Professional Documents
Culture Documents
365 Summary
Uploaded by
S MulaOriginal Title
Copyright
Available Formats
Share this document
Did you find this document useful?
Is this content inappropriate?
Report this DocumentCopyright:
Available Formats
365 Summary
Uploaded by
S MulaCopyright:
Available Formats
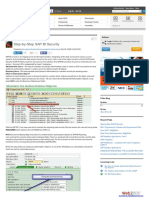
Investigate unusual use patterns for
accounts
https://compliance.microsoft.com Use Unified Access Logging Data
Not available for all access levels
Less-featured licenses offer fewer
Handles may different authentication
monitoring capabilities
Watch for Unauthorized Account Cloud SaaS Endpoint functions for Microsoft 365
License Downgrades
Look for accounts of E5, E3 level being Publicly Accessible
demoted to P1, SBP
icrosoft 365 Incident
M
Response: Identification Status code reveals details
Unauthorized Conditional Access policy about targeted user
changes
Look for MFA Access Changes Invalid credentials
New geographic, IP address MFA
exceptions
login.microsoft.com MFA (Microsoft) required
Returns Detailed Errors
et-Mailbox -Identity donovan.lea@
G
falsimentis.com | Format-List *audit* MFA (third-party) required
Investigate Accounts with Disabled Account disabled
-AuditEnabled=$false
Auditing
-AuditOwner @() Account locked out
Search logs for Set-Mailbox commands
with arguments:
Attacker Opportunity for Password
-AuditDelegate @()
Attacks
-AuditAdmin @()
Attack/Defense Tool Leverages login.microsoft.com for
Password Spray
Requires valid credentials!
Checks Multiple Microsoft Login
MSOLSpray Uses Error Codes to Optimize Attack
Endpoints
Use without valid credentials may trigger
account lockout Takes a User List and a Single Password
MFASweep
Identified Endpoints That Don't Require
e.g., Conditional Access exceptions MFA On-by-default Feature for Microsoft 365
Offers Brief Recommendations to Attempts to Thwart Many Types of Some advanced capabilities available with
Leverage Access Password Attacks more expensive user licenses
ICROSOFT 365
M
PASSWORD ATTACKS Account Lockout: Disable Login for
Universally applied across accounts Azure Smart Lockout Single Account After multiple failed attempts
Basic MFA is Effective
Doesn't always meet business needs After 10 login failures regardless of
username
Permit exceptions to MFA requirements Source Blocking: Don't Allow IP to Login
After 3 login failures for Azure .gov
Geolocation
Smart Lockout Defeats Common Spray
IP addresses or ranges of IP addresses MFA Bypass Attacks ... when originating from a single source IP
Conditional Access (CA)
Specific platforms
Amazon AWS Service
Legacy systems
Maps a single hostname to multiple
microservices
Looking for opportunities to login Attackers Use Valid Credentials with
without MFA MFA
HTTP Service for API Connectivity Each worker has a unique IP
Uses thousands of HTTP workers
Attack Tool to Easily Setup AWS API Worker IPs originate in the AWS IP
Gateway AWS API Gateway address space For the target region
Specify a Command, Region, and URL Cheap! 1 million requests is $1
Attacker submits HTTP requests through FireProx Creates the AWS API Gateway Attacker can proxy requests to target
FireProx HTTP endpoint
AWS API Gateway hostname Endpoint ttackers will use cloud services
A
against your organization
enerates URL like https://7t4id9w399.
G AWS API GW forwards attacker request
execute-api.us-east-1.amazonaws.com/ Attacker Opportunity to Masquerade IP through worker
fireprox/
ttackers can be very crafty in
A
Integrates with MSOLSpray Each request will come from a different
how they implement attacks
Specify FireProx API URL with source IP address
MSOLSpray -URL parameter
You might also like
- SAP Business Network Administration Process GuideDocument152 pagesSAP Business Network Administration Process Guidecharan.swastikNo ratings yet
- Lukhdhirji Engineering College (Diploma), Morbi.: Local Search Engine Project (UDP)Document22 pagesLukhdhirji Engineering College (Diploma), Morbi.: Local Search Engine Project (UDP)vicky popatNo ratings yet
- Identity and Access Management SimplifiedDocument10 pagesIdentity and Access Management SimplifiedManish AgarwalNo ratings yet
- Windows MatrixDocument1 pageWindows MatrixfolalikNo ratings yet
- IBM Tivoli Access Manager For Enterprise Single Sign-OnDocument6 pagesIBM Tivoli Access Manager For Enterprise Single Sign-OnPoorna KumarNo ratings yet
