Professional Documents
Culture Documents
3 Monitoring and Testing The Ethernet Network
Uploaded by
Sam eagle goodOriginal Title
Copyright
Available Formats
Share this document
Did you find this document useful?
Is this content inappropriate?
Report this DocumentCopyright:
Available Formats
3 Monitoring and Testing The Ethernet Network
Uploaded by
Sam eagle goodCopyright:
Available Formats
Module 5
3. MONITORING AND TESTING THE ETHERNET NETWORK
3.1 Introduction
The following parameters are covered by the Ethernet performance metrics:
Latency (delay) – the amount of time required for a frame to travel from
source to destination.
Jitter – a measure of the deviation of the latency from its average value.
Loss rate – the probability that an individual packet is lost (dropped) during
the transmission.
Throughput – the amount of digital data transferred per time unit.
Error rate – the ratio of the number of erroneous units of data to the total
number of units of data transmitted.
Bit error rate – the ratio of the number of incorrectly received bits to the
total number of transmitted bits.
There are many free and commercial applications available for common Operating
Systems such as MS Windows, Linux and OS X that can provide varying LAN throughput
performance measurement. There are also self contained hardware based solutions that
provide the most accurate LAN performance measurement / stress testing.
Software applications can cost up to several hundred euros. Hardware based solutions
range from a few hundred to tens of thousands of euros and are typically used by
manufacturers, carriers and professional IT consulting organizations.
Fig 3.1. Basic Ethernet measurement setup
In its most basic configuration Ethernet is relatively simple to measure. The base
configuration is shown in Figure 3.1. As shown here, Ethernet is a broadcast technology,
where all but the sending machine can see all of the traffic on the network. The Ethernet
Section 3: Monitoring/Testing Ethernet Network Page 1
Module 5
backbone could either be a coaxial cable string, as in 10base2 and 10base5, or a passive
hub using a 10 or 100baseT. In all of these situations every machine sees all of the traffic
at the same time, excluding cable delays. This means that all the monitor needs to do is
capture every packet from the network and timestamp it.
Unfortunately fewer and fewer networks are using such a simple broadcast system any
more. In order to obtain higher levels of performance and security, most networks use
some sort of active device for the backbone. A common example of this is a network
switch, where packets are sent only to the destination machine. This has the advantage
of being much more secure; only the destination machine can look at the traffic, and can
have higher performance. This is because if two pairs of machines are using the network
at once, in a broadcast system they all have to share the available bandwidth equally. In
a switch, however, each pair has the full available bandwidth between them. The possible
bandwidth between hosts only drops off when multiple hosts all want to transmit to the
same destination.
Both of these properties make passive measurement difficult. If the network traffic is no
longer broadcast, how can the monitor watch the traffic? There are two methods that can
allow this. First, it is often the case that an Ethernet switch will contain one port that
copies all the data. The problem with this port is that the switch must interfere with the
data. Normally two packets could be trying to flow through the switch at exactly the
same time, providing the source and destinations are different. If this occurs then the
switch must delay and queue one of the packets before it is sent to the port, introducing
inaccuracies in the timestamps on these packets. One other problem is that the data
rates inside a switch can exceed the data rates of a single line. In this case the switch
must `clip' the data that is sent to the accumulated port, dropping packets from the
trace.
The second alternative is to insert a passive electronic tap into the wire between a host
and switch. This situation ends up looking very similar to the ATM situation due to the full
duplex host to hub connection present on modern 100baseT systems, requiring 2
receiver interfaces on the monitor.
3.2 Hardware based measurement
Hardware solutions try to correct the many limitations of a software system. In a full
hardware solution, as much of the monitoring system is carried out on the custom
interface (card) as possible, and the system is used for storage and formatting of the
data.
The important features that can be carried out on the card are:
Section 3: Monitoring/Testing Ethernet Network Page 2
Module 5
-Timestamping
-Clock synchronization
-Dropped packet counting
-Traffic filtering
When recording network traffic, accurate timestamping of the arrival of packets is
essential for the subsequent analysis of performance metrics. Ideally the packet should
be timestamped as soon as it has arrived on the card, before any buffering or queuing
takes place.
