Professional Documents
Culture Documents
2.2.3 The Mobile Services Switching Centre
Uploaded by
Tushar SaxenaOriginal Title
Copyright
Available Formats
Share this document
Did you find this document useful?
Is this content inappropriate?
Report this DocumentCopyright:
Available Formats
2.2.3 The Mobile Services Switching Centre
Uploaded by
Tushar SaxenaCopyright:
Available Formats
2.2.
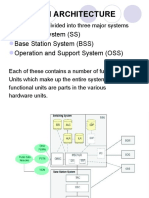
AN OVERVIEW OF THE GSM NETWORK ARCHITECTURE
73
controlling the transmitted power of an MS to ensure that it is just sufcient to reach its serving BTS. BSCs vary from manufacturer to manufacturer, but a BSC might typically control up to 40 BTSs. In addition to its processing capacity, a BSC will also have a limited switching capability, enabling it to route calls between the different BTSs under its control. The interface between a BSC and an associated BTS is known as the A-bis interface and it is fully dened by an open, or public, specication. In theory this allows a network operator the freedom to procure their BSCs and BTSs from different equipment manufacturers. The BTS and BSC are collectively known as the base station subsystem (BSS).
2.2.3
The mobile services switching centre
Referring to Figure 2.1, we see that each BSS is connected to a mobile services switching centre (MSC). The MSC is concerned with the routing of calls to and from the mobile users. It possesses a large switching capability that varies between manufacturers, but a typical MSC will control a few tens of BSCs and it will have a capacity of several tens of thousands of subscribers. The MSC is similar to the switching exchange in a xed network. However, it must include additional functions to cope with the mobility of the subscribers, e.g. functions to cope with location registration and handover. The GSM specications use the term MSC area to describe the part of a network that is covered by a particular MSC and its associated BSCs and BTSs. The interface between the MSC and BSS is known as the A interface and it is fully dened in the specications, giving the network operator the freedom to choose their MSCs and BSCs from different manufacturers. The interface between different MSCs is called the E interface. The network operator may also select one or a number of MSCs to act as gateway MSCs (GMSC). As its name would suggest, the GMSC provides the interface between the PLMN and external networks. In the event of an incoming call from another network, the GMSC communicates with the relevant network databases to ensure that the call is routed to the appropriate MS.
2.2.4
The GSM network databases
In the previous sections we have examined the various components within the GSM network that are used to form the communication path between an MS and another MS or a user on another network, e.g. the public switched telephone network (PSTN). Equally important in a commercial network are the means of charging and billing subscribers, maintaining accurate subscription records and preventing fraudulent network access. In a cellular network where subscribers are free to roam throughout the coverage area, the network must also possess some way to track MSs so that it is able successfully to route incoming calls to them. All of these functions are supported using a combination of databases or registers.
74
CHAPTER 2. THE GSM SYSTEM
The home location register (HLR) is used to store information that is specic to each subscriber. It will contain details of a particular users subscription, e.g. the services to which they have access, and some information relating to the location of each subscriber, e.g. the details of the MSC area within which the subscriber is currently registered. The information contained within the HLR may be accessed using either the subscribers IMSI or mobile station international ISDN (MSISDN) number, which is essentially the subscribers telephone number. Every GSM subscriber will have an entry in the HLR of their home network. The interface between an HLR and an MSC is called the C interface. Another GSM database that is very closely associated with the HLR is the authentication centre (AuC). The AuC is solely used to store information that is concerned with GSMs security features, i.e. user authentication and radio path encryption. It will contain the subscribers secret Ki key and the A3 and A8 security algorithms. The functions of the Ki key and the security algorithms are described in detail in Section 2.5. The AuC will only ever communicate with the HLR and it does this using the H interface. Another important database used in the GSM system is the visitor location register (VLR). A VLR is associated with one or a number of MSCs and it contains information relating to those subscribers that are currently registered within the MSC area(s) of its associated MSC(s). The area that is served by a particular VLR is termed the VLR area. It is termed the visitor location register because it holds information on those subscribers that are visiting its VLR area. The main function of the VLR is to provide a local copy of the subscribers information for the purposes of call handling and it removes the need to continually access the HLR to retrieve information about a particular subscriber. This becomes important in a system such as GSM where subscribers may use networks in countries other than the country of their home network. The VLR also contains information that enables the network to nd a particular subscriber in the event of an incoming call. The process of locating a subscriber is facilitated by subdividing the networks coverage area into a number of location areas, each consisting of one or a number of cells or sectors. The VLR will contain the details of the location area in which each subscriber is registered. In the event of an incoming call, an MS will be paged in each of the cells within its location area and this means that the MS may move freely between the cells of a location area without having to inform the network. However, when an MS moves between cells belonging to different location areas, it must register in the new area using the location updating procedure. Where a subscriber moves between location areas controlled by different VLRs, its details are copied from the HLR to the new VLR. The HLR will also ensure that the subscribers details are removed from the old VLR. The interface between the HLR and the VLR is called the D interface and the interface between an MSC and its associated VLR is called the B interface. An interface also exists between different VLRs and this is termed the G interface.
