Professional Documents
Culture Documents
Conexión de Modem GSM SIMXXXX MQTT Con AWS
Uploaded by
Mariene Di GregorioOriginal Title
Copyright
Available Formats
Share this document
Did you find this document useful?
Is this content inappropriate?
Report this DocumentCopyright:
Available Formats
Conexión de Modem GSM SIMXXXX MQTT Con AWS
Uploaded by
Mariene Di GregorioCopyright:
Available Formats
Conexión De modem GSM SIMXXXX MQTT con AWS_IOT
Configuracion de Broker mosquitto mqtt dentro de AWS EC2
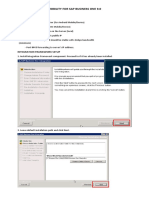
1. Go to the AWS Web Console and access the IAM service (Fig.
2. Click on Roles
3. Click on Create New Role (Fig. 2)
4. Name the role AWSIoTConfigAccess (Fig. 3)
5. Click Next Step
6. Select Amazon EC2 (Fig. 4)
7. Filter with the value AWSIoTConfigAccess (Fig. 5)
8. Select the policy AWSIoTConfigAccess and click on Next Step
9. Review the Role and click on Create Role (Fig. 6)
10. Now that the Role has been created you can go to Amazon EC2. Choose a region,
preferably where AWS IoT is available, in this article I am using Frankfurt.
11. Click on Launch Instance.
12. Scroll and Select Amazon Linux UBUNTU 2018 (Fig. 7)
13. Select the t2.micro instance type (Fig. 8)
14. Click on Next: Configure Instance Details
15. In the IAM Role, select AWSIoTConfigAccess (Fig. 9)
16. Leave default parameters as shown in the picture and click on Next: Add Storage
17. Leave everything as is and click on Next: Tag Instance
18. Give a name to your instance ‘MosquittoBroker’
19. Click on Next: Configure Security Groups
20. Create a new security group (Fig. 10)
21. Ports 1883 and 8883 TCP anyone. SSH tcp 22
22. Review and launch the EC2 instance
23. Follow instructions to connect to the EC2 instance once it is running.
24. Once logged in type the following commands:
sudo apt-get update
sudo apt-get install mosquitto mosquitto-clients
25. Now that we have installed Mosquitto onto our EC2 instance (or local gateway), we will
need to configure the bridge so that the Mosquitto broker can create a connection to AWS
IoT. We will first use the AWS CLI to create the necessary resources on AWS IoT side.
26. Enter the following commands in your terminal:
#Configure the CLI with your region, leave access/private keys blank
aws configure
#Create an IAM policy for the bridge
aws iot create-policy --policy-name bridge --policy-document '{"Version": "2012-10-
17","Statement": [{"Effect": "Allow","Action": "iot:*","Resource": "*"}]}'
#Place yourself in Mosquitto directory
#And create certificates and keys, note the certificate ARN
cd /etc/mosquitto/certs/
sudo aws iot create-keys-and-certificate --set-as-active --certificate-pem-outfile cert.crt --
private-key-outfile private.key --public-key-outfile public.key --region eu-central-1
#List the certificate and copy the ARN in the form of
# arn:aws:iot:eu-central-1:0123456789:cert/xyzxyz
aws iot list-certificates
#Attach the policy to your certificate
aws iot attach-principal-policy --policy-name bridge --principal <ARN_OF_CERTIFICATE>
#Add read permissions to private key and client cert
sudo chmod 644 private.key
sudo chmod 644 cert.crt
#Download root CA certificate
sudo wget https://www.amazontrust.com/repository/AmazonRootCA1.pem
27. We now have a client certificate for our bridge, this certificate is associated with an IAM
policy that will give all permissions to the bridge (this policy must be restricted for your
usage). The bridge will have everything it needs to connect, we just need to edit the
configuration file with our specific parameters for Mosquitto.
#Create the configuration file
sudo nano /etc/mosquitto/conf.d/bridge.conf
28. Edit the following by replacing the value address with your own AWS IoT endpoint. You
can use the AWS CLI to find it with ‘aws iot describe-endpoint’ as mentioned below. Then
copy the content and paste it in the nano editor, finally save the file.
