how to detect if an incoming call is a communicate with any o t h e r node
users on unspecified terminals, the h u m a n BBS user as o p p o s e d to an without the aid o r consent o f techni-
interfaces tend to be line oriented incoming FidoNet call, how to pass cal o r political groups at any level.
with r a t h e r primitive editing facili- h u m a n s t h r o u g h to a BBS, what This is in strong contrast to the u u c p
ties. Some BBS systems such as Fido times o f day to place expensive but network, Bitnet, a n d the Internet.
and Opus provide complete software t i m e - d e p e n d e n t calls, and so forth. In 1985, the first F i d o N e t policy
suites integrating all components Because the mailer provides the link d o c u m e n t was published. It con-
necessary to use FidoNet, while most level protocols, its characteristics de- cerned itself almost entirely with
other BBSs require the addition o f termine i n t e r n o d e compatibility; technical p r o c e d u r a l issues. It re-
external components ~:o use them t h e r e f o r e a node is best known for quired a capability to send and re-
with FidoNet. the mailer it runs. Hence a node ceive email, defined the national mail
An Editor is a console M / N U A might be known as a Binkley node or hour as mandatory, delineated roles
which is usually available for those a Fido node because it uses o f the local network hubs and
nodes which do not have a BBS, or BinkleyTerm o r Fido as its mailer. nodelist coordinators, a n d stated
where the system o p e r a t o r prefers a A Nodelist Compiler transforms the simple restrictions on routing o f traf-
different interface. A,; the system nodelist from the standard FTS-0005 fic t h r o u g h unsuspecting nodes. In
console generally has known charac- distribution format to that n e e d e d by addition, it stated two social rules, a
teristics, Editor M/NUAs tend to- the node's other software, (i.e., proscription against use o f the net-
ward screen-oriented, multicolor, mailer, BBS, editor, and/or packer). work for illegal purposes (e.g., pi-
fancy interfaces, often with quite Aside from trivial differences in syn- rated software) and a statement o f
sophisticated editing capabilities. tax, m o r e complex translations may FidoNet's basic social guideline: "Do
A Packer or Scanner is analogous to be needed, (i.e., mailer software usu- not be excessively annoying, and do
the mail/news transfer agent (M/ ally requires that telephone numbers not become excessively annoyed."
NTA). It transforms the data to/from be t r a n s f o r m e d given local rules). In 1986 a well-intentioned but
the internal (i.e., not :~tandardized) naive g r o u p f o r m e d t h e Interna-
storage fi3rmat from/to the external Policy and Politics tional F i d o N e t Association, intend-
FTS-0001/4 transmission format. In contrast to the uucp network or ing to p r o m u l g a t e the technology
Packer M/NTAs also make routing the Internet, a n d d u e mostly to the a n d coordinate publication o f the
decisions,, usually based[ on data in a low cost o f entry, from its earliest newsletter and o t h e r writings about
local routing rule file. T h e s e local days, F i d o N e t has been owned and the network. Unfortunately, as
routing rules tell the M/NTA what o p e r a t e d primarily by end users and FidoNet operators were far m o r e
routes to use for mail within the local hobbyists m o r e than by c o m p u t e r socially oriented than their m o r e
city network, cost reduction routes professionals. T h e r e f o r e , social and technical b r e t h r e n in the other net-
for mail within the zone, and any political issues arose in F i d o N e t far works, the formal organization o f
special routes for interzone mail. faster and m o r e seriously than might I F N A t e n d e d to draw considerable
T h e N T A portion use,; an echomail be expected by those raised in other political interest and attracted the
rule base to decide which echomail network cultures. less constructive political elements o f
groups are to be exchanged with T o m Jennings i n t e n d e d F i d o N e t the F i d o N e t culture. T h e issue came
which other nodes in the network. to be a cooperative anarchism to pro- to a head in 1989 with an attempt to
4 August 1993/Vol,36, No.8 I I I O M M U M I C A T I O M $ OF Tile lli¢lll
~J'J'~flffln~
load the I F N A board o f directors Larry Landweb,er incited the devel- tion Networks]; Special-Purpose
and pass a motion which explicitly o p m e n t o f this article, and has been Application-Based Systems
put I F N A in complete control o f the the major force to include FidoNet General Terms: Design
network. T h e motion was cleverly within the I n t e r n e t community. I
Additional Key Words and Phrases:
forced into a netwide r e f e r e n d u m and the networking community owe
FidoNet
(FidoNet's only global vote to date) a great debt to them. []
which required a majority o f the net- About the Author:
work assent to I F N A rule. T h e refer- References RANDY BUSH is a compiler netware,
e n d u m did not pass, and I F N A was 1. Baker, B. The distribution nodelist. tools hacker, and too often a software
subsequently dissolved. FSC-0027. engineering manager. Residing in Port-
2. Becker, P. YOOHOO and YOOHOO/ land, Oreg., he is currently a software
T h e first written policy was pub-
2U2: The Netmail handshake used by architect at Olsen and Assoc., Zurich. He
lished and adopted by informal con-
Opus-CBCS and other intelligent has been involved in the integration of
sent. Subsequently, three revisions o f FidoNet mail handling packages, FTS-
FidoNet policy have been written appropriate networking technology in the
0006.
