100% found this document useful (1 vote)
255 views42 pagesNetwork Security Lab Report Summary
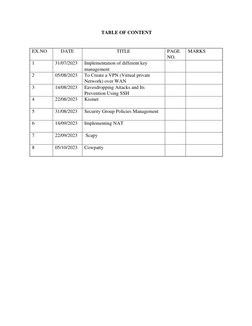
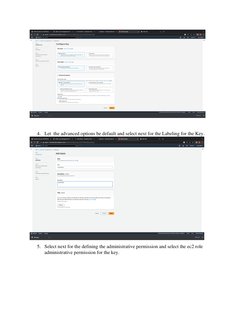
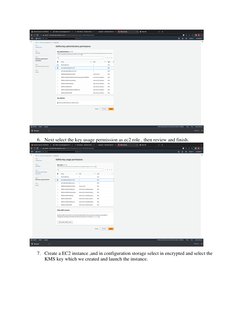
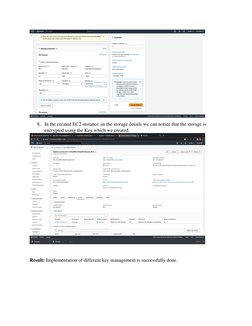
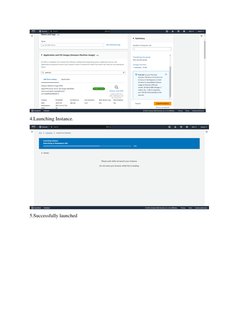
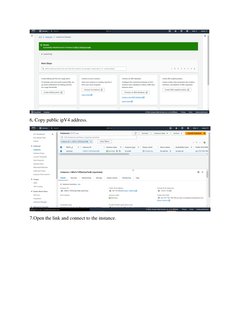
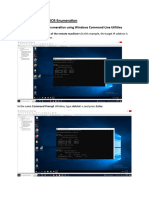
This document outlines procedures for implementing and managing security group policies in AWS. It discusses creating group policy objects and linking them to organizational units to apply settings like disabling Windows Messenger. It also describes determining which policies apply to a user or computer using the Group Policy Results Wizard and some common security settings that can be configured like password policies. The goal is to centrally manage security settings and access controls through group policies.
Uploaded by
Beññish Jőĥñ LèóCopyright
© © All Rights Reserved
We take content rights seriously. If you suspect this is your content, claim it here.
Available Formats
Download as PDF, TXT or read online on Scribd
100% found this document useful (1 vote)
255 views42 pagesNetwork Security Lab Report Summary
This document outlines procedures for implementing and managing security group policies in AWS. It discusses creating group policy objects and linking them to organizational units to apply settings like disabling Windows Messenger. It also describes determining which policies apply to a user or computer using the Group Policy Results Wizard and some common security settings that can be configured like password policies. The goal is to centrally manage security settings and access controls through group policies.
Uploaded by
Beññish Jőĥñ LèóCopyright
© © All Rights Reserved
We take content rights seriously. If you suspect this is your content, claim it here.
Available Formats
Download as PDF, TXT or read online on Scribd
![20CSE522J-NETWORK SECURITY
LAB REPORT
Submitted by
Lakshman Prasath.R [Reg.No:RA2212033010018]
Under the Guidance o](https://screenshots.scribd.com/Scribd/252_100_85/326/691569469/1.jpeg)