Professional Documents
Culture Documents
MSURJ Volume IV - Article 7
Uploaded by
Grado ZeroOriginal Description:
Original Title
Copyright
Available Formats
Share this document
Did you find this document useful?
Is this content inappropriate?
Report this DocumentCopyright:
Available Formats
MSURJ Volume IV - Article 7
Uploaded by
Grado ZeroCopyright:
Available Formats
The Evolution of Algorithms to find Prime Numbers
Maya Kaczorowski
Department of Mathematics and Statistics, McGill University, Burnside Hall, 1005 805, Sherbrooke Street West, Montreal, Quebec, Canada, H3A 2K6
Received: January 4, 2009 - Accepted: February 5, 2009
Prime numbers are what is left when you have taken all the patterns away. I think
prime numbers are like life. They are very logical but you could never work out
the rules, even if you spent all your time thinking about them.
- Mark Haddon, The Curious Incident of the Dog in the Night-time
Introduction the first 10 integers, 40% are prime; among the first 100, 1 in 4
Prime numbers, and the deterministic formulas used to find them, is prime. This pattern continues, such that in the first 100,000
have garnered considerable attention from mathematicians, pro- integers, 1 in 10.4 is prime (Peterson, 1996). In fact, Gauss wrote
fessionals and amateurs alike. A prime number is a positive integer, that “this frequency is on the average inversely proportional to
excluding 1, whose only divisors are 1 and itself. For example, 23 is the [natural] logarithm” (Tschinkel, 2006), so the approximate
a prime number as it can only be divided by 1 and 23. A number number of primes below a number n follows Equation(1):
that is not prime is called a composite number.
While prime numbers under 100 are fairly abundant,
they become less frequent and difficult to find in a systematic
manner as the digits in the number increase since they do not
Equation 1: Gauss’ equation of the distribution of prime numbers
appear to follow a predictable distribution. So why do resear-
chers keep studying them? For over 150 years, mathematicians
have attempted to uncover a deterministic formula to identify The French mathematician Adrien Marie Legendre inde-
prime numbers. If such a formula existed, all numbers could pendently developed a similar equation just a few years la-
be factored relatively quickly using computers. Paradoxically, ter. The result is known as the Prime Number Theorem, which
much of electronic data today is encrypted by taking advanta- while giving no definitive equation to find prime numbers, pro-
ge of the fact that it is difficult and time consuming for a com- vides an approximation of the distance between prime num-
puter program to factor a large composite number. A formula bers within any given interval. In fact, it states that the average
to find all prime numbers would be a significant breakthrough distance between two consecutive primes near some number
in mathematics, but severely detrimental to data security. n is close to the natural logarithm of n (Peterson, 1996). For
example, since ln(1000)=6.91, near 1000, approximately every
A simple algorithm to find prime numbers: seventh number should be prime.
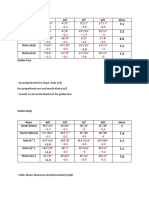
The Sieve of Eratosthenes As the density of prime numbers decreases, it might be ex-
As early as 200 BCE, in their efforts to determine the first few pected that eventually prime numbers get so scarce that there
prime numbers, Greek mathematicians developed an algo- exists a single largest prime number. However, the infinitude
rithm requiring relatively easy calculations. All integer numbers of prime numbers has been known since 300 BCE when it was
greater than 1 can be uniquely factored as a product of prime established in Euclid’s Elements. Euclid’s proof hinges on the
numbers; this is the Fundamental Theorem of Arithmetic (An- Fundamental Theorem of Arithmetic: if there is a single largest
drews, 1994). Consequently, it is a corollary that any composite prime number, there would be a finite set of prime numbers.
number must have at least one factor smaller than or equal to This theorem implies that all composite numbers could then
its square root. For example, consider the factorization of 118: be factored into these prime numbers. However, Euclid found a
118=2•59, and the factor 2 is less than 10.86=√118. number that could not be divided by any of these prime num-
Since all composite numbers have prime factors smaller bers, thus necessitating the existence of another prime num-
than or equal to their square roots, it follows that prime num- ber (Ore, 1988). By induction, prime numbers are thus infinite.
bers, which cannot be factored, do not. This idea prompted the For a concise proof and examples, see Figure 2.
