Professional Documents
Culture Documents
How To Monitor and Track Failed Logins For Your AWS Managed Microsoft AD AWS Security Blog
Uploaded by
Mahesh SubramanianOriginal Title
Copyright
Available Formats
Share this document
Did you find this document useful?
Is this content inappropriate?
Report this DocumentCopyright:
Available Formats
How To Monitor and Track Failed Logins For Your AWS Managed Microsoft AD AWS Security Blog
Uploaded by
Mahesh SubramanianCopyright:
Available Formats
& '
Click here to return to Amazon Web Services homepag
Get Started for Free Contact Us
Blog Home Category ! Edition !
AWS Security Blog
How to monitor and track failed
logins for your AWS Managed
Microsoft AD
by Tekena Orugbani | on 02 JUL 2021 | in AWS Directory
Service, Intermediate (200), Security, Identity, & Compliance
| Permalink | " Share
AWS Directory Service for Microsoft Active Directory
provides customers with the ability to review security logs
on their AWS Managed Microsoft AD domain controllers by
either using a domain management Amazon Elastic
Compute Cloud (Amazon EC2) instance or by forwarding
domain controller security event logs to Amazon
CloudWatch Logs.
You can further improve visibility by monitoring Windows
login activities on your AWS Managed Microsoft AD domain-
joined EC2 instances, and in this blog post, I show you how.
Monitoring and tracking Windows security events on your
AWS Managed Microsoft AD domain-joined instances can
reveal unexpected activities on your domain-joined EC2
instances so that you can take proactive remediating action.
For example, every time there is an unsuccessful attempt to
log in to a domain-joined EC2 instance or on-premises
server by using an AWS Managed Microsoft AD user or a
local account, an “Audit Failure” Windows security event
with ID 4625 is recorded on the EC2 instance itself. The
event data includes details of the account name,
workstation name, and source network address.
Unsuccessful attempts to log in to non–domain-joined EC2
instances and servers are handled the same way. You can
track and monitor these events on an ongoing basis across
your fleet of Windows EC2 instances by using the solution
described here.
Solution overview
Figure 1 shows the workflow for the solution.
Figure 1: Solution architecture
The workflow steps are as follows:
1. An Amazon CloudWatch agent that is running on the
EC2 instances sends the Windows security event logs
to Amazon CloudWatch.
2. CloudWatch filters the logs based on the filter you
specify. When the configured threshold is met,
CloudWatch posts an alert to an SNS topic.
3. Amazon Simple Notification Service (Amazon SNS)
invokes an AWS Lambda function.
4. The Lambda function scans through the events and
determines which EC2 instance(s) generated the
security events at a frequency that satisfies the
configured threshold. It discards any other instances
listed in the events that don’t meet the specified
criteria. The function sends an email to the configured
email address with a high-level description of the
event logs and the instance(s) that generated them.
5. Amazon Simple Email Service (Amazon SES) delivers
the emails in the specified mailbox.
Note: Although this example uses email
notification via Amazon SES to monitor
failed logins, there are opportunities to
extend the solution. For example, you can
integrate with a Security Information and
Event Management (SIEM) tool that may
potentially be integrated with a ticketing
service and/or some automation or incident
response process when a set threshold for
failed logins is breached.
Prerequisites
Before you deploy the solution, you must complete the
following steps:
1. Create AWS Identity and Access Management (IAM)
roles for use with the CloudWatch agent
2. Sign up for Amazon SES
3. Verify the sender and recipient email addresses that
you’ll use to send and receive email notifications
Deploy the solution
The solution I present here involves four main steps:
1. Install and configure the CloudWatch agent for your
EC2 instances.
2. Create a metric filter in CloudWatch.
3. Create a CloudWatch alarm based on the metric filter
and add SNS notification.
4. Create a Lambda function and subscribe the function
to the SNS topic.
Step 1: Install and configure the CloudWatch
agent for all your EC2 instances
The first step is to create an AWS Systems Manager
parameter to contain the JSON configuration for the
CloudWatch agent that runs on the EC2 instances. You’ll
then use Systems Manager Run Command to install the
CloudWatch agent on the instances and to apply the
configuration in the Parameter Store to the CloudWatch
agent.