2.2. AN OVERVIEW OF THE GSM NETWORK ARCHITECTURE
75
The introduction of the SIM card in GSM means that tracking a subscriber no longer implies the tracking of a piece of equipment, and vice versa. For this reason the equipment identity register (EIR) has been introduced to allow the network operator to track stolen and malfunctioning MEs. Each ME is assigned a unique 15-digit international mobile equipment identity (IMEI) at the point of manufacture. Each model of ME must undergo a process known as type approval, wherein a number of its features are tested using a GSM system simulator. The type approval testing is carried out by accredited laboratories that are independent of any manufacturing or operating companies and it is used to ensure that all GSM ME models meet a minimum standard, regardless of the manufacturer. Once an ME model has been type approved it will be assigned a six-digit type approval code (TAC) and this forms the rst six digits of an MEs IMEI. The next two digits of the IMEI represent the nal assembly code (FAC) and this is assigned by the manufacturer to identify the place where the ME was nally assembled or manufactured. The next six digits of the IMEI represent the MEs serial number (SNR) and this will be unique to every MS for a given combination of TAC and FAC. The remaining digit of the 15-digit IMEI is dened as spare. The EIR is used to store three different lists of IMEIs. The white list contains the series of IMEIs that have been allocated to MEs that may be used on the GSM network. The black list contains the IMEIs of all MEs that must be barred from using the GSM network. This will contain the IMEIs of stolen and malfunctioning MEs. Finally, the network operator may also use a grey list to hold the IMEIs of MEs that must be tracked by the network for evaluation purposes. During an access attempt or during a call, the network has the ability to command an MS to supply its IMEI at any time. If the IMEI is on the black list or it is not on the white list, the network will terminate the call or access attempt and the subscriber will be sent an illegal ME message. Once an MS has failed an IMEI check it will be prevented from making any further access attempts, location updates or paging call responses. However, this MS may still be used to make emergency calls. The IMEI check is performed within the EIR and the IMEI is passed to the EIR by the MSC that is currently serving the MS. The results of the IMEI check are then returned by the EIR to the relevant MSC. The interface between the EIR and the MSC is termed the F interface.
2.2.5
The management of GSM networks
From an operators viewpoint, an effective network management system is an important part of any telecommunications network. It is essential for the network operator to be able to identify problems in the network at an early stage and correct them quickly and efciently. It is also important for the network operator to be able to make changes to the network conguration with a minimum of effort and without affecting the service provided to its
76
CHAPTER 2. THE GSM SYSTEM
subscribers. The functional blocks associated with the management of the GSM network, as shown in Figure 2.1, are the operations and maintenance centre (OMC), the network management centre (NMC) and the administration centre (ADC). The OMC provides the means by which the operator controls the network. Each OMC will typically be in charge of a subsystem, e.g. the BSS or the Network Switching Subsystem, NSS (i.e. the MSC, HLR, VLR, etc.) The NMC is concerned with the management of the entire network and it generally has a wider operational role than an OMC. The ADC is concerned, as its name would suggest, with the administrative functions required within the network.
