Professional Documents
Culture Documents
IN1020 Oblig 1
Uploaded by
Kacper RzadkowskiOriginal Description:
Copyright
Available Formats
Share this document
Did you find this document useful?
Is this content inappropriate?
Report this DocumentCopyright:
Available Formats
IN1020 Oblig 1
Uploaded by
Kacper RzadkowskiCopyright:
Available Formats
1) The school's LMS containing personal information of pupils, teachers and parents as well
as the pupils' grades has a lot of values that are valuable for certain kinds of people. For
example, the pupils grades are much more valuable for pupils than for the teachers, as it is a
direct factor of the individual pupil’s academic success. In this case, the LMS becomes a
valuable target for pupils (or their parents) that want access to their grade register so that
they can change their (or somebody else's) grades. As the server room is located within the
school, a student may want to break in that room and gain physical access to the servers
where the LMS is stored. Also because the schools LSM is sent through a wireless
connection, anyone has the possibility of tuning into that connection and stealing the
students, parents or teachers personal data.
2) Confidentiality - Confidentiality is the access of sensitive data, for example: personal
data or banking information. When confidentiality is breached, unauthorised access to
confidential information is granted (or rather acquired). This quickly becomes dangerous as
sensitive information in the hands of wrong people may have serious consequences, for
example somebody may order products by invoice online with somebody's name and
personal ID, making you pay for the ordered products.
Integrity - Integrity is the access to modify data, a relevant example is: the modification of
pupils' grades in the school’s LMS, making the student’s grades (data) incorrect. The danger
of breached integrity is that the information found, for example: in a school’s LMS, cannot be
trusted to be authentic anymore.
Accessibility - Accessibility is the fact that a user’s data should be available to that person,
for example: diagnoses in your health journal. When accessibility fails, the user cannot
access the data files necessary for the service. The danger of accessibility is that necessary
information may be encrypted by a “hacker” and often that information is important to have
access to by the user.
3) A security control for...
a) confidentiality is access control, for example in the form of a two step verification
procedure, this makes it harder for wrong kinds of people to access your account and by that
also: your data.
b) integrity is encryption. That is, by encrypting the files that contain data. Even if a “hacker”
gains access to those files, they will have a hard time modifying or even opening those files.
They would have to decrypt them which may take a very long time (brute force) without vital
information about the person that’s being hacked.
4) I would definitely recommend accountability and authentication in this case, as these
security goals are an important factor in creating a secure system. The entirety of CIT can be
strengthened by authentication (ex: two-step verification), in addition is accountability
necessary for prevention of future attacks as well as having knowledge of who performed the
attack (ex: eventlog or inbuilt detection).
5) In order to implement the schools policy there needs to be a way to log onto the schools
service as a student, teacher or administrator. This can be done through the website and
mobile app as a separate login function for the respective users. The students do not get the
same access keys as teachers and administrators etc..With that being implemented, the
students do not have the same access to information as teachers etc.
6) The school absolutely needs to pay extra attention before they implement a report-
absence module, as they don’t want pupils to be able to report absence even though they
were at school and vice versa . This is a matter of integrity, the school needs to pay extra
attention to authentication, accountability and maybe a hierarchy of access. For example, a
teachers/admins absence report overwrites a student's report. In the case of the student
being present at school but still being reported as absent or another student reporting on
other students.
7) There are various dangers in having a network without a password, for example an
attacker may use a compromised or false access point. In this case the attacker gains
access to the user's data. A false access point is when the attacker creates a network that
claims to be the intended network (A to B), because a wireless device connects to the
access point with the strongest signal, there is no reason for the device to connect to the
intended network. A compromised access point is when the attacker can gain access to the
victims data by “listening” to the connection between the user and the host (A to B(attacker)
to C).
Both examples are dangers that violate confidentiality, which means that a network without a
password is not safe.
8) If I was to change a grade in the schools grade register, I would set up a compromised or
false access point right before the school opens in order to hopefully get access to an
admin's data. With that data I can access the grade registry and change whichever grades I
want.