Ancient Greek mathematician Eratosthenes to conceive of the Despite providing insight into the distribution of prime num-
Sieve of Eratosthenes to find small prime numbers (Ore, 1988). bers over the real number line, the Prime Number Theorem did not
In order to find prime numbers less than 100, for instance, Era- contribute to creating a definitive formula to find prime numbers.
tosthenes would remove all factors of 2; then all factors of 3;
then since 4 is not a prime, having already been removed as Finding a faster algorithm: Euler's formula, the Riemann
factors of 2, remove all factors of 5; etc. as seen in Figure 1. hypothesis, and a polynomial-time algorithm
The Sieve of Eratosthenes is an example of a deterministic Although the Sieve of Eratosthenes is a foolproof method to find prime
algorithm used to unearth all prime numbers, but is only prac- numbers, this primitive algorithm is very time consuming, and mathe-
tical for “small” prime numbers, those less than 10,000,000 (Ore, maticians have devoted their efforts to finding a faster method.
1988). Beyond that boundary, it is too resource-consuming for Leonhard Euler spent many years working on a deterministic
a computer to perform such a calculation. formula for finding prime numbers and eventually developed the
equation seen in Equation 2. However, this equation only works
The sporadic, but never-ending, primes: for restricted inputs and does not determine consecutive prime
the Prime Number Theorem and the Infinity of Primes numbers, meaning that its use as a test of primality is limited.
Even though the Sieve of Eratosthenes offers an effective
algorithm for finding small prime numbers, it gives little insight
into the distribution of prime numbers. Carl Friedrich Gauss
was the first to notice the only clear distributive property of
prime numbers: they get scarcer as numbers get larger. Among Equation 2: Euler’s prime generating function
36 MSURJ • Volume 4, Issue 1
Maya Kaczorowski
Figure 1: The Sieve of Eratosthenes Figure 1: The Riemann-Zeta function
The use of prime numbers in Cryptography and the conse-
quences of a deterministic formula for finding prime numbers
Cryptography, the science of encrypting and decrypting mes-
sages for transmission between a sender and an intended re-
cipient, may at first glance seem unrelated to the discovery of
prime numbers. Beginning in Roman times, information was
frequently encrypted using a private-key, meaning that the
sender and the recipient had to define a decryption codec that
would allow the recipient to decode the message. This practice
became impractical as technology evolved, since there was of-
ten no secure way to communicate the private-key, especially
Figure 2: Short proof of the infinitude of prime numbers
over considerable distances. To deal with these challenges,
public-key cryptography was developed. Presently, the most
Euler also developed the zeta function, relating a sum common encryption methods in use rely on the difficulty of
of fractions to a product of prime numbers, shown in Figure efficiently finding prime numbers.
3. Bernhard Riemann extended it into what is now known Whereas prime numbers are known up to several thou-
as the Riemann Zeta function (Ivic, 2003). In 1859 Riemann sands of digits, it is much harder to factor composite numbers
published his results and hypothesized that a function that with several thousands of digits, especially if they are com-
has a zero root uniquely defines a prime number. Recently, posed of large prime numbers; a deterministic exponential
in 2004, Gourdon and Sebah verified the Riemann hypothe- time algorithm could take centuries to factor the composite
sis for the first 10 trillion zeroes (Crandall and Pomerance, number. This is the basis of public-key cryptography using
2005); nevertheless, the hypothesis remains unproven. the RSA encryption method created in 1978 by Rivest, Shamir
The discovery of prime numbers is simplified by com- and Adleman. Two large prime numbers p and q decide a lar-
puter programs, where the main challenge is finding a more ge composite number N=pq as well as the encryption key e
rapid algorithm. Computer algorithms are usually compa- using an equation. From p, q and e, the decryption key d is de-
red using runtime analysis, which determines the worse termined by the same equation. An individual who wants to
case runtime given an input of length n. The runtime of a receive information securely makes public N and e, allowing
program is a function of the length of the input, and can be anyone to send them the information. If the information is
a polynomial, logarithmic or exponential equation. As the intercepted, then knowledge of d, which can only be deter-
input size increases, an exponential runtime will always be mined if p, q and e are known, is required for decryption. This
longer than a polynomial runtime, which in turn will be lon- means that in order to decrypt the intercepted information,
ger than a logarithmic runtime. the individual, who only knows N and e, must factor N back
The Sieve of Eratosthenes is an exponential algorithm to into p and q, which is a restrictively time consuming process.