Clock synchronization is important if there are multiple interfaces in a machine. If
packets are being captured by two interfaces, the timestamps need to be consistent
between interfaces.
In a hardware system, a check can be placed on any buffers to detect packet loss. A
hardware solution will not necessarily be perfect, but a well designed system will be able
to provide a definite count of any drops that have occurred in the system. For this
reliability to carry through to the final network trace, checks must be placed at every
point in the system that packet loss can occur. This includes any software components
that run on the host PC to deal with the storage of the data as it is delivered by the
monitor card.
Hardware solutions also allow a monitor to deal with larger data rates than software
solutions could. It is quite often the case that a limited amount of data will be saved in a
monitor, however in a software solution the operating system and possibly monitoring
application have to see all of the traffic, then decide if it should be kept. If the hardware
becomes intelligent, then it can carry out this function, discarding unwanted data at the
earliest possible point.
The major disadvantage of hardware monitoring systems has always been cost. Until
recently there have been limited amounts of hardware designed specifically for network
monitoring. This meant that any group wanting high accuracy network monitoring had to
design such a system from scratch. These solutions are often too costly for some
measurement work, so they tend to be used for projects requiring very high accuracy or
high speed systems.
Section 3: Monitoring/Testing Ethernet Network Page 3
Module 5
Fig. 3.2. Validator NT 955
Test-Um NT 955 Validator NT (Fig. 3.2) is an example of all-in-one network management
tool with a 4-inch color LCD screen. The NT955 Validator NT certifies, identifies,
configures and documents the Ethernet network.
The Test-Um NT955 Validator NT can:
Determine fault locations, cable length and delay or noise conditions.
Produce and print cable test schedules and cable test results.
Qualify lines for VoIP usage.
Identify - active components of your network on the other end of the cable
Identify all types of equipment and port service discovery with advertised
speed ratings and DHCP negotiation.
Access IP addresses, ping equipment and flash hubs/switches for positive port
location. · Configure - links between nodes at Gigabit speed.
Check IP addresses on netmask, Gateway/routers and domain name servers.
Confirm links between equipment for changes or upgrades.
3.3 Software based measurement
All measurement systems will require some software components, the important
distinction is that in a software system, no special assistance for measurement is
provided by any hardware.
Section 3: Monitoring/Testing Ethernet Network Page 4
Module 5
The simplest and quickest passive measurement system is to run the Unix program
tcpdump. This program is supported under most Unix systems. It will listen on a specified
network interface, and capture all traffic seen on that link. Regardless of its name, it will
dump all data sourced from and destined for that interface, as well as any other traffic
seen on that section of the network, and is not restricted to TCP. The tcpdump can run in
two modes, either capture traffic to a file, or display text information on every packet on
the screen. Also built in are filtering rules that allow capture of a specified subset of data,
for instance TCP traffic, on port 80, between host x and y.
The tcpdump is a not only a very common application, but provides a good example of
techniques used in software-based solutions. A software based monitor requires
assistance from the operating system kernel. In most operating systems the kernel
contains the network stack that provides an interface between the applications and the
network card. In normal operation there are two levels of filtering occurring. First the
network card will only transmit to the network stack packets that have to be dealt with
by this machine. For point to point network systems, this will be all packets, for
broadcast systems such as Ethernet, this will be only a subset of packets. Next the kernel
splits up packets, deals with some itself, and sends on the others to the appropriate
application to deal with.
A software monitor such as tcpdump will run as an application program. Without a special
interface to the network stack, this program would be unable to capture any packets that
were destined for other machines or other applications on the monitor. This would mean
that passive measurement would be impossible.
Figure 3.3. Software monitor setup
Figure 3.3 shows a representation of the network layering present in many Unix kernels.