You might also like
- KivevoDocument5 pagesKivevoPeter KivevoNo ratings yet
- Name Usama Ahtsham Roll No. 48 Class Bsit 6 Subject System and Network Administration Submitted To. Sir Chaudhary Ahmad SabDocument11 pagesName Usama Ahtsham Roll No. 48 Class Bsit 6 Subject System and Network Administration Submitted To. Sir Chaudhary Ahmad Sabاسامہ بن ریاستNo ratings yet
- Assign Edit ForDocument5 pagesAssign Edit ForLyvamie Sualog RaymundoNo ratings yet
- Data Privacy in Education SectorDocument25 pagesData Privacy in Education SectorReymart SupleoNo ratings yet
- 1.1 Statement of The ProblemsDocument75 pages1.1 Statement of The ProblemsK.Rohit GoudNo ratings yet
- Faculty: University of Southern California The Department of International AcademyDocument7 pagesFaculty: University of Southern California The Department of International AcademyZichun XuNo ratings yet
- Cybersecurity Considerations For K-12 Schools and School DistrictsDocument8 pagesCybersecurity Considerations For K-12 Schools and School DistrictsAudie Mar AgpawaNo ratings yet
- Elec4470 Hw1 Solution s2023Document7 pagesElec4470 Hw1 Solution s2023Sanyukta ReddyNo ratings yet
- Student Information System For Starlight School IncorporatedDocument28 pagesStudent Information System For Starlight School IncorporatedNick Joshua VasquezNo ratings yet
- Alvin Patrick R. Mayo Final RequirementsDocument7 pagesAlvin Patrick R. Mayo Final RequirementsAlvinPatrick Ibrahim RamonesMayoNo ratings yet
- Social EngineeringDocument2 pagesSocial EngineeringMiko Rosales100% (1)
- Moodlegate Securing Computer Driven ExamDocument7 pagesMoodlegate Securing Computer Driven ExammarkuskojakNo ratings yet
- Design and Implementation of Online Clearance SystemDocument21 pagesDesign and Implementation of Online Clearance SystemPeace NgozichukwukaNo ratings yet
- JUSUADocument3 pagesJUSUAJohn CamachoNo ratings yet
- Chapter One 1.1 Background of The StudyDocument32 pagesChapter One 1.1 Background of The StudyPax OladeleNo ratings yet
- Web-Based School Management System Using Cloud Technology For "Holy Trinity School Obando, Inc."Document10 pagesWeb-Based School Management System Using Cloud Technology For "Holy Trinity School Obando, Inc."benz bhenzNo ratings yet
- Web 3.0. and EducationDocument2 pagesWeb 3.0. and EducationIshaan PachauriNo ratings yet
- 20BCS5646 - 20BCS5634 (Anushka, Srishti Jain)Document23 pages20BCS5646 - 20BCS5634 (Anushka, Srishti Jain)bhanuNo ratings yet
- CRYPTOGRAPHYDocument8 pagesCRYPTOGRAPHYmegha.garg1No ratings yet
- Enrollment System IntroductionDocument2 pagesEnrollment System IntroductionLuis Norbert SantiagoNo ratings yet
- Notification To Data Subjects (Canvas) - 17Document2 pagesNotification To Data Subjects (Canvas) - 17Disguised owlNo ratings yet
- Enrollment System 2 PDF FreeDocument18 pagesEnrollment System 2 PDF FreeMonchie RoseteNo ratings yet
- School Internet Filtering: What Are We Really Blocking?Document4 pagesSchool Internet Filtering: What Are We Really Blocking?Jessica MaloneyNo ratings yet
- My Record of Group Contribution Group 2 Members:: Ortega, Katherine TDocument8 pagesMy Record of Group Contribution Group 2 Members:: Ortega, Katherine TKirsten FernandoNo ratings yet
- Final Examination QuestionsDocument6 pagesFinal Examination QuestionsCarlos Baul DavidNo ratings yet
- Class Teacher RefDocument1 pageClass Teacher Refsajee11No ratings yet
- Student Information SystemDocument49 pagesStudent Information SystemFLEXCODEC TECHNo ratings yet
