Professional Documents
Culture Documents
Chapter 2 Practise Questions
Uploaded by
Warrior-TankiCopyright
Available Formats
Share this document
Did you find this document useful?
Is this content inappropriate?
Report this DocumentCopyright:
Available Formats
Chapter 2 Practise Questions
Uploaded by
Warrior-TankiCopyright:
Available Formats
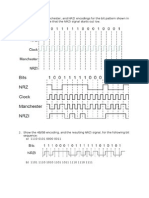
QUESTION 1.
5 Parity checks are often used to check for errors that may occur during data transmission.
(a) A system uses even parity.
Tick (✓) to show whether the following three bytes have been transmitted correctly or
incorrectly.
Received byte Byte transmitted correctly Byte transmitted incorrectly
11001000
01111100
01101001
[3]
(b) A parity byte is used to identify which bit has been transmitted incorrectly in a block of data.
The word “F L O W C H A R T” was transmitted using nine bytes of data (one byte per
character). A tenth byte, the parity byte, was also transmitted.
The following block of data shows all ten bytes received after transmission. The system uses
even parity and column 1 is the parity bit.
letter column column column column column column column column
1 2 3 4 5 6 7 8
byte 1 F 1 0 1 0 0 1 1 0
byte 2 L 1 0 1 0 1 1 0 0
byte 3 O 1 0 1 0 1 1 1 1
byte 4 W 1 0 1 1 0 1 1 1
byte 5 C 1 0 1 0 0 0 1 1
byte 6 H 0 0 1 0 1 0 0 0
byte 7 A 0 0 1 0 0 1 0 1
byte 8 R 1 0 1 1 0 0 1 0
byte 9 T 1 0 1 1 0 1 0 0
parity
1 0 1 1 1 1 1 0
byte
(i) One of the bits has been transmitted incorrectly.
Write the byte number and column number of this bit:
Byte number ......................................................................................................................
Column number .................................................................................................................
[2]
© UCLES 2015 0478/12/M/J/15
7
(ii) Explain how you arrived at your answer for part (b)(i).
...........................................................................................................................................
...........................................................................................................................................
...........................................................................................................................................
.......................................................................................................................................[2]
(c) Give the denary (base 10) value of the byte: 1 0111110
...................................................................................................................................................
...............................................................................................................................................[1]
(d) A parity check may not identify that a bit has been transmitted incorrectly.
Describe one situation in which this could occur.
...................................................................................................................................................
...................................................................................................................................................
...............................................................................................................................................[1]
© UCLES 2015 0478/12/M/J/15 [Turn over
QUESTION 2. 5
5 (a) Parity checks are often used to detect errors that may occur during data transmission.
The received bytes in the table below were transmitted using odd parity.
Tick (3) to show whether each byte has been corrupted during transmission or not
corrupted during transmission.
corrupted not corrupted
during during
Received byte
transmission transmission
(3) (3)
10110100
01101101
10000001
[3]
(b) Another method of error detection is Automatic Repeat reQuest (ARQ).
Explain how ARQ is used in error detection.
...................................................................................................................................................
...................................................................................................................................................
...................................................................................................................................................
...................................................................................................................................................
...................................................................................................................................................
...................................................................................................................................................
...................................................................................................................................................
...................................................................................................................................................
...................................................................................................................................................
.............................................................................................................................................. [4]
© UCLES 2017 0478/11/M/J/17 [Turn over
QUESTION 3. 7
7 Computer A is communicating with computer B.
(a) Draw an arrow or arrows to show simplex, duplex and half-duplex data transmission. The
direction of the data transmission must be fully labelled.
Simplex data transmission
Computer A Computer B
Duplex data transmission
Computer A Computer B
Half-duplex data transmission
Computer A Computer B
[6]
(b) State a use for the following data transmission methods. The use must be different for each
data transmission method.
Simplex .....................................................................................................................................
...................................................................................................................................................
Duplex ......................................................................................................................................
...................................................................................................................................................