2.3 The GSM Radio Interface
The radio interface provides the means by which an MS communicates with the BTSs of a GSM network whilst it moves within the coverage area. The performance of the radio interface, and particularly its ability to provide acceptable speech links in the face of co-channel interference from other users within the system, acutely affects the overall capacity of a cellular system. In this section we examine the features of the GSM radio interface. Figure 2.2 shows a simplied block diagram of the GSM radio link. In the following sections we will examine the function and operation of each of these blocks in some detail. It is difcult to keep to a strict top-down or bottom-up description of the GSM radio interface because, in some cases, in order to appreciate the reason for a particular feature of the radio interface, it is necessary to understand some features associated with a higher or lower layer protocol. For this reason we have adopted a somewhat unconventional approach to the description of the radio interface. We will begin by examining the modulation scheme and the carrier frequencies used in GSM. Then we will discuss the construction of the TDMA bursts, or packets, and the way in which these may be demodulated in the presence of intersymbol interference (ISI) caused by the radio channel and the modulation process itself. Following this we will discuss the different channels that are available in GSM and the manner in which the radio resources are allocated to each of the channels. At this point we will have effectively built up a picture of the radio interface as a bit pipe where data are applied to the transmitter and the same data, possibly with a number of errors, are recovered at the receiver. We will then turn our attention to the coding, interleaving and ciphering processes that occur on the GSM radio interface. These processes are different for speech information, user data (e.g. fax transmissions) and signalling information and, therefore, we will deal with each of these different types of information separately. Finally, we will bring the two halves of our radio interface description together by describing the manner in which the coded, interleaved and ciphered, or encrypted, data are mapped onto the TDMA bursts.
You might also like
- GSM Network ArchitectureDocument35 pagesGSM Network ArchitectureIkobayo AdewaleNo ratings yet
- GSM SystemDocument13 pagesGSM Systemiamhridoy74No ratings yet
- GSM Mobile Services: Project Report ONDocument67 pagesGSM Mobile Services: Project Report ONRahul MishraNo ratings yet
- GSM Network ArchitectureDocument5 pagesGSM Network Architecturekataz2010No ratings yet
- Introduction To GSM: GSM (Global System For Mobile Communications)Document12 pagesIntroduction To GSM: GSM (Global System For Mobile Communications)Anuj KuradeNo ratings yet
- GSM (Global System For Mobile Communication)Document3 pagesGSM (Global System For Mobile Communication)Pulkit SharmaNo ratings yet
- GSM ArchitectureDocument8 pagesGSM ArchitectureAbhishek PandeyNo ratings yet
- GSM NW ArchitectureDocument3 pagesGSM NW ArchitectureSreepad BharanNo ratings yet
- Telecom AssignmentDocument5 pagesTelecom Assignmentikra khanNo ratings yet
- GSM Network ComponentsDocument23 pagesGSM Network ComponentsShakeel AminNo ratings yet
- 2G Network: Elecom EtworkDocument13 pages2G Network: Elecom Etworkpg5555No ratings yet
- Global System For Mobile Communication (GSM)Document6 pagesGlobal System For Mobile Communication (GSM)RobertoNo ratings yet
- Mobile Computing1stDay19072018Document60 pagesMobile Computing1stDay19072018Kalyan DasNo ratings yet
- Second Generation (2G) Cellular Radio SystemsDocument40 pagesSecond Generation (2G) Cellular Radio SystemsMd. Golam Sarwar JoyNo ratings yet
- How GSM Networks Work - Key Components and ArchitectureDocument4 pagesHow GSM Networks Work - Key Components and ArchitectureAbuzarNo ratings yet