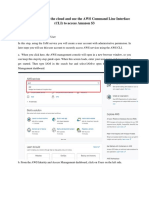
To install and configure the CloudWatch agent
1. Open the AWS Systems Manager console and in the
navigation pane, choose Parameter Store to create a
new Systems Manager parameter.
2. Give your parameter a name. In my example, I named
my parameter AmazonCloudWatch-Windows.
3. For Tier, choose Standard. For Type, choose String.
For Data type, choose Text.
4. For the value of the parameter, enter the following
JSON configuration and choose Create Parameter.
Note: This JSON configuration creates
a log group in CloudWatch with the
name /aws/SecurityAuditLogs. If
you would prefer to use another log
group name, you can modify the
JSON configuration. Also, if you
already have a Systems Manager
parameter named
AmazonCloudWatch-Windows, you
can use any other name of your
choice.
{ "logs": { "logs_collected": { "windows_
The Parameter details page should look similar to
the following.
Figure 2: Create the System Manager parameter for
the CloudWatch agent
5. Next, you’ll use Run Command to install and
configure the CloudWatch agent. In the navigation
pane, choose Run Command.
6. On the Run a command page, in the search box, enter
Document name prefix: Equals: AWS-
ConfigureAWSPackage. Press Enter and select the
document that appears.
7. Under Command parameters, for Name, enter
AmazonCloudWatchAgent.
Figure 3: Install the CloudWatch agent on the
instances
8. Under Targets, specify your EC2 instances based on
their tags, or choose them manually, and then choose
Run.
9. To configure the CloudWatch agent, choose Run
Command again. On the Run a command screen,
enter Document name prefix: Equals:
AmazonCloudWatch-ManageAgent. Press Enter and
select the document that appears.
10. Under Command parameters, for Optional
Configuration Location, enter the name of the
Systems Manager parameter you created earlier. In
my example, I used the name AmazonCloudWatch-
Windows. Keep the defaults for the other settings.
Figure 4: Configure the CloudWatch agent on the
instances
11. Under Targets, specify your EC2 instances based on
their tags, or choose them manually, and then choose
Run.
Step 2: Create a metric filter in CloudWatch
After the completion of the tasks in Step 1, your EC2
instances should now be sending logs to a log group in
Amazon CloudWatch called /aws/SecurityAuditLogs.
The log group should have log streams named after the EC2
instances that are sending the logs to CloudWatch. The next
step is to create a metric filter to filter the noise from the
logs.
To create a metric filter
1. Open the CloudWatch console and in the left
navigation menu, choose Log Groups.
2. Select the check box next to the
/aws/SecurityAuditLogs log group, choose
Actions, and then choose Create metric filter.
3. On the Define pattern page, enter Audit Failure,
keep the defaults for the other settings, and then
choose Next.
4. Enter values for Filter name, Metric namespace,
Metric name, and Metric value, and then choose Next
to create the metric filter.
Figure 5: Create a CloudWatch metric filter
Step 3: Create a CloudWatch alarm based on
the metric filter and add SNS notification
In this step, you set a threshold for how many “Audit
Failure” events you want to allow within a period of time
before triggering an alarm.
To create the CloudWatch alarm and add SNS
notification
1. Open the Amazon Simple Notification Service console
and in the left navigation menu, choose Topics.
2. Choose Create topic, and then choose Standard.
3. Provide a name for your topic, and then choose
Create topic. In my example, I named the topic
WindowsSecurityLogsAlarmNotifications.
4. Open the CloudWatch console, choose Log groups,
and select the /aws/SecurityAuditLogs log
group.
5. Choose the Metric filters tab, select the check box
next to the WindowsSecurityAuditFailures filter
you just created, and choose Create alarm.
6. On the Specify metric and conditions page, set the
parameters as follows:
a. For Statistic, choose Sample count.
b. For Period, choose 5 minutes.
c. For Threshold type, choose Static.
d. For Define the alarm condition, choose
Greater>threshold.
e. For Define the threshold value, specify the
threshold number of failed login attempts that
will cause a notification to be sent.
