Professional Documents
Culture Documents
5 Types of Cyber Criminals and How To Protect Against Them Travelers Insurance
Uploaded by
Hamidah Che Abdul HamidOriginal Title
Copyright
Available Formats
Share this document
Did you find this document useful?
Is this content inappropriate?
Report this DocumentCopyright:
Available Formats
5 Types of Cyber Criminals and How To Protect Against Them Travelers Insurance
Uploaded by
Hamidah Che Abdul HamidCopyright:
Available Formats
ABOUT CAREERS AGENTS INVESTORS SUSTAINABILIT Y CONTACT US
LOG IN
For Individuals For Business Claim Center Prepare & Prevent
! Types of Cyber Criminals and How to Protect Against Top Stories
Them ;Video=
5 Types of Cyber Criminals
Share
HowYs Your Cyber Knowledge? ;Tool=
Take this short cyber IQ quiz to see if you can
talk the talk.
Take the quiz
Related Content
Watch on Cyber Terms 101
Are You Prepared for Cyber Risks? Download
Understanding the types of cyber criminals and their techniques can help protect your organization the Cyber Guide
from a data breach. Here are some common threats and steps a business can take. Developing a Data Breach Incident Response
Plan [Video]
#? The Social Engineer
Cyber criminals pretending to be someone else can trick unsuspecting employees to compromise
data. In one scenario, a spoof email purporting to be from the CEO of the company directs an Related Products & Services
employee to send a PDF with employees’ 1099 tax forms for an upcoming meeting with the Internal
Revenue Service. The social engineer is able to capture Personally Identifiable Information (PII). Travelers Pre[Breach Services
provided by Symantec™
“We often see people making mistakes like this,” says Jennifer Coughlin, a partner at Mullen Coughlin
LLC, a data breach law firm that works with Travelers Insurance. “Encourage employees to make a Better together when it comes to cyber
phone call and speak to the person, instead of leaving a voicemail – to verify all requests for sensitive, protection.
confidential, or protected information and financial information before they reply with the requested
information. Employees should also ensure the “Reply To” address is, in fact, the email address of the
requesting employee, and send this type of information via an encrypted email message.” Beware
time-sensitive requests, as social engineers sometimes use a sense of urgency to compel victims CyberRisk for Multiple Industries and
into unsafe behavior. Business Sizes
#B The Spear Phisher Broad cyber liability coverage customized to
fit the needs of small businesses to Fortune
Social threats factored into just under one-third of confirmed data breaches, with phishing the tactic 500 companies and every organization in
used in 92 percent of social-related attacks.1 An email can appear to be from a legitimate sender, but between.
actually contain a malicious attachment or link that can give spear phishers access to banking
credentials, trade secrets and other information that they are able to access.
“Companies can have employee training that both prepares and tests employees to recognize and View More Cyber Insurance Options
respond to malicious phishing attempts,” says Tim Francis, Travelers Enterprise Cyber Lead. If a
phishing attempt is successful, having the proper security in place provides another line of defense:
protecting the rest of your network by segmenting the network and implementing strong
Need an Agent?
authentication between the network and important data.
#C The Hacker ZIP Code Find an Agent
Nearly two-thirds of confirmed data breaches involved leveraging weak, default or stolen passwords.2
Malware poses a serious threat, as it can capture keystrokes from an infected device even if
employees use strong passwords with special characters and a combination of upper- and lower- See All Cyber Content
case letters.
Still, strong passwords are the first line of defense against hackers, according to Tim Francis. “Use
multi-factor authentication, enforce strong password requirements, patch operating systems,
software and apps, and increase redundancy and bandwidth,” Francis says.
#E The Rogue Employee
Disgruntled employees present an insider threat to data. Insider threats accounted for 15 percent of
breaches across all patterns,3 and they can be especially challenging for companies because
employees often have both access to data and knowledge of what is stored and where.
Restricting access to sensitive data to only employees with an immediate need to use the data can
help reduce the threat. Companies can limit, log and monitor internal account usage to protect
against rogue employees, as well as protect against external attackers disguising themselves as
legitimate users.