- Introduction To GSM GSM Network Components Mobile Services Switching Centre-MscDocument11 pagesIntroduction To GSM GSM Network Components Mobile Services Switching Centre-MscDenaiya Watton LeehNo ratings yet
- Base Station Subsystem (BSS) Network and Switching Subsystem (NSS) Operation Support Subsystem (OSS)Document3 pagesBase Station Subsystem (BSS) Network and Switching Subsystem (NSS) Operation Support Subsystem (OSS)api-19624645No ratings yet
- GSM Network ArchitectureDocument28 pagesGSM Network ArchitectureZain ABNo ratings yet
- Network Switching SubsystemDocument24 pagesNetwork Switching SubsystemAIC DSNo ratings yet
- Mobile Computing5thDay5.08.2019Document61 pagesMobile Computing5thDay5.08.2019Kalyan DasNo ratings yet
- GSM Network ArchitectureDocument55 pagesGSM Network Architecturealeesha1987No ratings yet
- GSM Network Architecture ExplainedDocument11 pagesGSM Network Architecture ExplainedYe YintNo ratings yet
- Prepared By: Rady AbdelwahedDocument168 pagesPrepared By: Rady AbdelwahedAmr Sunhawy50% (2)
- GSM Data CompleteDocument12 pagesGSM Data CompleteAdeel TajNo ratings yet
- MD - Hasanuzzaman Assignment01Document17 pagesMD - Hasanuzzaman Assignment01MD HasanNo ratings yet
- GSM Network ArchitectureDocument5 pagesGSM Network ArchitecturePrashant KulkarniNo ratings yet
- Global System For Mobile Communication (GSM) : DefinitionDocument9 pagesGlobal System For Mobile Communication (GSM) : DefinitionAnfal AslamNo ratings yet
- Mobile Networks Chapter 4Document31 pagesMobile Networks Chapter 4Kamdem kamgaing Gilles ChristianNo ratings yet
- Archtecture of GSMDocument8 pagesArchtecture of GSMMjrtMQNo ratings yet
- The history and overview of the GSM mobile systemDocument18 pagesThe history and overview of the GSM mobile systemhieuvnp3No ratings yet
- Global System For Mobile Communications (GSM) : Asad AliDocument66 pagesGlobal System For Mobile Communications (GSM) : Asad AliMuhammadwaqasnaseemNo ratings yet
- Communication SystemDocument9 pagesCommunication SystemNouman BajwaNo ratings yet
- Introduction To GSM 2Document12 pagesIntroduction To GSM 2mba_1604No ratings yet
- GSM Architecture: Switching System (SS) Base Station System (BSS) Operation and Support System (OSS)Document19 pagesGSM Architecture: Switching System (SS) Base Station System (BSS) Operation and Support System (OSS)aimslifeNo ratings yet
- 1.GSM OverviewDocument46 pages1.GSM OverviewAmit ThakurNo ratings yet
- Wireless Comm Securiy 5Document27 pagesWireless Comm Securiy 5abdulsahibNo ratings yet
- The GSM System History: NextDocument19 pagesThe GSM System History: NextJoseph DavisNo ratings yet
- Chapter 6 - CDMA Network ArchitectureDocument13 pagesChapter 6 - CDMA Network Architectureukb_8414No ratings yet
- CC CC CC: C CC CC CC CDocument19 pagesCC CC CC: C CC CC CC Cpk_babuaNo ratings yet
- Unit-I (1)Document19 pagesUnit-I (1)Kiran janjalNo ratings yet
- MOBILE STATION FUNCTIONS AND IDENTITIESDocument51 pagesMOBILE STATION FUNCTIONS AND IDENTITIESSathish RajaNo ratings yet
- Overview of The Global System For MobileDocument16 pagesOverview of The Global System For MobilevenkateshmukharjiNo ratings yet
- GSM Network Architecture: GSM (Global System For Mobile)Document5 pagesGSM Network Architecture: GSM (Global System For Mobile)mard gharibNo ratings yet
- E5-E6 - Text - Chapter 3. Overview of Mobile CommunicationDocument46 pagesE5-E6 - Text - Chapter 3. Overview of Mobile Communicationsumit15sksNo ratings yet
- GSM Full InitialDocument22 pagesGSM Full Initialvishwajeet1986100% (1)
- Architecture of The GSM NetworkDocument17 pagesArchitecture of The GSM NetworkOmFaNo ratings yet
- GSM Network ArchitectureDocument13 pagesGSM Network ArchitectureZameer HussainNo ratings yet
- Ik1330lab2 (KTH)Document7 pagesIk1330lab2 (KTH)Mehdi RabbaniNo ratings yet
