Professional Documents
Culture Documents
Vgs Black 01
Uploaded by
shahidshaikh565656Original Title
Copyright
Available Formats
Share this document
Did you find this document useful?
Is this content inappropriate?
Report this DocumentCopyright:
Available Formats
Vgs Black 01
Uploaded by
shahidshaikh565656Copyright:
Available Formats
A PROJECT REPORT
ON
VISITOR GATEPASS
SYSTEM
BY
Mr . Krushna Yuvraj Patil
And
Mr. Shiyon Joseph George
Towards The Partial Fulfillment of the
Bachelor Of Computer Application
Tilak Maharashtra Vidyapeeth Pune
Faculty of Regular Education
[2022-2023]
Certificate
This is to certify that the project’
“VISITOR GATEPASS SYSTEM”
Has been satisfactorily completed by
Mr. Krushna Y Patil
And
Mr. Shiyon Joseph George
Towards The Partial Fulfillment of the ‘Bachelor of
Computer Application’, For the Academic Year 2022-
2023 At Tilak Maharashtra Vidyapeeth , Pune (Faculty
of Regular Education )
And it is approved.
Project Guide Examiner Head of
Department
ACKNOWLEDGEMENT
“The successful” makes everyone happy. But the happiness will be gold
without glitter if we didn’t state the persons who have supported us to make it’s
a success.
Success will be crowned to people who have made it a reality but the
people whose constant guidance and encouragement made it possible will be
crowned first on the eve of success.
We have taken efforts in this project .However , it would not have been
possible without the kind support and help of many individuals. We would like
to extend my sincere thanks to all of them.
We are highly indebted to Miss. Shruti Gosavi for their guidance and
constant supervision as well as for providing necessary information regarding
the project & also for their support in completing the project.
We would like to express our gratitude toward HOD of computer Science
Department “For their kind co-operation and encouragement which help me in
completion of this project.
Last but not least, we thanks and appreciations also go to those people who
have willingly helped me out with their abilities , indirectly guided and helped
us in preparation of this project.
Mr. Krushna Yuvraj Patil Mr. Shiyon Joseph George
PRN:46420000104 PRN:46420000224
Table of Content
1. Introduction…………………………………………………………..04
1.1 Existing system……………………………………………………....07
1.2 Fact-finding techniques……………………………………………...08
1.3Need for system ……………………………………………………...10
1.4 Scope of the system …………………………………………………11
1.5 Feasibility study …………………………………………………….12
1.6 Background Information…………………………………………….16
1.7 Software requirements………………………………………………17
1.8Hardware requirements………………………………………………18
2. Proposed System…………………………………………………….19
2.1 The objective of the system…………………………………………20
2.2 User requirement……………………………………………………21
3. System Analysis and Design………………………………………...23
3.1 System Architecture ………………………………………………...26
3.2 Using Data Dictionary………………………………………………27
3.3 Introducing the Data Dictionary…………………………………….28
3.4 Database Table………………………………………………………30
4.0 UML Diagrams………...................................................................33
4.1 Use Case Diagram…………………………………………………34
VISITOR GATEPASS SYSTEM 4
4.2 Class Diagram…………………………………………………….36
4.3 Sequence Diagram………………………………………………..37
4.4 Activity Diagram………………………………………………....39
4.5 Component Diagram……………………………………………..40
VISITOR GATEPASS SYSTEM 5
1.Introduction
The Visitor Gatepass System App is a digital solution that allows organizations
to manage their visitors efficiently. This app helps to streamline the process of
issuing gate passes to visitors and ensures that all necessary security checks are
completed before granting access to the premises. The Visitor Gatepass System
app is a software application designed to manage and track visitors' entry and
exit from an organization or any other premises. This app can be used to
maintain a secure and organized environment by recording visitor details,
generating gate passes, and tracking their IN & OUT logs. This is a green
initiative that has less/no manual intervention and the use of paper. In the
traditional way of booking it use to be very easy to search or track any user
when the user base was less, but gradually when data grows it will be really a
challenge to manage data efficiently. This app/ solution solves all those
drawbacks. This solution is a need of the hour since the world is going through
a pandemic phase where less interaction with humans is recommended, this
solution makes sure your organization is not compromising security by
following general guidelines issued by the government.
The project Visitor Gatepass System is a client-server architecture application.
Has main Three modules client, server, and admin dashboard
1. Client is an Android app. Which is responsible for getting visitor details,
creating new visitor entries, and logging visit details. This is thin client all post
process is done at server end.
VISITOR GATEPASS SYSTEM 6
2. Server is a Django API server. This server is responsible for doing all data
processing and serving it to the front-end client.
3. Admin dashboard is django admin panel which can be used to do CRUD
operation on the database.
1.1 Existing system
Security is one of the most important aspects of any Industry (this project
currently focuses on corporate premises security systems but this project could
be extended to other areas as well). There are many people day in and day out
who visit any office, be it delivery personnel, vendor, clients, employees,
interview candidates, etc. This includes people we know and may not know, I
made some rough surveys about the visitors and visitor type/purpose in a few
startups and got to know that count of unknown people is the highest among
visitors.