Note: In my example, I’ve
specified to be notified after
five failed login attempts. You
should determine the
appropriate threshold to use,
based on your organization’s
security policies.
Figure 6: Create a CloudWatch alarm
7. On the Configure actions page, choose Next.
8. Choose In alarm, choose Select an existing SNS
topic, and then select the SNS topic you created
earlier in this procedure.
9. Specify a name for the alarm, and then choose Create
Alarm.
Step 4: Create a Lambda function and
subscribe the function to the SNS topic
CloudWatch alarm messages are predefined, can’t be
modified, and don’t provide details based on CloudWatch
streams. Additionally, a CloudWatch alarm will trigger when
a combination of failed login attempts on two or more
instances meets the threshold. For instance, in my example,
when there are three failed attempts on one instance and
two failed attempts on a second instance all within a 5-
minute period, a CloudWatch alarm will be triggered.
The purpose of the Lambda function that you’ll create in
this step is to validate whether the triggered alarms meet
the specified threshold on a per-instance basis before the
function sends an email notification to the designated email
address. When a CloudWatch alarm is triggered, the
function reads through the CloudWatch logs and filters the
logs based on CloudWatch log streams that meet the
specified threshold for the alarm. If no individual
CloudWatch log stream (that is, no individual instance or
server) meets the threshold, the function won’t send a
notification. The function only sends a notification if it
determines that one or more instances have each met the
specified threshold. The function also provides more
information about the failed login attempts when it does
send you an email.
To create the Lambda function and subscribe it to
the SNS topic
1. Open the AWS Lambda console and choose Create
function.
2. Choose Author from scratch, and provide a name for
your function. Under Runtime, select Node.js 14.x,
and then choose Create function.
3. Double-click index.js, replace the code with the
following code, and then choose Deploy.
var aws = require('aws-sdk');
var cwl = new aws.CloudWatchLogs();
var ses = new aws.SES();
let alarmThreshold = process.env.ALARM_TH
exports.handler = function(event, context
var message = JSON.parse(event.Record
var alarmName = message.AlarmName;
var oldState = message.OldStateValue;
var newState = message.NewStateValue;
var reason = message.NewStateReason;
var requestParams = {
metricName: message.Trigger.Metri
metricNamespace: message.Trigger.
};
cwl.describeMetricFilters(requestPara
if(err) console.error('Error is:'
else {
console.log('Metric Filter da
4. Choose Add trigger, and in the drop-down list,
choose SNS.
5. Under SNS topic, select the SNS topic you created in
Step 3, and then choose Add.
Figure 7: Create the AWS Lambda function
6. Choose the Configuration tab, and then choose
Environment variables. Choose Edit to add the
environment variables for ALARM_THRESHOLD,
RECIPIENT_EMAIL, and SENDER_EMAIL, and then
choose Save.
Figure 8: The Lambda environment variables
Note: The variables’ keys must be set exactly
as ALARM_THRESHOLD, RECIPIENT_EMAIL,
and SENDER_EMAIL, because otherwise the
code will fail. For the recipient, you can
specify a single email or multiple email
addresses that are separated by commas, as
shown in Figure 8, provided that the emails
are verified as specified in the Prerequisites
section.
Next, create an IAM policy, which you’ll attach to a role that
will be assumed by the Lambda function. This policy
provides permissions to perform the
DescribeMetricFilters, FilterLogEvents, and
SendEmail API calls that are necessary for the function to
work. It also provides permissions to create a log group and
log stream in CloudWatch for the Lambda function, so that
you can review the logs if the Lambda function fails to run
properly.
To create the IAM policy
1. Sign in to the IAM console, and in the navigation bar,
choose Policies.
2. In the content pane, choose Create policy, and then
choose JSON.
3. Replace the content with the following script. Make
sure to replace the placeholders with the ARN of the
Lambda function, the ARNs for log group creation and
the ARN of your SES verified email address to use as
sender.