#! The Ransom Artist
Bad actors have been modifying codes and implementing new ransom attack methods, sparking a
rise in ransomware as the fifth most common form of malware, up from the 22nd most common in the
2014 Verizon Data Breach Incident Report.4 Many companies are paying ransom, often via
anonymous bitcoin payments, to have their data restored.
“The people who fall victim to ransomware are not following the information security rules, including
encryption and frequent backups,” Pascal Millaire, Vice President and General Manager of Cyber
Insurance at Symantec. If you are able to independently restore the data, you will be less affected by
the ransom attempt, but you will still need to determine how the cyber thief gained access to your
network before making their ransom attempt.
Sources:
1 http://www.verizonenterprise.com/resources/reports/rp_data-breach-digest-2017-perspective-is-
reality_xg_en.pdf
2 Ibid.
3 Ibid.
4 Ibid.
Learn More About Travelers Cyber Insurance Options
More Prepare & Prevent
BSB? Travelers Risk How Does Cyber Building Resilience to
IndexU Cyber Insurance Work? Cyber Threats
;Infographic=
Learn more about having the For more information on how
Here's a look at key findings coverage that is right for your to help protect your company
from the 2021 Travelers Risk company. from cyber risk, see our
Index, including what are the whitepaper.
top cyber-specific concerns.
Travelers and The Travelers Umbrella are registered trademarks of The Travelers Indemnity Company in the U.S. and other countries.
© 2022 The Travelers Indemnity Company. All rights reserved.
PRODUCTS & SERVICES OUR COMPANY CONNECT LEGAL & COMPLIANCE
For Individuals About Travelers Customer Support Terms of Service
For Businesses Careers MyTravelers® Privacy & Security
Claim Services Investors For Agents Accessibility
Prepare & Prevent Sustainability Find an Agent Producer Compensation Disclosure
Travelers Institute
You might also like
- Cyber Security in Finance InstitutionsDocument17 pagesCyber Security in Finance Institutionsriyasharma.ubsNo ratings yet
- Arista ETM White Paper Employee Training Cybersecurity 101Document7 pagesArista ETM White Paper Employee Training Cybersecurity 101Orly, Jr. PalomarNo ratings yet
- Employee Training Cybersecurity 101 e Book 1 UntangleDocument17 pagesEmployee Training Cybersecurity 101 e Book 1 UntangleJuan Carlos Morales100% (2)
- Create a Cyber Risk-Aware CultureDocument13 pagesCreate a Cyber Risk-Aware CulturegamallofNo ratings yet
- Identity Security Why It Matters and Why NowDocument14 pagesIdentity Security Why It Matters and Why NowFernando PeñaNo ratings yet
- CybersecurityDocument8 pagesCybersecuritykali linuxNo ratings yet
- CRA Buyers Guide 20180906Document5 pagesCRA Buyers Guide 20180906Lawrence LauNo ratings yet
- Zero Trust' Requires Sophistication: ViewpointDocument6 pagesZero Trust' Requires Sophistication: ViewpointMoney HavenNo ratings yet
- IT SecurityDocument28 pagesIT SecurityWahib WaqasNo ratings yet
- CYBER SECURITY HANDBOOK Part-2: Lock, Stock, and Cyber: A Comprehensive Security HandbookFrom EverandCYBER SECURITY HANDBOOK Part-2: Lock, Stock, and Cyber: A Comprehensive Security HandbookNo ratings yet
- Role of HR in CybersecurityDocument19 pagesRole of HR in CybersecurityLife at Nust UniversityNo ratings yet
- Cybersecurity FundamentalsDocument13 pagesCybersecurity FundamentalsNishant MeenaNo ratings yet
- Cns Full MaterialDocument233 pagesCns Full MaterialMadhuri BethaNo ratings yet