[2]
© UCLES 2017 0478/12/M/J/17 [Turn over
QUESTION 4. 4
4 A company transmits data to external storage at the end of each day.
(a) Parity checks can be used to check for errors during data transmission.
The system uses odd parity.
(i) Tick (✓) to show for each of the received bytes whether they have been transmitted
correctly or transmitted incorrectly.
Received byte Transmitted Transmitted
correctly incorrectly
(✓) (✓)
10001011
10101110
01011101
00100101
[4]
(ii) State one other method that could be used to check for transmission errors.
...................................................................................................................................... [1]
(b) Data can be transferred using parallel or serial data transmission.
(i) Describe what is meant by parallel data transmission.
...........................................................................................................................................
...........................................................................................................................................
...........................................................................................................................................
...................................................................................................................................... [2]
(ii) Give one application of parallel data transmission.
...........................................................................................................................................
...................................................................................................................................... [1]
© UCLES 2018 0478/13/M/J/18
5
(iii) Explain why serial data transmission is normally used for transferring data over a long
distance.
...........................................................................................................................................
...........................................................................................................................................
...........................................................................................................................................
...................................................................................................................................... [2]
(c) Data transferred over a network is encrypted to improve data security.
The system uses 64-bit symmetric encryption.
(i) Explain how encryption improves data security.
...........................................................................................................................................
...........................................................................................................................................
...........................................................................................................................................
...................................................................................................................................... [2]
(ii) Explain one method that could be used to increase the level of security provided by the
encryption.
...........................................................................................................................................
...........................................................................................................................................
...........................................................................................................................................
...................................................................................................................................... [2]
© UCLES 2018 0478/13/M/J/18 [Turn over
QUESTION 5. 10
9 Four 7-bit binary values are being transmitted from one computer to another. An odd parity check
is being used to check for errors in the binary values.
Write the correct Parity bit for each 7-bit binary value to make sure it meets odd parity.
Parity bit 7-bit binary value
..................... 0000011
..................... 1000000
..................... 0111111
..................... 1010101
[4]
© UCLES 2020 0478/13/M/J/20
Buy O / A Level & IGCSE Original Books, Solved Past Papers & Notes Online at Discounted Prices.
Home Delivery all over Pakistan Call / WhatsApp: (0331-9977798) Visit: www.TeachifyMe.com/Shop
QUESTION 6. 4
4 A file server is used as a central data store for a network of computers.
Rory sends data from his computer to a file server that is approximately 100 metres away.
It is important that the data is transmitted accurately. Rory needs to be able to read data from and
write data to the file server at the same time.
(a) (i) Use ticks (3) to identify the most suitable data transmission methods for this application.
Method 1 Tick Method 2 Tick
(3) (3)
Serial Simplex
Parallel Half-duplex
Duplex
[2]
(ii) Explain why your answer to part (a)(i) is the most suitable data transmission.
...........................................................................................................................................
...........................................................................................................................................
...........................................................................................................................................
...........................................................................................................................................
...........................................................................................................................................
...........................................................................................................................................
...........................................................................................................................................
.......................................................................................................................................[4]
© UCLES 2017 0478/12/O/N/17
5
(b) Identify and describe two methods of error checking that can be used to make sure that the
data stored after transmission is accurate.
Method 1 ...................................................................................................................................
...................................................................................................................................................
...................................................................................................................................................
...................................................................................................................................................
...................................................................................................................................................
...................................................................................................................................................
...................................................................................................................................................
...................................................................................................................................................
Method 2 ...................................................................................................................................
...................................................................................................................................................
...................................................................................................................................................
...................................................................................................................................................
...................................................................................................................................................
...................................................................................................................................................
...................................................................................................................................................
...................................................................................................................................................
