Professional Documents
Culture Documents
Web Application Security
Uploaded by
EllisOriginal Description:
Original Title
Copyright
Available Formats
Share this document
Did you find this document useful?
Is this content inappropriate?
Report this DocumentCopyright:
Available Formats
Web Application Security
Uploaded by
EllisCopyright:
Available Formats
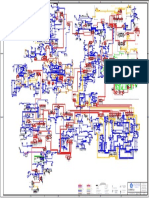
client-supplied data gets
echoed back to the screen
reflected XSS problem
most common via search box
JS payload doesn't need to be
unique form of XSS
sent or echoed by web server
can be persistent if
similar to reflected XSS
incorporates cookies
3 types
DOM based XSS object structure to access &
DOM (Document Object Model) manipulate nodes, values and
attributes
completely relies on JS and insecure use of
input validation vulnerability
dynamically obtained data from DOM
on the client side JS
structure
stored XSS
user is able to define
content which gets
evaluated as javascript or
create own javascript
resulting from missing/bad blocks
input/input handling
Password Change/Forgotten Functions
developer doesn't apply needed
sanitzation for given context of user
Brute Forcible Login supplied input
XSS
Verbose Failure Messages technique to force web sites to display browser doesn't have to be
malicious code which gets executed in users susceptible to any
web browser vulnerability
Insecure Credential Distribution
user supplied data doesn't only all headers may be spoofed by logging infrastructure must the target is usually the admin,
Predictable Usernames/Initial Passwords
Logical Flaws reach the server via GET and user including cookie, referer and implement proper escaping for which will gain the attacker admin
POST host everything logged rights
Predictable Account Activation
Link/ID
variable width encoding can
make escaping invalid
Bad Passwords
encoding can pose a problem
server can't correctly check and filter the
Fail-Open Login encoding the browser uses to interpret the
page is a different
defective multi-stage login
history stealing getComputedStyle API visited style
if want access to a subdomain both pages intranet hacking
problem must explicitly set the document.domain to
the same value
JS can completely alter look of
web site
flash has xml policy files that possible attack methods defacement
define exceptions called
only the exact same domain can be leveraged for phishers
/crossdomain.xml
explicit exceptions can be made enforced by utilizing domain names to occur on the real website
can be accessed
new Header called Access-Control
only allow to read data abuse users browser to run as filesharing node
originating from the same Same Origin Policy applications without user
in xml XMLHttpRequest source approval
as part of anonymity network
<?access-control processing
instruction
unaware developer might those can be revealed by
compiled bytecode
include secrets into code decompilers and reversing
protocol
Client Side Flash Security each exact domain gets an crossdomain.xml for cross
sources are the same if the
hostname cross domain requests
following matches own sandbox sandbox communication
port (not for IE?) sandboxing
Java Security
session management
closely related to
authentication mechanism session management needed to browser connects to malicious
identify different users across server with dns timeout of 1
requests second
webapplications becoming like
desktop applications -> need http is stateless
state JS tells browser to connect
back in 2 seconds
main technology Cookies attack without dns pinning
browser resolves name again
since no longer valid
basic
dns server replies with arbitrary ip this ip may be in the intranet
digest address it wants to get the contents providing attacker access to the
from inner network
NTLM http authentication