The interface that allows programs such as tcpdump to work, is the packet capturing
interface. This interface, referred to often as the pcap interface, is accessed through a C
library called libpcap. This library also allows reading and writing to files, providing
uniform access to a program for trace files and live networks. tcpdump is a higher level
Section 3: Monitoring/Testing Ethernet Network Page 5
Module 5
interpretation and filtering program that sits on top of libpcap. For this reason it is
common to refer to files created by libpcap as tcpdump files.
libpcap provides the method for a software program to capture packets that are destined
for other applications. To allow capture of all packets seen on a network, it is often
necessary to put a network card in promiscuous mode. In this mode a network card will
provide the network stack with all packets on the network, not only the ones to be dealt
with locally. These packets will normally be discarded at the kernel level, but will be
forwarded to the pcap interface if requested.
The problem with software monitoring solutions is the fact that none of the components
have been designed or optimized for this use. There are many delays, and buffers in a
software solution that reduce the accuracy of timestamps and increase the possibility of
packet loss.
The first place this occurs is at the hardware level. A network card may not be reliable
enough to capture every packet on a network. In normal use these dropped packets
would be corrected for by the TCP stack for a reliable connection. In a monitoring
situation, undetected packet loss could cause problems with analysis, or just reduce the
accuracy of results. Another common problem is caused by attempting to increase
performance; many network cards will buffer a stream of packets, the card will then only
interrupt the host once and deliver a collection of packets, as opposed to doing this for
each packet. This increases host performance, but means that the timestamps on
successive packets may not represent the actual inter-packet time.
The timestamping process on a libpcap system occurs in the kernel. This timestamp can
be delayed if the host system is under load, and the interrupt service for a packet is
delayed. Also the buffers that store the packet before delivery to the libpcap application
may be unchecked. If an application program does not clear the buffer quickly enough,
then packets can be silently dropped.
Software based systems are not limited to using the pcap interface. A user could write a
custom network card driver to provide an interface to the network card for use with
passive measurement only. This solution would remove the ability to use the network
card as a standard network interface, but it could still suffer from many of the problems
of a libpcap system.
Software solutions have one major advantage. They are likely to be much cheaper and
quicker to setup than a specialist hardware solution. They offer only limited accuracy of
the data measured.
Section 3: Monitoring/Testing Ethernet Network Page 6
Module 5
3.4 Further reading
For more information visit:
http://www.ixiacom.com
http://www.testersandtools.com
http://www.wand.net.nz
http://www.ethernetextender.com
Sources:
Figure [3.1], [3.2] http://www.wand.net.nz
Figure [3.3] http://www.elnex.pl
Authors: P.Bogdanski, W. Grega
Section 3: Monitoring/Testing Ethernet Network Page 7
You might also like
- Fuzzy Logic Trafc Control for High-Speed NetworksDocument9 pagesFuzzy Logic Trafc Control for High-Speed NetworksanraomcaNo ratings yet