[6]
© UCLES 2017 0478/12/O/N/17 [Turn over
You might also like
- Ahmed Abid CS Past - Paper - AssignmentDocument9 pagesAhmed Abid CS Past - Paper - AssignmentWarrior-TankiNo ratings yet
- 1 2 1-Data-TransmissionDocument24 pages1 2 1-Data-TransmissionjesuNo ratings yet
- Computer Science (2210) Sample Paper For O Level 1Document9 pagesComputer Science (2210) Sample Paper For O Level 1Mehwish TahirNo ratings yet
- Computing SnaptestDocument3 pagesComputing Snaptesttedjackson608No ratings yet
- Error Detection and CorrectionDocument5 pagesError Detection and CorrectionVon Gary RasNo ratings yet
- Error Checking NoteDocument6 pagesError Checking NoteJackson EkoNo ratings yet
- Computer Science (2210) Sample Paper For O Level 2Document9 pagesComputer Science (2210) Sample Paper For O Level 2Mehwish TahirNo ratings yet
- cs64 2012 PDFDocument18 pagescs64 2012 PDFAyan RoyNo ratings yet
- 2 - 1. CN Data Link LayerDocument81 pages2 - 1. CN Data Link LayerPankaj DhullNo ratings yet
- Data and Computer Communications: Tenth Edition by William StallingsDocument21 pagesData and Computer Communications: Tenth Edition by William Stallingsbilal nagoriNo ratings yet
- 10 IGCSE CS Chapter 2 Comprehensive For Boards ExamDocument4 pages10 IGCSE CS Chapter 2 Comprehensive For Boards ExamShreyas ParekhNo ratings yet
- Lab # 7Document19 pagesLab # 7Farhan AslamNo ratings yet
- HW1 SolutionshDocument11 pagesHW1 SolutionshHrithik SharmaNo ratings yet
- Shift Registers - SISO - SIPO - PIPO - Oct 31Document6 pagesShift Registers - SISO - SIPO - PIPO - Oct 31Ravi CharanNo ratings yet
- 2 1 in A Particular Computer System, Real Numbers Are Stored Using Floating-Point Representation WithDocument15 pages2 1 in A Particular Computer System, Real Numbers Are Stored Using Floating-Point Representation WithNouman ShamimNo ratings yet
- Combinational Circuits Are Defined As The Time Independent Circuits Which Do NotDocument10 pagesCombinational Circuits Are Defined As The Time Independent Circuits Which Do NotBrilliant Billykash KashuwareNo ratings yet
- Quiz - 23 Data Transmission TechnologiesDocument8 pagesQuiz - 23 Data Transmission TechnologiesMugerwa CharlesNo ratings yet
- Lecture 08 Parity Generator and Checker EEE 357Document12 pagesLecture 08 Parity Generator and Checker EEE 357Shuvodip DasNo ratings yet
- Error DetectionDocument22 pagesError DetectionAdhara MukherjeeNo ratings yet
- Lab Bitstff, Hamming CodeDocument9 pagesLab Bitstff, Hamming Codekarpagam jeyakumarNo ratings yet
- Part 1: Adder and SubtracterDocument12 pagesPart 1: Adder and SubtracterVenus Ilagan100% (2)
- Digital Electronic4Document9 pagesDigital Electronic4TECH CHO3013No ratings yet
- Tutorial 5-7Document19 pagesTutorial 5-7lucyNo ratings yet
- Channel Coding ProblemsDocument6 pagesChannel Coding Problemssamaa saadNo ratings yet
- Digital Lab ReportDocument9 pagesDigital Lab ReportNg Ming FengNo ratings yet
- CH-06-DCC10e-Error Detection and CorrectionDocument22 pagesCH-06-DCC10e-Error Detection and Correctionmarwahamoudi8No ratings yet
- Revision Notes - 23 Data Transmission Technologies PDFDocument14 pagesRevision Notes - 23 Data Transmission Technologies PDFdemira lalNo ratings yet
