Professional Documents
Culture Documents
ISEC-210 UNIT 02 - Information Security Threats and Attacks
Uploaded by
Kutemwa MithiCopyright
Available Formats
Share this document
Did you find this document useful?
Is this content inappropriate?
Report this DocumentCopyright:
Available Formats
ISEC-210 UNIT 02 - Information Security Threats and Attacks
Uploaded by
Kutemwa MithiCopyright:
Available Formats
Malawi University of Science and Technology
Malawi Institute of Technology
Information Security
ISEC-210
Module Compiler
Allan Nila Chongwe – MSc. Computer Science, BSc. Information Technology
ISEC-210 Module Guide – A.N. Chongwe Page | 1
Copyright
This material is a property of the Malawi University of Science and Technology
This material is not to be sold.
2021
All rights are reserved. No part of this publication may be reproduced, stored in a
retrieval system or transmitted in any form or by any means, electronic or
mechanical, including photocopying, recording or otherwise without copyright
clearance from Malawi University of Science and Technology.
Malawi University of Science and Technology,
P.O. Box 5196,
Limbe,
Malawi.
Tel: (265) 1 478 000
Fax: (265) 1 478 220
Email: registrar@must.ac.mw
Website: www.must.ac.mw
ISEC-210 Module Guide – A.N. Chongwe Page | 2
Unit 2
Information Security Threats and Attacks
2.0 Introduction
Welcome to Unit 2. This Unit discusses the common information security
threats and attacks. We will look at the common categories of
information security threats and the different types of attacks which can
compromise the information security of an organisation. We will
conclude with a look at risks and vulnerabilities.
2.1 Intended Learning Outcomes
By the end of this unit, you should be able to:
a. Define information security threats.
b. Compare and contrast a threat and an attack.
c. Describe the different types of threats and attacks.
d. Explain some of the risks to an organisation’s information
e. Define information security vulnerability
2.2 Key Terms
During the course of this unit, you will find the following key words or
phrases. Watch out for these and make sure that you understand what
they mean.
Threat Attacks Risks
Polymorphic worm Malware Vulnerabilities
ISEC-210 Module Guide – A.N. Chongwe Page | 3
2.3 Threats and Attacks
As discussed in Unit 1, the goal of information security is to protect the
information assets for an individual or within an organisation. An asset
is, mainly an organizational, resource that is being protected. It can be
logical, such as a Web site or a software, information, or data; or it can
be physical, such as a person, computer system, a server, or other
tangible object. Assets, and particularly information assets, are the focus
of security efforts; they are what those efforts are attempting to protect.
In information security, the focus is protecting these assets from any
threats or attacks. A threat is any events or circumstances that have the
potential to adversely affect an organisation’s operations and assets –
anything bad that can happen to the assets – e.g. forces of nature,
deliberate software attacks, theft, etc. A threat can be realized through
a vulnerability or a weakness in a system. An attack is an intentional or
unintentional act that can cause damage to or otherwise compromise
information and/or the systems that support it by exploiting any
vulnerability i.e. password cracking, man in the middle, etc.
The main difference between a threat and an attack is that a threat can
be either intentional or unintentional where as an attack is intentional.
2.3.1 Categories of Threats
The Chinese general Sun Tzu Wu's 'The Art of War', written around 500
B.C., emphasizes the importance of knowing yourself as well as the
threats you face. These two points also applies in information security
for organisations today in the sense that it is important to;
ISEC-210 Module Guide – A.N. Chongwe Page | 4
i. know yourself; that is, be familiar with the information to be
protected and the systems that store, transmit, and process it; and
ii. know the threats that you face.
To make sound decisions about information security, management must
be informed about the various threats to an organization’s people,
applications, data, and information systems. In the context of
information security, a threat could be an object, person, or other entity
that presents an ongoing danger to an asset.
The following general categories represent common clear and present
dangers to an organization’s people, information, and systems;
i. Compromises to Intellectual Property
ii. Deliberate Software Attacks
iii. Espionage or Trespass
iv. Forces of Nature
v. Human Error or Failure
vi. Information Extortion
vii. Missing, Inadequate, or Incomplete Controls
viii. Sabotage or Vandalism
ix. Theft
x. Technical Hardware/Software Failures or Errors
xi. Technical Hardware/Software Failures or Errors
xii. Technological Obsolescence
We shall look at each of these in the subsequent sections.