find prime numbers, which renders it ineffective in finding On the other hand, if prime numbers could be found quic-
exceptionally large prime numbers. Since Eratosthenes, all kly, then composite numbers could be factored much more
deterministic algorithms to find primes have been exponen- swiftly, and the RSA method would fail, rendering electronic
tial, so it was remarkable when a relatively simple determi- public-key encryption insecure.
nistic polynomial algorithm was finally discovered in 2002 by A similar threat to secure encryption is quantum computing,
Agrawal, Kayal and Saxena (AKS). The AKS algorithm, based which is based on the principle that quantum properties could
on Fermat’s Little Theorem and other proven mathematical be used to represent data and perform operations as a traditional
assumptions, is an improvement but may still have an extre- computer does. If quantum computing evolves beyond the experi-
mely long runtime, rendering it impractical. The search for an mental stages where it currently is, it presents the possibility of per-
expeditious yet deterministic formula to find prime numbers forming computations in record time. The same algorithms could
is still underway, and there is no doubt that computers will be used, but would be executed much faster. For example, while it
continue to provide mathematicians with the ability to make may take centuries to break an RSA code using a traditional compu-
further improvements. ter, a quantum computer could take just seconds or minutes.
March 2009 • msurj.mcgill.ca 37
The Evolution of Algorithms to find Prime Numbers
Conclusion 3. Crandall, R. E. and Pomerance, C. 2005. Prime Numbers.
The field of prime numbers is ever changing, with new prime New York, NY: Springer.
numbers discovered every few years. Early mathematicians
dealt with the distribution and infinitude of prime numbers, 4. Haddon, M. 2003. The Curious Incident of the Dog in the
whereas modern mathematicians aspire to find a determi- Night-time. London: Vintage Random House.
nistic formula to identify all prime numbers. Algorithms that
quickly generate small prime numbers already exist, and the 5. Ivic, A. 2003. The Riemann Zeta-Function. Mineola, NY:
recent AKS polynomial time algorithm will even allow large Courier Dover Publications.
prime numbers to be found quickly. Although finding prime
numbers with ease would be a seminal accomplishment in 6. Ore, O. 1988. Number Theory and Its History. Mineola,
mathematics, it would also create new challenges for the NY: Courier Dover Publications.
safety of electronic data encryption. Are the benefits of a
deterministic prime generator to mathematics worth the 7. Peterson, I. 1996. Prime Theorem of the Century. Math-
destruction of the most common form of data encryption in Trek, 1 (41). December
computer science? Only time will tell.
8. 14, 2008. http://www.maa.org/mathland/mathland_12_23.html
References
9. Rivest, R.L. Shamir, A. Adleman, L. 1978. A Method for Ob-
1. Agrawal. Manindra. Kayal. Neeraj. Saxena. Nitin. taining Digital Signatures and Public-Key Cryptosystems.
2004. PRIMES is in P. Annals of Mathematics 160: Communications of the ACM 21(2):120-126.
781-793.
10. Tschinkel, Y. 2006. About the cover: On the distribution
2. Andrews, G. E. 1994. Number Theory. Mineola, NY: Cou- of primes – Gauss’ tables. Bulletin of the American Ma-
rier Dover Publications. thematical Society 43:89-91.
