Professional Documents
Culture Documents
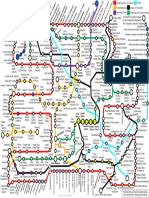
SOC Monitoring Mindmap
Uploaded by
Win ErOriginal Description:
Copyright
Available Formats
Share this document
Did you find this document useful?
Is this content inappropriate?
Report this DocumentCopyright:
Available Formats
SOC Monitoring Mindmap
Uploaded by
Win ErCopyright:
Available Formats
Malware protection (eg.
anti-virus) logs
• HTTP proxy logs Network intrusion detection systems (NIDS)
File Integrity Monitoring
DNS, DHCP and FTP logs Network intrusion prevention systems (NIPS)
Web and SQL server logs Technical Data loss protection (DLP)
Server Access Logs
Tools that employ potential malware Cybersecurity Tools
Appflow logs
isolation and investigation techniques (eg.
Spams
sandboxing or virtual execution engines) Phishing Emails Malwares
System activity logs (eg. Administrator), Application Server (Website)
including storage Other relevant security management Server Access Activities
appliances or tools
• Endpoint (and agent-based) logs
Logs from standard (eg. SAP) and
customised applications System
Authentication (eg. Windows) logs
Physical security logs
EDR
Starters
• Email, firewall, VPN and Netflow logs Logs
Networking Movers
Regarding Suspicious Processes IDS
Leavers
IAM
SSO
Configuration and Compliance
Vulnerabilities Logon Activities
IAM SaaS
IPS
Phishing Activities
Malicious EXEs using Bulk Hash Search
Execution
Suspicious Network Activities Persistence
Outdated Everything
Privilege Escalation
Credential Access
Number of Attacks Defense Evasion
Unauthorised Changes on System, Registry,
Server, Application Discovery
Lateral Movement
Exfiltration
Firewall
Malicious/Suspicious Activities
SIEM Doormant Accounts
Via Third-Party Informing
Non-Approved Software Installation Via Employee Informing
Usage of Remote Administration Tools
Encryption at Rest
Accounts Pertaining to left users
Encryption at Motion
Via Help Desk Team User Accounts
Incidents Monitoring
Data Security
Usage of Virtual Devices
Floating Topic
Application Management
Domain Accounts
Accounts
Local Admin Accounts
Usage of Proxy/VPN Tools
Mobiles
Company Provided Devices Tablets
Devices
BYOD
Expired Passwords What's your SOC USB
monitoring
Password Policy
Passwords not set in last 3 months
EDR
Malwares
Patches
Anti-Malware
CASB Non-Approved Desktop Based Cloud Apps
File-Sharing Tools
Third-party softwares Threat Intelligence Feeds
Non-Approved Clour URLs
Backup Monitoring
Windows
Feeds - IPs, Hashes, Filenames, Threat
Configuration Changes Actors, URLs, Domains
Custom Feeds Commercial Feeds
All Unix and MAC OS
Open Source Feeds
Active Directory
Change Requests
Networking Devices
Servers
VM team
Clients
Vulnerabilities and Alerts
Scanners
Workstations
Firewall
Pentest Services
Servers
Compliance Team
IDS/IPS
Operating Systems
Applications
Proxy Wi-Fi
You might also like
- DB 19c ArchitectureDocument40 pagesDB 19c Architectureharirk1986100% (2)
- TCS DynatraceTrainingDocument127 pagesTCS DynatraceTrainingSreenivasulu Reddy Sanam100% (2)
- CCNA Interview Questions and AnswersDocument72 pagesCCNA Interview Questions and Answersgodwin dsouzaNo ratings yet