- Ict Final RequirementDocument7 pagesIct Final RequirementSaturnino A. Padungao Jr.No ratings yet
- Group 1 Chapter 1Document6 pagesGroup 1 Chapter 1Matias, Nadine Rianna D.No ratings yet
- WA - Personalized Learning (FINAL)Document2 pagesWA - Personalized Learning (FINAL)Kathleen BenavidezNo ratings yet
- Enhanced Security For Online Exams Through Data VisualizationDocument8 pagesEnhanced Security For Online Exams Through Data VisualizationGanesh JonnaNo ratings yet
- Inhs Teacher ResearchDocument29 pagesInhs Teacher ResearchJANNA NAVARRANo ratings yet
- Cyber Safety K-12 Fact Sheet 508CDocument8 pagesCyber Safety K-12 Fact Sheet 508Chasimah5768No ratings yet
- Methodology 1Document3 pagesMethodology 1YuuchaNo ratings yet
- Module 201Document3 pagesModule 201api-516201614No ratings yet
- Teaching Online SafetyDocument5 pagesTeaching Online SafetyKevin MartinNo ratings yet
- My-Record-of-Group-Contribution KTODocument9 pagesMy-Record-of-Group-Contribution KTOKirsten FernandoNo ratings yet
- Chapter One 1.1 Background of The StudyDocument28 pagesChapter One 1.1 Background of The StudyM.HassanNo ratings yet
- Cyber Security Concerns in E-Learning Ed PDFDocument7 pagesCyber Security Concerns in E-Learning Ed PDFmitaNo ratings yet
- Student Tuition FessDocument7 pagesStudent Tuition FessAjewole Eben TopeNo ratings yet
- Cyber Security AwarenessDocument4 pagesCyber Security Awarenessatejoy12jesuscaresNo ratings yet
- The Remote Proctoring System Is AnDocument3 pagesThe Remote Proctoring System Is Antarun rathi 220No ratings yet
- Student Management System - A Survey: International Research Journal of Computer Science (IRJCS)Document5 pagesStudent Management System - A Survey: International Research Journal of Computer Science (IRJCS)Ima JeevarajNo ratings yet
- 1.1 Introduction and Its BackgroundDocument7 pages1.1 Introduction and Its BackgroundJoevette CarpioNo ratings yet
- Enrollment SystemDocument18 pagesEnrollment SystemJimuel Ocaso100% (3)
- 22 ML and LSTMDocument22 pages22 ML and LSTMabourifa hananeNo ratings yet
- Five Issues or Challenges Pertaining To Computer SecurityDocument1 pageFive Issues or Challenges Pertaining To Computer SecurityBea TrinidadNo ratings yet
- Unit 1Document15 pagesUnit 1abcd1011891No ratings yet
- Sessional Exam Answers Cys 121Document6 pagesSessional Exam Answers Cys 121christianandretembaNo ratings yet
- Grammarian THESIS-AMS-FinalDocument100 pagesGrammarian THESIS-AMS-FinalJoevan PonceNo ratings yet
- Capstone Documents LCCDocument16 pagesCapstone Documents LCCmarksalaoNo ratings yet
- The Relationship Between Technology and Ethics From Society To SchoolsDocument8 pagesThe Relationship Between Technology and Ethics From Society To SchoolsJanice A. BragatNo ratings yet
- M Learning: Cloud ComputingDocument26 pagesM Learning: Cloud ComputingOdumodu UmuleriNo ratings yet
- A Web-Based Lost and Found System For Gardner College DilimanDocument3 pagesA Web-Based Lost and Found System For Gardner College DilimanAngela Louise TomasNo ratings yet
- Online Monitoring and Prevention of Internal Security Threats in Academic CampusesDocument6 pagesOnline Monitoring and Prevention of Internal Security Threats in Academic CampusesInternational Journal of Application or Innovation in Engineering & ManagementNo ratings yet
- Practical Research CSSDocument5 pagesPractical Research CSSbryan garciaNo ratings yet
- Privacy and SecurityDocument3 pagesPrivacy and Securityapi-325943973No ratings yet