38 MSURJ • Volume 4, Issue 1
You might also like
- Prime NumberDocument1 pagePrime NumberRaghavendra RaghavNo ratings yet
- Prime Numbers and Cryptography: A L A PDocument8 pagesPrime Numbers and Cryptography: A L A PEsteban BelboNo ratings yet
- Prime Numbers - TRMsDocument5 pagesPrime Numbers - TRMsAkalatronic TunezNo ratings yet
- The Skeleton Key of Mathematics: A Simple Account of Complex Algebraic TheoriesFrom EverandThe Skeleton Key of Mathematics: A Simple Account of Complex Algebraic TheoriesNo ratings yet
- CNS LA-2 Report (044,035,153,114)Document12 pagesCNS LA-2 Report (044,035,153,114)AC AviShekNo ratings yet
- Riemann Hypothesis and Its Impact On RSADocument11 pagesRiemann Hypothesis and Its Impact On RSAluciolangtryNo ratings yet
- Number TheoryDocument10 pagesNumber TheoryabhijeetNo ratings yet
- Prime NumberDocument1 pagePrime NumberGodo 365No ratings yet
- Calder BankDocument7 pagesCalder BankedinNo ratings yet
- Structure and Randomness in The Prime Numbers: Terence TaoDocument17 pagesStructure and Randomness in The Prime Numbers: Terence TaoLázaro AlbuquerqueNo ratings yet
- Gold Prime NumberDocument197 pagesGold Prime NumberOdesola SamuelNo ratings yet
- Introduction To Natural Numbers and Real Numbers PDFDocument25 pagesIntroduction To Natural Numbers and Real Numbers PDFOmar FrancoNo ratings yet
- Prime NumbersDocument1 pagePrime NumbersMisa PerisicNo ratings yet
- RSA LecDocument36 pagesRSA LecInshal AyazNo ratings yet
- Module 1Document11 pagesModule 1Arcel CampusNo ratings yet
- Irish Math. Soc. Bulletin Number 76, Winter 2015, 79-81 ISSN 0791-5578Document3 pagesIrish Math. Soc. Bulletin Number 76, Winter 2015, 79-81 ISSN 0791-5578How to do anything By HimanshuNo ratings yet
- Assignment 6 Adv. Thermo (002, 025)Document3 pagesAssignment 6 Adv. Thermo (002, 025)divyaNo ratings yet
- Cryptographic PrimitivesDocument59 pagesCryptographic Primitivesposer4uNo ratings yet
- Primes, Quantum Chaos, and Computers: A. M. OdlyzkoDocument21 pagesPrimes, Quantum Chaos, and Computers: A. M. OdlyzkoptrrssllNo ratings yet
- HakimrasullmuhammadDocument15 pagesHakimrasullmuhammadBrikhov XNo ratings yet
- Graduate Examination: Department of Computer Science The University of Arizona Spring 2003Document15 pagesGraduate Examination: Department of Computer Science The University of Arizona Spring 2003Aditya MishraNo ratings yet
- Mazur Barry Prime Numbers and The Riemanns Hypothesis PDFDocument153 pagesMazur Barry Prime Numbers and The Riemanns Hypothesis PDFjangojangoNo ratings yet
- Crypto PrimerDocument28 pagesCrypto PrimerMohd Hanif HassanNo ratings yet
- Cryptography and Network Security Self-Study: Submitted byDocument28 pagesCryptography and Network Security Self-Study: Submitted byHarryNo ratings yet
- PrimenumbersDocument6 pagesPrimenumbersMuharem MušićNo ratings yet
- The Mathematics of The RSA Public-Key CryptosystemDocument11 pagesThe Mathematics of The RSA Public-Key CryptosystemAlla HoumourNo ratings yet
- Secrets of Number Theoretic Tools in Network Security Algorithms of Public-Key CryptosystemsDocument25 pagesSecrets of Number Theoretic Tools in Network Security Algorithms of Public-Key CryptosystemsVijay AnandNo ratings yet
- Methods of Primality TestingDocument10 pagesMethods of Primality TestingimnomusNo ratings yet