Many companies have a security guard who will take manual entries in a book
regarding visitor information. Now, this has two concerns this is an offline and
insecure way of storing information i.e These books would pile up in years and
won't be maintained in years secondly, these records won’t fully identify the
visitor. Visitors with wrong intent might just have their goofed-up name and
fake ID, no other identity to validate the user henceforth. Another big concern is
these details from books can be manipulated. Security of current security system
can be compromised.
VISITOR GATEPASS SYSTEM 7
1.2 Fact-finding techniques
After completion of requirement specification phase next is requirement
gathering. Means how to collect the information what is being specified. There
are main four techniques by which information of requirement is collected. To
collect information from, is an art of analyst because there are many reason that
people do not support for system to be developed.
• Interview
• Questionnaires
• Record Review
• Observation
According to the need and scope of system, analyst can use all or any of them
for information retrieval.
Interview
Interview is most effective technique for requirement gathering. This technique
is mainly used for upper management where client is in limited no. Analyst can
arrange meeting in advanced time, duration, and place for meeting is being
specify in advanced. Some time client is not interested in providing right
information or may hide the fact. At this time analyst have to be smart and take
information whatever is need. Analyst have to take care about not only client is
speak but in what way he is. This technique is very effective as compare to
VISITOR GATEPASS SYSTEM 8
second one because face to fact communication is possible so it is possible that
information will be true.
Questionnaires
Questionnaires are useful when client side is very large. where individual
interaction is not possible for example 200 employee are there and every one
need to be questioned then this technique is very useful as compare to interview.
There are chances that client may not take interest in giving answer or provide
wrong answer to the questions. Generally there are many questions in one form
with options provided or open ended described answers.
Record Review
Above to techniques are concerns with human interaction. Where they can
speak wrong but document can't. Record review means the existing system
which is currently working is being accessed by analyst. The purpose behind is
that to collect information
stored in documents. For example the process of conducting examination, can
be retrieve by accessing previous records of candidates. Previously stored
records are facts about main system.
VISITOR GATEPASS SYSTEM 9
Observation
Above all techniques are very important but there are few things which can be
understood by behaviour of overall organization. By observing the environment
information about reality can be retrieved. / Observation is an art which can be
achieved only by experience.
1.3 Need for system
➢ The problem with existing system is that all information is recorded
manually in books/registers and having the possibility of repetitions &
mistakes.
➢ The problem with existing system is not centralized due to the reasons
such as multiple files/books are created in multiple gates/entries.
➢ The existing system can deal with unauthorized person but it is difficult
to trace unauthorized access.
➢ The system is not secure, it lacks in providing reliability and integrity for
some records available in the system.
➢ It is a tedious work to search the existing visitor's record who deals again
for the same problem, in such case the agent needs to search whole
document manually and it will be very complicated task to trace out and
merge.
➢ It is difficult to generate Date wise, visitor type wise (interview
candidates, housekeep staff, vendors person, sales person, client etc)
reports.
VISITOR GATEPASS SYSTEM 10
The visitor's information cannot be searched, reviewed or analyzed easily in this
system and it becomes more difficult if the number of customer's increases
1.4 Scope of the system
Startups/small-scale industries cannot even invest in having a security
guard or receptionist to take note of all the visitors and generate gatepass. Few
companies have a manual process of generating gatepasses, where receptionists
will note down all the details and hand over a paper gatepass or temporary ID.
Now, this approach is a very nonefficient way of having details stored and there
is a possibility of data temperament. It is also very difficult to search for a
record if required.
➢ VGS is a solution to solve security check-in issues for startup/small-scale
industries. This will automate the entire gatepass provisioning system in a
contactless and more efficient way.
➢ This app will available to visitors at the reception area in a kiosk or e-
table pc form.
➢ The visitor will register himself and get an e-gatepass generated for
himself or just add his mobile number and mark his attendance or visit.
➢ This system is a green solution that also helps in the contactless process
following all COVID-19 guidelines.
VISITOR GATEPASS SYSTEM 11
1.5 Feasibility study
While developing any computerized system it is necessary to examine
whether the developed computerized system is feasible in the point of view
operational, technical and financial. In the most commercial software
developments there are also some activities performed before the requirement
analysis takes place. These can be combined into a feasibility analysis phase. In
this phase feasibility of the project is analysis and a business proposal is put
forth, with a very general plan for the project and some cost estimates. For
feasibility analysis, some understanding of the major requirements of the system
is essential. Once the business proposal is accepted or the contract is the
awarded, the development begins with the requirement analysis phase.
The tests are categorized as follows:
l. Operational Feasibility.
2. Technical Feasibility.
3. Economical Feasibility.
VISITOR GATEPASS SYSTEM 12
1. Operational Feasibility
Proposed projects are beneficial only if they can be turned into information
systems that will meet organization's operating requirements. This test of
feasibility asks if the system will work when it is developed and installed. It has
to be seen whether there is sufficient support from the management and the user.