- ZeroTrustSecurity PDFDocument7 pagesZeroTrustSecurity PDFzdravkoNo ratings yet
- SANS DFIR Malware Analysis Tips and Tricks Poster v2Document2 pagesSANS DFIR Malware Analysis Tips and Tricks Poster v2Rotem SalinasNo ratings yet
- Learn Cyber SecurityDocument1 pageLearn Cyber SecurityPHẠM MINH TRÍNo ratings yet
- The Virtual CampfireDocument200 pagesThe Virtual CampfireIbrahim KhaladNo ratings yet
- Oracle EBS Technical Step by Step - AP To GL Link Using XLA TablesDocument11 pagesOracle EBS Technical Step by Step - AP To GL Link Using XLA TableskartheekbeeramjulaNo ratings yet
- Digital Marketing Brochure PDFDocument36 pagesDigital Marketing Brochure PDFSai Kumar Pittala100% (1)
- Learning Life Cycle ManagementDocument21 pagesLearning Life Cycle ManagementjessyhamidNo ratings yet
- Idps Siem PDFDocument33 pagesIdps Siem PDFaqib ahmedNo ratings yet
- Odesk Question On Social Media MarketingDocument5 pagesOdesk Question On Social Media MarketingNabin Sayeed100% (1)
- IT Operations With Splunk: - Splunkd Is A Distributed C/C++ Server That Accesses, Processes and Indexes Streaming IT DataDocument5 pagesIT Operations With Splunk: - Splunkd Is A Distributed C/C++ Server That Accesses, Processes and Indexes Streaming IT DataAbdul Rahim100% (1)
- CISSP Cheat Sheet Domain 3Document1 pageCISSP Cheat Sheet Domain 3PremdeepakHulagbaliNo ratings yet
- Macro Programming GuideDocument15 pagesMacro Programming GuidesalvaleuvenNo ratings yet
- Final - Log Processing and Analysis With ELK Stack PDFDocument27 pagesFinal - Log Processing and Analysis With ELK Stack PDFRahul NairNo ratings yet
- Microsoft Zero Trust Maturity Model - Oct 2019Document7 pagesMicrosoft Zero Trust Maturity Model - Oct 2019Javier MoralesNo ratings yet
- ArcSight BasicsDocument57 pagesArcSight BasicsPradeep KumarNo ratings yet
- Module-3: Information Security ManagementDocument17 pagesModule-3: Information Security ManagementAkshi ChauhanNo ratings yet
- Secospace ElogDocument6 pagesSecospace ElogUtopia MediaNo ratings yet
- D2 - T8 - Reviewing Individual ESM Components - 092015Document46 pagesD2 - T8 - Reviewing Individual ESM Components - 092015trollmindNo ratings yet
- Mapping-Reference MonitorDocument3 pagesMapping-Reference Monitorapi-593553065No ratings yet
- DAP DatasheetpdfDocument3 pagesDAP DatasheetpdfNilangaNo ratings yet
- Apt Attacks Map Government 2019Document1 pageApt Attacks Map Government 2019spamstopsNo ratings yet
- BDSCP Module 09 MindmapDocument1 pageBDSCP Module 09 MindmappietropesNo ratings yet
- RSM AS400 Iseries DatasheetDocument3 pagesRSM AS400 Iseries DatasheetvasanthakumarGNo ratings yet
- System HackingDocument1 pageSystem Hackingwhatsapp88704717No ratings yet
- HexCoder Python Learning PathsDocument1 pageHexCoder Python Learning Pathssandunmeesara.testNo ratings yet
- Brochure Aida EngbDocument2 pagesBrochure Aida EngbchristianmaderoyepezNo ratings yet
- Ds Application Filtering IntelligenceDocument5 pagesDs Application Filtering IntelligenceErnesto MorenoNo ratings yet
- SIPAC Signal Intelligence ProcessingDocument12 pagesSIPAC Signal Intelligence ProcessingEwan RidzwanNo ratings yet
- BTEC Level 3 IT Unit 1 Knowledge MapDocument1 pageBTEC Level 3 IT Unit 1 Knowledge MapRini SandeepNo ratings yet