- Chapter One: 1.1 Background of The StudyDocument29 pagesChapter One: 1.1 Background of The StudyIgbani VictoryNo ratings yet
- Paradox Magellan-Catalog enDocument11 pagesParadox Magellan-Catalog enCornelCiorcanNo ratings yet
- MSC in Multimedia Research ProposalDocument13 pagesMSC in Multimedia Research ProposalKealeboga Duece ThoboloNo ratings yet
- Data Protection - Are We Prepared - Economic Laws Practice UpdatepdfDocument25 pagesData Protection - Are We Prepared - Economic Laws Practice UpdatepdfAnchit JassalNo ratings yet
- Load BalancingDocument7 pagesLoad BalancingParuchuri KiranNo ratings yet
- Visiting Sap AG WalldorfDocument14 pagesVisiting Sap AG WalldorfIza ŠušteršičNo ratings yet
- BRKDCN 2099 PDFDocument111 pagesBRKDCN 2099 PDFTariq SheikhNo ratings yet
- Lip PlateDocument4 pagesLip PlateNaimi AzizNo ratings yet
- Config AP Pertemuan SBLM UTSDocument5 pagesConfig AP Pertemuan SBLM UTSRevando LumbanrajaNo ratings yet
- Advanced Java SecurityDocument10 pagesAdvanced Java SecurityArunendu MajiNo ratings yet
- Research Project On The Effects of Marketing Mix Elements On Student EnrolmentDocument87 pagesResearch Project On The Effects of Marketing Mix Elements On Student EnrolmentWellingtonMarumbiNo ratings yet
- Publish To The World: Powerful PythonDocument3 pagesPublish To The World: Powerful PythonErivaldoNo ratings yet
- Network SiteDocument6 pagesNetwork Sitedesx redjNo ratings yet
- Advance Java MCQDocument3 pagesAdvance Java MCQPrathamesh PatilNo ratings yet
- BRM Project ProposalDocument4 pagesBRM Project ProposalVijeta BaruaNo ratings yet
- OTA000004 SDH Principle ISSUE 2.20Document52 pagesOTA000004 SDH Principle ISSUE 2.20rainydays2010No ratings yet
- User S Manual For CBMS-StatSimPro5.0Document22 pagesUser S Manual For CBMS-StatSimPro5.0William Yagyagan CornelioNo ratings yet
- Ims DC TransitionDocument39 pagesIms DC TransitionNitin Digraje100% (3)
- PDF Affiliate Marketing Service in Delhi IndiaDocument3 pagesPDF Affiliate Marketing Service in Delhi IndiaKomal SwamiNo ratings yet
- Active Reports 9Document1,100 pagesActive Reports 9faraonchisNo ratings yet
- ADC01-DOC-146 ADVC Protocol Manual DNP3 R15 WEB PDFDocument40 pagesADC01-DOC-146 ADVC Protocol Manual DNP3 R15 WEB PDFAlexander MorenoNo ratings yet
- Yamrajgaming V3Document194 pagesYamrajgaming V3sniper GamingNo ratings yet
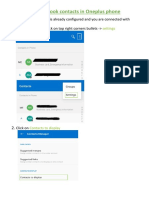
- Access Outlook Contacts in Oneplus PhoneDocument2 pagesAccess Outlook Contacts in Oneplus PhonesossmsNo ratings yet
- Work Intruction Bwa5 Wibas ExeDocument80 pagesWork Intruction Bwa5 Wibas ExeElvan Lumbung100% (1)
- Alvin C. Samonte Yahoo Inc Case Study AnalysisDocument19 pagesAlvin C. Samonte Yahoo Inc Case Study AnalysisAlvin SamonteNo ratings yet
- PUSOY DOS: A Multiplayer Web Based Card Gaming AppDocument11 pagesPUSOY DOS: A Multiplayer Web Based Card Gaming Appyukihime kaizerNo ratings yet
- Business Plan Paper Khamiri CSRDocument30 pagesBusiness Plan Paper Khamiri CSRStill TheaNo ratings yet
- Inside Anti-Vaccine Telegram GroupsDocument1 pageInside Anti-Vaccine Telegram GroupsdaedalxNo ratings yet
- Aman Sanduja: Date of BirthDocument3 pagesAman Sanduja: Date of BirthamansandujaNo ratings yet
- Online Pay ManagerDocument55 pagesOnline Pay Managersadysharma67% (3)
- M04 - Part 2 Case Project - Lake Point Security Consulting-Shaker MohammadtomDocument12 pagesM04 - Part 2 Case Project - Lake Point Security Consulting-Shaker MohammadtomShakerNo ratings yet