If system is well liked and used to the extent that the person will not be able to
see any reasons for a change, there may be no resistance.
If the current business methods are not acceptable for the users, they may
welcome a change that will bring about a more operational and useful system. It
has to be seen that the proposed system does not harm the organization or
individual performance being poor after implementation. Therefore all
operational aspects have been considered carefully.
Since we are providing the solution for the problems which are currently
faced administrator which we have already specify under "Problem
Specification" heading. After installing this software the faced problem will be
removed. Thus it will meet the user's requirements.
2. Technical Feasibility
The technical issues usually raised during the stage of investigation. It includts
the following:
a) Does the necessary technology exist to do what is suggested ? As per my
knowledge such software for managing the task flexible & reliable.
b) Can the system be expanded if developed?
VISITOR GATEPASS SYSTEM 13
The system can also be expanded if the need arises. Following can be the future
expansion:
[1] Implement Keys: Implement Primary Key, Foreign Key, and Candidate key.
[2] Build Constraints: Build all Types of constraints such as Null, Not Null, and
Unique.
[3] Join The Tattles: Join the table to inap the relation.
[4] Implement Functions: Implement all type of functions such as Pow(), Sqrt(),
Date().
3. Economic And Financial Feasibility
A system can he developed technically and will be used (if installed) must still
be a good investment for organization. Financial benefits must equal or exceed
the costs.
The financial and economical questions raised during the preliminary
investigations are for the purpose of estimating the following:
• The cost of constructs a full system.
• The cost of hardware and software for the class of application being
considered.
• The benefits in the form of reduced cost or fewer costly errors.
To be judged feasible a project proposal must pass on these tests.
Otherwise it is not a feasible project. My preliminary investigation revealed Nix
the project is feasible in all aspects.
VISITOR GATEPASS SYSTEM 14
4. Goal of Gate Pass Management System
This new online system is used to define the allowed personnel authorized to
allow access by car to guests. Which means for every entry there is someone
responsible for.
The end user will have secured web interface i.e. GATE PASS SYSTEM to
enter the guest details with inviter credentials which will be processed for
validity and up on success will be accessible online to Security personnel
occupying the gate post. Now system would have information who is visiting,
for what purpose for, who has invited him.
The invitation will be kept in the database and will be available to the Security
staffs and to the invitees. Admin can view any record at any point in time.
Full web based administration and report engine were implemented based on
SQL queries. The database has all records and safety measure of records
VISITOR GATEPASS SYSTEM 15
1.6 Background Information:
Industries faced difficulties when handing materials and human resources
which moves in and out through security points as there were higher number of
movements per day. As a solution for this organization started to implement gate
pass management process. Even though the process is called as an automotive
process still requires a considerable involvement of human resource. This will
reduce the efficiency and the effectiveness of the process as it wastes certain
amount of man hours. Therefore a requirement for a completed automated
system arises.
The main benefit of newly implementing gatepass system is it act as a
complete automotive system, once the system is it initiate by a personnel. This
will reduce the number of man hours on the resources wasted on maintenance
on basic gatepass system. The most unique feature in the newly implementing
gate pass management system is the ability to manage all transaction of
materials, employees and visitors in a one framework.
Generation of frequent status reports, providing different authorization levels
for all the transaction, availability of facility and traceability between each and
every records will make system more expertise on gatepass System.
VISITOR GATEPASS SYSTEM 16
1.7 Software requirements
➢ Python
➢ Django
➢ SQLite
➢ IDE (Visual Studio Code)
➢ Web Browser
➢ Flutter
➢ Android SDK
➢ Document Editing Software(Word & Google Docs)
VISITOR GATEPASS SYSTEM 17
1.8 Hardware requirement
➢ Personal Computer/laptop
➢ Minimum spec required i3 processor & 8GB RAM.
➢ Keyboard
➢ Mouse
➢ Mobile
➢ Final App can run on any android device above 4.1
VISITOR GATEPASS SYSTEM 18
2.0 Proposed System:
Once a visitor enters the office promise VGS(Visitor Gatepass system) app will
be available to visitors at the reception area in a kiosk or e-table pc form. This
system has two core modules, Visitor & Admin.
Visitor:
➢ Visitor will add his identity details onto the screen and click a photo.
➢ Post this activity VGS will add all his details into a database and generate
an e-gatepass which will be stored in an image format on the server also
a link (to view or download )would be sent to visitor's registered mobile
number.
➢ And system will log his/her attendance/visit data time stamp in the
database.
➢ If visitors are visiting the office a second time they will be prompted to
just add their already registered mobile number, and this will log them
IN.
VISITOR GATEPASS SYSTEM 19
Admin:
➢ Admin module will have secure access to the database with all visitor
details.
➢ Admin can view and modify details.
➢ Admin can search for specific visitor details and his/her visit history.
➢ User has to have security credentials to access this module.
2.1 The objective of the system:
The objective of a visitor gatepass system for a startup is to manage the
access of visitors to the company's premises in a secure and organized manner.
This system can help to increase the safety and security of the workplace by
controlling who enters the premises and monitoring their movements.
