Professional Documents
Culture Documents
Attacks On Passwords
Attacks On Passwords
Uploaded by
c3074474Original Description:
Original Title
Copyright
Available Formats
Share this document
Did you find this document useful?
Is this content inappropriate?
Report this DocumentCopyright:
Available Formats
Attacks On Passwords
Attacks On Passwords
Uploaded by
c3074474Copyright:
Available Formats
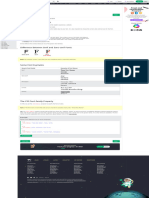
Attacker gains physical
Resetting access to computer and
resets password
Not really practical -
Online guessing
will take TOO long
Phishing, shoulder
surfing, dumpster Social engineering
diving
Keylogger, protocol
analyser (e.g.,
Wireshark)
Capturing
Method used by most
Man-in-the-middle and password attacks today
replay attacks Attacks on Passwords
Compare with
Attackers steal file with
Substituting letters/ encrypted passwords
encrypted password
placing numbers within they have created
words
Offline cracking
Every possible
Spelling words combination of letters,
backwards numbers, and
Slightly alter dictionary
Hybrid attack 1. Brute force characters used to
words
create encrypted
Slightly misspelling passwords and matched
words against stolen file
Offline cracking types:
Including special Attacker creates
characters encrypted versions of
common dictionary
2. Dictionary attack
words, Compares
against stolen password
Large pre-generated file
data set of encrypted
passwords
Used for reversing
cryptographic hash
Rainbow tables functions
Used in recovering a
plaintext password up
to a certain length
consisting of a limited
set of characters
You might also like
- CAT c15 Ecm PinoutDocument13 pagesCAT c15 Ecm Pinoutmohamedfatoh87% (15)
- Barbershop Booking System 2Document39 pagesBarbershop Booking System 2eymannNo ratings yet
- OM - 11594020 - NIRWise Plus Software - enDocument34 pagesOM - 11594020 - NIRWise Plus Software - enSamuel SuNo ratings yet
- Table of Learning Materials - Reading (7A 2A) Table of Learning Materials - Reading (7A 2A)Document4 pagesTable of Learning Materials - Reading (7A 2A) Table of Learning Materials - Reading (7A 2A)Vijay AntonyNo ratings yet
- Data Type For Word Documents Handling: WorddocumentDocument9 pagesData Type For Word Documents Handling: WorddocumentciganoNo ratings yet
- Password Cracking Detection System With Honeyword: Florita Sylvester TuscanoDocument4 pagesPassword Cracking Detection System With Honeyword: Florita Sylvester TuscanoEditor IJRITCCNo ratings yet
- Class Password Hacking 2023Document38 pagesClass Password Hacking 2023AyushNo ratings yet
- Comprehensive Data Tracking ResourceDocument9 pagesComprehensive Data Tracking ResourceJenna HaynieNo ratings yet
- Password Cracking Technique: A Survey: Himanshu Kumar, Neelam MathurDocument3 pagesPassword Cracking Technique: A Survey: Himanshu Kumar, Neelam MathurNamrata PaudelNo ratings yet
- Types of Printed DocumentsDocument3 pagesTypes of Printed DocumentsdesbestNo ratings yet
- Password Data Security-ENG (iSEC)Document9 pagesPassword Data Security-ENG (iSEC)Jhon Fredrick KeliatNo ratings yet
- Unhashing Passwords: Asst. Prof. Rajesh Dhakad Rhythum TamraDocument4 pagesUnhashing Passwords: Asst. Prof. Rajesh Dhakad Rhythum TamrarhythumtNo ratings yet
- 1b. Explain The Characteristics of The Given Java Token.Document8 pages1b. Explain The Characteristics of The Given Java Token.Hemant ThawaniNo ratings yet
- Ipad Apps For Complex Communication Support NeedsDocument1 pageIpad Apps For Complex Communication Support Needsapi-403858721No ratings yet
- Who Usually Use Dictionary Attack?Document9 pagesWho Usually Use Dictionary Attack?Princess Gift ParconNo ratings yet
- Compiler SDocument43 pagesCompiler SRachit SrivastavNo ratings yet
- Csharp-Roadmap DrawioDocument1 pageCsharp-Roadmap Drawiobabaoarba0000No ratings yet
- Cempedak - Computer AttacksDocument1 pageCempedak - Computer AttacksAnis SofiaNo ratings yet
- Lab 1 DFDDocument1 pageLab 1 DFDPac SaQiiNo ratings yet
- Password PresentationDocument15 pagesPassword PresentationRisabh ShuklaNo ratings yet