and made operational by various, but developing world for over four years,
3. Bush, R. A basic FidoNet technical
using FidoNet, UUCP, and TCP/IP. An-
less democratic, procedures. T h e standard. FTS-0001.
thor's Present Address: randy@psg.com
cu r r en t document, Policy-4, was 4. Guillarmod, F.J. From FidoNet to
written by the regional nodelist coor- Internet: The evolution of a national
dinators and has a large a m o u n t o f network. In Proceedings of INET'92.
social and political content enshrin- 1992. Permission to copy without fee all or part of this
5. Murray, J. K12 Network:Global educa- material is granted providedthat the copiesare not
ing a hierarchy o f coordinators: an madeor distributed fordirectcommercialadvantage,
tion through telecommunications. In
International Coordinator (IC), a the ACMcopyrightnoticeand the titleofthe publi-
Proceedings of 1NET'92. 1992. cation and its date appear, and notice is givethat
Zone Coordinator (ZC) on each con-
copying is by permission of the Association for
tinent, Regional Coordinators (RCs) CR Categories and Subject Descrip- Computing Machinery. To copy otherwise, or to
in subdivisions o f the continents, tors: C.2.1 [Computer-Communication republish, requiresa fee and/or specificpermission.
usually countries, and a Network Networks]: Network Architecture and
Coordinator (NC) for each local net- Design; C.2.3 [Computer-Communiea- © ACM 0002-0782/93/0800-031 $1.50
work. As it was written by the self-
anointed RCs, ZCs and the IC are
elected by the RCs, and NCs are ap-
pointed by the RCs. Although the
d o c u m e n t has caused considerable
acrimony and is large and complex, it
contains many useful operational
guidelines, and is t h e r e f o r e generally
observed.
The amazing resilience of
FidoNet's social and technical struc-
ture was made evident yet again in
1989-'90, when the RCs on many o f
the continents attempted to exert
serious social control u n d e r the re-
FACT #2:
cently published Policy-4. While
echomail provided quite high-
bandwidth (albeit low content) com- ACM Member Services Department
munication, and thus the political sit- 1515Broadway
NY~ N Y 10036
uation could be openly debated, the TFfLEPHONE." 1. 212. 626. 0500/
power structure's inability to restrict FAX." L212.944.1318
EMAIL: ACMHELP@ACM.ORG
node-to-node communication pre-
vented any real control from being FACT #3:
effected. A fair n u m b e r o f RCs and
NCs were forced to resign, and the
others have since taken m o r e passive
and facilitative roles.
PAX: 1.212.944.1318
EMAIL: ACMPUBS@ACM.ORG
Acknowledgments For pre-paid and purchase orders mailyour order and payment to:
ACM Order Department
T o m J e n n i n g s not only designed and PO Box 12114
developed FidoNet, but has been a Church St. Station
NY, N Y 10257 USA
friend as well as reviewer. Ishida For SIGGRAPH Video Reviewcall First Priority at 1.800.523.5503 or 1.708.250.0807;
Haruhisa provided encouragement, fax: 1.70&250.0038.
incentive, and very helpful reviews.