Specifically, a visitor gatepass system for a startup can have the following
objectives:
1. Access control: The system should be able to authenticate the identity of
visitors and allow access only to authorized individuals.
2. Security: The system should be able to monitor the movements of visitors and
detect any unauthorized activities or security breaches.
3. Record keeping: The system should maintain a record of all visitors who
enter and exit the premises, including their personal information and purpose of
visit.
VISITOR GATEPASS SYSTEM 20
4. Time management: The system should help manage the time spent by visitors
on the premises and ensure that they are not overstaying their welcome.
5. Efficiency: The system should be easy to use and administer, with minimal
disruption to the daily operations of the startup.
2.2 user Requirements
A visitor gatepass system is designed to meet the user requirements of
businesses that need to manage visitor access to their premises. The following
are some of the key user requirements that a visitor gatepass system should
address:
1. Security: One of the primary user requirements for a visitor gatepass system
is to enhance the security of the premises. This includes verifying the identity of
visitors, controlling access to different areas of the premises, and monitoring
visitor movements.
2. Ease of Use: The system should be easy to use for both visitors and
administrators. This includes having a simple registration process, clear
instructions for visitors, and a user-friendly interface for administrators.
3. Customization: Different businesses have different security requirements, and
the visitor gatepass system should be customizable to meet those needs. This
includes being able to set different authorization levels for visitors, create
custom visitor passes, and configure access control settings.
VISITOR GATEPASS SYSTEM 21
4. Integration: The visitor gatepass system should be able to integrate with other
security systems, such as CCTV cameras and alarm systems. This helps to
provide a more comprehensive security solution for the premises.
5. Reporting: The system should be able to generate reports on visitor traffic,
visitor history, and security incidents. This helps administrators to identify
trends and potential security issues.
6. Scalability: The system should be able to scale as the business grows. This
includes being able to handle a large volume of visitors and having the
flexibility to adapt to changing security needs.
7. Support: The vendor should provide adequate support for the system,
including training for administrators and technical support when needed.
By addressing these user requirements, a visitor gatepass system can help
Startup businesses to manage visitor access more efficiently and improve the
security of their premises.
VISITOR GATEPASS SYSTEM 22
3.0 System Analysis and Design
System Analysis and Design is an important phase in developing a visitor
gatepass system. This phase involves analyzing the requirements of the system,
designing its architecture, and specifying its components and functionalities.
The following is a report on the System Analysis and Design phase for a visitor
gatepass system:
1. System Requirements Analysis: The first step in the System Analysis and
Design phase is to analyse the requirements of the visitor gatepass system. This
includes identifying the key features and functionalities of the system, such as
visitor registration, authentication, access control, monitoring, record keeping,
reporting, and customization.
2. System Architecture Design: The next step is to design the system
architecture. This includes identifying the hardware and software components of
the system, such as servers, databases, user interfaces, and network devices. The
architecture should be scalable, secure, and flexible to accommodate future
changes.
3. User Interface Design: The user interface of the visitor gatepass system
should be user-friendly and intuitive for both visitors and administrators. The
design should focus on simplicity, clarity, and ease of use.
4. Database Design: The database is a crucial component of the visitor gatepass
system, as it stores all the visitor data and records. The database design should
ensure data integrity, security, and scalability.
VISITOR GATEPASS SYSTEM 23
6. Security Design: Security is a critical aspect of the visitor gatepass system,
and the security design should ensure that the system is secure and protected
against unauthorized access or data breaches. This includes implementing
authentication mechanisms, encryption, and access control policies.
7. Testing and Validation: Finally, the visitor gatepass system should be
thoroughly tested and validated to ensure that it meets the requirements and
specifications. This includes functional testing, usability testing, and security
testing.
In conclusion, the System Analysis and Design phase is a critical step in
developing a visitor gatepass system. It helps to identify the requirements,
design the system architecture, specify the components and functionalities, and
validate the system before it is deployed. This phase sets the foundation for the
successful development and implementation of the visitor gatepass system.
VISITOR GATEPASS SYSTEM 24
1. Primary Design phase:
In this phase, the system is designed at block level . The blocks are
created on the basis of analysis done in the problem identification phase.
Different blocks are created for different function emphasis is put on
minimising the information flow between blocks . Thus, all activities
which require more interaction are kept in one block.
2. Secondary Design Phase:
In various blocks for overall system process.
The general tasks involved in the design process are following:
1. Designed various blocks for overall system process.
2. Design Smaller
3. Compact and workable modules in each block.
4. Specify the details of programs to achieve desired functionality.
5. System reviews .
VISITOR GATEPASS SYSTEM 25
3.1 System Architecture
System Architecture Design is a crucial step for software and application
developers to describe the basic software or application structure by separating
functional areas into layers. It depicts how a typical software / application
system might interact with its users, external systems, data sources, and
services. The architecture of implementing system is mentioned below.