- Document 2 UeDr 10022016Document12 pagesDocument 2 UeDr 10022016Msik MssiNo ratings yet
- Password Defences Password PoliciesDocument1 pagePassword Defences Password Policieslavanya.puri14No ratings yet
- A Comparison Between Brute-Force & Rainbow AttacksDocument2 pagesA Comparison Between Brute-Force & Rainbow Attacksdonia hussinNo ratings yet
- Honey Encryption - 1Document7 pagesHoney Encryption - 1Cent SecurityNo ratings yet
- Password Policy InfographicDocument1 pagePassword Policy InfographicPedro Manuel MendezNo ratings yet
- Password Security: How Passwords Are Cracked..Document1 pagePassword Security: How Passwords Are Cracked..Denny TobingNo ratings yet
- Cache Memory MappingDocument8 pagesCache Memory MappingAman DubeyNo ratings yet
- Password Manager SynopsisDocument5 pagesPassword Manager SynopsisKavin LartiusNo ratings yet
- Statistical Models Based Password Candidates Generation For Specified Language Used in Wireless LAN Security AuditDocument4 pagesStatistical Models Based Password Candidates Generation For Specified Language Used in Wireless LAN Security Auditmgtar2006No ratings yet
- DomainmodelDocument1 pageDomainmodelhadiyafaisal15No ratings yet
- Honey Encryption - 1Document7 pagesHoney Encryption - 1Cent SecurityNo ratings yet
- Fast Multi-Language LSTM-based Online Handwriting RecognitionDocument14 pagesFast Multi-Language LSTM-based Online Handwriting RecognitionAnastasia SusciucNo ratings yet
- English Unpacked CG G3 Q1Q2Q3Q4 1Document116 pagesEnglish Unpacked CG G3 Q1Q2Q3Q4 1reachel ann orcaNo ratings yet
- Cisco Mfa Password Security Infographic PDFDocument1 pageCisco Mfa Password Security Infographic PDFCharismatic ArslanNo ratings yet
- Big Ideas: Objectives: Resources: Differentiation: Exceeding: To CreateDocument3 pagesBig Ideas: Objectives: Resources: Differentiation: Exceeding: To CreatekairaliNo ratings yet
- Securing Network and It InfrastructureDocument13 pagesSecuring Network and It InfrastructureBhuvi VermaNo ratings yet
- Red Team Ops - Mind MapDocument1 pageRed Team Ops - Mind Map0xt3stNo ratings yet
- Base Monospace: Zuzana Licko Rudy VanderlansDocument6 pagesBase Monospace: Zuzana Licko Rudy VanderlansHaissarPintoNo ratings yet
- CSS FontsDocument1 pageCSS FontsbilicimehmettalhaNo ratings yet
- Assignment 2 (2583)Document6 pagesAssignment 2 (2583)Musheeza LiaqatNo ratings yet
- NIC AI Based Chatbot (Vani)Document2 pagesNIC AI Based Chatbot (Vani)Hitesh KumarNo ratings yet
- PictureDocument2 pagesPicturePooja JainNo ratings yet
- Language and ComputerDocument19 pagesLanguage and ComputerSyahiirah JaafarNo ratings yet
- 3 Compiler - SlideDocument8 pages3 Compiler - Slidegilbertelena7898No ratings yet
- Building A Multi-Lingual OCR EngineDocument21 pagesBuilding A Multi-Lingual OCR EngineYasserAl-mansourNo ratings yet
- Building A Multi-Lingual OCR EngineDocument21 pagesBuilding A Multi-Lingual OCR EnginerossloveladyNo ratings yet
- Tatli CrackingmorePasswordHasheswithPatterns FINAL-IEEEDocument12 pagesTatli CrackingmorePasswordHasheswithPatterns FINAL-IEEEMsik MssiNo ratings yet
- CSEC Study Guide - January 25, 2011Document12 pagesCSEC Study Guide - January 25, 2011Angel LawsonNo ratings yet
- LLM's Application and How They WorkDocument1 pageLLM's Application and How They WorkamitNo ratings yet
- VL2020210503423Document28 pagesVL2020210503423Captain ThejaNo ratings yet
- Grade 8 English Schemes of Work Term 1 LonghornDocument36 pagesGrade 8 English Schemes of Work Term 1 LonghornmosesforgivenNo ratings yet
- Rsa Netwitness PlatformDocument7 pagesRsa Netwitness Platformdoan nguyenNo ratings yet
- Unit 7 Working OnlineDocument3 pagesUnit 7 Working OnlineedzellNo ratings yet
- Gough's One Second of ReadingDocument2 pagesGough's One Second of Readingbaunsit.josepharnold.mccNo ratings yet
- Go To Page Word Fillable-1 1 - 1Document4 pagesGo To Page Word Fillable-1 1 - 1api-536496827No ratings yet
- Low Delay Burst Erasure Correction Codes: Emin Martinian Carl-Erik W. SundbergDocument5 pagesLow Delay Burst Erasure Correction Codes: Emin Martinian Carl-Erik W. Sundberghelmantico1970No ratings yet