{
"Version": "2012-10-17",
"Statement": [
{
"Effect": "Allow",
"Action": "ses:SendEmail",
"Resource": "<arn-of-verified
},
{
"Effect": "Allow",
"Action": [
"logs:DescribeMetricFilte
],
"Resource": "<arn-for-CloudWa
},
{
"Effect": "Allow",
"Action": [
"logs:FilterLogEvents"
Here is how it appears in my example. Note that
FilterSendSecurityEvents is the name of my
Lambda function and /aws/SecurityAuditLogs is
the name my log group created in Step 1.
Figure 9: Example policy for the IAM role to be
attached to the Lambda function
4. Choose Review policy, specify a name and a
description for the policy, and then choose Create
policy.
Next, create an IAM role and attach this policy.
To create the IAM role and attach the policy
1. In the IAM console navigation bar, choose Roles, and
then choose Create role.
2. Under Choose the service that will use this role,
choose Lambda, and then choose Next: Permissions.
3. On the next page, select the policy you just created,
and then choose Next: Tags. Add an optional tag, and
then choose Next: Review.
4. Specify a name and description for the role, and then
choose Create role.
5. To attach this role to the Lambda function, go to the
AWS Lambda console. Navigate to the Lambda
function, and choose Configurations.
6. Choose Permissions, and then under Execution role,
choose Edit.
7. On the Edit basic settings page, under Existing role,
select the role you just created, and then choose Save.
And that’s it! You will now be notified whenever there are
“Audit Failure” events that reach the threshold you set on a
per-instance basis for your AWS Managed Microsoft AD
domain-joined instances. If you installed and configured the
CloudWatch agent on non–domain-joined instances in Step
1, then you’ll also get notifications for “Audit Failure” events
that are generated by failed login attempts that use local
accounts.
Conclusion
In this post, I showed you how you can proactively track and
monitor Windows security audit failures across your AWS
Managed Microsoft AD domain-joined EC2 instances. This
helps provide greater visibility into Windows login activities
for administrators, so that they can take action to maintain
the security of their server fleet. This solution can also be
extended to potentially trigger an automation workflow or
incident response process in the event of unexpected
events.
Although this blog has specifically targeted AWS Managed
Microsoft AD domain-joined instances, the procedure here
also applies to standalone EC2 instances or on-premises
servers that are configured to send logs to CloudWatch.
If you have feedback about this post, submit comments in
the Comments section below. If you have questions about
this post, start a new thread on the AWS Directory Service
forum or contact AWS Support.
Want more AWS Security how-to content, news, and
feature announcements? Follow us on Twitter.
Tekena Orugbani
Tekena is a Cloud Support Engineer at the
AWS Cape Town office. He has many years
of experience working with Windows Systems,
virtualization/cloud technologies, and directory
services. When he’s not helping customers make the
most of their cloud investments, he enjoys hanging out
with his family and watching Premier League football
(soccer).
TAGS: AWS Directory Service, Identity management,
Security Blog
AWS Podcast
Subscribe for weekly AWS news and interviews
Learn more #
AWS Partner Network
Find an APN member to support your cloud
business needs
Learn more #
AWS Training & Certifications
Free digital courses to help you develop your skills
Learn more #