VISITOR GATEPASS SYSTEM 26
3.2 Using data Dictionary:
A data dictionary is a useful tool for managing data in a database or information
system. It can be used in various stages of the software development lifecycle,
from requirements analysis to design, implementation, and testing. Here are
some examples of how a data dictionary can be used:
1. Requirements Analysis: During requirements analysis, a data dictionary can
be used to define and document the data elements that will be used in the
system. This helps ensure that all stakeholders have a common understanding of
the data, and can help identify any inconsistencies or gaps in the requirements.
2. Design: During design, a data dictionary can be used to define the data model
and its relationships. This helps ensure that the data is organized and structured
in a way that supports the requirements of the system, and that the data is
consistent and accurate.
3. Implementation: During implementation, a data dictionary can be used to
generate code automatically. This helps reduce errors and saves time, since the
code can be generated from the data dictionary instead of being written
manually.
4. Testing: During testing, a data dictionary can be used to validate the data and
ensure that it meets the requirements of the system. This helps identify any
errors or inconsistencies in the data, which can then be addressed before the
system is deployed.
5. Maintenance: After the system is deployed, a data dictionary can be used to
manage and maintain the data. It provides a reference for developers and other
VISITOR GATEPASS SYSTEM 27
stakeholders, and helps ensure that any changes to the data are properly
documented and tracked.
In summary, a data dictionary is a useful tool for managing data in a database or
information system. It helps ensure consistency and accuracy in the data model,
and provides a reference for developers, testers, and other stakeholders
throughout the software development lifecycle.
3.3 Introducing the data Dictionary:
A data dictionary is a structured collection of metadata, which provides a
detailed description of the data elements or attributes in a database or
information system. It is essentially a database of data about data.
The purpose of a data dictionary is to define and document the data elements
and their relationships in a database or information system. It provides a
common language and understanding of the data, which facilitates
communication and collaboration among stakeholders. A data dictionary
typically includes the following information about each data element:
1. Name: The name or identifier of the data element.
2. Description: A brief description of the data element and its purpose.
3. Data Type: The type of data, such as string, integer, date, etc.
4. Size: The size or length of the data element, if applicable.
5. Format: The format or pattern of the data element, if applicable.
VISITOR GATEPASS SYSTEM 28
6. Constraints: Any constraints or rules that apply to the data element, such as
a unique key or a required field.
7. Relationships: The relationships between the data elements, such as foreign
keys and dependencies.
8. Ownership: The owner or source of the data element, if applicable.
A data dictionary can be used in various stages of the software development
lifecycle, from requirements analysis to design, implementation, and testing. It
helps ensure consistency and accuracy in the data model, and provides a
reference for developers, testers, and other stakeholders. A data dictionary can
also be used to generate code or documentation automatically, which saves time
and reduces errors.
In summary, a data dictionary is an essential tool for managing data in a
database or information system. It provides a comprehensive and standardized
view of the data, which helps ensure data quality, consistency, and usability.
VISITOR GATEPASS SYSTEM 29
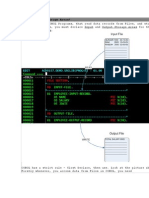
3.4 Database Table :
Table no:1
Table Name: Visitor
No Filed Name Data Type Size Constraints
1 mobile_no integer - Primary Key
2 firstname varchar 20 Not Null
3 lastname varchar 20 Not Null
4 idproof_type varchar 20 Not Null
5 idproof_no varchar 20 Not Null
VISITOR GATEPASS SYSTEM 30
Table No:2
Table Name:visit
Description : This table will have every visitor’s visit logs.
No Filed Name Data Size Constraints
Type
1 visit_id integer - Primary Key
2 visitor_id integer 10 Foreign Key
3 checkin_datetime datetime - Not Null
4 checkout_datetime datetime - Not Null
5 visit_purpose_desc varchar 150 Not Null
VISITOR GATEPASS SYSTEM 31
Table No: 3
Table Name: auth_user
Description: This table (is created by django by default) have admin user
details and credentials.
No Filed Name Data Type Size Constraints
1 id integer - Primary Key
2 password varchar 128 Not Null
3 last_login datetime 8 Not Null
4 is_superuser bool - Not Null
5 username varchar 150 Not Null
6 lastname varchar 150 Not Null
7 is_staff bool - Not Null
8 is_active bool - Not Null
9 date_joined datetime - Not Null
10 first_name varchar 150 Not Null
VISITOR GATEPASS SYSTEM 32
4.0 UML Diagrams:
UML stands for Unified Modeling Language, which is a graphical
language used to represent, design, and communicate software systems.
UML diagrams are visual representations of different aspects of a software
system, which help software engineers to understand, analyze, and design
the software system.
There are several types of UML diagrams, each with a specific purpose
and level of abstraction. Some of the most commonly used UML diagrams
include:
1. Use Case Diagram: A use case diagram is used to represent the
functional requirements of a software system. It shows the interaction
between actors (users or external systems) and the system to achieve a
particular goal.
2. Class Diagram: A class diagram is used to represent the static structure
of a software system. It shows the classes, interfaces, attributes, and
relationships between them.