- Estimating The Probability of Primes With in A Finite Integral Domain in Higher Order RangeDocument8 pagesEstimating The Probability of Primes With in A Finite Integral Domain in Higher Order RangeInternational Journal of Innovative Science and Research TechnologyNo ratings yet
- Primitive Weird Numbers Having More Than Three Distinct Prime FactorsDocument6 pagesPrimitive Weird Numbers Having More Than Three Distinct Prime FactorsPILBNo ratings yet
- Science of Computer Programming: Roland Backhouse, João F. FerreiraDocument21 pagesScience of Computer Programming: Roland Backhouse, João F. FerreiraELOK YULIA FAIKOHNo ratings yet
- Primes in Tuples I-0508185v1Document36 pagesPrimes in Tuples I-0508185v1Fabiano FerreiraNo ratings yet
- About Prime NumbersDocument21 pagesAbout Prime NumbersMeliza AdvinculaNo ratings yet
- History of Prime NumbersDocument4 pagesHistory of Prime NumberssubhaNo ratings yet
- An Introduction To The Mathematics of Digital Signal Processing - Part I - Algebra, Trigonometry, and The Most Beautiful Formula in MathematicsDocument11 pagesAn Introduction To The Mathematics of Digital Signal Processing - Part I - Algebra, Trigonometry, and The Most Beautiful Formula in MathematicsAlfredo ÁlvarezNo ratings yet
- It Is Easy To Determine Whether A Given Integer Is PrimeDocument36 pagesIt Is Easy To Determine Whether A Given Integer Is PrimebluedremzNo ratings yet
- 1 49Document49 pages1 49Ethel Kris AntonioNo ratings yet
- 12 PDFDocument34 pages12 PDFaarushiNo ratings yet
- Biteranta NumtheoryDocument10 pagesBiteranta Numtheoryapi-619829083No ratings yet
- Toward The Unification of Physics2 1 PDFDocument55 pagesToward The Unification of Physics2 1 PDFFulanito de TalNo ratings yet
- Cryptic Primes: Generating Prime NumbersDocument3 pagesCryptic Primes: Generating Prime NumbersMed Amjed RezguiNo ratings yet
- 2206 14775Document8 pages2206 14775Marcelo Marcy Majstruk CimilloNo ratings yet
- Clark W Edwin Elementary Number TheoryDocument129 pagesClark W Edwin Elementary Number TheoryDireshan Pillay100% (1)
- MathIlluminated 02 TXT PDFDocument57 pagesMathIlluminated 02 TXT PDFashisNo ratings yet
- Algoritmo de Shor - Sistema RSADocument6 pagesAlgoritmo de Shor - Sistema RSAJailson F. LeiteNo ratings yet
- Pre Print 4Document2 pagesPre Print 4shivana_shivaNo ratings yet
- Ccs Unit III NotesDocument22 pagesCcs Unit III NotesVasantha Kumar VNo ratings yet
- RSA Algorithm CS13Document6 pagesRSA Algorithm CS13api-3730515100% (1)
- Sma 205 Pages 59 To 65Document7 pagesSma 205 Pages 59 To 65Sounak SadhukhanNo ratings yet
- Perfect Number in Number Theory (Perfect Numbers, Fermat)Document11 pagesPerfect Number in Number Theory (Perfect Numbers, Fermat)Conwi John Ken Hudson T.No ratings yet
- Sieve PDFDocument97 pagesSieve PDFemilioNo ratings yet
- Analytic Number TheoryDocument8 pagesAnalytic Number TheoryaoajvxazzjxohenwmrNo ratings yet
- Cdrom PDF CryptoDocument4 pagesCdrom PDF CryptoalexNo ratings yet
- On Random and Hard-to-Describe Numbers: IBM Watson Research Center Yorktown Heights, NY 10598, USADocument8 pagesOn Random and Hard-to-Describe Numbers: IBM Watson Research Center Yorktown Heights, NY 10598, USATiasa MondolNo ratings yet
- Obtencion de MasaDocument58 pagesObtencion de MasaRamdul GonzalezNo ratings yet
- FundamentalDocument28 pagesFundamentalomsaiboggala811No ratings yet