Resources
AWS Cloud Security
AWS Compliance
AWS Security Reference Architecture
Best Practices
Data Protection at AWS
General Data Protection Regulation (GDPR)
Follow
$ Twitter
% Facebook
You might also like
- REST API DeploymentDocument10 pagesREST API DeploymentJesudass JamesNo ratings yet
- Agile Key With Answers-Consolidated PDF Scrum (Software Development) Agile Software DevelopmentDocument1 pageAgile Key With Answers-Consolidated PDF Scrum (Software Development) Agile Software DevelopmentReena DewanganNo ratings yet
- Launch A Linux Virtual MachineDocument16 pagesLaunch A Linux Virtual MachineVeerabhadra DurgamNo ratings yet
- Quantum Secure Direct CommunicationDocument24 pagesQuantum Secure Direct CommunicationAmogh GajaréNo ratings yet
- Lab 1: Introduction To Amazon EC2: Version 1.1.7 (spl200)Document16 pagesLab 1: Introduction To Amazon EC2: Version 1.1.7 (spl200)nguyensonvnpt0% (1)
- Amazon Web Services in Action, Third Edition: An in-depth guide to AWSFrom EverandAmazon Web Services in Action, Third Edition: An in-depth guide to AWSNo ratings yet
- AWS 20free 20labs 20 - 20lab 203 20 - 20EC2 20 - 20student 20instructions PDFDocument7 pagesAWS 20free 20labs 20 - 20lab 203 20 - 20EC2 20 - 20student 20instructions PDFlegendacNo ratings yet
- Create custom CloudWatch metricDocument7 pagesCreate custom CloudWatch metricPradeep KRNo ratings yet
- Creating An Amazon Virtual Private Cloud (VPC) With AWS Cloud FormationDocument18 pagesCreating An Amazon Virtual Private Cloud (VPC) With AWS Cloud Formationgoyal_86964227No ratings yet
- Modul 3 Creatae InstanceDocument11 pagesModul 3 Creatae Instanceardhya dwiNo ratings yet
- Microsoft Teams Developer Final AssesmentDocument2 pagesMicrosoft Teams Developer Final AssesmentAnkur Singh100% (1)
- Assignment 4 - Feb 11, 2024Document31 pagesAssignment 4 - Feb 11, 2024simran.sazanNo ratings yet
- ComputeDocument14 pagesCompute88awscloudNo ratings yet
- Te Comp 14 Exp03Document24 pagesTe Comp 14 Exp03Abhinav DesaiNo ratings yet
- EC@1Document13 pagesEC@1Magneto Eric Apollyon ThornNo ratings yet
- Ec 2Document9 pagesEc 2pratikNo ratings yet
- Create An AWS InstanceDocument8 pagesCreate An AWS InstancebirhanuNo ratings yet
- AWSDocument79 pagesAWSVandana GariaNo ratings yet
- Introduction To Amazon EC2Document15 pagesIntroduction To Amazon EC2Chaitanya SangaNo ratings yet
- What Is Amazon EC2Document6 pagesWhat Is Amazon EC2Rocky ArunnNo ratings yet
- Exercise 3 ComputeDocument5 pagesExercise 3 Computejeandanielflorestal70No ratings yet
- Cloud WatchDocument5 pagesCloud WatchTECHIE HORIZONNo ratings yet
- Amazon Elastic Compute Cloud: Getting Started Guide API Version 2012-12-01Document21 pagesAmazon Elastic Compute Cloud: Getting Started Guide API Version 2012-12-01dibpalNo ratings yet
- Amazon Elastic Compute Cloud: Getting Started Guide API Version 2012-07-20Document31 pagesAmazon Elastic Compute Cloud: Getting Started Guide API Version 2012-07-20ssiieu9586No ratings yet
- AWS Cloud WatchDocument14 pagesAWS Cloud Watchilyas2sapNo ratings yet
- AmazonElasticComputeCloud-Getting Started With EC2Document19 pagesAmazonElasticComputeCloud-Getting Started With EC2Konstantinos ChatziamallosNo ratings yet
- What Is Amazon EC2Document11 pagesWhat Is Amazon EC2Akhil ManglaNo ratings yet
- Shri Ramdeobaba College of Engineering and Management: Aradhita Menghal (04) Ketki Fadnavis (05) Shreyas NemaniDocument15 pagesShri Ramdeobaba College of Engineering and Management: Aradhita Menghal (04) Ketki Fadnavis (05) Shreyas NemaniShubham Manikant JhaNo ratings yet