#Copy paste the following in the nano editor:
# =================================================================
# Bridges to AWS IOT
# =================================================================
# AWS IoT endpoint, use AWS CLI 'aws iot describe-endpoint'
connection awsiot
address XXXXXXXXXX.iot.eu-central-1.amazonaws.com:8883
# Specifying which topics are bridged (topics of devices)
# example topic aws/things/clientid1/shadow/update both 1
topic device1 both 1
topic device2 both 1
# Setting protocol version explicitly
bridge_protocol_version mqttv311
bridge_insecure false
# Bridge connection name and MQTT client Id,
# enabling the connection automatically when the broker starts.
cleansession true
clientid bridgeawsiot
start_type automatic
notifications false
log_type all
# =================================================================
# Certificate based SSL/TLS support
# -----------------------------------------------------------------
#Path to the rootCA
bridge_cafile /etc/mosquitto/certs/rootCA.pem
# Path to the PEM encoded client certificate
bridge_certfile /etc/mosquitto/certs/cert.crt
# Path to the PEM encoded client private key
bridge_keyfile /etc/mosquitto/certs/private.key
29. Now we can start the Mosquitto broker with this new configuration:
#Starts Mosquitto in the background
sudo mosquitto -c /etc/mosquitto/conf.d/bridge.conf –d
#Enable Mosquitto to run at startup automatically
sudo chkconfig --level 345 scriptname on
30. Create a thing in AWS IoT Core and attach certificate and policy.
Parametros MQTT mosquito-broker para programar a sim900 o simXXXX
unsigned short MQTTProtocolNameLength;
unsigned short MQTTClientIDLength;
unsigned short MQTTUsernameLength;
unsigned short MQTTPasswordLength;
unsigned short MQTTTopicLength;
const char * MQTTHost ="34.218.99.251"; ///ip publica o dns
const char * MQTTPort ="1883"; //Puerto configurado como listener
const char * MQTTClientID = "device1"; ////topico
const char * MQTTTopic = "device1"; ///mensaje1
const char * MQTTTopic2 = "device1";////mensaje2
const char * MQTTProtocolName = "MQIsdp";
const char MQTTLVL =0x03;//
const char MQTTFlags = 0xC2;//
unsigned short MQTTKeepAlive = 0x3C;
const char * MQTTUsername ="" ;
const char * MQTTPassword ="";
const char MQTTQOS = 0x00;
const char MQTTPacketID = 0x0001;
Requisitos
Tener instalado en la PC el software Putty para acceder a la instancia Ubuntu almacenada en AWS
EC2.
Manejar comandos para edición VI y edición NANO en software libre.
You might also like
- Deploying Certificates Cisco Meeting Server: Design your certificates for CMS services and integrate with Cisco UCM Expressway and TMSFrom EverandDeploying Certificates Cisco Meeting Server: Design your certificates for CMS services and integrate with Cisco UCM Expressway and TMSNo ratings yet
- Cisco CCNA Command Guide: An Introductory Guide for CCNA & Computer Networking Beginners: Computer Networking, #3From EverandCisco CCNA Command Guide: An Introductory Guide for CCNA & Computer Networking Beginners: Computer Networking, #3No ratings yet
- Providing and Using Certificates For MosquittoDocument24 pagesProviding and Using Certificates For MosquittoJan RittelNo ratings yet
- Fortigate Aws DeploymentDocument39 pagesFortigate Aws Deploymentpaulo_an7381No ratings yet
- UM017004E AWS IoT UserManual EngDocument16 pagesUM017004E AWS IoT UserManual EngTomer WNo ratings yet
- 12 Steps To Setup Kubernetes Cluster On AWS EC2 - GoLinuxCloudDocument42 pages12 Steps To Setup Kubernetes Cluster On AWS EC2 - GoLinuxCloudMarcos LinsNo ratings yet