- Cybersecurity Essentials for Small Businesses: Safeguarding Your Digital AssetsFrom EverandCybersecurity Essentials for Small Businesses: Safeguarding Your Digital AssetsNo ratings yet
- Ey Cyber Insurance Thought LeadershipDocument20 pagesEy Cyber Insurance Thought LeadershipPieter NoppeNo ratings yet
- Cybersecurity for Small Businesses: Comprehensive Guide to Protecting a Small Business from Various Types of Cyber ThreatsFrom EverandCybersecurity for Small Businesses: Comprehensive Guide to Protecting a Small Business from Various Types of Cyber ThreatsNo ratings yet
- 8835 Test 1Document5 pages8835 Test 1Surjeet SinghNo ratings yet
- Chapter 5: Cybersecurity, Risk Management, and Financial CrimeDocument56 pagesChapter 5: Cybersecurity, Risk Management, and Financial CrimeAuliya HafizNo ratings yet
- PFPT Us SB Securing Financial Institutions and Insurance OrganizationsDocument5 pagesPFPT Us SB Securing Financial Institutions and Insurance OrganizationsShaharudin BmnNo ratings yet
- Order 2434907.editedDocument8 pagesOrder 2434907.editedPaul WahomeNo ratings yet
- Cyber-Security-Infographic - FCADocument1 pageCyber-Security-Infographic - FCAMousumi Utkarsh RayNo ratings yet
- ? Protect Your Business From A Cyber Attack ?Document1 page? Protect Your Business From A Cyber Attack ?M. Tanveer BhattíNo ratings yet
- Cybersecurity For Beginners: Learn How To Defend Against Online ThreatsFrom EverandCybersecurity For Beginners: Learn How To Defend Against Online ThreatsNo ratings yet
- Cyber Security in The Use of ICT Cyber and Digital SecurityDocument20 pagesCyber Security in The Use of ICT Cyber and Digital SecurityDhesserie PaglinawanNo ratings yet
- Cyber Security 3Document11 pagesCyber Security 3Saeed FaNo ratings yet
- Cyber Security: Protecting Yourself OnlineDocument21 pagesCyber Security: Protecting Yourself OnlineMehar SanaNo ratings yet
- Small Biz Sunday Cybersecurity For The Small BusinessDocument16 pagesSmall Biz Sunday Cybersecurity For The Small BusinessEnkayNo ratings yet
- Security Controls To Reduce Risks and Cyber InsuranceDocument13 pagesSecurity Controls To Reduce Risks and Cyber InsuranceMarcio CassianoNo ratings yet
- Centrify Platform EbookDocument26 pagesCentrify Platform EbookMartin ChamamboNo ratings yet
- CH 05Document38 pagesCH 05Febri MonikaNo ratings yet
- Cybersecurity for Beginners : Learn the Fundamentals of Cybersecurity in an Easy, Step-by-Step Guide: 1From EverandCybersecurity for Beginners : Learn the Fundamentals of Cybersecurity in an Easy, Step-by-Step Guide: 1No ratings yet
- RISKSDocument5 pagesRISKSCarleen Grace DeleonNo ratings yet
- Buyers Guide Office 365 G Suite SecurityDocument11 pagesBuyers Guide Office 365 G Suite SecurityDif TargNo ratings yet
- Protecting Data Together: A Team Playbook For Securely Handling Your Company's DataDocument15 pagesProtecting Data Together: A Team Playbook For Securely Handling Your Company's Datajaycee.wongNo ratings yet
- Activity Sheet # 3Document4 pagesActivity Sheet # 3JaeNo ratings yet
- Cybersecurity Case 5Document1 pageCybersecurity Case 5Gaurav KumarNo ratings yet
- GX Gra CyberriskDocument86 pagesGX Gra CyberriskSürəyya MəmmədzadəNo ratings yet
- The Difference Between Threat, Vulnerability, and Risk, and Why You Need To Know - Trava-MinDocument4 pagesThe Difference Between Threat, Vulnerability, and Risk, and Why You Need To Know - Trava-MinpriyankaNo ratings yet
- Defense Guide: Uidacent Hreat DvisoryDocument5 pagesDefense Guide: Uidacent Hreat DvisoryRoberto HNo ratings yet
- Como Cuantificar El Riesgo Es CiberseguridadDocument15 pagesComo Cuantificar El Riesgo Es CiberseguridadJose Miguel Iriarte NeiraNo ratings yet