- Amazon Elastic Compute Cloud: Guía de Primeros Pasos API Version 2012-04-01Document31 pagesAmazon Elastic Compute Cloud: Guía de Primeros Pasos API Version 2012-04-01Estrada CesarNo ratings yet
- Create AWS Instance, setup web restrictionDocument45 pagesCreate AWS Instance, setup web restrictionEurekia EvolutionNo ratings yet
- Amazon Elastic Compute Cloud: Getting Started Guide API Version 2011-12-15Document32 pagesAmazon Elastic Compute Cloud: Getting Started Guide API Version 2011-12-15Sohan KunkerkarNo ratings yet
- Amazon AWS Cloud Discovery Step by Step ConfigurationDocument3 pagesAmazon AWS Cloud Discovery Step by Step ConfigurationUsman AkbarNo ratings yet
- Lab 2 - Build A Web ServerDocument7 pagesLab 2 - Build A Web ServerHector AndradeNo ratings yet
- 6p Cloud ComputingDocument3 pages6p Cloud ComputingJohnNo ratings yet
- AWS LambdaDocument6 pagesAWS LambdaVishakha SinghNo ratings yet
- Install Dimension - Amazon EC2 - v1 3Document10 pagesInstall Dimension - Amazon EC2 - v1 3arthurcmnNo ratings yet
- CC Practical 1Document2 pagesCC Practical 1abhinavdeokar7No ratings yet
- Assignment CC 1Document8 pagesAssignment CC 1tahreem nazim0% (1)
- Amazon Elastic Compute Cloud: Getting Started Guide API Version 2011-01-01Document31 pagesAmazon Elastic Compute Cloud: Getting Started Guide API Version 2011-01-01William TovarNo ratings yet
- Lamp ServerDocument3 pagesLamp ServerJaveed AhamedNo ratings yet
- Get started with Amazon EC2Document18 pagesGet started with Amazon EC2Carlo SerioNo ratings yet
- AWS Discovery Day - Image Recognition HandoutDocument15 pagesAWS Discovery Day - Image Recognition HandoutDivya PrasoonaNo ratings yet
- cloud service management labDocument34 pagescloud service management labPrabha HaranNo ratings yet
- Amazon EC2Document16 pagesAmazon EC2jayNo ratings yet
- Exercise 2 IAMDocument5 pagesExercise 2 IAMjeandanielflorestal70No ratings yet
- Creating An Amazon Virtual Private Cloud (VPC) With AWS CloudFormationDocument15 pagesCreating An Amazon Virtual Private Cloud (VPC) With AWS CloudFormationChaitanya SangaNo ratings yet
- Create custom CloudWatch metricDocument7 pagesCreate custom CloudWatch metricPradeep KRNo ratings yet
- Create custom CloudWatch metricDocument7 pagesCreate custom CloudWatch metricPradeep KRNo ratings yet
- AWS C3 SCHOOLS-abDocument322 pagesAWS C3 SCHOOLS-abLachureNo ratings yet
- Connect 2 Car Things to IoT Core from Cloud9Document17 pagesConnect 2 Car Things to IoT Core from Cloud9Alexander ReyesNo ratings yet
- Create AWS EC2 Key PairDocument320 pagesCreate AWS EC2 Key Pairsrinubasani131No ratings yet
- Aws Lab1Document12 pagesAws Lab1Chengyi QuNo ratings yet
- CCL Exp 4Document16 pagesCCL Exp 4Harsh MendaparaNo ratings yet
- Create AWS EC2 Instance in 12 StepsDocument31 pagesCreate AWS EC2 Instance in 12 StepsAkhilesh SharmaNo ratings yet
- TASK SHEET 2 (1)Document21 pagesTASK SHEET 2 (1)Syed SalmanNo ratings yet
- Set up AWS Cloud9 dev environmentDocument15 pagesSet up AWS Cloud9 dev environmentsats phNo ratings yet
- Amazon GuardDutyDocument11 pagesAmazon GuardDutyChalermpanYenprasitNo ratings yet
- St. John College of Engineering and ManagementDocument3 pagesSt. John College of Engineering and ManagementHarsh MendaparaNo ratings yet
- 10901182021_TejasviSinghDocument43 pages10901182021_TejasviSinghrsb.122411No ratings yet
- Aws Tutorial 2Document7 pagesAws Tutorial 2Bommireddy RambabuNo ratings yet
- CC Assign10Document5 pagesCC Assign10113SOURYADIPTA DASNo ratings yet
- PracticalDocument8 pagesPracticalgaurav sharmaNo ratings yet