- AWS Toolkit For VS Code: User GuideDocument34 pagesAWS Toolkit For VS Code: User GuideshadmanNo ratings yet
- Installing and Configuring Informatica Intelligent Cloud Services In+ The AWS CloudDocument14 pagesInstalling and Configuring Informatica Intelligent Cloud Services In+ The AWS CloudPrawin RamNo ratings yet
- Iot2050 Aws Iot Greengras Getting Started EnUS en-USDocument4 pagesIot2050 Aws Iot Greengras Getting Started EnUS en-USfaspNo ratings yet
- How To Configure Cisco Trustsec Sgts U PDFDocument27 pagesHow To Configure Cisco Trustsec Sgts U PDFHamza AbdelsalamNo ratings yet
- Lab 5.2 Securing A Router With Cisco Autosecure: Learning ObjectivesDocument8 pagesLab 5.2 Securing A Router With Cisco Autosecure: Learning ObjectivesManuel J.No ratings yet
- Soal Uji Coba LKS Provinsi JatimDocument33 pagesSoal Uji Coba LKS Provinsi JatimARGA DWI NURCAHYONo ratings yet
- Soal Provinsi Modul1 2023Document12 pagesSoal Provinsi Modul1 2023ARGA DWI NURCAHYONo ratings yet
- CiscoDocument16 pagesCiscoShakespeare RodasNo ratings yet
- Con Gure SSH On Routers and Switches: Updated: June 3, 2022 Document ID: 4145Document13 pagesCon Gure SSH On Routers and Switches: Updated: June 3, 2022 Document ID: 4145ehsan.ghaNo ratings yet
- MB CloudSecurityConnectorforAWS AdministratorGuideV1.3Document33 pagesMB CloudSecurityConnectorforAWS AdministratorGuideV1.3Napster KingNo ratings yet
- Seguridad Iot Mos Quit ToDocument10 pagesSeguridad Iot Mos Quit ToHector JuradoNo ratings yet
- Virtual Private CloudDocument52 pagesVirtual Private CloudtanzeelmoinNo ratings yet
- Creating Hybrid ConnectionsDocument22 pagesCreating Hybrid ConnectionsUriel TijerinoNo ratings yet
- AWS RDS CONFIGURATIONDocument37 pagesAWS RDS CONFIGURATIONPranav KavathekarNo ratings yet
- Simple Odoo ERP Auto Scaling On AWS: ObjectivesDocument17 pagesSimple Odoo ERP Auto Scaling On AWS: ObjectivesIdris IdrisNo ratings yet
- VMware Cloud Web Security - Web Proxy Configuration GuideDocument25 pagesVMware Cloud Web Security - Web Proxy Configuration GuideRahul JainNo ratings yet
- EC2: Cost-Effective Strategies for Optimizing Virtual ServersDocument7 pagesEC2: Cost-Effective Strategies for Optimizing Virtual ServersNaresh BabuNo ratings yet
- HowTo-100-CA Signed PxGridClient Selfsigned PxGridISEnodeDocument22 pagesHowTo-100-CA Signed PxGridClient Selfsigned PxGridISEnodeToua LorNo ratings yet
- Use AWS CodeBuild With Amazon Virtual Private Cloud - AWS CodeBuildDocument5 pagesUse AWS CodeBuild With Amazon Virtual Private Cloud - AWS CodeBuildfuturegm2400No ratings yet
- Check Point Vlan v1 0Document26 pagesCheck Point Vlan v1 0Jignesh BhalsodNo ratings yet
- React-Node-MySql Setup On AWSDocument16 pagesReact-Node-MySql Setup On AWSManish KumarNo ratings yet
- API Security Using OIDCDocument7 pagesAPI Security Using OIDCks_reddysekhar7966No ratings yet
- VPN Watchguard - AzureDocument9 pagesVPN Watchguard - Azureaquey1No ratings yet
- AWS Compute With CLIDocument35 pagesAWS Compute With CLIsatyacharanNo ratings yet
- Modul ADocument5 pagesModul AAchmad IlmiNo ratings yet
- Deploy Microsoft IIS 7.0 with A10 ADCDocument31 pagesDeploy Microsoft IIS 7.0 with A10 ADCSebas TianNo ratings yet
- 4.2.3.3 Packet Tracer - Securing Cloud Services in The IoTDocument4 pages4.2.3.3 Packet Tracer - Securing Cloud Services in The IoTHalima AqraaNo ratings yet
- Intelligent Wan Public Key Infrastructure Deployment Guide: Cisco Validated DesignDocument25 pagesIntelligent Wan Public Key Infrastructure Deployment Guide: Cisco Validated Designsrinivas gavaraNo ratings yet