technologies the browser pins once received IPs browser protection to prevent attackers from
(Kerberos) to domains to prevent the attack breaking the same-origin policy through DNS
above tricks
client certificates
the browser is re-requesting dns if
the web server isn't reachable
in cookie anymore
encoded session state
being pushed to client
in hidden form fields same as above, but this time the base
DNS Pinning Vulnerabilites it needs to firewall the port in question not the
attacker system firewalls itself to be
attack whole server, so the whole process can be
simple attack huge impact on unreachable for the browser in the second
carried out for different IPs on a single server
web app security request
anti-dns pinning
possible because browser implicitly appends checking the host header if the this would already happen if virtual
perform actions in users targeted system by the browser is hosting is used, but there usually is a
Cookies to every request for the allowed
behalf via users browser really ours default
domain(s)
anti-anti-dns pinning
cannot read from other exploits in client side request building
domain, but influence it
doesn't obey to same-origin policy Web Application Security anti-anti-anti-dns pinning mechanisms to spoof the host header defeats
CSRF this kind of protection
XSS and CSRF can let unsuspecting
user attack a webserver on attackers it is not possible to hijack session via
behalf automated sending of cookies with this,
because cookie sending is determined by
domain not IP
nonce could be read by JS
incorporate nonces into state-changing possibility to take over
XSS vulnerability would bypasses this counter measures
JS enables to act with web requests systems in the intranet
site like the user intranet scanning can be combined with an
automated search for vulnerabilities in the
intranet use XSS or CSRF exploit to attack users
webapp accepts provided browser to steal information or authentication
tokens as new sessions tokens
Session Hijacking
webapp doesn't create new redefine Array object to have
token on login Session Fixation the results accessible
request json from other side
via
attacker can smuggle new session token into <script> include XMLHttpRequest wouldn't
users browser and continue his session after work because of same origin
login policy
JavaScript Hijacking
guessable meaningful tokens user is authenticated on other
Sessions web service via cookie
reproducible algorithm
concealed sequences if web service discloses
enabling brute-forcing
privacy relevant information
attacks over json
the keyspace can be minimized the
better the timeframe of generation is token-generation process predictable tokens weak Session IDs
time dependency
known depends only/mostly on time
SQL databases are usually called indirected by a web
application, which passes a complete query containing
weak (P)RNG parts of user supplied content to the database
subsystem
tokens holds authorization data user doesn't need to log in static tokens
requests to retrieve
information
fallback to http after login
SELECT
injection point usually the
usage of https only cookies http for all static content
WHERE clause
disclosure of tokens on network
tricked by attacker to make http request to
creates new row
server, not matter if successful, token will
be disclosed
INSERT attackers usually have to guess database brute-forcing the number with
schema and therefore doesn't know the 1s (or 2000s for possible
logout doesn't invalidate session order and number of columns dates) or NULLs
user didn't log out vulnerable session termination
change one or more data rows
no session expiration
possibly user got force quit UPDATE
usual entry point the WHERE
clause and or the SET clause
so in default the cookie is sent in all cookies are default sent in every request
requests to subdomains and the domain web-servers sharing the same right-hand-side
