100% found this document useful (1 vote)
5K views15 pagesFortigate Firewall
The document provides step-by-step instructions for configuring a Fortigate firewall to:
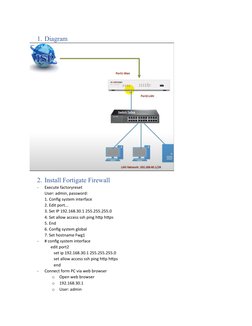
1) Install the Fortigate and configure basic network and firewall settings including interfaces, DHCP, and NAT rules.
2) Separate networks for servers and clients and allow traffic between them.
3) Enable web filtering and application control to block specific websites and applications.
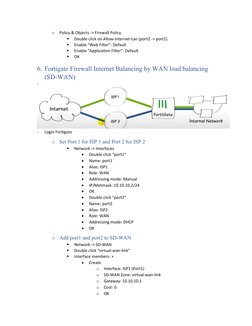
4) Configure WAN load balancing across two ISPs using SD-WAN.
Uploaded by
Steven itCopyright
© © All Rights Reserved
We take content rights seriously. If you suspect this is your content, claim it here.
Available Formats
Download as DOCX, PDF, TXT or read online on Scribd
100% found this document useful (1 vote)
5K views15 pagesFortigate Firewall
The document provides step-by-step instructions for configuring a Fortigate firewall to:
1) Install the Fortigate and configure basic network and firewall settings including interfaces, DHCP, and NAT rules.
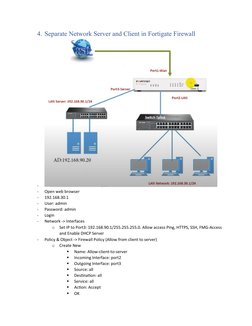
2) Separate networks for servers and clients and allow traffic between them.
3) Enable web filtering and application control to block specific websites and applications.
4) Configure WAN load balancing across two ISPs using SD-WAN.
Uploaded by
Steven itCopyright
© © All Rights Reserved
We take content rights seriously. If you suspect this is your content, claim it here.
Available Formats
Download as DOCX, PDF, TXT or read online on Scribd
- Diagram and Initial Setup
- Configure Client Access
- Separate Network and Client
- Block Websites and Control Applications
- Load Balancing with SD-WAN
- High Availability Setup
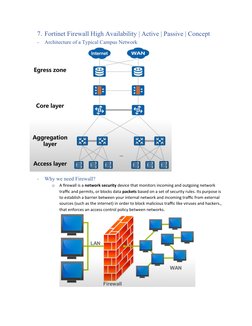
- SDWAN with 3 ISP