- Migrating A Monolithic Website To Micro Services On Google Kubernetes EngineDocument23 pagesMigrating A Monolithic Website To Micro Services On Google Kubernetes EnginesubodhNo ratings yet
- Configuring Websphere App Server7 Secure Sockets Layer Client Certificate Authentication Sas9 3 Ebi ServerDocument28 pagesConfiguring Websphere App Server7 Secure Sockets Layer Client Certificate Authentication Sas9 3 Ebi ServerAshokNo ratings yet
- Mobility For Sap Business One 9.0: Integration Framework SetupDocument13 pagesMobility For Sap Business One 9.0: Integration Framework SetupRobeth John BacalanNo ratings yet
- Neoway AWS IoT Core Application Notes V1.3.20201216155848Document25 pagesNeoway AWS IoT Core Application Notes V1.3.20201216155848Applied Embedded ProgrammersNo ratings yet
- MB SSLDocument33 pagesMB SSLRajesh0% (1)
- NetBrain Quick Setup Guide AWSDocument47 pagesNetBrain Quick Setup Guide AWSajrob69_187428023No ratings yet
- CCP VPN Routera Routerb Config 00 PDFDocument20 pagesCCP VPN Routera Routerb Config 00 PDFharry2uniqueNo ratings yet
- Supply and Installation of SSL Certificate For Central Statistics Agency (Csa) As-Built DocumentDocument14 pagesSupply and Installation of SSL Certificate For Central Statistics Agency (Csa) As-Built DocumentAhmedin abukiaNo ratings yet
- Ruckus Icx Cisco Ise Cwa DPDocument26 pagesRuckus Icx Cisco Ise Cwa DPpaulo_an7381No ratings yet
- B UCSM CLI Configuration Guide 2 0 Chapter 0110Document24 pagesB UCSM CLI Configuration Guide 2 0 Chapter 0110Alexander Lopez PulidoNo ratings yet
- MQTT Secure Connection Over TLSDocument8 pagesMQTT Secure Connection Over TLSMohamed Yassine GaraliNo ratings yet
- CitectSCADA V7.20 WebClient Quick Start GuideDocument56 pagesCitectSCADA V7.20 WebClient Quick Start GuidefachriyansyahNo ratings yet
- Cisco CSR 1000v Avec GNS3Document9 pagesCisco CSR 1000v Avec GNS3reno51No ratings yet
- Assignment 3Document4 pagesAssignment 3Shubham ThorboleNo ratings yet
- Configuring A VPN Using Easy VPN and An Ipsec Tunnel: Figure 6-1Document12 pagesConfiguring A VPN Using Easy VPN and An Ipsec Tunnel: Figure 6-1Toufik AchrafeNo ratings yet
- Configuring An Ipsec VPN Tunnel Between A Cisco Sa 500 and A Mac Ipsecuritas ClientDocument11 pagesConfiguring An Ipsec VPN Tunnel Between A Cisco Sa 500 and A Mac Ipsecuritas Clientjhoan9924No ratings yet
- CISCO Identity Services Engine: 802.1X and TACACS+ Configuration LabDocument59 pagesCISCO Identity Services Engine: 802.1X and TACACS+ Configuration LabIlham CahyaNo ratings yet
- How To Create VTIDocument3 pagesHow To Create VTIEsteban GraciaNo ratings yet
- 4.3.9 Packet Tracer Configure Site To Site VPN Answer KeyDocument4 pages4.3.9 Packet Tracer Configure Site To Site VPN Answer Keymalaklmawt0000No ratings yet
- KB Implementing SD-WAN WorkbookDocument150 pagesKB Implementing SD-WAN WorkbookPrashantPatilNo ratings yet
- Kubernetes On AWS Free TierDocument13 pagesKubernetes On AWS Free TierMallikarjun BankoliNo ratings yet
- Configuring PPTP (VPDN) Server On A Cisco RouterDocument7 pagesConfiguring PPTP (VPDN) Server On A Cisco RouterMaria VirginiaNo ratings yet
- Virtual Private CloudDocument17 pagesVirtual Private CloudvgprasadNo ratings yet
- Solution - VNXe3200 - Configure MPIO On Windows For iSCSI LUNsDocument15 pagesSolution - VNXe3200 - Configure MPIO On Windows For iSCSI LUNsAitor LongarteNo ratings yet
- AWS Iot - Vending MachineDocument4 pagesAWS Iot - Vending Machinerevathi kunchalaNo ratings yet