¢OMMUNICATIOHS OF THE ACM August 1993/Vol.36, No.8 3S
You might also like
- Introduction to Internet & Web Technology: Internet & Web TechnologyFrom EverandIntroduction to Internet & Web Technology: Internet & Web TechnologyNo ratings yet
- Public Switched Telephone Network (PSTN)Document4 pagesPublic Switched Telephone Network (PSTN)Syed Zulfiqar Haider BukhariNo ratings yet
- Introduction To The Technology: HistoryDocument4 pagesIntroduction To The Technology: HistoryAlia RhmnNo ratings yet
- The Telephone NetworkDocument2 pagesThe Telephone NetworkSrividhya SriNo ratings yet
- Public Switched Telephone NetworkDocument4 pagesPublic Switched Telephone NetworkYemmanAllibNo ratings yet
- The International Telecommunications Regime: Domestic Preferences And Regime ChangeFrom EverandThe International Telecommunications Regime: Domestic Preferences And Regime ChangeNo ratings yet
- Technical DocumentDocument3 pagesTechnical DocumentashwanileoNo ratings yet
- An Introduction To Voip: End-To-End Elements and Qos ParametersDocument18 pagesAn Introduction To Voip: End-To-End Elements and Qos ParametershocineNo ratings yet
- Wireless Local Loop: Fiber To The HomeDocument5 pagesWireless Local Loop: Fiber To The HomePrince ArafatNo ratings yet
- Unit 1 Notes - Computer CommunicationDocument28 pagesUnit 1 Notes - Computer Communicationmitrarittika004No ratings yet
- Unit IIDocument8 pagesUnit IIJayprakash DuveNo ratings yet
- What is a Computer Network? Components and TypesDocument39 pagesWhat is a Computer Network? Components and TypesSelva PalaniNo ratings yet
- E-Commerce Answer Set - IDocument6 pagesE-Commerce Answer Set - IrameshNo ratings yet
- CS 55 - Local Area NetworksDocument181 pagesCS 55 - Local Area NetworksJun Ramos YoursNo ratings yet
- Computer Networks Notes-ShashiDocument27 pagesComputer Networks Notes-ShashiMgi IndoreNo ratings yet
- Tompong-Kirby-Dimson-A-Pre-Midterm-Performance TaskDocument7 pagesTompong-Kirby-Dimson-A-Pre-Midterm-Performance TaskGet-Free PokeCoins-ClickHereNo ratings yet
- Answer To Selected Review Questions in Chapter 1Document3 pagesAnswer To Selected Review Questions in Chapter 1moahamd hashemNo ratings yet
- Network Protocols NotesDocument3 pagesNetwork Protocols NotesChinmaya Sahu100% (1)
- Unit 1 FirstDocument46 pagesUnit 1 FirstSimran LalchandaniNo ratings yet
- What Is The InternetDocument43 pagesWhat Is The InternetApuesto de MaravillsoNo ratings yet
- ReviewerDocument6 pagesReviewerairakeiziaNo ratings yet
- Computer Networks BookletDocument59 pagesComputer Networks Bookletnethrag2006No ratings yet
- Basic Networking - Cyber Security - Ethical HackingDocument25 pagesBasic Networking - Cyber Security - Ethical HackingShanzida Anika MimNo ratings yet
- Destination FTTHDocument80 pagesDestination FTTHmorozco1965No ratings yet
- 2016 Question Bank Computer NetworksDocument17 pages2016 Question Bank Computer Networksaarthy100% (1)
- Application of DTNDocument14 pagesApplication of DTNAndima Jeff HardyNo ratings yet
- NetwrokDocument9 pagesNetwrokmayank barsenaNo ratings yet
- Network TopologyDocument2 pagesNetwork Topologyjamek_boyNo ratings yet
- Advanced Computer NetworkingDocument42 pagesAdvanced Computer Networkingmustefa endrisNo ratings yet
- DCN PrefaceDocument5 pagesDCN PrefaceAnonymous OQjmTwnVkNo ratings yet
- Introduction To NetworkDocument21 pagesIntroduction To NetworkPRIYAM XEROXNo ratings yet
- Part 1:networkingbasics Part 2:addingspeed Part 3:sharingdevicesDocument12 pagesPart 1:networkingbasics Part 2:addingspeed Part 3:sharingdevicesMališa MiloševićNo ratings yet