- Access ControlDocument1 pageAccess Controlulhaqz2No ratings yet
- Holo Registration and SetupDocument18 pagesHolo Registration and SetupAdil SadikiNo ratings yet
- Word Prediction Using Trie Data Structure: J Component Project ReportDocument81 pagesWord Prediction Using Trie Data Structure: J Component Project ReportSPANDAN KUMARNo ratings yet
- Ed Adjectives: in Touch With Your FeelingsDocument2 pagesEd Adjectives: in Touch With Your FeelingsÖvünçNo ratings yet
- Desh Raj: Center For Language and Speech Processing Draj@cs - Jhu.eduDocument1 pageDesh Raj: Center For Language and Speech Processing Draj@cs - Jhu.edusantoso elektroNo ratings yet
- Vision and Scope Document: Version 1.0 ApprovedDocument8 pagesVision and Scope Document: Version 1.0 ApprovedMahammed Hasen MuhummedNo ratings yet
- b0700sz CDocument70 pagesb0700sz Cabdel taibNo ratings yet
- Building Andriod App StepsDocument40 pagesBuilding Andriod App StepsAbdulrazaq Saleh OkumuNo ratings yet
- Design and Implementation of A Campus Navigation Application PDFDocument86 pagesDesign and Implementation of A Campus Navigation Application PDFKen kanakiNo ratings yet
- Lesson 1 - Introduction To Computer NetworkDocument90 pagesLesson 1 - Introduction To Computer NetworktvdanNo ratings yet
- PUBG TutorialDocument3 pagesPUBG TutorialSarika BhabburNo ratings yet
- DLMS HandbookDocument68 pagesDLMS Handbookharsh100% (3)
- Clint Cha k726p 36012p Brochure 0325 enDocument2 pagesClint Cha k726p 36012p Brochure 0325 enDorin100% (1)
- BADocument18 pagesBAManickavel ManoharanNo ratings yet
- Q2 - (05+05 Marks) Write The Code For - A) Suppose Y...Document2 pagesQ2 - (05+05 Marks) Write The Code For - A) Suppose Y...Unlimited EchoNo ratings yet
- Embedded SystemsDocument25 pagesEmbedded SystemsVasavi MagadapalliNo ratings yet
- Chapter 4 - System Design Part 1Document9 pagesChapter 4 - System Design Part 1ShaluNo ratings yet
- Purpose: Post-Production Workflow ModelDocument2 pagesPurpose: Post-Production Workflow ModelLucifer RegeneratedNo ratings yet
- Transition To European Medical Device Regulation (MDR) : Ongoing ChallengesDocument23 pagesTransition To European Medical Device Regulation (MDR) : Ongoing ChallengesMohammed HammedNo ratings yet
- CamJam EduKit - Worksheet 2 - LEDsDocument5 pagesCamJam EduKit - Worksheet 2 - LEDsmbozhoNo ratings yet
- Packet TracerDocument2 pagesPacket TracerJuan RicardoNo ratings yet
- Computer Science Option A DatabaseDocument9 pagesComputer Science Option A DatabaseKrish Madhav ShethNo ratings yet
- Quick Start Guide - Barco - Encore E2Document2 pagesQuick Start Guide - Barco - Encore E2OnceUponAThingNo ratings yet
- Sarscape For Envi: A Complete Sar Analysis SolutionDocument47 pagesSarscape For Envi: A Complete Sar Analysis SolutionDimas AkhdanNo ratings yet
- RRV2090 DV-515Document50 pagesRRV2090 DV-515Victor Javelosa Azuelo Jr.No ratings yet
- (Junos) How To Mount A USB Drive On The EX - SRXDocument3 pages(Junos) How To Mount A USB Drive On The EX - SRXLi KangNo ratings yet
- Reinforcement Learning Is Direct Adaptive Optimal Control: Richard S. Sutton, Andrew G. Barto, Ronald J. WilliamsDocument7 pagesReinforcement Learning Is Direct Adaptive Optimal Control: Richard S. Sutton, Andrew G. Barto, Ronald J. Williamshewitt0724No ratings yet
- ClansmanDocument6 pagesClansmandarkeagle111No ratings yet
- Littelfuse RC Snubber Networks For Thyristor Power Control and Transient Suppression PDFDocument22 pagesLittelfuse RC Snubber Networks For Thyristor Power Control and Transient Suppression PDFWafik RkabNo ratings yet
- Diff. BW FM N SubroutineDocument1 pageDiff. BW FM N SubroutineHarish GaddamNo ratings yet
- Developing 4X5 Sheet Film An Alternative MethodDocument4 pagesDeveloping 4X5 Sheet Film An Alternative MethodIhsan BalkisNo ratings yet
- Chapter Seven: Electronic Training Methods Multiple-Choice QuestionsDocument8 pagesChapter Seven: Electronic Training Methods Multiple-Choice QuestionsNotesfreeBook100% (1)