- Monitoring NetworksDocument5 pagesMonitoring Networksraghunandhan.jmeterNo ratings yet
- Network Tap - WikipediaDocument48 pagesNetwork Tap - Wikipediaلمسة امل100% (1)
- What Are The Difference Between Hub and SwitchDocument10 pagesWhat Are The Difference Between Hub and SwitchSameer HussainNo ratings yet
- Networking PRACTICALDocument24 pagesNetworking PRACTICALMohit GusainNo ratings yet
- Network protocols define communication rules between devicesDocument5 pagesNetwork protocols define communication rules between devicesNeenetoots GarciaNo ratings yet
- Advance Lec1 2Document49 pagesAdvance Lec1 2xuz xuzNo ratings yet
- IP HanserAutomotive 201304 PressArticle EN PDFDocument5 pagesIP HanserAutomotive 201304 PressArticle EN PDFSaravanan ElumalaiNo ratings yet
- Ipt NotesDocument4 pagesIpt NotesDavid PhanNo ratings yet
- Assignment-1: Internet & Multimedia TechnologyDocument6 pagesAssignment-1: Internet & Multimedia TechnologySwarnim ShuklaNo ratings yet
- ATM Provides QoS Support for Multimedia Apps on Same NetworkDocument23 pagesATM Provides QoS Support for Multimedia Apps on Same Networkmahboobiqbal09No ratings yet
- Reg No: 1947234: Performance Problems in Computer NetworksDocument5 pagesReg No: 1947234: Performance Problems in Computer NetworksAbhiNo ratings yet
- Chapter Eight Network Control and Monitoring: Circuit SwitchingDocument7 pagesChapter Eight Network Control and Monitoring: Circuit Switchingshavali56No ratings yet
- TCP/IP PROTOCOL SUITE AND ATM LAYERSDocument12 pagesTCP/IP PROTOCOL SUITE AND ATM LAYERSsravan123No ratings yet
- Ex No: 6 Raw Sockets (Packet Capturing & Filtering)Document6 pagesEx No: 6 Raw Sockets (Packet Capturing & Filtering)Pitchairaj BhuvaneswariNo ratings yet
- Part 5: Transport Protocols For Wireless Mobile Networks: Sequence NumbersDocument6 pagesPart 5: Transport Protocols For Wireless Mobile Networks: Sequence NumbersKani MozhiNo ratings yet
- 2 Link Layer Technologies: T.O.P. Businessinteractive GMBH Page 1 of 18Document18 pages2 Link Layer Technologies: T.O.P. Businessinteractive GMBH Page 1 of 18Daniel CafuNo ratings yet
- Networking NotesDocument10 pagesNetworking NotesADITYA RAJNo ratings yet
- What Are Network Taps?Document5 pagesWhat Are Network Taps?Krishna Chaitanya BhagavatulaNo ratings yet
- Choosing The Right Industrial Ethernet Switch: What Does A Switch Do?Document4 pagesChoosing The Right Industrial Ethernet Switch: What Does A Switch Do?newgenbeNo ratings yet
- Data Packets Analyzer AND Controller LanDocument7 pagesData Packets Analyzer AND Controller LanMumbai AcademicsNo ratings yet
- Methodology Used To Identify The Flows: Flow AnalysisDocument24 pagesMethodology Used To Identify The Flows: Flow AnalysisRaj Vinod KumarNo ratings yet
- EC8551 CN Question BankDocument43 pagesEC8551 CN Question BankRaja Pirian100% (3)
- 201980090184+computer Network Final AssignmentDocument10 pages201980090184+computer Network Final AssignmentMd. Ziaul Haque ShiponNo ratings yet
- Packet SniffersDocument42 pagesPacket SniffersAmit BoraNo ratings yet
- NETWORKINGDocument13 pagesNETWORKINGraghuvarunbtech777No ratings yet
- 20.verification of Four Port Router For Network On Chip (Noc)Document5 pages20.verification of Four Port Router For Network On Chip (Noc)vijaykannamallaNo ratings yet
- Networking Basics 1Document32 pagesNetworking Basics 1raghuvarunbtech777No ratings yet
- Crowd Management SystemDocument18 pagesCrowd Management SystemChitiBujiNo ratings yet