3. Sequence Diagram: A sequence diagram is used to represent the
dynamic behavior of a software system. It shows the interactions between
objects or components in a particular scenario or use case.
4. Activity Diagram: An activity diagram is used to represent the flow of
activities or processes in a software system. It shows the actions,
decisions, and transitions between different states or activities.
5. Component Diagram: A component diagram is used to represent the
physical structure of a software system. It shows the components,
interfaces, and dependencies between them.
UML diagrams are used throughout the software development lifecycle,
from requirements analysis to design, implementation, and testing. They
provide a common language and notation for software engineers to
VISITOR GATEPASS SYSTEM 33
communicate and collaborate on the design and development of software
systems.
4.1 Use case Diagram :
Use case Diagram for admin user:
VISITOR GATEPASS SYSTEM 34
2. Use case diagram for admin user :
VISITOR GATEPASS SYSTEM 35
4.2 Class Diagram
1. Class Diagram for VGS(Visitor Gatepass System):
VISITOR GATEPASS SYSTEM 36
4.3 Sequence Diagram
1.0 Sequence diagram for visitor:
VISITOR GATEPASS SYSTEM 37
1.1 Sequence diagram for Visitor interacting with app scenario:
VISITOR GATEPASS SYSTEM 38
4.4 Activity Diagram
Activity Diagram for admin:
VISITOR GATEPASS SYSTEM 39
4.5 Component diagram
VISITOR GATEPASS SYSTEM 40
VISITOR GATEPASS SYSTEM 41
VISITOR GATEPASS SYSTEM 42
VISITOR GATEPASS SYSTEM 43
VISITOR GATEPASS SYSTEM 44
VISITOR GATEPASS SYSTEM 45
VISITOR GATEPASS SYSTEM 46
VISITOR GATEPASS SYSTEM 47
VISITOR GATEPASS SYSTEM 48
VISITOR GATEPASS SYSTEM 49
VISITOR GATEPASS SYSTEM 50
VISITOR GATEPASS SYSTEM 51
VISITOR GATEPASS SYSTEM 52
VISITOR GATEPASS SYSTEM 53
VISITOR GATEPASS SYSTEM 54
VISITOR GATEPASS SYSTEM 55
VISITOR GATEPASS SYSTEM 56
VISITOR GATEPASS SYSTEM 57
VISITOR GATEPASS SYSTEM 58
VISITOR GATEPASS SYSTEM 59
VISITOR GATEPASS SYSTEM 60
VISITOR GATEPASS SYSTEM 61
VISITOR GATEPASS SYSTEM 62
VISITOR GATEPASS SYSTEM 63
VISITOR GATEPASS SYSTEM 64
VISITOR GATEPASS SYSTEM 65
VISITOR GATEPASS SYSTEM 66
VISITOR GATEPASS SYSTEM 67
VISITOR GATEPASS SYSTEM 68
VISITOR GATEPASS SYSTEM 69
VISITOR GATEPASS SYSTEM 70
VISITOR GATEPASS SYSTEM 71
VISITOR GATEPASS SYSTEM 72
VISITOR GATEPASS SYSTEM 73
VISITOR GATEPASS SYSTEM 74
VISITOR GATEPASS SYSTEM 75
VISITOR GATEPASS SYSTEM 76
VISITOR GATEPASS SYSTEM 77
VISITOR GATEPASS SYSTEM 78
VISITOR GATEPASS SYSTEM 79
VISITOR GATEPASS SYSTEM 80
VISITOR GATEPASS SYSTEM 81
VISITOR GATEPASS SYSTEM 82
VISITOR GATEPASS SYSTEM 83
VISITOR GATEPASS SYSTEM 84
VISITOR GATEPASS SYSTEM 85
You might also like
- List of File FormatsDocument78 pagesList of File Formatschaitanya_bholeNo ratings yet
- Gym Management System 1234545Document76 pagesGym Management System 1234545Sajin JosephNo ratings yet
- AnsibleFest 2019 - Managing Meaningful InventoriesDocument38 pagesAnsibleFest 2019 - Managing Meaningful InventoriesGuillaume LavoixNo ratings yet
- Software Requirements Specification Online Food Ordering SystemDocument9 pagesSoftware Requirements Specification Online Food Ordering SystemPC KRUNAL89% (9)
- Doc-Attendance Management SystemDocument41 pagesDoc-Attendance Management Systemanand k kumarNo ratings yet
- MySQL - Crash Course (PDFDrive)Document85 pagesMySQL - Crash Course (PDFDrive)samuelNo ratings yet
- Hospital Management System SrsDocument71 pagesHospital Management System SrsYash Kapoor75% (12)
- Kakinada: Submitted To The Faculty of Engineering ofDocument44 pagesKakinada: Submitted To The Faculty of Engineering ofVijay TejaNo ratings yet
- "Doctor-Patient Interaction System ": Kajol Kamble. Seat NO:-183440Document34 pages"Doctor-Patient Interaction System ": Kajol Kamble. Seat NO:-183440Poonam PawaleNo ratings yet
- Microprocessor and Microcontroller MCQS by SanfoundryDocument121 pagesMicroprocessor and Microcontroller MCQS by SanfoundrySajjadNo ratings yet
- Fundamentals of Cyber Security: Principles, Theory and PracticesFrom EverandFundamentals of Cyber Security: Principles, Theory and PracticesNo ratings yet