- Basic Networking Concepts: 2. Protocols 3. Protocol Layers 4. Network Interconnection/InternetDocument29 pagesBasic Networking Concepts: 2. Protocols 3. Protocol Layers 4. Network Interconnection/InternethemendraNo ratings yet
- Communications and NetworksDocument14 pagesCommunications and Networksfscprimary05No ratings yet
- Fixed&Mobile Network&IP TCPDocument12 pagesFixed&Mobile Network&IP TCPNana Yaw AdehNo ratings yet
- Networks 1Document4 pagesNetworks 1sterrrrNo ratings yet
- History of Digital CommunicationsDocument4 pagesHistory of Digital CommunicationsShawn JamesNo ratings yet
- Packet RadioDocument10 pagesPacket Radiopdf.unlisted046No ratings yet
- R20 - CN Unit 1 - CDocument38 pagesR20 - CN Unit 1 - CKesavaNo ratings yet
- DCC Unit I Lecture NotesDocument13 pagesDCC Unit I Lecture NotesMaheedhar ReddyNo ratings yet
- Telecommunications and Internet/networks 4.1 Internet: Page 1 of 7Document7 pagesTelecommunications and Internet/networks 4.1 Internet: Page 1 of 7Eng. Bagunda Yves DescartesNo ratings yet
- Dist 03 4 PDFDocument28 pagesDist 03 4 PDFTazar phyo waiNo ratings yet
- Basic Networking Concepts: 2. Protocols 3. Protocol Layers 4. Network Interconnection/InternetDocument28 pagesBasic Networking Concepts: 2. Protocols 3. Protocol Layers 4. Network Interconnection/InternetAbdinasir RobleNo ratings yet
- Basic Networking ConceptsDocument28 pagesBasic Networking Conceptsapi-3832232100% (2)
- E-Commerce Infrastructure: The Internet, Web and Mobile PlatformDocument52 pagesE-Commerce Infrastructure: The Internet, Web and Mobile PlatformMoti DiroNo ratings yet
- FiberToTheHome FTTH PDFDocument80 pagesFiberToTheHome FTTH PDFmorozco1965No ratings yet
- LAN vs WAN: Key Differences in Coverage Area and DevicesDocument6 pagesLAN vs WAN: Key Differences in Coverage Area and DevicesSyed JaWad HyderNo ratings yet
- Network Fundamentals: Topologies, Types and HistoryDocument80 pagesNetwork Fundamentals: Topologies, Types and HistorysrinusirisalaNo ratings yet
- Week 16Document30 pagesWeek 16api-3737023No ratings yet
- Computer Network NotesDocument22 pagesComputer Network NotesHeta Desai100% (1)
- Telecomms ConceptsDocument111 pagesTelecomms ConceptsKAFEEL AHMED KHANNo ratings yet
- Debdeep Dan Xi-A Sci It-802 ProjectDocument28 pagesDebdeep Dan Xi-A Sci It-802 ProjectDebdeep DanNo ratings yet
- NetworkDocument75 pagesNetworkHarsh PathakNo ratings yet
- Networking EssentialsDocument2 pagesNetworking EssentialsMurugan K CbiNo ratings yet
- Unit 13Document11 pagesUnit 13Luis Norbert SantiagoNo ratings yet
- TelecommunicationDocument50 pagesTelecommunicationwudnehkassahun97No ratings yet
- Design and Fabrication of Hexapod Robot With Wirelss ActuationDocument41 pagesDesign and Fabrication of Hexapod Robot With Wirelss ActuationTesterNo ratings yet
- ASSIGNMENT NO 3 of DBSDocument6 pagesASSIGNMENT NO 3 of DBSHaider FarooqNo ratings yet
- Skybox ChangeManager UsersGuide V10!0!300Document79 pagesSkybox ChangeManager UsersGuide V10!0!300pisanij123No ratings yet
- Major Project FileDocument9 pagesMajor Project FilesqwNo ratings yet
- List of Concept - and Mind-Mapping SoftwareDocument7 pagesList of Concept - and Mind-Mapping Softwarenoah676No ratings yet
- Experiment 8: Generate and Analyze Line CodesDocument4 pagesExperiment 8: Generate and Analyze Line CodesSanskar GuptaNo ratings yet
- IntroductionDocument3 pagesIntroductionYogie NovriandiNo ratings yet
- 8.1 Cloud Solution Architect Sec 04 Chap 002 VPC V03 - DEMO Slides PDFDocument7 pages8.1 Cloud Solution Architect Sec 04 Chap 002 VPC V03 - DEMO Slides PDFPeter L. MontezNo ratings yet
- Processing XML Files With SQL Server Functions: Data Transformation Services OPENROWSET FunctionDocument3 pagesProcessing XML Files With SQL Server Functions: Data Transformation Services OPENROWSET FunctionDBNo ratings yet