- A GSM Network Is Composed of Several Functional EntitiesDocument3 pagesA GSM Network Is Composed of Several Functional EntitiesNauman ChaudaryNo ratings yet
- DT DocumentsDocument10 pagesDT DocumentsSobaan ArshadNo ratings yet
- GSM Fundamentals: Prepared by Asem Mohammed ShamsDocument38 pagesGSM Fundamentals: Prepared by Asem Mohammed ShamsMahmoud EL-BannaNo ratings yet
- GSM Network ArchitectureDocument5 pagesGSM Network Architecturenarayanan07No ratings yet
- Network ArchitectureDocument17 pagesNetwork ArchitecturesumantabhuinNo ratings yet
- Introduction To GSMDocument3 pagesIntroduction To GSMYasir LiaqatNo ratings yet
- GSM SMS and Call FlowDocument21 pagesGSM SMS and Call FlowLendry NormanNo ratings yet
- GSMDocument33 pagesGSMHemangi Priya Devi DasiNo ratings yet
- GSM TECHNOLOGY OVERVIEWDocument7 pagesGSM TECHNOLOGY OVERVIEWJaspreet KaurNo ratings yet
- Figure 1. General Architecture of A GSM NetworkDocument15 pagesFigure 1. General Architecture of A GSM NetworkPiyush MalviyaNo ratings yet
- Third Generation CDMA Systems for Enhanced Data ServicesFrom EverandThird Generation CDMA Systems for Enhanced Data ServicesRating: 5 out of 5 stars5/5 (1)
- Wisdom Classes Classification and AnalogyDocument26 pagesWisdom Classes Classification and AnalogyTushar SaxenaNo ratings yet
- Andhra Bank - Recruitment of Probationary Officers (PGDBF 2016 - 17)Document1 pageAndhra Bank - Recruitment of Probationary Officers (PGDBF 2016 - 17)Tushar SaxenaNo ratings yet
- UPTU Syllabus for Computer Science & Engineering 2nd YearDocument16 pagesUPTU Syllabus for Computer Science & Engineering 2nd YearPrakash KumarNo ratings yet
- CWE-SPL-IV-Recruitment of Specialist Officers PDFDocument2 pagesCWE-SPL-IV-Recruitment of Specialist Officers PDFTushar SaxenaNo ratings yet
- L-26 (TB) Three Phase TransformerDocument16 pagesL-26 (TB) Three Phase Transformervelisbar100% (1)
- BtechDocument27 pagesBtechakash nairNo ratings yet
- Basic Electrical NotesDocument58 pagesBasic Electrical NotesKamal Joshi100% (2)
- Signal Processing:: ACF PDF CDF Communication:: Block Diagram Analog and Digital Modulation Schemes NoiseDocument1 pageSignal Processing:: ACF PDF CDF Communication:: Block Diagram Analog and Digital Modulation Schemes NoiseTushar SaxenaNo ratings yet
- Signals and CommunicationDocument3 pagesSignals and CommunicationTushar SaxenaNo ratings yet
- Di Capsule BA Part 1Document5 pagesDi Capsule BA Part 1Tushar SaxenaNo ratings yet
- Elitmus Probability Questions For Elitmus - Elitmus Questions For PH Test Page 1 PDFDocument3 pagesElitmus Probability Questions For Elitmus - Elitmus Questions For PH Test Page 1 PDFTushar Saxena0% (1)
- Syll ELitmusDocument2 pagesSyll ELitmusTushar SaxenaNo ratings yet
- 8085 Microprocessor Lab ManualDocument43 pages8085 Microprocessor Lab ManualMukulSinghNo ratings yet
- Cse 2ndyear SyllabusDocument11 pagesCse 2ndyear Syllabusashish jainNo ratings yet
- CL 11Document8 pagesCL 11Tushar SaxenaNo ratings yet
- Syll ELitmusDocument2 pagesSyll ELitmusTushar SaxenaNo ratings yet
- Banking Pathway 2015: English (Mix Quiz) : Bankers Adda Old Logo SeminarDocument7 pagesBanking Pathway 2015: English (Mix Quiz) : Bankers Adda Old Logo SeminarTushar SaxenaNo ratings yet
- Some Basic ConceptsDocument10 pagesSome Basic ConceptsTushar SaxenaNo ratings yet
- Features of IndiaDocument2 pagesFeatures of IndiaTushar SaxenaNo ratings yet
- Days of National and International Importance JanurayDocument7 pagesDays of National and International Importance JanurayTushar SaxenaNo ratings yet
- EMI BasicsDocument11 pagesEMI BasicsTushar SaxenaNo ratings yet
- BCADocument23 pagesBCATushar SaxenaNo ratings yet
- Progrmming LanguageDocument2 pagesProgrmming LanguageTushar SaxenaNo ratings yet
- AdvertisementDocument2 pagesAdvertisementTushar SaxenaNo ratings yet
- P-N Junction DiodeDocument7 pagesP-N Junction DiodeTushar SaxenaNo ratings yet