- 4 Bit Adder SubtractorDocument15 pages4 Bit Adder SubtractorBiveyNo ratings yet
- BSC CS FY - 4 - Funda. of DEDocument21 pagesBSC CS FY - 4 - Funda. of DEVirendra RathodNo ratings yet
- 5 Error DetectionDocument10 pages5 Error DetectionLawrence Mashifta MachariaNo ratings yet
- Comp Assignment 1Document1 pageComp Assignment 1Chrissy ChrisNo ratings yet
- Lab3 ManualDocument13 pagesLab3 Manual02chng.jiadeNo ratings yet
- Faculty of Engineering Technology: Office Use OnlyDocument9 pagesFaculty of Engineering Technology: Office Use OnlyMadusanka WeebeddaNo ratings yet
- Computer Science CH 1 (Example Q&A)Document8 pagesComputer Science CH 1 (Example Q&A)Min KhantNo ratings yet
- Solution PDFDocument5 pagesSolution PDFCedric SunNo ratings yet
- Error Detection and CorrectionDocument21 pagesError Detection and CorrectionHamza AwanNo ratings yet
- Name: Izaan Ahmed Khan STD ID: FA19-BSCS-0049 COURSE: DLD Theory Assignment # 03Document10 pagesName: Izaan Ahmed Khan STD ID: FA19-BSCS-0049 COURSE: DLD Theory Assignment # 03Izaan Ahmed KhanNo ratings yet
- CCN Assignment: Name:-Hermain Fayyaz KarimDocument7 pagesCCN Assignment: Name:-Hermain Fayyaz KarimHermain Fayyaz KarimNo ratings yet
- Binary To Octal DecoderDocument4 pagesBinary To Octal DecoderJulfikar RahmanNo ratings yet
- 1 3 1-Logic-GatesDocument26 pages1 3 1-Logic-GatesjesuNo ratings yet
- EN1802 - Basic Electronics: S7 - Logic Gates and Circuits By: Dr. S. ThayaparanDocument9 pagesEN1802 - Basic Electronics: S7 - Logic Gates and Circuits By: Dr. S. ThayaparanAruna KumarasiriNo ratings yet
- Experiment 4Document5 pagesExperiment 4AAAAALLENNNo ratings yet
- Sheet No.5Document6 pagesSheet No.5samaa saadNo ratings yet
- Network ExerciseDocument3 pagesNetwork ExerciseSundari MuthuNo ratings yet
- Lecture Notes For Digital ElectronicsDocument43 pagesLecture Notes For Digital ElectronicsPV RKNo ratings yet
- Ovi 5Document6 pagesOvi 5Naimur Asif BornoNo ratings yet
- Question Paper Code:: Reg. No.Document3 pagesQuestion Paper Code:: Reg. No.ManimegalaiNo ratings yet
- Solution ST1 Set ADocument12 pagesSolution ST1 Set Agaurika.sawhney2003No ratings yet
- IIT Convolution CodesDocument11 pagesIIT Convolution CodesHarshaNo ratings yet
- Computer Science Paper 1 (70 Marks)Document4 pagesComputer Science Paper 1 (70 Marks)JD 1308No ratings yet
- Experiment 5Document3 pagesExperiment 5AAAAALLENNNo ratings yet
- Connectrix B-Series How To Interpret The Brocade Porterrshow Output, and What Do The Counters MeanDocument6 pagesConnectrix B-Series How To Interpret The Brocade Porterrshow Output, and What Do The Counters MeanHakim HamzaouiNo ratings yet
- WINSEM2021-22 CSE1004 ELA VL2021220502914 Reference Material I 20-01-2022 Class 7 Error Det CorrDocument47 pagesWINSEM2021-22 CSE1004 ELA VL2021220502914 Reference Material I 20-01-2022 Class 7 Error Det CorrSamriddh PrasadNo ratings yet
- CS3351 - DP & CO Notes - 03 - by WWW - Notesfree.inDocument213 pagesCS3351 - DP & CO Notes - 03 - by WWW - Notesfree.inbbook6930No ratings yet
- 3 Bit Synchronous Up CounterDocument15 pages3 Bit Synchronous Up CounterMaruf MorshedNo ratings yet
- Mock 2022Document9 pagesMock 2022Muhammad Ahsan SaleemNo ratings yet
- Switching Theory and Logic DesignDocument10 pagesSwitching Theory and Logic DesignRajkumarBattuNo ratings yet