- DCN Unit-2saqDocument7 pagesDCN Unit-2saqsravan kumarNo ratings yet
- RealTime EthernetDocument20 pagesRealTime Ethernetgsvijay57No ratings yet
- Network Packet Sniffer Project SynopsisDocument4 pagesNetwork Packet Sniffer Project SynopsisMallikarjunaNo ratings yet
- Rift Valley University Bishoftu CampusDocument58 pagesRift Valley University Bishoftu CampusAyansa TeshomeNo ratings yet
- Final bn-208 GoluDocument19 pagesFinal bn-208 GoluVirender AryaNo ratings yet
- CN Unit1 8-7-10Document20 pagesCN Unit1 8-7-10nallapatiharika0% (1)
- Method To Monitor The Transfer of Packets: Packet Sniffer: AbstractDocument3 pagesMethod To Monitor The Transfer of Packets: Packet Sniffer: AbstractNikhil ChowdaryNo ratings yet
- Ee7234: Advanced Data Communication: Tutorial No: 01 - High Speed Packet SwitchingDocument17 pagesEe7234: Advanced Data Communication: Tutorial No: 01 - High Speed Packet SwitchingNuwanSachithraLansakaraNo ratings yet
- CB - EN.U4AIE22016 Computer Networking AssignmentDocument3 pagesCB - EN.U4AIE22016 Computer Networking AssignmentPranNo ratings yet
- 2 Real-Time Control System and Real-Time NetworksDocument7 pages2 Real-Time Control System and Real-Time NetworksSam eagle goodNo ratings yet
- CN Manual Lab (R20)Document85 pagesCN Manual Lab (R20)4416 LikhithaNo ratings yet
- Computer Networking: An introductory guide for complete beginners: Computer Networking, #1From EverandComputer Networking: An introductory guide for complete beginners: Computer Networking, #1Rating: 4.5 out of 5 stars4.5/5 (2)
- Computer Networks Unit-I IntroductionDocument21 pagesComputer Networks Unit-I IntroductionKurumeti Naga Surya Lakshmana KumarNo ratings yet
- What's The Difference Between Ethernet Types?Document4 pagesWhat's The Difference Between Ethernet Types?leonardo_melo_costaNo ratings yet
- Arcnet 2Document11 pagesArcnet 2Boris BarzalloNo ratings yet
- Network Emulation With NetEmDocument9 pagesNetwork Emulation With NetEmghostreamNo ratings yet
- Question No 1: Describe The Key Elements of A Simple Communication ModelDocument9 pagesQuestion No 1: Describe The Key Elements of A Simple Communication ModelmuneebhaseebNo ratings yet
- 1.3.1.3 Lab - Mapping The InternetDocument11 pages1.3.1.3 Lab - Mapping The InternetHugoSantaellaSr100% (1)
- INDP Part 2Document8 pagesINDP Part 2Cruz Fultz LisaNo ratings yet
- Chapter_Four of NetworkingDocument64 pagesChapter_Four of NetworkinghaileNo ratings yet
- Mini Project - 18CSC302J - COMPUTER NETWORKS: Team MembersDocument6 pagesMini Project - 18CSC302J - COMPUTER NETWORKS: Team MembersVijay RamrajNo ratings yet
- Functional Design Specification NetworkDocument33 pagesFunctional Design Specification Networkmoch lutfi100% (1)
- It 1Document48 pagesIt 1mitalisgawadeNo ratings yet
- 1 - OSI Model: Network Revision - Reference ModelDocument5 pages1 - OSI Model: Network Revision - Reference Modelyaasir_7868868No ratings yet
- Unit 3 System Interfacing and ControllersDocument48 pagesUnit 3 System Interfacing and ControllersSrinivasan V PNo ratings yet
- Week 3Document5 pagesWeek 3hiren_keepsmilingNo ratings yet
- Protocol Interview QuestionsDocument10 pagesProtocol Interview QuestionsSam RogerNo ratings yet
- CN 16 Marks With AnswersDocument35 pagesCN 16 Marks With AnswersSankar GaneshNo ratings yet
- S7-TCPIP Ethernet InterfaceDocument124 pagesS7-TCPIP Ethernet InterfaceSam eagle goodNo ratings yet
- A03 StartupDocument48 pagesA03 StartupSam eagle goodNo ratings yet
- Deck BleDocument1 pageDeck BlenemoneoNo ratings yet