- Tale of Two SievesDocument13 pagesTale of Two SievesMark MarkesonNo ratings yet
- Staircase Functions, Spectral Rigidity, and A Rule For Quantizing ChaosDocument10 pagesStaircase Functions, Spectral Rigidity, and A Rule For Quantizing ChaosGrado ZeroNo ratings yet
- Bond A61 Million Person 2012aDocument5 pagesBond A61 Million Person 2012aGrado ZeroNo ratings yet
- Montagnier - Waves, WaterDocument11 pagesMontagnier - Waves, WaterGrado ZeroNo ratings yet
- Max MSP FiltersDocument4 pagesMax MSP FiltersGrado ZeroNo ratings yet
- Csound in Maxmsp: FLOSS ManualsDocument7 pagesCsound in Maxmsp: FLOSS ManualsGrado ZeroNo ratings yet
- Symbolic MusicDocument165 pagesSymbolic MusicGrado ZeroNo ratings yet
- Structuring JSON Data With The (Dict) Object in Max. - × - C o MDocument1 pageStructuring JSON Data With The (Dict) Object in Max. - × - C o MGrado ZeroNo ratings yet
- Digital Sound Generation 2Document46 pagesDigital Sound Generation 2Grado ZeroNo ratings yet
- Bourrée in E Minor: Lute or Lute-Harpischord (Lautenwerk)Document1 pageBourrée in E Minor: Lute or Lute-Harpischord (Lautenwerk)Grado ZeroNo ratings yet
- Z LevelMQP (Set1) PDFDocument1 pageZ LevelMQP (Set1) PDFRekha ThakareNo ratings yet
- NHB Quantitative Aptitude Old Paper PDFDocument5 pagesNHB Quantitative Aptitude Old Paper PDFJogen LoharNo ratings yet
- Business Maths - BBA 1yr - Unit 1Document107 pagesBusiness Maths - BBA 1yr - Unit 1ADISH JAINNo ratings yet
- G4 Decimals #1Document2 pagesG4 Decimals #1Simply SaltNo ratings yet
- LET Math Final HandoutDocument9 pagesLET Math Final HandoutCarla Naural-citeb86% (7)
- Golden Ratio MathDocument2 pagesGolden Ratio MathKhaina AustriaNo ratings yet
- Paper D - 2020Document7 pagesPaper D - 2020ridderNo ratings yet
- Unit 1 TestDocument3 pagesUnit 1 TestAKASH MNo ratings yet
- Grade6 Fractions Addition and Subtraction PDFDocument12 pagesGrade6 Fractions Addition and Subtraction PDFEduGainNo ratings yet
- 4 Let Arithmetic - pdf9Document9 pages4 Let Arithmetic - pdf9novey_casio50% (2)
- ACFrOgB - pBMhSbJKvRodjD9tdnEa7SKfOKZD TlrYz66t 3fIaPdM1mTNIsEQ761eafv9Dhr 93ywIMyyXlXv3Bojeb - GNWh5EVx iXCgFd89OPP4WvYntZ3F46 VLz9uLJBt1sJLlvWxh7GXFCCDocument14 pagesACFrOgB - pBMhSbJKvRodjD9tdnEa7SKfOKZD TlrYz66t 3fIaPdM1mTNIsEQ761eafv9Dhr 93ywIMyyXlXv3Bojeb - GNWh5EVx iXCgFd89OPP4WvYntZ3F46 VLz9uLJBt1sJLlvWxh7GXFCCWaqas AkmalNo ratings yet
- Itl Public School Sector - 9, Dwarka: SESSION 2014 - 2015Document3 pagesItl Public School Sector - 9, Dwarka: SESSION 2014 - 2015ik62299No ratings yet
- Units and Measurements Lec-07 Physics Shyam Sir 06AN21EDocument24 pagesUnits and Measurements Lec-07 Physics Shyam Sir 06AN21EsymphonybugNo ratings yet
- Important-Question-Class-8-Maths-Chapter-6 Cubes and Cube RootsDocument6 pagesImportant-Question-Class-8-Maths-Chapter-6 Cubes and Cube Rootsnirmal krisnaNo ratings yet
- Grade 4 Mathematics FinalDocument103 pagesGrade 4 Mathematics FinalAL Jeff Puguon100% (9)
- Chapterd 5 C SolutionsDocument57 pagesChapterd 5 C SolutionsazharjavedNo ratings yet
- SSC MTS 2020 - LCM HCFDocument5 pagesSSC MTS 2020 - LCM HCFlakshmi dileepNo ratings yet
- Primary Mathematics Scheme of Work: Stage 4Document17 pagesPrimary Mathematics Scheme of Work: Stage 4DanielleNo ratings yet
- Measures of Central Tendency & Location WorksheetsDocument11 pagesMeasures of Central Tendency & Location WorksheetsAngelica AlejandroNo ratings yet