ISEC-210 Module Guide – A.N. Chongwe Page | 5
2.3.1.1 Compromises to Intellectual Property
Many organizations create, or support the development of, intellectual
property (IP) as part of their business operations. Intellectual property is
defined as “the ownership of ideas and control over the tangible or
virtual representation of those ideas. Use of another person’s intellectual
property may or may not involve royalty payments or permission, but
should always include proper credit to the source.” Intellectual property
can be trade secrets, copyrights, trademarks, and patents.
The unauthorized appropriation of IP constitutes a threat to information
security. Employees may have access privileges to the various types of
IP, and may be required to use the IP to conduct day-to-day business.
The most common IP breach is the unlawful use or duplication of
software-based intellectual property, commonly known as software
piracy. Many individuals and organizations do not purchase software as
mandated by the owner’s license agreements. Because most software is
licensed to a particular purchaser, its use is restricted to a single user or
to a designated user in an organization. If the user copies the program
to another computer without securing another license or transferring the
license, he or she has violated the copyright.
2.3.1.2 Deliberate Software Attacks
Deliberate software attacks occur when one or more people deliberately
designs and deploys software to attack a system. Most of this software
is referred to as malicious software, or sometimes malware. These
software components or programs are designed to damage, destroy, or
ISEC-210 Module Guide – A.N. Chongwe Page | 6
deny service to the target systems. Most individuals and organisations
fall victim to malwares very frequently. A malware is any piece of
software written with the intention of damaging devices, stealing data,
and generally causing a mess. They include viruses, worms, trojans,
adware, spyware, rogue software, and ransomware.
i. Viruses - The commonly found software in the malware family
are viruses. Like their biological namesakes, viruses attach
themselves to clean files and infect other clean files. They can
spread uncontrollably, damaging a system’s core functionality and
deleting or corrupting files. They usually appear as an executable
file (.exe).
ii. Worms - A worm is malware that copy itself repeatedly and
consume disk space or other resources. Unlike viruses, worms do
not require user intervention to be launched; they are self-
propagating. Worms infect entire networks of devices, either local
or across the internet, by using network interfaces.
iii. Trojans - This kind of malware disguises itself as legitimate
software, or is hidden in legitimate software that has been
tampered with. It tends to act discreetly and create backdoors in
your security to let other malware in. Once a Trojan horse has
network access, it can be used to log keystrokes for the purpose
of stealing highly sensitive personal information.
iv. Spyware - Simply put, a spyware is malware designed to spy on
its victims. It hides in the background and takes notes on what
ISEC-210 Module Guide – A.N. Chongwe Page | 7
you do online, including your passwords, credit card numbers,
surfing habits, and more.
v. Ransomware - Ransomware is a form of malware that encrypts a
victim's files. The attacker then demands a ransom from the victim
to restore access to the data upon payment or threatens to erase
everything unless a ransom is paid.
vi. Adware - Though not always malicious in nature, aggressive
advertising software can undermine your security just to serve you
ads – which can give other malware an easy way in.
vii. Logic Bomb - A logic bomb is malware internationally designed
to start at a specific time in the future or when a specified
condition exists.
2.3.1.3 Espionage or Trespass
Espionage or trespass occurs when an unauthorized individual attempts
to gain illegal access to organisational information. When an
unauthorized individual gains access to the information an organization
is trying to protect, that act is categorized as espionage or trespass.
Attackers can use many different methods to access the information
stored in an information system. When information gatherers employ
techniques that cross the threshold of what is legal or ethical, they are
conducting industrial espionage. When foreign governments are
involved, these activities are considered espionage and a threat to
national security.
ISEC-210 Module Guide – A.N. Chongwe Page | 8
2.3.1.4 Forces of Nature
Also referred to as Acts of God, forces of nature are dangerous because
they are unexpected and come without very little warning. They disrupt
lives of individuals but also causes damage to information but also the
storage, transmission, processing, and use of information. They include
fire, flood, earthquake, hurricane and lightning as well as volcanic
eruption and insect infestation. Since it is not possible to avoid many of
these threats, individuals and organisations must implement controls to
limit damage and also prepare contingency plans for continued
operations such as disaster recovery plans, business continuity plans, and
incident response plans.
2.3.1.5 Human Error or Failure
Human error is an unintentional action or decision. They includes acts
performed without intent or malicious purpose by an authorized user.
To err is human… – when people use information systems, mistakes
happen. Inexperience, improper training, and the incorrect assumptions
are just some of the things that can cause these misadventures.