- Siemens PLC Programming Example1 PDFDocument12 pagesSiemens PLC Programming Example1 PDFHani ErrachidNo ratings yet
- Deckble KO-7KFMSDocument1 pageDeckble KO-7KFMSSam eagle goodNo ratings yet
- SIMATIC NET Commissioning PC Stations - ManualDocument221 pagesSIMATIC NET Commissioning PC Stations - ManualSam eagle goodNo ratings yet
- Brochure Simatic-Wincc-Flexible enDocument28 pagesBrochure Simatic-Wincc-Flexible enSam eagle goodNo ratings yet
- Programação em Realtime SystemDocument26 pagesProgramação em Realtime SystemSam eagle goodNo ratings yet
- Simatic Configuration Communication - 2Document18 pagesSimatic Configuration Communication - 2Sam eagle goodNo ratings yet
- Simatic FM 351: First Steps in CommissioningDocument6 pagesSimatic FM 351: First Steps in CommissioningSam eagle goodNo ratings yet
- Dinamic BrakeDocument18 pagesDinamic BrakeSam eagle goodNo ratings yet
- Sink SourceDocument4 pagesSink SourceSam eagle goodNo ratings yet
- Scan Flow ChartDocument2 pagesScan Flow ChartSam eagle goodNo ratings yet
- Control Techniques Drives and Controls Handbook PDFDocument384 pagesControl Techniques Drives and Controls Handbook PDFbudak150% (2)
- TF5200 Gantry Operation enDocument33 pagesTF5200 Gantry Operation enSam eagle goodNo ratings yet
- Brake DynamicDocument3 pagesBrake DynamicSam eagle goodNo ratings yet
- Driver Gantry Rigid Control FunctionDocument22 pagesDriver Gantry Rigid Control FunctionSam eagle goodNo ratings yet
- SIMATIC NET Siemens PROFIBUS Controller 3 User DescriptionDocument106 pagesSIMATIC NET Siemens PROFIBUS Controller 3 User DescriptionSam eagle goodNo ratings yet
- FM 351 - Getting - StartedDocument20 pagesFM 351 - Getting - StartedSam eagle goodNo ratings yet
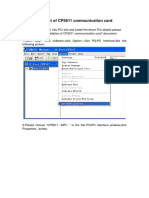
- The Test of CP5611 Communication CardDocument8 pagesThe Test of CP5611 Communication CardSam eagle goodNo ratings yet
- FM 351 Positioning Function Installation and ParameterDocument170 pagesFM 351 Positioning Function Installation and ParameterSam eagle goodNo ratings yet
- FM 351 Positioning With S7-300Document204 pagesFM 351 Positioning With S7-300Sam eagle goodNo ratings yet
- CP5512E InstallationDocument12 pagesCP5512E InstallationSam eagle goodNo ratings yet
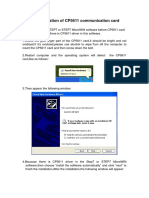
- The Installation of CP5611 Communication CardDocument4 pagesThe Installation of CP5611 Communication CardSam eagle goodNo ratings yet
- SIMATIC NET Siemens PROFIBUS Controller 4 User DescriptionDocument96 pagesSIMATIC NET Siemens PROFIBUS Controller 4 User DescriptionSam eagle goodNo ratings yet
- SIMATIC NET Siemens PROFIBUS Controlle 3 Hardware DescriptionDocument68 pagesSIMATIC NET Siemens PROFIBUS Controlle 3 Hardware DescriptionSam eagle goodNo ratings yet
- CP5611 Card IntroductionDocument2 pagesCP5611 Card IntroductionSam eagle goodNo ratings yet
- PROFIBUS Servo Positioning Controller ARS 2000Document84 pagesPROFIBUS Servo Positioning Controller ARS 2000Sam eagle goodNo ratings yet
- C79000-G8976-C157-0 SIMATIC NET PROFIBUS Controller SPC 4-2Document126 pagesC79000-G8976-C157-0 SIMATIC NET PROFIBUS Controller SPC 4-2Sam eagle goodNo ratings yet
- PROFIBUS FMS-OLE-DDE S5 CP5431 and PC FMS-CP5412Document24 pagesPROFIBUS FMS-OLE-DDE S5 CP5431 and PC FMS-CP5412Sam eagle goodNo ratings yet
- Seminar Report JonesDocument26 pagesSeminar Report JonesJones GNo ratings yet
- Ethernet Media and Connection RequirementsDocument3 pagesEthernet Media and Connection Requirementsadrienne clarisseNo ratings yet
- The (almost completely) Open Source Whitebox RouterDocument13 pagesThe (almost completely) Open Source Whitebox RoutertobecaNo ratings yet