- Why BPSKDocument1 pageWhy BPSKTushar SaxenaNo ratings yet
- Chemistry Class 11 Syllabus - 2015-2016 CBSEsyllabusDocument4 pagesChemistry Class 11 Syllabus - 2015-2016 CBSEsyllabusTushar SaxenaNo ratings yet
- BJTDocument14 pagesBJTTushar SaxenaNo ratings yet
- Michelle Obama wife of Barack ObamaDocument7 pagesMichelle Obama wife of Barack ObamaTushar SaxenaNo ratings yet
- InjusticeDocument1 pageInjusticeTushar SaxenaNo ratings yet
- AARA HandbookDocument14 pagesAARA HandbookjohnielviraNo ratings yet
- General DynamicsDocument12 pagesGeneral DynamicsNelson Gonzalez EscalanteNo ratings yet
- An 25 Data Repeater NetworkDocument20 pagesAn 25 Data Repeater NetworkSixtusNo ratings yet
- TMA2094F01V2-1 700 MHZ Twin TMA With 850-900 Bypass AISG20Document5 pagesTMA2094F01V2-1 700 MHZ Twin TMA With 850-900 Bypass AISG20David MooneyNo ratings yet
- Lora Part15Document13 pagesLora Part15Alexander SincheNo ratings yet
- TDQM 609016 172718DEI 65FT2v02 - 7 16Document1 pageTDQM 609016 172718DEI 65FT2v02 - 7 16Сергей МирошниченкоNo ratings yet
- AT92MDocument2 pagesAT92MQooNo ratings yet
- Angle Modulation ChapterDocument5 pagesAngle Modulation ChapterJoseph Paulo DandanNo ratings yet
- Tri-Band Clover AntennaDocument5 pagesTri-Band Clover Antenna'Theodora Georgiana100% (1)
- Narrowband IoT A Survey On Downlink and Uplink PerspectivesDocument9 pagesNarrowband IoT A Survey On Downlink and Uplink PerspectivesJúlio SantosNo ratings yet
- 001-91445 AN91445 Antenna Design and RF Layout GuidelinesDocument61 pages001-91445 AN91445 Antenna Design and RF Layout GuidelinesPaulo Lima CamposNo ratings yet
- Antena TrivalDocument14 pagesAntena TrivalazaharNo ratings yet
- Microwave system parameters and calculationsDocument2 pagesMicrowave system parameters and calculationsEdwin Quinlat DevizaNo ratings yet
- ROTEX Telecom Catalog 2021-EnglishDocument32 pagesROTEX Telecom Catalog 2021-EnglishAmine DabbabiNo ratings yet
- Parabolic AntennaDocument36 pagesParabolic Antennawafiuddin suparmanNo ratings yet
- GSM RF Planning ConceptsDocument78 pagesGSM RF Planning ConceptsSuresh Muthukumar89% (9)
- Dual-Band A-Panel Dual Polarization Half-Power Beam WidthDocument1 pageDual-Band A-Panel Dual Polarization Half-Power Beam WidthКурбан УмархановNo ratings yet
- Flexi Remote Radio Head 2TX 900Document5 pagesFlexi Remote Radio Head 2TX 900Reza BordbarNo ratings yet
- Demodulation Demodulation: - Coherent (Synchronous) Demodulation/detectionDocument38 pagesDemodulation Demodulation: - Coherent (Synchronous) Demodulation/detectionanasmos danielNo ratings yet
- En 300 330-1 V1.8.1Document68 pagesEn 300 330-1 V1.8.1SosialNo ratings yet
- FMCW RADAR PROJECT REPORTDocument6 pagesFMCW RADAR PROJECT REPORTshivkumarNo ratings yet
- CDMA TutorialDocument65 pagesCDMA Tutorialsamtec32No ratings yet
- Analog Signal Transmission and ReceptionDocument109 pagesAnalog Signal Transmission and ReceptionMonic AprilliaNo ratings yet
- Unit-3 Diversity Techniques: (1) Repetition Coding and Time DiversityDocument14 pagesUnit-3 Diversity Techniques: (1) Repetition Coding and Time DiversityRakesh DevallaNo ratings yet
- Diversity AntennaDocument12 pagesDiversity AntennaLee NghiaNo ratings yet
- XPIC Feature and 1+1 Protection Configuration: XPIC Group With 1+1 Protection Configured On Single-IF BoardsDocument4 pagesXPIC Feature and 1+1 Protection Configuration: XPIC Group With 1+1 Protection Configured On Single-IF BoardsvydaicaNo ratings yet
- 2019 Rosenberger Multi Beam Antenna Catalogue PDFDocument90 pages2019 Rosenberger Multi Beam Antenna Catalogue PDFGabriel Cenato100% (2)
- Rfid - An Attempt To Make: Everything AutomaticDocument10 pagesRfid - An Attempt To Make: Everything AutomaticRichard LoboNo ratings yet
- v100NX Datasheet PDFDocument2 pagesv100NX Datasheet PDFSergey LukinNo ratings yet
- How GSM WorksDocument24 pagesHow GSM Workssifatb90% (10)