Regardless of the cause, even a smallest mistake can cause extensive
damage. One of the greatest threats to an organization’s information
security is the organization’s own employees. Employees are the threat
agents closest to the organizational data. Because employees use data in
everyday activities to conduct the organization’s business, their mistakes
represent a serious threat to the confidentiality, integrity, and
availability of data more than the threats from outsiders. This is because
employee mistakes can easily lead to the following: revelation of
ISEC-210 Module Guide – A.N. Chongwe Page | 9
classified data, entry of erroneous data, accidental deletion or
modification of data, storage of data in unprotected areas, and failure
to protect information. Leaving classified information in unprotected
areas, such as on a desktop, on a Web site, or even in the trash can, is
as much a threat to the protection of the information as is the individual
who seeks to exploit the information, because one person’s carelessness
can create a vulnerability and thus an opportunity for an attacker.
However, if someone damages or destroys data on purpose, the act
belongs to a different threat category known as sabotage or vandalism.
2.3.1.6 Information Extortion
Information extortion occurs when an attacker or trusted insider steals
information from a computer system and demands compensation for its
return or for an agreement not to disclose it. Extortion is common in
credit card number theft. For example, Web-based retailer CD Universe
was the victim of a theft of data files containing customer credit card
information. The culprit was a Russian hacker named Maxus, who
hacked the online vendor and stole several hundred thousand credit
card numbers. When the company refused to pay the $100,000
blackmail, he posted the card numbers to a Web site, offering them to
the criminal community. His Web site became so popular he had to
restrict access.
2.3.1.7 Theft
Theft is the illegal taking of another’s property, which can be physical,
electronic, or intellectual. The value of information is diminished when
it is copied without the owner’s knowledge. Physical theft can be
ISEC-210 Module Guide – A.N. Chongwe Page | 10
controlled quite easily by means of a wide variety of measures, from
locked doors to trained security personnel and the installation of alarm
systems. Electronic theft, however, is a more complex problem to
manage and control. When someone steals a physical object, the loss is
easily detected; if it has any importance at all, its absence is noted. When
electronic information is stolen, the crime is not always readily apparent.
If thieves are clever and cover their tracks carefully, no one may ever
know of the crime until it is far too late.
2.3.1.8 Technical Hardware Failures or Errors
A hardware failure is a malfunction within the electronic circuits or
electromechanical components e.g. disks (figure 2.1) of a computer
system. Recovery from a hardware failure requires repair or replacement
of the affected part.
Figure 2.1 – Damaged hard drive
Technical hardware failures or errors occur when a manufacturer
distributes equipment containing a known or unknown flaw. These
defects can cause the system to perform outside of expected parameters,
resulting in unreliable service or lack of availability. Some errors are
ISEC-210 Module Guide – A.N. Chongwe Page | 11
terminal – that is, they result in the unrecoverable loss of the equipment.
Some errors are intermittent, in that they only periodically manifest
themselves, resulting in faults that are not easily repeated, and thus,
equipment can sometimes stop working, or work in unexpected ways.
One of the best-known hardware failures is that of the Intel Pentium II
chip (FDIV), which had a defect that resulted in a calculation error under
certain circumstances.
2.3.1.9 Technical Software Failures or Errors
Technical software failure is the inability of a program to continue
processing due to erroneous logic. It is much bigger problem because it
is not easy to debug a program with millions of lines of code than it is
to diagnose a piece of hardware.
Figure 2.2 – Software failure
Large quantities of computer code are written, debugged, published,
and sold before all their bugs are detected and resolved. Sometimes,
combinations of certain software and hardware reveal new bugs. These
ISEC-210 Module Guide – A.N. Chongwe Page | 12
failures range from bugs to untested failure conditions. Sometimes these
bugs are not errors, but rather purposeful shortcuts left by programmers
trying to fix something.
2.3.1.10 Technological Obsolescence
Old-fashioned or outdated infrastructure (software and hardware) can
lead to unreliable and untrustworthy systems. Management must
recognize that when technology becomes outdated, there is a risk of loss
of data integrity from attacks. Management’s strategic planning should
always include an analysis of the technology currently in use. Ideally,
proper planning by management should prevent technology from
becoming obsolete, but when obsolescence is manifest, management
must take immediate action. IT professionals play a large role in the
identification of probable obsolescence. Storage media such as floppy
drives as sown in figure 2.3 are now a story of the past.