- DCOM Univ PaperDocument9 pagesDCOM Univ Paper111ashwin0% (1)
- 8900d Radar Gauge - Calibration ManualDocument18 pages8900d Radar Gauge - Calibration ManualhussamNo ratings yet
- Error Correcting CodesDocument27 pagesError Correcting Codesjohn fisherNo ratings yet
- Manual Técnico Del Módulo IQ ModbusDocument57 pagesManual Técnico Del Módulo IQ ModbusGaleano Castrillonz AndresNo ratings yet
- 4 DLL Error ControlDocument7 pages4 DLL Error Controlraj25comNo ratings yet
- Arinc 429 PDFDocument32 pagesArinc 429 PDFparantnNo ratings yet
- CH 2Document6 pagesCH 2Munguntuya AltangerelNo ratings yet
- Spa BusDocument4 pagesSpa Busmanu2020No ratings yet
- 2.3 - Error Detection & CorrectionDocument19 pages2.3 - Error Detection & CorrectionbobjonesNo ratings yet
- Cat TM9000manualDocument3 pagesCat TM9000manualhs_handsomeNo ratings yet
- PS-In202SS Operators Manual EnglishSpanishDocument32 pagesPS-In202SS Operators Manual EnglishSpanishOdali100% (1)
- 5.1 RaidDocument14 pages5.1 Raidgidum2007100% (1)
- (英文) HART实用命令详解 PDFDocument11 pages(英文) HART实用命令详解 PDFvirgil guimanNo ratings yet
- Computer Organization Unit 4 AssignmentDocument4 pagesComputer Organization Unit 4 Assignmentsaiteja1234No ratings yet
- Error DetectDocument32 pagesError DetectclassNo ratings yet
- Biomedical Data ManagementDocument22 pagesBiomedical Data ManagementJonas MückeNo ratings yet
- Module 3 Information RedundancyDocument136 pagesModule 3 Information RedundancyynjuanNo ratings yet
- Digital ElectronicDocument17 pagesDigital Electronicfaiyaz pardiwalaNo ratings yet
- Digital Electronics UNIT 1Document67 pagesDigital Electronics UNIT 1Selva KumarNo ratings yet
- Circuit Diagram: Monostable Multivibrator:: +VCC 5VDocument25 pagesCircuit Diagram: Monostable Multivibrator:: +VCC 5VKAVIKRISHNAVEL TNo ratings yet
- Fireeye Network Threat Prevention PlatformDocument5 pagesFireeye Network Threat Prevention PlatformFernando PrietoNo ratings yet
- Digital ElectronicsDocument125 pagesDigital ElectronicsAditya SharmaNo ratings yet
- DD Notes Section1Document23 pagesDD Notes Section1mabuhzaimaNo ratings yet
- 2.9 Menu Bar and Toolbar (Options) Options: Chapter 2 Creating and Editing Screens - Scredit Software User ManualDocument11 pages2.9 Menu Bar and Toolbar (Options) Options: Chapter 2 Creating and Editing Screens - Scredit Software User ManualryoNo ratings yet
- AN3155 Application Note: USART Protocol Used in The STM32 BootloaderDocument42 pagesAN3155 Application Note: USART Protocol Used in The STM32 Bootloadersu ddNo ratings yet
- Lis Manual RMV10 - SW235Document4 pagesLis Manual RMV10 - SW235iheb nasrNo ratings yet
- Alarmes Mach 6Document25 pagesAlarmes Mach 6Marcos LemosNo ratings yet
- Error Control CodesDocument15 pagesError Control Codesابوالحجاج الجماعيNo ratings yet
- MATLAB To PIC Serial Interface PDFDocument5 pagesMATLAB To PIC Serial Interface PDFjose2525No ratings yet
- Improved Hamming Code For Error DetectionDocument20 pagesImproved Hamming Code For Error Detection陳鍾誠100% (1)
- B-84175EN/03 Troubleshooting: Figure 3.7.1-1 LED On The Main BoardDocument6 pagesB-84175EN/03 Troubleshooting: Figure 3.7.1-1 LED On The Main Boardkaori quinteroNo ratings yet