- What Is CybersecurityDocument74 pagesWhat Is CybersecurityPhương NguyễnNo ratings yet
- Cyber Risk Liabilit InsDocument4 pagesCyber Risk Liabilit Inssentoubudo1647No ratings yet
- CybersecurityDocument8 pagesCybersecuritykali linuxNo ratings yet
- A Hacker-Centric Approach To Securing Your Digital DomainDocument16 pagesA Hacker-Centric Approach To Securing Your Digital DomainZaiedul HoqueNo ratings yet
- Cybersecurity 101 SMBs US Feb 21Document12 pagesCybersecurity 101 SMBs US Feb 21Binu KoshyNo ratings yet
- Final Report For Business WritingDocument15 pagesFinal Report For Business Writingapi-457374067No ratings yet
- CounterCraft Dont Toss The PhishDocument10 pagesCounterCraft Dont Toss The PhishMA ONo ratings yet
- Construction Guidance English Printer VersionDocument38 pagesConstruction Guidance English Printer VersionFred BloggsNo ratings yet
- Chapter 1Document4 pagesChapter 1Chow MoowNo ratings yet
- Ebook - A Complete Guide To CybersecurityDocument29 pagesEbook - A Complete Guide To CybersecuritydsaNo ratings yet
- RG Cybersecurity From Inside Out Case StudyDocument10 pagesRG Cybersecurity From Inside Out Case StudyKhalid Ahmed KhanNo ratings yet
- Cisco Security Info Graphic 1017 FinalDocument1 pageCisco Security Info Graphic 1017 FinalSandro MeloNo ratings yet
- Cyber Security & Penetration Testing Services Cyber Radar SystemsDocument15 pagesCyber Security & Penetration Testing Services Cyber Radar Systemscyberradar systemNo ratings yet
- Cybersecurity For Small Business: The FundamentalsDocument48 pagesCybersecurity For Small Business: The FundamentalsMansur KhanNo ratings yet
- Assignment: On Cyber Crime and Cyber SecurityDocument15 pagesAssignment: On Cyber Crime and Cyber SecurityFarhan ShawkatNo ratings yet
- Risk Associated With Electronic CommerceDocument38 pagesRisk Associated With Electronic CommerceChan YeolNo ratings yet
- delinea-whitepaper-cyber-insurance-mappingDocument18 pagesdelinea-whitepaper-cyber-insurance-mappingNapolNo ratings yet
- دورة تكوينية في السلامة المعلوماتية سبتمبر 2021Document27 pagesدورة تكوينية في السلامة المعلوماتية سبتمبر 2021Abd'Errahmen MharbiNo ratings yet
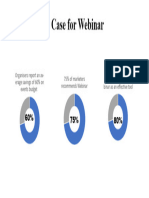
- Makingacasefor WebinarDocument1 pageMakingacasefor WebinarHamidah Che Abdul HamidNo ratings yet
- Hamidah Binti Che Abdul Hamid - Module 3 Assignment 4 - Design A Rewards and Recognition ProgramDocument2 pagesHamidah Binti Che Abdul Hamid - Module 3 Assignment 4 - Design A Rewards and Recognition ProgramHamidah Che Abdul HamidNo ratings yet
- Case Study 2020Document8 pagesCase Study 2020gbNo ratings yet
- M1L1 Understanding The Role and The Context of The School HeadDocument3 pagesM1L1 Understanding The Role and The Context of The School HeadHamidah Che Abdul HamidNo ratings yet
- Resilient Capacity of Malaysian Schools' Headteachers in Adversity: A ReviewDocument3 pagesResilient Capacity of Malaysian Schools' Headteachers in Adversity: A ReviewHamidah Che Abdul HamidNo ratings yet
- 00-The Need For School Leadership and Assessment Capability in Disruptive TimesDocument28 pages00-The Need For School Leadership and Assessment Capability in Disruptive TimesHamidah Che Abdul HamidNo ratings yet
- Building National Resilience MMCDocument29 pagesBuilding National Resilience MMCHamidah Che Abdul HamidNo ratings yet
- User and Best Practices Guide: Downloaded From Manuals Search EngineDocument78 pagesUser and Best Practices Guide: Downloaded From Manuals Search Enginesrx devNo ratings yet