Figure 2.3 – Obsolete technology
Windows 8 support ended in January 2016 while Windows 10 support
will go up to 2025. Ubuntu is expected to retire its 20.04 LTS release in
2025. The software vendor Symantec retired support for a legacy
ISEC-210 Module Guide – A.N. Chongwe Page | 13
version of its popular antivirus software, and organizations interested in
continued product support were obliged to upgrade immediately to a
different antivirus control software. In organizations where IT personnel
had kept management informed of the coming retirement, these
replacements were made more promptly and at lower cost than at
organizations where the software was allowed to become obsolete.
2.3.2 Information Security Attacks
An attack is an act that takes advantage of a vulnerability to compromise
a controlled system. It is accomplished by a threat agent - a person or a
group responsible for the attack - that damages or steals an
organization’s information or physical asset. A vulnerability is an
identified weakness in a controlled system, where controls are not
present or are no longer effective. Unlike threats, which are always
present, attacks only exist when a specific act may cause a loss. For
example, the threat of damage from a lightening is present throughout
the rainy season in many areas, but an attack and its associated risk of
loss only exist for the duration of an actual lightening.
We will look at the major types of attacks, used against information
systems, in the subsequent sections.
2.3.2.1 Malware Attacks
The malicious code attack includes the execution of viruses, worms,
Trojan horses, and any other malicious code with the intention of
destroying or stealing information. The most sophisticated malicious
code attack is the polymorphic, or multivector, worm. These attack
ISEC-210 Module Guide – A.N. Chongwe Page | 14
programs exploit a variety of vulnerabilities in commonly found
information system devices.
2.3.2.2 Denial of service (DoS) attack
A denial of service (DoS) attack is an attack designed to overwhelm a
machine or server with excessive requests, with the ultimate goal of
preventing it from handling legitimate requests and traffic. Unlike other
threats, the aim of a DoS attack is not to steal information but to slow
or take down a network service such as a website.
Figure 2.4 – DoS and DDoS attacks
An attack of this sort in which many computers are hijacked and used to
flood the target with so many requests than the server can handle,
thereby blocking normal traffic, is called a distributed denial of service
(DDoS) attack. DDoS attacks can be disastrous for companies that make
their money operating online, potentially causing millions in lost
revenue every day the service is down. The British Internet service
provider Cloudnine is believed to be the first business affected by a
denial-of-service attack in January 2002.
ISEC-210 Module Guide – A.N. Chongwe Page | 15
2.3.2.3 Password Cracking
Attempting to reverse-calculate a password is often called cracking.
Simply put, password cracking is the process of recovering the password.
It is used when a copy of the password file e.g. Security Account
Manager (SAM), which contains hashed representation of the user’s
password, can be obtained. A password can be hashed using the same
algorithm and compared to the hashed results. If they are the same, the
password has been cracked.
2.3.2.4 Brute Force Attack
The application of computing and network resources to try every
possible password combination is called a brute force attack. Since the
brute force attack is often used to obtain passwords to commonly used
accounts, it is sometimes called a password attack. If attackers can
narrow the field of target accounts, they can devote more time and
resources to these accounts. That is one reason to always change the
manufacturer’s default administrator account names and passwords.
Password attacks are rarely successful against systems that have adopted
the manufacturer’s recommended security practices. Controls that limit
the number of unsuccessful access attempts allowed per unit of elapsed
time are very effective against brute force attacks.
2.3.2.5 Dictionary Attack
The dictionary attack is a variation of the brute force attack which
narrows the field by selecting specific target accounts and using a list of
commonly used passwords (the dictionary) instead of random
ISEC-210 Module Guide – A.N. Chongwe Page | 16
combinations. Organizations can use similar dictionaries to disallow
passwords during the reset process and thus guard against easy-to-guess
passwords. In addition, rules requiring numbers and/or special characters
in passwords make the dictionary attack less effective.
2.3.2.6 Man-in-the-Middle Attack
A man-in-the-middle (MiTM) attack requires three players – the victim,
the entity with which the victim is trying to communicate, and the
attacker or “man in the middle,” who is intercepting the victim’s
communications.
Figure 2.5 – MiTM attack.
Critical to the scenario is that the victim is not aware of the man in the
middle. In the well-known man-in-the-middle or TCP hijacking attack,
an attacker monitors (or sniffs) packets from the network, modifies
them, and inserts them back into the network. This type of attack uses
IP spoofing to enable an attacker to impersonate another entity on the
network. It allows the attacker to eavesdrop as well as to change, delete,
reroute, add, forge, or divert data.