- Jagdish Solanke - Analyst Programmer (l2) - 7 Yrs 4 MonthsDocument4 pagesJagdish Solanke - Analyst Programmer (l2) - 7 Yrs 4 MonthsPraveen PadmaNo ratings yet
- LCD 128x64 Tech12864GDocument10 pagesLCD 128x64 Tech12864GMarlon PerinNo ratings yet
- Error List AcupulseDocument5 pagesError List AcupulseJuan CarrascoNo ratings yet
- Swift HouseDocument10 pagesSwift HouseSantoshNo ratings yet
- AppearTV - XC Platform User ManualDocument337 pagesAppearTV - XC Platform User ManualRui LourencoNo ratings yet
- Core BSS IVR SolutionDocument4 pagesCore BSS IVR SolutionRafiq MagdyNo ratings yet
- Grade 12 CSS DHCP ConfigurationDocument3 pagesGrade 12 CSS DHCP ConfigurationSergio B. Goco Jr.No ratings yet
- Ble-Sniffer - Win - 1.2 - User GuideDocument17 pagesBle-Sniffer - Win - 1.2 - User GuideracarmonNo ratings yet
- VL4010 System Verilogl T P CDocument1 pageVL4010 System Verilogl T P CDarwinNo ratings yet
- C# Coding Standards and Best Programming PracticesDocument17 pagesC# Coding Standards and Best Programming PracticesCibin JoseNo ratings yet
- Hyperv SizingDocument24 pagesHyperv SizingbcmailistNo ratings yet
- Single Shunt Sensorless Vector Control of PMSM - Renesas - R01an0901eu0200 - rx62tDocument25 pagesSingle Shunt Sensorless Vector Control of PMSM - Renesas - R01an0901eu0200 - rx62tshivguptaNo ratings yet
- Alcatel Omnipcx EnterpriseDocument30 pagesAlcatel Omnipcx EnterpriseAriel BecerraNo ratings yet
- Cf-Ru5102 Uhf Rfid Reader User's Manual v1.2Document36 pagesCf-Ru5102 Uhf Rfid Reader User's Manual v1.2ssssssssssssssaaaaNo ratings yet
- COM 508 Assignment 3Document10 pagesCOM 508 Assignment 3sonaNo ratings yet
- US6567915 GutheryDocument17 pagesUS6567915 GutheryztakahashiNo ratings yet
- Verimatrix Encryptionengine™: High-Performance Cryptographic Operations in Compact Form FactorDocument2 pagesVerimatrix Encryptionengine™: High-Performance Cryptographic Operations in Compact Form FactorLucho OrtegaNo ratings yet
- Absolute File Name:: Unit-V Files, Modules and Packages FilesDocument13 pagesAbsolute File Name:: Unit-V Files, Modules and Packages FilesSUGANYA NNo ratings yet
- Q Guidance System With Spine Guidance Software BrochureDocument7 pagesQ Guidance System With Spine Guidance Software BrochureliuyonglogNo ratings yet
- How To Register A Site in CTISDocument3 pagesHow To Register A Site in CTISOlwys FernándezNo ratings yet
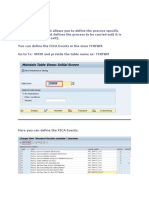
- Define FICA Events and Call Event FM in Billing ProcessDocument24 pagesDefine FICA Events and Call Event FM in Billing ProcessSanjeev SinghNo ratings yet
- Microsoft Azure Infrastructure Services for Architects: Designing Cloud SolutionsFrom EverandMicrosoft Azure Infrastructure Services for Architects: Designing Cloud SolutionsNo ratings yet
- AWS Certified Cloud Practitioner Study Guide: CLF-C01 ExamFrom EverandAWS Certified Cloud Practitioner Study Guide: CLF-C01 ExamRating: 5 out of 5 stars5/5 (1)
- Computer Systems and Networking Guide: A Complete Guide to the Basic Concepts in Computer Systems, Networking, IP Subnetting and Network SecurityFrom EverandComputer Systems and Networking Guide: A Complete Guide to the Basic Concepts in Computer Systems, Networking, IP Subnetting and Network SecurityRating: 4.5 out of 5 stars4.5/5 (13)
- CCNA: 3 in 1- Beginner's Guide+ Tips on Taking the Exam+ Simple and Effective Strategies to Learn About CCNA (Cisco Certified Network Associate) Routing And Switching CertificationFrom EverandCCNA: 3 in 1- Beginner's Guide+ Tips on Taking the Exam+ Simple and Effective Strategies to Learn About CCNA (Cisco Certified Network Associate) Routing And Switching CertificationNo ratings yet