removes one or more rows
itself of the domain
DELETE
domain
usual entry point is WHERE clause
enabling also other webservers on a
domain value can be changed
subdomain to read the cookie from liberal cookie scope
upto one below the tld
users combine two or more
SQL Injection SELECTs
too liberal path value again might enable similar to domain path defines to which
other users on the system to obtain cookies subdirectories on the server cookies will be path attacks can be leveraged to gain information
from users of that application passed from different tables than original
query
if an attacker uses the session of a user it will be
detected because the page token replied will not be selected fields must be same
the last provided, because there are two open UNION operator number and type (structure)
instances
pro Attacks
Server Side names of tables and fields
names can be queried from
can be leveraged to track user creating additional page tokens database specific metadata
must be known
movement on page tables
counter measures
opening several tabs at the same inject ORDER BY $colnum until search for columns of string type by
time will be interpreted as an con usual steps error to check for number of inserting NULL in all but one field, which
attack columns holds a string until string is displayed
deauthenticating user when suspicious Blind SQL injection
activity is noticed like modified hidden form reactive session termination
fields or strings associated with SQLi or XSS
timing attacks
correctly escaped user user content is fetched from database
content is written to the and used again without further
database sanitization
Second Order SQL Injection
foo' is fetched from database and used
foo' gets correctly escaped to
to create update statement for
foo'' as username
password without futher sanitization
Remote File Inclusion
executed code is built at
runtime containing user
supplied content
usually interpreted languages
utilizing special characters to break out of
Remote Code Execution data context therefore being able to
execute arbitrary commands
in compiled languages attack not leverages
syntactic features of programming payload contains machine code
language
Path Traversal
Web Application Firewall ModSecurity (Apache)
You might also like
- Suresh IAS Academy NotesDocument176 pagesSuresh IAS Academy NotesMohamed Harun91% (11)
- Google Browser Security HandbookDocument54 pagesGoogle Browser Security HandbookelgurifloresNo ratings yet
- Universal, 900 Packing Layout (23.6.2023) - Model - 2Document1 pageUniversal, 900 Packing Layout (23.6.2023) - Model - 2thinh daoxuanNo ratings yet
- BN-MLS-21-PTSC-307302 - Rev02 UFD - Vent and Drains System - Code 2Document2 pagesBN-MLS-21-PTSC-307302 - Rev02 UFD - Vent and Drains System - Code 2citramuaraNo ratings yet
- 11 10 Layout1Document1 page11 10 Layout1Shah MuzzamilNo ratings yet
- L2 E. Desain Drainase Cover v4Document17 pagesL2 E. Desain Drainase Cover v4Muhammad WafidNo ratings yet
- The Schur Algorithm: Digtal Signal Processing (Et 4235)Document22 pagesThe Schur Algorithm: Digtal Signal Processing (Et 4235)KrishNo ratings yet
- SystemMap Aug2021Document1 pageSystemMap Aug2021FOX5 VegasNo ratings yet
- CommunityBus Transit TabloidDocument1 pageCommunityBus Transit Tabloidshortstak337No ratings yet
- SVVSVDocument1 pageSVVSVMunzurulKaderNo ratings yet
- 1503off SubseaposterDIG PDFDocument1 page1503off SubseaposterDIG PDFHWANG INBUMNo ratings yet
- Sex Chat For Clients PDFDocument1 pageSex Chat For Clients PDF2qkhfz7kgmNo ratings yet
- Australian RMS Drawing LegendsDocument1 pageAustralian RMS Drawing LegendsrakhbirNo ratings yet
- Staten Island Bus MapDocument1 pageStaten Island Bus MapRay marteNo ratings yet
- 710 Option Floor PlansDocument1 page710 Option Floor Plansevans munakuNo ratings yet