ISEC-210 Module Guide – A.N. Chongwe Page | 17
2.3.2.7 Social Engineering
Not all attacks are technological in nature. Social engineering is the
process of using social skills to convince people to reveal access
credentials or other valuable information to the attacker. There are
several social engineering techniques, which usually involve a
perpetrator posing as a person higher in the organizational hierarchy
than the victim or an attacker pretending to be someone. To prepare
for this false representation, the perpetrator may have used social
engineering tactics against others in the organization to collect seemingly
unrelated information that, when used together, makes the false
representation more credible. Social engineering attacks may involve
individuals posing as new employees or as current employees requesting
assistance. Sometimes attackers threaten, persuade, or beg to sway the
target in giving them information that was not supposed to be given to
them.
2.4 Information Security Risk
Information security risk comprises the impacts to an organization and
its stakeholders that could occur due to the threats and vulnerabilities
associated with the operation and use of information systems and the
environments in which those systems operate. The primary means of
mitigating information security-related risk is through the selection,
implementation, maintenance, and continuous monitoring of
preventive, detective, and corrective security controls to protect
information assets from compromise or to limit the damage to the
organization should a compromise occur. Information security risk
ISEC-210 Module Guide – A.N. Chongwe Page | 18
overlaps with many other types of risk in terms of the kinds of impact
that might result from the occurrence of a security-related incident.
2.5 Information Security Vulnerabilities
In order to understand information security vulnerability, we need to
first understand what a vulnerability is. A vulnerability is, in broad terms,
a weak spot in your defense. Every organization has multiple security
measures to protect its assets. We can think of such security measures as
the fence around your house. Vulnerabilities are cracks and openings in
this fence. Through information security vulnerabilities, an unauthorized
person can find his or her way into your information thereby posing
danger of deleting, copying, modifying or preventing other legitimate
users accessing the data. Information security vulnerability refers to any
kind of exploitable weak spot that threatens the security of an
organization's information. For example, if an organization does not
have lock on its front door, this poses a security vulnerability since one
can easily come in and steal something like a desktop computer or a
laptop.
Similarly, if the organization does not have proper firewalls, antivirus
software, or authentication mechanisms in there systems, an intruder can
easily find their way to the organisation's information. Since the asset
under threat is a digital one, not having proper measures poses
information security vulnerability.
ISEC-210 Module Guide – A.N. Chongwe Page | 19
Unit Summary
In this Unit, we looked at the common types of threats and attacks to
information systems. We first looked at categories of threats, such as
malwares, technical hardware and software failures and the common
attacks to information systems. We concluded with a brief on
information security risk and vulnerabilities.
ISEC-210 Module Guide – A.N. Chongwe Page | 20
Unit Activity
1. Define the following terms;
a. Threat
b. Attack
c. Vulnerability
2. What is the main difference between a virus and a worm?
3. How does a ransomware differ from a spyware?
4. Categorise the following as a threat, an attack, or a vulnerability:
Social engineering, malware, password cracking, denial of service,
brute force ransomware, lightening or thunder, man in the
middle, SQL injection, employee personal laptop
5. Justify all the categorizations in question 5.
6. What is information extortion? Describe how such an attack can
cause losses.
7. Explain how technology obsolescence can affect information
security is as far as availability is concerned
ISEC-210 Module Guide – A.N. Chongwe Page | 21
References
1. Whitman, M.E., Mattord, H.J. (2012). Principles of information
security (4th ed.). Boston: Thomson Educational.
2. Whitman, M. E., & Mattord, H. J. (2013). Management of
information security. Nelson Education.
3. Fogla, P., Sharif, M. I., Perdisci, R., Kolesnikov, O. M., & Lee, W.
(2006, August). Polymorphic Blending Attacks. In USENIX
security symposium (pp. 241-256).