- Va A Data Clustering Algorithm For Mining Patterns From Event LogsDocument8 pagesVa A Data Clustering Algorithm For Mining Patterns From Event LogsredzgnNo ratings yet
- Database Security Policies and Procedures and Implementation For The Disaster Management Communication SystemDocument17 pagesDatabase Security Policies and Procedures and Implementation For The Disaster Management Communication SystemWissam ShehabNo ratings yet
- PD I 2015 Web Application SecurityDocument46 pagesPD I 2015 Web Application SecurityMunirul Ula PhDNo ratings yet
- WormDocument12 pagesWormSapaNo ratings yet
- Security Checklist - SecureframeDocument4 pagesSecurity Checklist - SecureframeNahom DejeneNo ratings yet
- AIM ECS Overview GCG Tenant Ops - Mar-2020 PDFDocument18 pagesAIM ECS Overview GCG Tenant Ops - Mar-2020 PDFEdgar Flores oNo ratings yet
- Secured Perimeter: Product HighlightsDocument2 pagesSecured Perimeter: Product Highlightshappy girlNo ratings yet
- 1761 RiskevalDocument2 pages1761 RiskevalTarik ShiguteNo ratings yet
- JWP Presentation Slides Davis Horwath ZabiukDocument13 pagesJWP Presentation Slides Davis Horwath ZabiukYassou InsatNo ratings yet
- Jeremy Banahene: Information Security Analyst Information Security AnalystDocument8 pagesJeremy Banahene: Information Security Analyst Information Security AnalystAshwani kumarNo ratings yet
- An - Approach - To - Understand - The - End - User - Behaviour Trough Log AnalysisDocument8 pagesAn - Approach - To - Understand - The - End - User - Behaviour Trough Log Analysisbasy decoNo ratings yet
- Secure Log Scheme For Cloud Forensics: Shweta N. Joshi Mrs - Geetha R.Chillarge Assistant ProfessorDocument6 pagesSecure Log Scheme For Cloud Forensics: Shweta N. Joshi Mrs - Geetha R.Chillarge Assistant ProfessorE-533 Kangane machhidranath subhashNo ratings yet
- Log Analysis Final Part 3 1703257926Document21 pagesLog Analysis Final Part 3 1703257926ahmed2trainerNo ratings yet
- DevOps Module 1 Symbol LegendDocument1 pageDevOps Module 1 Symbol Legendzulhelmy zulhelmyNo ratings yet
- Spell Streaming Parsing of System Event LogsDocument6 pagesSpell Streaming Parsing of System Event LogsredzgnNo ratings yet
- Arcsight Data Platform - LoggerDocument22 pagesArcsight Data Platform - LoggerBrice TOSSAVINo ratings yet
- Experience With An IT Asset Management SystemDocument23 pagesExperience With An IT Asset Management SystemCA Ghanathe RamakrishnaNo ratings yet
- Cysemol Manual ShortDocument59 pagesCysemol Manual ShortSrikanth S.No ratings yet
- CH 01Document24 pagesCH 01Nam NguyenNo ratings yet
- Ideas On A DCS ArchitectureDocument6 pagesIdeas On A DCS ArchitectureajayvgNo ratings yet
- SIEM Checklist ContentDocument1 pageSIEM Checklist Contentindian boyNo ratings yet
- Paladion ArcSight Training1Document92 pagesPaladion ArcSight Training1Krishna Gollapalli100% (2)
- Alvaristar: Network Management System For Broadband Wireless AccessDocument25 pagesAlvaristar: Network Management System For Broadband Wireless Accesslucorchea1No ratings yet
- Verax NMS & APM - Unified Network, Application and Infrastructure ManagementDocument2 pagesVerax NMS & APM - Unified Network, Application and Infrastructure ManagementVerax Systems Corp.No ratings yet