- ITIL 4: Digital and IT strategy: Reference and study guideFrom EverandITIL 4: Digital and IT strategy: Reference and study guideRating: 5 out of 5 stars5/5 (1)
- The Compete Ccna 200-301 Study Guide: Network Engineering EditionFrom EverandThe Compete Ccna 200-301 Study Guide: Network Engineering EditionRating: 5 out of 5 stars5/5 (4)
- Amazon Web Services (AWS) Interview Questions and AnswersFrom EverandAmazon Web Services (AWS) Interview Questions and AnswersRating: 4.5 out of 5 stars4.5/5 (3)
- The CompTIA Network+ Computing Technology Industry Association Certification N10-008 Study Guide: Hi-Tech Edition: Proven Methods to Pass the Exam with Confidence - Practice Test with AnswersFrom EverandThe CompTIA Network+ Computing Technology Industry Association Certification N10-008 Study Guide: Hi-Tech Edition: Proven Methods to Pass the Exam with Confidence - Practice Test with AnswersNo ratings yet
- The Ultimate Kali Linux Book - Second Edition: Perform advanced penetration testing using Nmap, Metasploit, Aircrack-ng, and EmpireFrom EverandThe Ultimate Kali Linux Book - Second Edition: Perform advanced penetration testing using Nmap, Metasploit, Aircrack-ng, and EmpireNo ratings yet
- Computer Networking: The Complete Beginner's Guide to Learning the Basics of Network Security, Computer Architecture, Wireless Technology and Communications Systems (Including Cisco, CCENT, and CCNA)From EverandComputer Networking: The Complete Beginner's Guide to Learning the Basics of Network Security, Computer Architecture, Wireless Technology and Communications Systems (Including Cisco, CCENT, and CCNA)Rating: 4 out of 5 stars4/5 (4)
- Evaluation of Some Websites that Offer Virtual Phone Numbers for SMS Reception and Websites to Obtain Virtual Debit/Credit Cards for Online Accounts VerificationsFrom EverandEvaluation of Some Websites that Offer Virtual Phone Numbers for SMS Reception and Websites to Obtain Virtual Debit/Credit Cards for Online Accounts VerificationsRating: 5 out of 5 stars5/5 (1)
- Computer Networking: The Complete Guide to Understanding Wireless Technology, Network Security, Computer Architecture and Communications Systems (Including Cisco, CCNA and CCENT)From EverandComputer Networking: The Complete Guide to Understanding Wireless Technology, Network Security, Computer Architecture and Communications Systems (Including Cisco, CCNA and CCENT)No ratings yet
- Designing and Building Security Operations CenterFrom EverandDesigning and Building Security Operations CenterRating: 3 out of 5 stars3/5 (3)
- ITIL® 4 Direct, Plan and Improve (DPI): Your companion to the ITIL 4 Managing Professional and Strategic Leader DPI certificationFrom EverandITIL® 4 Direct, Plan and Improve (DPI): Your companion to the ITIL 4 Managing Professional and Strategic Leader DPI certificationNo ratings yet
- Introduction to Cyber-Warfare: A Multidisciplinary ApproachFrom EverandIntroduction to Cyber-Warfare: A Multidisciplinary ApproachRating: 4.5 out of 5 stars4.5/5 (3)
- AWS Certified Solutions Architect Study Guide: Associate SAA-C02 ExamFrom EverandAWS Certified Solutions Architect Study Guide: Associate SAA-C02 ExamNo ratings yet
- ITIL® 4 Create, Deliver and Support (CDS): Your companion to the ITIL 4 Managing Professional CDS certificationFrom EverandITIL® 4 Create, Deliver and Support (CDS): Your companion to the ITIL 4 Managing Professional CDS certificationRating: 5 out of 5 stars5/5 (2)
- Advanced Antenna Systems for 5G Network Deployments: Bridging the Gap Between Theory and PracticeFrom EverandAdvanced Antenna Systems for 5G Network Deployments: Bridging the Gap Between Theory and PracticeRating: 5 out of 5 stars5/5 (1)