ISEC-210 Module Guide – A.N. Chongwe Page | 22
ISEC-210 Module Guide – A.N. Chongwe Page | 23
You might also like
- CEH: Certified Ethical Hacker v11 : Exam Cram Notes - First Edition - 2021From EverandCEH: Certified Ethical Hacker v11 : Exam Cram Notes - First Edition - 2021No ratings yet
- David Jose and Francesca Almato-Banfield's Affidavit Repudiation To Dept of StateDocument31 pagesDavid Jose and Francesca Almato-Banfield's Affidavit Repudiation To Dept of StateThe Daily Haze100% (1)
- Iss-Assignment IIDocument36 pagesIss-Assignment IImelesse bisema50% (2)
- Flight International World Air FORCES 2016Document36 pagesFlight International World Air FORCES 2016bashirsba100% (1)
- Chapter 2 - The Need For SecurityDocument17 pagesChapter 2 - The Need For SecurityAshura OsipNo ratings yet
- IT10 Module1 MelendresDocument7 pagesIT10 Module1 MelendresValerie MelendresNo ratings yet
- IT10 Module1 MelendresDocument7 pagesIT10 Module1 MelendresValerie MelendresNo ratings yet
- Introduction To Cyber SecurityDocument11 pagesIntroduction To Cyber SecurityDeepika SharmaNo ratings yet
- College of Engineering and Technology School of Computing and Informatics Department of Information TechnologyDocument16 pagesCollege of Engineering and Technology School of Computing and Informatics Department of Information TechnologyAbdataa waaqaaNo ratings yet
- CSS4-Q1 Module 2Document10 pagesCSS4-Q1 Module 2Lielanie NavarroNo ratings yet
- Unit 1 (CSS)Document10 pagesUnit 1 (CSS)hasansyedamanNo ratings yet
- W7 Lesson 7 - Introduction To Information Security - ModuleDocument8 pagesW7 Lesson 7 - Introduction To Information Security - ModuleDagsman DieciemNo ratings yet
- Comprehensive LabDocument32 pagesComprehensive LabSudharsan BalaNo ratings yet
- Information Security in GeneralDocument12 pagesInformation Security in GeneralAliNo ratings yet
- IT 101 - Chapter 3Document10 pagesIT 101 - Chapter 3Val PaladoNo ratings yet
- Internship Project ReportDocument82 pagesInternship Project Reportudhiman681No ratings yet
- Monitor Threats To The NetworkDocument12 pagesMonitor Threats To The NetworkAlage TekaNo ratings yet
- Unit II Info Sec Question Ans cs1014Document12 pagesUnit II Info Sec Question Ans cs1014N.VivekananthamoorthyNo ratings yet
- Ifs Chap 1Document22 pagesIfs Chap 1moviesera851No ratings yet
- IT NS 1 - Chapter 1b Types of Attacks and DetectionDocument6 pagesIT NS 1 - Chapter 1b Types of Attacks and DetectionGALAPON FRANCISNo ratings yet
- Chapter 2 - The Need For SecurityDocument34 pagesChapter 2 - The Need For SecurityDana E. AranasNo ratings yet
- Modlue 4: Cybersecurity Awareness: ObjectivesDocument9 pagesModlue 4: Cybersecurity Awareness: ObjectivesJulie RamosNo ratings yet
- Submitted By:: Shweta Verma Ashaina Neha KumariDocument10 pagesSubmitted By:: Shweta Verma Ashaina Neha Kumariamitkumarpal2571No ratings yet
- Social EngineeringDocument10 pagesSocial Engineeringjpaul42391No ratings yet
- Safety, System Security and Safe ComputingDocument40 pagesSafety, System Security and Safe Computingobua markNo ratings yet
- IT Security 20210426203847Document60 pagesIT Security 20210426203847ChandanaNo ratings yet
- IT Security 20210426203847Document60 pagesIT Security 20210426203847Abhijeet RaoNo ratings yet
- Taimur Info Ass 2 - 2Document6 pagesTaimur Info Ass 2 - 2Furqan WhtsappNo ratings yet
- Chapter 2 - Attacks, Concepts and TechniquesDocument21 pagesChapter 2 - Attacks, Concepts and TechniquesS. M. AkashNo ratings yet
- Cristo Rey Reforsado - Assignment 5Document3 pagesCristo Rey Reforsado - Assignment 5Grazelyn RabeNo ratings yet
- Group 1Document9 pagesGroup 1Raphy OctaNo ratings yet
- Assignment02 NahidurDocument5 pagesAssignment02 NahidurMD Nahidur RahmanNo ratings yet