- Practical Guide to Data-Driven Content MarketingDocument43 pagesPractical Guide to Data-Driven Content MarketingAmy KayeNo ratings yet
- Ip SQP 2Document9 pagesIp SQP 2Vineeta SinghNo ratings yet
- Design Hybrid IdentityDocument869 pagesDesign Hybrid IdentityRavinder SinghNo ratings yet
- Case Study Chapter 5 Green ComputingDocument6 pagesCase Study Chapter 5 Green Computingaashir chNo ratings yet
- MediaInformationLiteracy12 Q3 Ver4 Mod1Document31 pagesMediaInformationLiteracy12 Q3 Ver4 Mod1Ma. Clarissa De RamosNo ratings yet
- Advanced Web Programming SolnDocument38 pagesAdvanced Web Programming Solnnitin kachhiNo ratings yet
- Machine and Deep Learning For Resource Allocation in Multi-Access Edge Computing - A SurveyDocument51 pagesMachine and Deep Learning For Resource Allocation in Multi-Access Edge Computing - A Surveyjean claude lionel ng'anyogoNo ratings yet
- Financial Accounting Principles for Law PractitionersDocument71 pagesFinancial Accounting Principles for Law PractitionersDianahDadaKundidzora0% (2)
- 3HAC023113 AM ABB IRC5 OPC Server HelpDocument62 pages3HAC023113 AM ABB IRC5 OPC Server HelpGerardoNo ratings yet
- Intouch User Guide: Business Communications ManagerDocument32 pagesIntouch User Guide: Business Communications Managerronny zubietaNo ratings yet
- Aws Glue InformationDocument46 pagesAws Glue Information华希希No ratings yet
- Hire Employee Without Workday RecruitingDocument5 pagesHire Employee Without Workday RecruitingSwathi BinduNo ratings yet
- Deploying Workloads With Juju and MAAS PDFDocument28 pagesDeploying Workloads With Juju and MAAS PDFjohnlondon125No ratings yet
- CSS LabDocument5 pagesCSS LabanmolNo ratings yet
- How To Create EC2 Instance in AWS - Step by Step TutorialDocument46 pagesHow To Create EC2 Instance in AWS - Step by Step TutorialTECHIE HORIZONNo ratings yet
- jQuery: Lightweight JavaScript library for DOM manipulationDocument5 pagesjQuery: Lightweight JavaScript library for DOM manipulationjloNo ratings yet
- OpenText Documentum Foundation Classes CE 22.2 Release NotesDocument13 pagesOpenText Documentum Foundation Classes CE 22.2 Release NotesDamoNo ratings yet
- PROVIX COVID19 Temperature Detection Camera System 1Document11 pagesPROVIX COVID19 Temperature Detection Camera System 1Sales HONo ratings yet
- Norton™ Internet Security: Product ManualDocument99 pagesNorton™ Internet Security: Product ManualGeorge LucaNo ratings yet
- Arpan - Food Donation Android ApplicationDocument28 pagesArpan - Food Donation Android ApplicationTUSHAR SHARMA100% (1)
- DebuglogDocument7 pagesDebuglogdreyes2288No ratings yet
- Dance 3 SyllabusDocument12 pagesDance 3 SyllabusSally MistyNo ratings yet
- Salawu Semiu Dolapo 2021 PDFDocument387 pagesSalawu Semiu Dolapo 2021 PDFJesús PachecoNo ratings yet
- Entuity Core ReferenceDocument370 pagesEntuity Core ReferenceMara FloresNo ratings yet
- GuardII Platform User ManualDocument54 pagesGuardII Platform User ManualEléctrica EBYNo ratings yet
- DS-2CD1153G0-I Datasheet V5.5.52 20211223Document5 pagesDS-2CD1153G0-I Datasheet V5.5.52 20211223Ibrahim AlqhtaniNo ratings yet
- JQuery Programming CookbookDocument57 pagesJQuery Programming CookbookHicham Ennajih100% (1)
- Industry 4.0 and Supply Chain Management: A Methodological ReviewDocument5 pagesIndustry 4.0 and Supply Chain Management: A Methodological ReviewWajid AliNo ratings yet
- SIOS Protection Suite For Linux Network Attached Storage Reovery Kit v9.2.2Document23 pagesSIOS Protection Suite For Linux Network Attached Storage Reovery Kit v9.2.2Vasu VasuNo ratings yet