- @StudyPivot Plancess Maths 11 PDFDocument1,192 pages@StudyPivot Plancess Maths 11 PDFJatin SinglaNo ratings yet
- Fractions and Decimals: ©ncert Not To Be RepublishedDocument28 pagesFractions and Decimals: ©ncert Not To Be Republishedrekshana100% (1)
- Experiment-11 BCD Code To 7-Segment Decoder 11-1 ObjectDocument3 pagesExperiment-11 BCD Code To 7-Segment Decoder 11-1 ObjectMohammed Dyhia AliNo ratings yet
- DTE Unit 1 Part 2Document3 pagesDTE Unit 1 Part 2John TefaneNo ratings yet
- Solving Real Life Situation ProblemsDocument11 pagesSolving Real Life Situation ProblemsSVÁNN YouTubeNo ratings yet
- % Class 5Document9 pages% Class 5Vaishali GargNo ratings yet
- Multiplying Mixed Numbers: Grade 5 Fractions WorksheetDocument2 pagesMultiplying Mixed Numbers: Grade 5 Fractions WorksheetshilpaNo ratings yet
- Course Name: Digital Electronics Course Code: U18Esec303 Topic: Number SystemsDocument36 pagesCourse Name: Digital Electronics Course Code: U18Esec303 Topic: Number SystemsPriyanka ShanmugamNo ratings yet
- Basic Concept of MathematicsDocument15 pagesBasic Concept of MathematicsAbdul SamiNo ratings yet
- แนวข้อสอบเข้า ม.4 ชุดที่ 1Document8 pagesแนวข้อสอบเข้า ม.4 ชุดที่ 1อลงกรณ์ แซ่ตั้งNo ratings yet
- Genmath q1 Mod2 Evaluatingfunctions v2Document27 pagesGenmath q1 Mod2 Evaluatingfunctions v2Jomark RebolledoNo ratings yet
- Basic Math & Pre-Algebra Workbook For Dummies with Online PracticeFrom EverandBasic Math & Pre-Algebra Workbook For Dummies with Online PracticeRating: 4 out of 5 stars4/5 (2)
- Quantum Physics: A Beginners Guide to How Quantum Physics Affects Everything around UsFrom EverandQuantum Physics: A Beginners Guide to How Quantum Physics Affects Everything around UsRating: 4.5 out of 5 stars4.5/5 (3)
- A-level Maths Revision: Cheeky Revision ShortcutsFrom EverandA-level Maths Revision: Cheeky Revision ShortcutsRating: 3.5 out of 5 stars3.5/5 (8)
- Limitless Mind: Learn, Lead, and Live Without BarriersFrom EverandLimitless Mind: Learn, Lead, and Live Without BarriersRating: 4 out of 5 stars4/5 (6)
- HP Prime Guide Algebra Fundamentals: HP Prime Revealed and ExtendedFrom EverandHP Prime Guide Algebra Fundamentals: HP Prime Revealed and ExtendedNo ratings yet
- Calculus Made Easy: Being a Very-Simplest Introduction to Those Beautiful Methods of Reckoning Which are Generally Called by the Terrifying Names of the Differential Calculus and the Integral CalculusFrom EverandCalculus Made Easy: Being a Very-Simplest Introduction to Those Beautiful Methods of Reckoning Which are Generally Called by the Terrifying Names of the Differential Calculus and the Integral CalculusRating: 4.5 out of 5 stars4.5/5 (2)
- Teaching STEM in the Early Years: Activities for Integrating Science, Technology, Engineering, and MathematicsFrom EverandTeaching STEM in the Early Years: Activities for Integrating Science, Technology, Engineering, and MathematicsRating: 3.5 out of 5 stars3.5/5 (5)
- Build a Mathematical Mind - Even If You Think You Can't Have One: Become a Pattern Detective. Boost Your Critical and Logical Thinking Skills.From EverandBuild a Mathematical Mind - Even If You Think You Can't Have One: Become a Pattern Detective. Boost Your Critical and Logical Thinking Skills.Rating: 5 out of 5 stars5/5 (1)