- Cyber Security Notes Unit 1Document9 pagesCyber Security Notes Unit 1Reshma BasuNo ratings yet
- Lecture 02 - Information Security Threats and AttacksDocument26 pagesLecture 02 - Information Security Threats and AttacksCarlitos MandalaNo ratings yet
- 1st Activity - IMSDocument4 pages1st Activity - IMSJhun Mar T. BelloNo ratings yet
- IT 111 Module 05 MalwareDocument8 pagesIT 111 Module 05 MalwareExodus GreyratNo ratings yet
- Cyber SecurityDocument9 pagesCyber Securityadeebkhan072004No ratings yet
- Cyber Security FinalDocument6 pagesCyber Security FinalDivyasriNo ratings yet
- EFISDocument12 pagesEFISHiếu VănNo ratings yet
- BTICS501 Network Security & Cryptography (Unit-1 To 5)Document90 pagesBTICS501 Network Security & Cryptography (Unit-1 To 5)svvv ganduNo ratings yet
- ITSecurity 20210426203847Document60 pagesITSecurity 20210426203847Razor -No ratings yet
- ISEC-210 UNIT 01 - Introduction To Information SecurityDocument15 pagesISEC-210 UNIT 01 - Introduction To Information SecurityCarlitos MandalaNo ratings yet
- Cyber Security-NotesDocument49 pagesCyber Security-NotesReshma BasuNo ratings yet
- LO1 Asset and Security Threat Week 02Document40 pagesLO1 Asset and Security Threat Week 02kaung kyaw zaNo ratings yet
- Cyber Security Introduction Latest Cyber Security Threats 5594e707Document10 pagesCyber Security Introduction Latest Cyber Security Threats 5594e707Lý Nghĩa PhanNo ratings yet
- Threats To Information SecurityDocument21 pagesThreats To Information SecurityGetnete degemuNo ratings yet
- Emerging Technologies34Document12 pagesEmerging Technologies34teddyNo ratings yet
- Assignment02 NahidurDocument5 pagesAssignment02 NahidurMD Nahidur RahmanNo ratings yet
- Information Security All ChapterDocument73 pagesInformation Security All ChapterbilisummaaNo ratings yet
- Information Assistant and SecurityDocument9 pagesInformation Assistant and SecurityWala LangNo ratings yet
- Computer Security and EthicsDocument5 pagesComputer Security and EthicsHumphrey Mwila ChilesheNo ratings yet
- Introduction To Cyber Security Handbook PDFDocument104 pagesIntroduction To Cyber Security Handbook PDFVjay MadhamNo ratings yet
- Cybersecurity PrologueDocument44 pagesCybersecurity PrologueRaj Prabhu RajendranNo ratings yet
- 03 - CO1-ethical Hacking TerminologiesDocument53 pages03 - CO1-ethical Hacking TerminologiesWoyNo ratings yet
- Lecture 1 - Network Security BasicsDocument7 pagesLecture 1 - Network Security BasicsHillary AyabeiNo ratings yet
- Unit 5 Computer SecurityDocument12 pagesUnit 5 Computer SecurityPauline TorionNo ratings yet
- Chapter 1 Introduction and Security TrendDocument10 pagesChapter 1 Introduction and Security TrendNARESH BADWENo ratings yet
- IS STR and MGMNT - 2Document11 pagesIS STR and MGMNT - 2Hizbe EthiopiaNo ratings yet
- Cyber SecurityDocument20 pagesCyber SecuritydeadasmpNo ratings yet
- Network Security: Ict - Css Third Quarter - Week 9 - Module 9Document12 pagesNetwork Security: Ict - Css Third Quarter - Week 9 - Module 9Kaylene VillaNo ratings yet
- CYBER SECURITY HANDBOOK Part-1: Hacking the Hackers: Unraveling the World of CybersecurityFrom EverandCYBER SECURITY HANDBOOK Part-1: Hacking the Hackers: Unraveling the World of CybersecurityNo ratings yet
- Cybersecurity and Ethical Hacking: Exploring the Dark Art of Ethical Hacking and Penetration TestingFrom EverandCybersecurity and Ethical Hacking: Exploring the Dark Art of Ethical Hacking and Penetration TestingNo ratings yet
- NR1 NR1: Malawian CitizensDocument2 pagesNR1 NR1: Malawian CitizensKutemwa MithiNo ratings yet
- OSYS-210 Course OutlineDocument3 pagesOSYS-210 Course OutlineKutemwa MithiNo ratings yet
- Lecture 02 Oop210Document17 pagesLecture 02 Oop210Kutemwa MithiNo ratings yet