- University of Huddersfield Repository: Original CitationDocument9 pagesUniversity of Huddersfield Repository: Original CitationGIAN PIERO RODRIGUEZ SANTOSNo ratings yet
- Sample 17141 PDFDocument16 pagesSample 17141 PDFAayush GargNo ratings yet
- 2.normal KLDocument1 page2.normal KLRyanNo ratings yet
- 2.132 Jin Out - KLDocument1 page2.132 Jin Out - KLRyanNo ratings yet
- 2.KL - KL OutageDocument1 page2.KL - KL OutageRyanNo ratings yet
- 2.N-1 KL TFDocument1 page2.N-1 KL TFRyanNo ratings yet
- Can Be Has: M/2019/01/02/hash-Match - Join - InternalsDocument1 pageCan Be Has: M/2019/01/02/hash-Match - Join - InternalsJMjm07No ratings yet
- Titas 376 CVL SD 04 Exc 0100 0001 C10Document1 pageTitas 376 CVL SD 04 Exc 0100 0001 C10Ibrahim GaflanovNo ratings yet
- Cahir Issue A1 LDocument1 pageCahir Issue A1 LOluwaseyi JohnNo ratings yet
- 3.4 - Requirements Traceability MatrixDocument1 page3.4 - Requirements Traceability MatrixViệt Châu VõNo ratings yet
- WW Ms ST 00 Mosque Minaret1631123643798Document7 pagesWW Ms ST 00 Mosque Minaret1631123643798孔庆龙No ratings yet
- Kunjungi Saya Di Blog Sini Ya!!: A A C C 6 6 - A ADocument1 pageKunjungi Saya Di Blog Sini Ya!!: A A C C 6 6 - A Adasep rudiNo ratings yet
- 2022 Worldwide FPSO UnitsDocument1 page2022 Worldwide FPSO UnitscourarodrigoNo ratings yet
- 2 JCB 000100 1NP 12 008020 Layout1Document1 page2 JCB 000100 1NP 12 008020 Layout1md shahbajNo ratings yet
- The Interaction Between Any Two Charges Is Completely Unaffected by The Presence of OthersDocument9 pagesThe Interaction Between Any Two Charges Is Completely Unaffected by The Presence of Otherssuma mumuNo ratings yet
- 2.KL E2 1PHDocument1 page2.KL E2 1PHRyanNo ratings yet
- 2.KL E1 1PHDocument1 page2.KL E1 1PHRyanNo ratings yet
- Kerajaan Malaysia: Minconsult Sdn. BHDDocument15 pagesKerajaan Malaysia: Minconsult Sdn. BHDJak CuboNo ratings yet
- Pet Suites Building SF 13,900 : BelowDocument1 pagePet Suites Building SF 13,900 : BelowchrisNo ratings yet
- School Zones Elementary)Document1 pageSchool Zones Elementary)ecooper26No ratings yet
- 01 - Large NetworksDocument38 pages01 - Large Networksasim zamanNo ratings yet
- JC Ward PrecDocument1 pageJC Ward PrecJENNIFER WEISERNo ratings yet
- Pwa-F-Key-320: K-Pnl-Touch-320Document1 pagePwa-F-Key-320: K-Pnl-Touch-320IvayloNo ratings yet
- Sample 17140Document16 pagesSample 17140AbhinavNo ratings yet
- Utawala-Bantu Sewers DWGDocument28 pagesUtawala-Bantu Sewers DWGAsaph MungaiNo ratings yet
- ASC PHASE II 16-09 UpdatedDocument1 pageASC PHASE II 16-09 UpdatedCharsaddadiv formsNo ratings yet
- Benja PlanDocument1 pageBenja Planmasumba patrickNo ratings yet
- Enewsletter 2016-17Document8 pagesEnewsletter 2016-17Vinayak Ashok BharadiNo ratings yet
- Tenant Revised Floor Plans 17 Nov 22Document4 pagesTenant Revised Floor Plans 17 Nov 22Titus OmondiNo ratings yet
- Diptico FinalDocument2 pagesDiptico Finalfaperador9753No ratings yet
- 1.normal JinjangDocument1 page1.normal JinjangRyanNo ratings yet
- Acs03 C10766 110 P Dpe 0001 02 - Z1 - Iab - 20200825 - en Al - 01Document1 pageAcs03 C10766 110 P Dpe 0001 02 - Z1 - Iab - 20200825 - en Al - 01Parim BuziNo ratings yet
- Equipamientos Administrativos PunoDocument1 pageEquipamientos Administrativos PunoAldahir Sucari BanegasNo ratings yet
- PubsubDocument1 pagePubsubJavierNo ratings yet
- SGHS3-ES-DG-60L2000 SECURITY LAYOUT (Editted)Document1 pageSGHS3-ES-DG-60L2000 SECURITY LAYOUT (Editted)rc.design0911No ratings yet
- Matsama Abil Hasan 2021 Form BedaharaDocument1 pageMatsama Abil Hasan 2021 Form Bedaharaelsa diadorapambayunNo ratings yet
- Security Challenges To Telecommunication Networks: An Overview of Threats and Preventive StrategiesDocument7 pagesSecurity Challenges To Telecommunication Networks: An Overview of Threats and Preventive StrategiesBabul BhattNo ratings yet
