0% found this document useful (0 votes)
750 views10 pagesShibboleth IDP Setup for Researchers
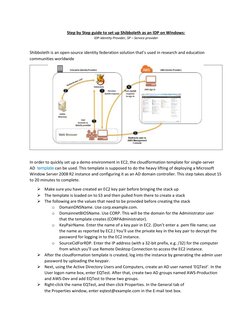
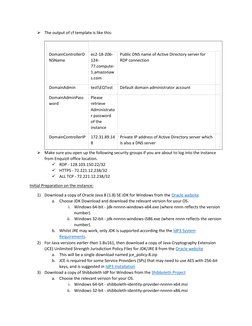
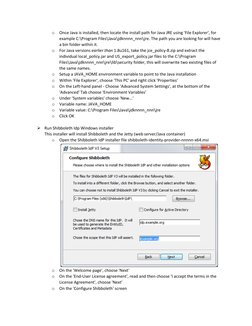
This document provides step-by-step instructions for setting up Shibboleth as an identity provider (IDP) on a Windows server using Amazon Web Services (AWS). It describes deploying an Active Directory instance using an AWS CloudFormation template, then configuring the server as an IDP with Shibboleth. Key steps include installing Java, downloading and running the Shibboleth IDP installer, configuring the IDP's DNS name and scope, and integrating it with the Active Directory domain for user authentication.
Uploaded by
maham sabirCopyright
© © All Rights Reserved
We take content rights seriously. If you suspect this is your content, claim it here.
Available Formats
Download as PDF, TXT or read online on Scribd
0% found this document useful (0 votes)
750 views10 pagesShibboleth IDP Setup for Researchers
This document provides step-by-step instructions for setting up Shibboleth as an identity provider (IDP) on a Windows server using Amazon Web Services (AWS). It describes deploying an Active Directory instance using an AWS CloudFormation template, then configuring the server as an IDP with Shibboleth. Key steps include installing Java, downloading and running the Shibboleth IDP installer, configuring the IDP's DNS name and scope, and integrating it with the Active Directory domain for user authentication.
Uploaded by
maham sabirCopyright
© © All Rights Reserved
We take content rights seriously. If you suspect this is your content, claim it here.
Available Formats
Download as PDF, TXT or read online on Scribd
- Introduction to Shibboleth
- Initial Preparation
- Installation and Configuration
- Advanced Configuration and Security
- AWS Integration Setup
- Troubleshooting and References