- TAS 2000 VOIP-Ex Installation and Programming ManualDocument56 pagesTAS 2000 VOIP-Ex Installation and Programming ManualOscar Damián Gómez HernándezNo ratings yet
- "Devices For Connecting Network": Presented To The College of Computer Studies Data Communication and Networking 2Document9 pages"Devices For Connecting Network": Presented To The College of Computer Studies Data Communication and Networking 2Apple CamaliganNo ratings yet
- 12 Computer Science Notes CH08 Communication and Open Source ConceptsDocument16 pages12 Computer Science Notes CH08 Communication and Open Source ConceptsVibha Sethi50% (2)
- CCBoot Diskless Boot Solution OverviewDocument24 pagesCCBoot Diskless Boot Solution Overviewhuracanrojo94No ratings yet
- Chapter1 InfoDocument88 pagesChapter1 InfoDinda Alifal BalqisNo ratings yet
- S7600 Series Switches DatasheetDocument21 pagesS7600 Series Switches Datasheetmariadpg4No ratings yet
- Identify and Resolve Network ProblemsDocument19 pagesIdentify and Resolve Network ProblemsAbubeker Hashim100% (3)
- Microsoft Official Course: Networking With Windows Server 2016Document19 pagesMicrosoft Official Course: Networking With Windows Server 2016Hdjjsdj HdkdjdhNo ratings yet
- Ekinops PM - Lc4-Mp2-A: 400G Line Module For ETS Compact ChassisDocument2 pagesEkinops PM - Lc4-Mp2-A: 400G Line Module For ETS Compact ChassisBhargav SomepalliNo ratings yet
- Ch4. MSPPDocument6 pagesCh4. MSPPnibchandrapurNo ratings yet
- National Internet Backbone IIDocument13 pagesNational Internet Backbone IIAbhinav100% (10)
- Cisco - Pre .300-730.by .VCEplus.60q-DEMODocument33 pagesCisco - Pre .300-730.by .VCEplus.60q-DEMOPhúc HồngNo ratings yet
- CN Lab - Lesson Plan - 2023Document7 pagesCN Lab - Lesson Plan - 2023Suman PanditNo ratings yet
- Lab 04-Scanning2-ZenmapDocument11 pagesLab 04-Scanning2-ZenmapNguyen Chi Hoang MinhNo ratings yet
- Basic Networking Commands and ConceptsDocument9 pagesBasic Networking Commands and ConceptsKrishna NithariyaNo ratings yet
- 16740-Telephone System (IP Telephony)Document13 pages16740-Telephone System (IP Telephony)Ali SaifNo ratings yet
- EGX100 - Installation Guide PDFDocument2 pagesEGX100 - Installation Guide PDFRodolfoAntonioLeónCárdenasNo ratings yet
- How To Connect To iSCSI Targets On QNAP NAS Using MPIO On Windows 2008Document30 pagesHow To Connect To iSCSI Targets On QNAP NAS Using MPIO On Windows 2008Jazz OberoiNo ratings yet
- PERC RES EST 3Document6 pagesPERC RES EST 3Gab CruzNo ratings yet
- ASA Failover Troubleshooting On 7.x and 8Document5 pagesASA Failover Troubleshooting On 7.x and 8Akash ThakurNo ratings yet
- Routing and Switching Lab - 2019Document8 pagesRouting and Switching Lab - 2019Chinen momoNo ratings yet
- Brocade FastIron 07202 Config Guide Sx800-1600Document1,878 pagesBrocade FastIron 07202 Config Guide Sx800-1600sunrunners0% (1)
- Solution Ccna 2Document12 pagesSolution Ccna 2kalpNo ratings yet
- PERIODIC TEST in ICT-Grade 9 (Computer System Servicing)Document3 pagesPERIODIC TEST in ICT-Grade 9 (Computer System Servicing)Julius Ryan HipolitoNo ratings yet
- Comparative Study Waypoint The Evaluation: Random and Gauss-Markov Models Performance ofDocument6 pagesComparative Study Waypoint The Evaluation: Random and Gauss-Markov Models Performance ofGuru MekalaNo ratings yet
- Etsi TS 143 129 V6.13.0Document83 pagesEtsi TS 143 129 V6.13.0Patt ChaNo ratings yet
- Study Major Network ComponentsDocument9 pagesStudy Major Network ComponentsSandip MouryaNo ratings yet