- Data Structure and Algorithm Sample QuestionsDocument5 pagesData Structure and Algorithm Sample QuestionsKutemwa MithiNo ratings yet
- Dsal-211 Assignment 1Document2 pagesDsal-211 Assignment 1Kutemwa MithiNo ratings yet
- Drug Dependence & AlcoholismDocument2 pagesDrug Dependence & AlcoholismJayselle BacaltosNo ratings yet
- ILEI Forms of Legal Reasoning 2014Document16 pagesILEI Forms of Legal Reasoning 2014JeralynNo ratings yet
- Criminal Law 2 Andrea de GuzmanDocument2 pagesCriminal Law 2 Andrea de GuzmanAndrea Gural De GuzmanNo ratings yet
- England Report enDocument42 pagesEngland Report enIovu CiprianNo ratings yet
- BacoorDocument24 pagesBacoorAliahMharuPabloNo ratings yet
- 20) Mighty Corporation vs. E. & J. Gallo WineryDocument34 pages20) Mighty Corporation vs. E. & J. Gallo WineryYap, Nathalie JeanNo ratings yet
- Script ProgrMDocument2 pagesScript ProgrMvenice gabrielleNo ratings yet
- Insolvency and Bankruptcy Board of India NCLT - ChennaiDocument2 pagesInsolvency and Bankruptcy Board of India NCLT - ChennaiGuna KrishNo ratings yet
- Cadet Guide 2015Document98 pagesCadet Guide 2015api-280106412No ratings yet
- Importance of Islamic MonthsDocument54 pagesImportance of Islamic MonthsRizwan Ahmed100% (2)
- Pak StudiesDocument21 pagesPak StudiesMy life choiceNo ratings yet
- Quisay v. People - GR No. - J. Perlas-Bernabe - January 13, 2016 - Who Must ProsecuteDocument3 pagesQuisay v. People - GR No. - J. Perlas-Bernabe - January 13, 2016 - Who Must ProsecuteSienna Nacario100% (1)
- 11 Warning Signs of GaslightingDocument2 pages11 Warning Signs of Gaslightingsimon8schumacherNo ratings yet
- New Evidence Reveals ARSA Massacred Scores in Rakhine StateDocument23 pagesNew Evidence Reveals ARSA Massacred Scores in Rakhine Stateebooks library home blogNo ratings yet
- Kelas Kick BoxingDocument5 pagesKelas Kick BoxingNurhazwaniSyahrinNo ratings yet
- Fight Your Tickets:A Comprehensive Guide To Traffic TicketsDocument249 pagesFight Your Tickets:A Comprehensive Guide To Traffic TicketsFight Your Tickets100% (5)
- Sites Am-Rr - Filtro CMDocument38 pagesSites Am-Rr - Filtro CMPanela QuenteNo ratings yet
- The Daily Stoic 366 Meditations On Wisdom, Perseverance, and The Art of Living (PDFDrive) - 51-55Document5 pagesThe Daily Stoic 366 Meditations On Wisdom, Perseverance, and The Art of Living (PDFDrive) - 51-55map 7alleNo ratings yet
- Fortich Vs Corona Case DigestDocument6 pagesFortich Vs Corona Case DigestMonica Bolado-AsuncionNo ratings yet
- 2012 Alabama Precinct Election ResultsDocument196 pages2012 Alabama Precinct Election ResultsJohn MNo ratings yet
- Compilation of Case Digest For Due Process of LawDocument19 pagesCompilation of Case Digest For Due Process of LawJay Mark BalbosaNo ratings yet
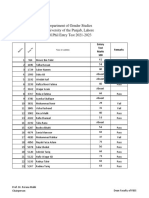
- Entry Test Result of M.phil Gender Studies 2021Document12 pagesEntry Test Result of M.phil Gender Studies 2021Shariq WaheedNo ratings yet
- Proclamation of Independence, 17 April 1971: East West University GEN 226 / Lecture 17Document11 pagesProclamation of Independence, 17 April 1971: East West University GEN 226 / Lecture 17Md SafiNo ratings yet
- Violent Video GamesDocument8 pagesViolent Video GamesRodrigo RojasNo ratings yet
- Alaska Inmate Search Department of Corrections LookupDocument4 pagesAlaska Inmate Search Department of Corrections LookupinmatesearchinfoNo ratings yet
- Alitiw ZamoraDocument9 pagesAlitiw Zamorakendrick.belgaNo ratings yet
- Iloilo Traders Finance Inc. VS Heirs of Soriano's G.R. No. 149683 June 16, 2003Document1 pageIloilo Traders Finance Inc. VS Heirs of Soriano's G.R. No. 149683 June 16, 2003Jay VeeNo ratings yet
- Lesson 3 CitizenshipDocument53 pagesLesson 3 CitizenshipkvelezNo ratings yet