- Cisco Unified Computing System 2.2 v1: About This Cisco SolutionDocument54 pagesCisco Unified Computing System 2.2 v1: About This Cisco SolutionChad LeeNo ratings yet
- Re-registering a vehicle in Karnataka - A step-by-step guideDocument4 pagesRe-registering a vehicle in Karnataka - A step-by-step guideHidayathulla HasanNo ratings yet
- Lorenzo Tan National High School 2018-2019 Federated Parent Teacher Association Officers and Board of DirectorsDocument4 pagesLorenzo Tan National High School 2018-2019 Federated Parent Teacher Association Officers and Board of DirectorsWilliam Vincent SoriaNo ratings yet
- Connect Debug LogDocument20 pagesConnect Debug LogrohanZorba100% (1)
- PACiS GTW EN O C80Document170 pagesPACiS GTW EN O C80paradiseparasNo ratings yet
- Comments PRAG FinalDocument13 pagesComments PRAG FinalcristiancaluianNo ratings yet
- Nevada Reports 1882-1883 (17 Nev.) PDFDocument334 pagesNevada Reports 1882-1883 (17 Nev.) PDFthadzigsNo ratings yet
- Document - University Admission SystemDocument100 pagesDocument - University Admission SystemNaresh SharmaNo ratings yet
- AfghanistanLML OnlinDocument117 pagesAfghanistanLML Onlinعارف حسینNo ratings yet
- Big Kaiser2019 PDFDocument624 pagesBig Kaiser2019 PDFGoto SamNo ratings yet
- Lista Carti Audio Dezvoltare PersonalaDocument4 pagesLista Carti Audio Dezvoltare PersonalaNicu Osan50% (2)
- Mechanical Engineering Semester SchemeDocument35 pagesMechanical Engineering Semester Schemesantvan jagtapNo ratings yet
- Application For Transmission of Shares / DebenturesDocument2 pagesApplication For Transmission of Shares / DebenturesCS VIJAY THAKURNo ratings yet
- Altracs: A Superior Thread-Former For Light AlloysDocument8 pagesAltracs: A Superior Thread-Former For Light AlloysSquidwardNo ratings yet
- Decolonising The FutureDocument20 pagesDecolonising The Futurebybee7207No ratings yet
- r6 - SCV - PV - 2012 June MarkB PDFDocument32 pagesr6 - SCV - PV - 2012 June MarkB PDFsanjiivNo ratings yet
- Study of The Pre-Processing Impact in A Facial Recognition SystemDocument11 pagesStudy of The Pre-Processing Impact in A Facial Recognition Systemalmudena aguileraNo ratings yet
- Cis Bin Haider GRP LTD - HSBC BankDocument5 pagesCis Bin Haider GRP LTD - HSBC BankEllerNo ratings yet
- 452-Chapter 15 PDFDocument14 pages452-Chapter 15 PDFYoan Barriga BerriosNo ratings yet
- F INALITYp 3Document23 pagesF INALITYp 3api-3701467100% (1)
- One SheetDocument1 pageOne Sheetadeel ghouseNo ratings yet
- Themed: MathematicsDocument32 pagesThemed: MathematicsMohamed LamihNo ratings yet
- 18th Century Political Formation. CL 7Document22 pages18th Century Political Formation. CL 7Gamer AditKills100% (1)
- Design of Grounding System For GIS Indoor SubstationDocument4 pagesDesign of Grounding System For GIS Indoor Substationzerferuz67% (3)
- Segilola Gold ProjectDocument11 pagesSegilola Gold ProjectaishaNo ratings yet
- Rate of Grease Penetration of Flexible Barrier Materials (Rapid Method)Document3 pagesRate of Grease Penetration of Flexible Barrier Materials (Rapid Method)DanZel Dan100% (1)
- 2021 Subsector OutlooksDocument24 pages2021 Subsector OutlooksHungNo ratings yet
- Chetan Tour and Travel: Pickup Spot: Destination SpotDocument2 pagesChetan Tour and Travel: Pickup Spot: Destination SpotRahulNo ratings yet
- RAN15.0 Feature ListDocument34 pagesRAN15.0 Feature ListmyososNo ratings yet
- 20-Sdms-02 (Overhead Line Accessories) Rev01Document15 pages20-Sdms-02 (Overhead Line Accessories) Rev01Haytham BafoNo ratings yet