- RTO Management System 1Document36 pagesRTO Management System 1Kuldeep ParekhNo ratings yet
- Onine Attendence SystemDocument65 pagesOnine Attendence SystemShan KhanNo ratings yet
- "Shopify": A Project Report ONDocument39 pages"Shopify": A Project Report ONParth ParmarNo ratings yet
- SRS For Online Pizza StoreDocument49 pagesSRS For Online Pizza StoreR_Arpan60% (10)
- Gym Management System 1234545Document69 pagesGym Management System 1234545javed9890No ratings yet
- Synopsis: Student Information SystemDocument16 pagesSynopsis: Student Information SystemsunilmbaNo ratings yet
- Pogi 2Document96 pagesPogi 2Wilrenz CastroNo ratings yet
- College Fees SystemDocument24 pagesCollege Fees SystemYuktaNo ratings yet
- The Certificate of Originality: To Whom It May ConcernDocument31 pagesThe Certificate of Originality: To Whom It May Concernsauptik_007No ratings yet
- Bloodbank ReportDocument44 pagesBloodbank ReportPimpri39Abhishek GaikwadNo ratings yet
- Placement Cell Final 15Document79 pagesPlacement Cell Final 15Rachit Goyal43% (7)
- Toaz - Info Doc Attendance Management System PRDocument41 pagesToaz - Info Doc Attendance Management System PRom sivamNo ratings yet
- Hospital Management Project ReportDocument99 pagesHospital Management Project ReportSyed Masud33% (3)
- Final Doc Project of Training and PlacementDocument60 pagesFinal Doc Project of Training and PlacementPreeti Dahiya100% (1)
- Reliance Fresh Inventory Management SystemDocument65 pagesReliance Fresh Inventory Management SystembkNo ratings yet
- Project Report AmritDocument13 pagesProject Report AmritAmandeep KaurNo ratings yet
- Hospital Management SystemDocument18 pagesHospital Management SystemVinay KanasuNo ratings yet
- TY Jitendra-Jadhav Dinesh-MahajanDocument19 pagesTY Jitendra-Jadhav Dinesh-Mahajancheenujoshi2007No ratings yet
- CapstoneDocument8 pagesCapstoneMichael Vergara100% (1)
- Project Tours and TourismDocument28 pagesProject Tours and Tourismanjalikodre9No ratings yet
- System ManagementDocument67 pagesSystem ManagementMukul SharmaNo ratings yet
- Bus Reservation SystemDocument31 pagesBus Reservation SystemSOHAIL PATHAN2No ratings yet
- Project Report AppDocument14 pagesProject Report AppJOHN WICKNo ratings yet
- Computerized Voting System of The StudenDocument25 pagesComputerized Voting System of The Studenjustin robrigadoNo ratings yet
- Project FileDocument57 pagesProject FileAmit SinghNo ratings yet
- Cse09 Project DocumentDocument90 pagesCse09 Project DocumentSravanti PhanindraNo ratings yet
- Proforma For The Approval Project ProposalDocument54 pagesProforma For The Approval Project Proposalarman khanNo ratings yet
- Mobile Shop Management SystemDocument25 pagesMobile Shop Management SystemTSA32 SYBSCIT Rasika TambeNo ratings yet
- Fertilization Full Doc Format NewDocument43 pagesFertilization Full Doc Format NewDhinesh kumarNo ratings yet
- Clinic Management SystemDocument26 pagesClinic Management SystemSyed IntikhabNo ratings yet
- ICT3713 Portfolio PDFDocument11 pagesICT3713 Portfolio PDFtebogo_nkwanetNo ratings yet
- NatashaDocument16 pagesNatashajunior chikodzeNo ratings yet
- Kiambu County ProposalDocument22 pagesKiambu County ProposalChege HiramNo ratings yet
- Mysem1project ReportDocument51 pagesMysem1project ReportUday KumarNo ratings yet
- Bachelor of Technology Computer Science and Engineering: Gym WebsiteDocument12 pagesBachelor of Technology Computer Science and Engineering: Gym WebsitePriyanshu SinghalNo ratings yet
- Gym Management System: G. S. College of Commerce & Economics, Nagpur (Autonomous) (Computer Application) Final YearDocument129 pagesGym Management System: G. S. College of Commerce & Economics, Nagpur (Autonomous) (Computer Application) Final YearS Mohamed AsifNo ratings yet
- Final Black BookDocument77 pagesFinal Black BookImran KhanNo ratings yet
- Gym Mangment SystemDocument39 pagesGym Mangment SystemShivshahi ParivarNo ratings yet
- Municipality SystemDocument32 pagesMunicipality SystemAparna JanwalkarNo ratings yet