- Inzaar Magazine 2021 MarDocument52 pagesInzaar Magazine 2021 MarTalha IsmailNo ratings yet
- Free Press Indore Edition 21 Feb 2021Document15 pagesFree Press Indore Edition 21 Feb 2021SbsjsjNo ratings yet
- Sadi - Uni2019 - 03 - PropDocument1 pageSadi - Uni2019 - 03 - PropDanielNo ratings yet
- Uni2020 04 TensionDocument1 pageUni2020 04 TensionFederico BacaliniNo ratings yet
- Uni2021 05 TensionDocument1 pageUni2021 05 TensionMario RamosNo ratings yet
- Uni2020 04 PropDocument1 pageUni2020 04 PropFederico BacaliniNo ratings yet
- 9th Sem Interview PortfolioDocument30 pages9th Sem Interview PortfolioRudra VyasNo ratings yet
- Uni2020 06 PropDocument1 pageUni2020 06 PropAguz TaletNo ratings yet
- Tracking MechanismDocument14 pagesTracking MechanismAlejandro Londoño CongoteNo ratings yet
- Making Ajax QueriesDocument47 pagesMaking Ajax QueriesЮля ЦурканNo ratings yet
- JavaScriptExecutor in Selenium WebDriver With ExamplDocument4 pagesJavaScriptExecutor in Selenium WebDriver With Exampljeevi jeevaNo ratings yet
- Burp Scanner ReportDocument3 pagesBurp Scanner ReportPr RabariNo ratings yet
- Exploiting Misconfigured CORSDocument10 pagesExploiting Misconfigured CORSWinning WhalesNo ratings yet
- Web Browser Security: Vitaly ShmatikovDocument60 pagesWeb Browser Security: Vitaly ShmatikovSrinivasan KrishnanNo ratings yet
- CIS6013 Web-Application-Security ETH 1 AC41Document9 pagesCIS6013 Web-Application-Security ETH 1 AC41;(No ratings yet
- HTTP ZineDocument28 pagesHTTP Zineing.firemanNo ratings yet
- 10 HTML5 SecurityDocument32 pages10 HTML5 SecurityAdarsh SuparnaNo ratings yet
- Hacking Facebook - Same Origin Policy ExploitDocument9 pagesHacking Facebook - Same Origin Policy ExploitWendy ChristopherNo ratings yet
- Wagner Spring 2014 CS 161 Computer Security Midterm 1: (Last) (First)Document7 pagesWagner Spring 2014 CS 161 Computer Security Midterm 1: (Last) (First)Ahsan RamzanNo ratings yet
- Ilya Kantor - The Modern JavaScript Tutorial - Part IIIDocument333 pagesIlya Kantor - The Modern JavaScript Tutorial - Part IIIhediyyeall.shopNo ratings yet
- HTML 5 Web SecurityDocument82 pagesHTML 5 Web Securityc0moshackNo ratings yet
- Chromium Security ArchitectureDocument10 pagesChromium Security ArchitectureVijay HmNo ratings yet
- Vulnerability ReportDocument47 pagesVulnerability Reportprajapati brijeshNo ratings yet
- 09 Web Attacks PDFDocument79 pages09 Web Attacks PDFangelhbNo ratings yet
- Web ApplicationDocument47 pagesWeb ApplicationVIJAYNo ratings yet
- Elearning Course CatalogDocument68 pagesElearning Course CatalogManoharrNo ratings yet
- A Secure Proxy-Based Cross-Domain Communication FoDocument9 pagesA Secure Proxy-Based Cross-Domain Communication FobruteforceNo ratings yet
- Chen 2017 J. Phys. Conf. Ser. 910 012016Document7 pagesChen 2017 J. Phys. Conf. Ser. 910 012016Haider SultanNo ratings yet
- Scan Report: June 4, 2023Document63 pagesScan Report: June 4, 2023BruhNo ratings yet
- XSS - Web For PentesterDocument22 pagesXSS - Web For PentesterjoaolopesnetosemrifNo ratings yet
- Google Chrome Disables Domain Relaxation Starting M109 - SAP For MeDocument1 pageGoogle Chrome Disables Domain Relaxation Starting M109 - SAP For MePhildarPhunsiNo ratings yet
- Master Frontend in 60 DaysDocument21 pagesMaster Frontend in 60 DaysgulamnabiesiyariNo ratings yet
- Web Browser SecurityDocument70 pagesWeb Browser SecurityDhairyaNo ratings yet
- Intrebari Pentru Interviu de FrontendDocument5 pagesIntrebari Pentru Interviu de FrontendIlie Bogdan-MihaiNo ratings yet
- DNS CNAME TrackingDocument21 pagesDNS CNAME TrackingJesus VilchezNo ratings yet
- Broken Web SecurityDocument87 pagesBroken Web SecurityBo BeanNo ratings yet
- Cross-Domain Security in Web Applications: HapterDocument83 pagesCross-Domain Security in Web Applications: Haptergood2000moNo ratings yet