- Cheetah Functional ArchitectureDocument2 pagesCheetah Functional ArchitectureADITYA DUBEYNo ratings yet
- Cyber SecurityDocument8 pagesCyber SecurityAsghar AliNo ratings yet
- IT Training Certification - Microsoft Certified Systems Engineer (MCSE) Course OutlineDocument14 pagesIT Training Certification - Microsoft Certified Systems Engineer (MCSE) Course OutlineDayakar MeruguNo ratings yet
- Ch02 OS9eDocument97 pagesCh02 OS9ejeomxonNo ratings yet
- Module 5Document29 pagesModule 5ወንድሙ ዘገዬNo ratings yet
- IntroductionDocument15 pagesIntroductionmonitoring suhu ruanganNo ratings yet
- Phases: Covering Your Tracks: - Steganography - Event Logs AlterationDocument9 pagesPhases: Covering Your Tracks: - Steganography - Event Logs AlterationhiyuNo ratings yet
- Facebook Chatbot Thesis PaperDocument37 pagesFacebook Chatbot Thesis PaperAnNi GuPtaNo ratings yet
- Caselet 13: Pandora Radio: Fire Unprofitable Customers?: Key Aspects About Pandora's Business ModelDocument2 pagesCaselet 13: Pandora Radio: Fire Unprofitable Customers?: Key Aspects About Pandora's Business ModelAiswarya MishraNo ratings yet
- Beijer Electronics IX HMI BroschureDocument9 pagesBeijer Electronics IX HMI BroschureElectromateNo ratings yet
- KSHITIJ Info - Tech ProjectDocument39 pagesKSHITIJ Info - Tech Projectkshitij94No ratings yet
- H12 211 PDFDocument18 pagesH12 211 PDFAlly RoyNo ratings yet
- Choral Speaking TextDocument4 pagesChoral Speaking TextNurul MazniNo ratings yet
- Alpine LinuxDocument5 pagesAlpine LinuxmussabbeNo ratings yet
- NTserverDocument150 pagesNTservergolemicNo ratings yet
- WF4 Pre Production HoWDocument142 pagesWF4 Pre Production HoWrohit_lNo ratings yet
- Elementary: LevelDocument5 pagesElementary: LevelviktoriaNo ratings yet
- For ProjectDocument14 pagesFor ProjectNitesh pandeyNo ratings yet
- SpotifyDocument200 pagesSpotifyfidelekamsu12No ratings yet
- SC10E016ADocument3 pagesSC10E016AMahendra SingNo ratings yet
- PVT 2012 Lab Cisco JabberDocument88 pagesPVT 2012 Lab Cisco JabberGilles de PaimpolNo ratings yet
- Some Aspects of Cyberlaw Related To B2B MarketingDocument51 pagesSome Aspects of Cyberlaw Related To B2B Marketingarpit5179No ratings yet
- Zotonic 733468258Document471 pagesZotonic 733468258guneshrajNo ratings yet
- EcoStruxure Panel Server - PAS800LDocument3 pagesEcoStruxure Panel Server - PAS800LRahmat HardityoNo ratings yet
- SEDocument197 pagesSEAnkit PriyarupNo ratings yet
- Voice PortalDocument8 pagesVoice PortalthegownuproosterNo ratings yet
- ComPro-DNA CompressedDocument8 pagesComPro-DNA CompressedAnggi RodesNo ratings yet
- h16567 Connectrix Ds 6600b Switches SsDocument6 pagesh16567 Connectrix Ds 6600b Switches Ssanhsang123No ratings yet
- Strategies For High School Students To Develop Networking Skills-2Document1 pageStrategies For High School Students To Develop Networking Skills-2api-236019943No ratings yet
- Add TRX Bts Plus NokiaDocument11 pagesAdd TRX Bts Plus NokiatohompurbaNo ratings yet
- Tejas Product Brochure v3 FDocument12 pagesTejas Product Brochure v3 FjtosehoreNo ratings yet
- Detecting Cyber Security Threats in WeblogsDocument12 pagesDetecting Cyber Security Threats in Weblogsayoub_itNo ratings yet