- What is AWS CloudWatchDocument5 pagesWhat is AWS CloudWatchBharathNo ratings yet
- Torrent ProjectDocument18 pagesTorrent ProjectRahulNo ratings yet
- 2N Easy Gate PRO User Guide en 1.4Document78 pages2N Easy Gate PRO User Guide en 1.4Sry SantosNo ratings yet
- Programming User RPLIn PCDocument26 pagesProgramming User RPLIn PCselm27No ratings yet
- Dynamic Segmentation Campus VXLAN EVPN Architecture GuideDocument20 pagesDynamic Segmentation Campus VXLAN EVPN Architecture Guideagirob1000No ratings yet
- Active Directory - Limit Concurrent User Logins - TechNet Articles - United States (English) - TechNet WikiDocument16 pagesActive Directory - Limit Concurrent User Logins - TechNet Articles - United States (English) - TechNet WikiVincent JubithanaNo ratings yet
- Security Advisory: TBOX-SA-2021-0007Document5 pagesSecurity Advisory: TBOX-SA-2021-0007edisonpcNo ratings yet
- 2016 Capacity Planner Training Certification and Registration Instructio...Document1 page2016 Capacity Planner Training Certification and Registration Instructio...vahoh94266No ratings yet
- Dcps Ae Administrators Guide enDocument114 pagesDcps Ae Administrators Guide enaymoz thierryNo ratings yet
- ECE241 MIDTERM BOOLEAN ALGEBRA AND GATESDocument2 pagesECE241 MIDTERM BOOLEAN ALGEBRA AND GATESNandini JayakumarNo ratings yet
- Benchmarking Cryptography and Stenography: Introduction To CrypotgraphyDocument21 pagesBenchmarking Cryptography and Stenography: Introduction To CrypotgraphyprofessionalwritersNo ratings yet
- Media and Information Literacy-Ws-5Document2 pagesMedia and Information Literacy-Ws-5Gabrelle OgayonNo ratings yet
- Assignment NoDocument2 pagesAssignment NozeshanNo ratings yet
- New Perspectives Microsoft Office 365 and Excel 2016 Comprehensive 1st Edition Parsons Solutions ManualDocument5 pagesNew Perspectives Microsoft Office 365 and Excel 2016 Comprehensive 1st Edition Parsons Solutions ManualSandraMurraykean100% (47)
- 1KHW001496ce Firmware Download For ETL600Document9 pages1KHW001496ce Firmware Download For ETL600Salvador FayssalNo ratings yet
- Describe Something Special You Want To Buy in The FutureDocument13 pagesDescribe Something Special You Want To Buy in The FutureĐẳng Nguyễn PhúcNo ratings yet
- Nu Soft Enod4t Eth e ManualDocument86 pagesNu Soft Enod4t Eth e ManualSurya TanjayaNo ratings yet
- Ieee Embedded 2022-23Document7 pagesIeee Embedded 2022-23Nexgen TechnologyNo ratings yet
- JK Bms Price ListDocument2 pagesJK Bms Price ListguamNo ratings yet
- Employee Leave Management System Project ReportDocument91 pagesEmployee Leave Management System Project Report007Ãrnav SinghaNo ratings yet
- 0417 w19 QP 13 PDFDocument16 pages0417 w19 QP 13 PDFRudraNo ratings yet
- Blue Futuristic Illustrative Artificial Intelligence Project PresentationDocument12 pagesBlue Futuristic Illustrative Artificial Intelligence Project PresentationGovind rajgorNo ratings yet
- Calculating Density and Cylinder PropertiesDocument4 pagesCalculating Density and Cylinder PropertiesKhawla AlameriNo ratings yet
- Aspire U5610Document71 pagesAspire U5610Predescu VasileNo ratings yet
- Heloel Hernandez - PythonDocument2 pagesHeloel Hernandez - PythonHeloel HernándezNo ratings yet
- QTL Mapping in Biparental Genetic Populations (BIP) : 1. Open The SoftwareDocument16 pagesQTL Mapping in Biparental Genetic Populations (BIP) : 1. Open The SoftwareEmilie GuilloteauNo ratings yet
- 01-Terminologi IC DigitalDocument15 pages01-Terminologi IC DigitalDonaDoniAntoniNo ratings yet
- Network DiagramDocument33 pagesNetwork DiagramRanjana Priya100% (1)