- Student Management SystemDocument39 pagesStudent Management SystemKavya BhattNo ratings yet
- Work Hunter System: Deolali - Pravara. Department of Computer Application. A Project Report OnDocument22 pagesWork Hunter System: Deolali - Pravara. Department of Computer Application. A Project Report OnSARANG MORENo ratings yet
- Report ProjectDocument29 pagesReport ProjectRimjhim KymariNo ratings yet
- Placement Management System ProjectDocument40 pagesPlacement Management System ProjectAkash LawandeNo ratings yet
- Hardware Management Information System-14550044 PDFDocument99 pagesHardware Management Information System-14550044 PDF20BCC088 PandeesWaranNo ratings yet
- Online Face Recognition SystemDocument15 pagesOnline Face Recognition SystemUmran JabbarNo ratings yet
- Chap 1-4Document31 pagesChap 1-4Dr-Adeel AsgharNo ratings yet
- Online ExaminationDocument63 pagesOnline Examinationkrishnagomel25100% (1)
- Group - 8 - Fitness Centre - PrintDocument29 pagesGroup - 8 - Fitness Centre - Printsaisantosh63721No ratings yet
- PROJECTDocument114 pagesPROJECTbablujsrNo ratings yet
- Reliance Fresh Inventory Management SystemDocument64 pagesReliance Fresh Inventory Management Systemhonestguy09No ratings yet
- Suraj Report Summary ContDocument25 pagesSuraj Report Summary Contsuraj mishraNo ratings yet
- Student Information System Project Thesis DocumentationDocument6 pagesStudent Information System Project Thesis DocumentationTony Lisko100% (2)
- Proveedor SYNNEX WESTCONDocument10 pagesProveedor SYNNEX WESTCONLesly A. PinillosNo ratings yet
- Enterprise Application Architecture (EAI)Document18 pagesEnterprise Application Architecture (EAI)Karl Alvin Reyes HipolitoNo ratings yet
- CS8461 - 17.3Document4 pagesCS8461 - 17.3swethaNo ratings yet
- Shonascript LearnDocument76 pagesShonascript LearnTechnical gurujii SuperstarNo ratings yet
- LAB211 Assignment: Title Background Program SpecificationsDocument3 pagesLAB211 Assignment: Title Background Program SpecificationsPhạm V. NghĩaNo ratings yet
- XCAT 2.0: A Component-Based Programming Model For Grid Web ServicesDocument10 pagesXCAT 2.0: A Component-Based Programming Model For Grid Web Servicesxico107No ratings yet
- SAP IDOC Tutorial: Definition, Structure, Types, Format & TablesDocument9 pagesSAP IDOC Tutorial: Definition, Structure, Types, Format & TablesgayatriscribdNo ratings yet
- FS - Rate Field in STPO InvoiceDocument9 pagesFS - Rate Field in STPO InvoiceDaxeshNo ratings yet
- Exception 2Document4 pagesException 2Giovanni Edward AndreianaNo ratings yet
- LogDocument37 pagesLogJulio SouzaNo ratings yet
- !! ReadMe !!Document2 pages!! ReadMe !!Radwan AhmedNo ratings yet
- CSC 101 - Assignment 2 - Fall2022Document4 pagesCSC 101 - Assignment 2 - Fall2022Just Do ItNo ratings yet
- Pastebincom FAQ Frequently Asked QuestionsDocument3 pagesPastebincom FAQ Frequently Asked QuestionsMahatma AryaNo ratings yet
- JAVA Lab PracticesDocument7 pagesJAVA Lab PracticesSubhajit GhoshNo ratings yet
- Cpe106l - Experiment 2Document22 pagesCpe106l - Experiment 2Loven GarciaNo ratings yet
- OperatorsDocument96 pagesOperatorsShweta ShahNo ratings yet
- Course: PHP Course Type: Advanced Programming Languages Course Duration: 72 Hours SyllabusDocument3 pagesCourse: PHP Course Type: Advanced Programming Languages Course Duration: 72 Hours SyllabussanasNo ratings yet
- Dynamic Auditing With Cloud Data Integrity Via Group User RevocationDocument4 pagesDynamic Auditing With Cloud Data Integrity Via Group User RevocationnebulaaNo ratings yet
- B.B.A (C.a) 2013 Pattern (1) 2 - OrganizedDocument5 pagesB.B.A (C.a) 2013 Pattern (1) 2 - OrganizedDhara rahejaNo ratings yet
- 2 Chapter 2 - Algorithmic Problem SolvingDocument27 pages2 Chapter 2 - Algorithmic Problem SolvingNunalif YawaumimNo ratings yet
- Elb v2 ApiDocument180 pagesElb v2 ApikhalandharNo ratings yet
- What Are DB2 Storage AreasDocument9 pagesWhat Are DB2 Storage AreassujijayaNo ratings yet
- UNIT - 4::: TOPIC Link ListDocument21 pagesUNIT - 4::: TOPIC Link ListGaurav KumarNo ratings yet
- Debug Diag White PaperDocument63 pagesDebug Diag White PaperThilaka BalanNo ratings yet