- Sample Tech Writing - Solution Architecture, Ritzie Edson V. LaminaDocument25 pagesSample Tech Writing - Solution Architecture, Ritzie Edson V. LaminaritzieevlaminaNo ratings yet
- ARX Presenation PDFDocument10 pagesARX Presenation PDFintellectdesignNo ratings yet
- Dark Trace - Mapping To MITREDocument19 pagesDark Trace - Mapping To MITREDonghan KimNo ratings yet
- Enable or disable Keycloak featuresDocument5 pagesEnable or disable Keycloak featureshisyam darwisNo ratings yet
- Pharma PlanningDocument1 pagePharma PlanningBhavin FadaduNo ratings yet
- Eilago 2.0 Master-FeaturesDocument4 pagesEilago 2.0 Master-FeaturesMazhar WaqarNo ratings yet
- Ems E3Document1 pageEms E3andini eldanantyNo ratings yet
- Usecase Diagram For Visitor: AvailableconnectionsDocument12 pagesUsecase Diagram For Visitor: AvailableconnectionsBaluNo ratings yet
- A2 - Broken Authentication: © 2020 Nexusguard Limited - Confidential & ProprietaryDocument9 pagesA2 - Broken Authentication: © 2020 Nexusguard Limited - Confidential & ProprietaryCesar Jr SalacataNo ratings yet
- Online Shopping System Synopsis by Atulya and SakshiDocument147 pagesOnline Shopping System Synopsis by Atulya and SakshiAtulya AgrawalNo ratings yet
- B2B Project PlanningDocument14 pagesB2B Project PlanningGian BacayNo ratings yet
- (EV 2.4) (8-Sep-21) Access Request - 08sepDocument2 pages(EV 2.4) (8-Sep-21) Access Request - 08sepsohaib siddiqueNo ratings yet
- Fort I AuthenticatorDocument6 pagesFort I AuthenticatorPremNo ratings yet
- Step-by-Step SAP BI Security: Kamaljeet - KharbandaDocument22 pagesStep-by-Step SAP BI Security: Kamaljeet - KharbandaJaveed PetashaikNo ratings yet
- M&E System Architecture For UNICEF - Turkey: Sub-Form BulderDocument1 pageM&E System Architecture For UNICEF - Turkey: Sub-Form BulderMohammad EreiqatNo ratings yet
- BKJ S4hana2021 BPD en MXDocument47 pagesBKJ S4hana2021 BPD en MXDiego AgüeroNo ratings yet
- Lateral Movement Detection GPO Settings Cheat Sheet: Accounts, Users and GroupsDocument1 pageLateral Movement Detection GPO Settings Cheat Sheet: Accounts, Users and GroupsSergio TamayoNo ratings yet
- Overview of Payroll IntegrationsDocument10 pagesOverview of Payroll IntegrationsrifkiNo ratings yet
- Online Grocery Shopping Made EasyDocument40 pagesOnline Grocery Shopping Made EasyZia RahmanNo ratings yet
- 1ez S4hana2021 BPD en MXDocument37 pages1ez S4hana2021 BPD en MXEnrique MarquezNo ratings yet
- Sprint 18 Showcase V1Document12 pagesSprint 18 Showcase V1Medha KhajuriaNo ratings yet
- Key ClockDocument6 pagesKey ClockJithin MNo ratings yet
- Supervised By: RAJIB DAS Lecturer of CSE Dep. IsttDocument19 pagesSupervised By: RAJIB DAS Lecturer of CSE Dep. IsttMirza WaleedNo ratings yet
- PDF DokumentumDocument1 pagePDF DokumentumPetra FarkasNo ratings yet
- Employee Management SystemDocument1 pageEmployee Management SystemOlugbile Adeyinka OlumideNo ratings yet
- Mailing SystemDocument23 pagesMailing SystemStromer07No ratings yet
- Sim 208Document62 pagesSim 208jatinashraNo ratings yet
- Fina Cle Overview U Corr B 1709719131632Document17 pagesFina Cle Overview U Corr B 1709719131632Avishek KhanNo ratings yet
- FIWS-DCM-AN-BI Portal Service Architecture - v0.1Document8 pagesFIWS-DCM-AN-BI Portal Service Architecture - v0.1Nam Nguyễn ThànhNo ratings yet
- 1ez S4hana2021 BPD en inDocument34 pages1ez S4hana2021 BPD en invenkatNo ratings yet
- Kofax MarkView AP Solution OverviewDocument8 pagesKofax MarkView AP Solution OverviewSesirekha RavinuthulaNo ratings yet
- weAccess user requestDocument1 pageweAccess user requestPRECIOUS DIANNE BARDON-MEMPINNo ratings yet
- Agenda: Stage Setting - EDM Intro EDM Governance Who Are The Data Stewards ? EDM RequirementsDocument3 pagesAgenda: Stage Setting - EDM Intro EDM Governance Who Are The Data Stewards ? EDM Requirementssudiptocontact17No ratings yet
- New Updated PAM Access Request Form-3Document1 pageNew Updated PAM Access Request Form-3bekiami2013No ratings yet
- i-bizRAKYAT maintenance form updatesDocument2 pagesi-bizRAKYAT maintenance form updatesKhairul AbidinNo ratings yet
- Evidian WAM Training MaterialDocument180 pagesEvidian WAM Training MaterialuuekshiidkfhslkjdiNo ratings yet
- Sun Identity Manager and SAP GRCDocument46 pagesSun Identity Manager and SAP GRCBurak Semir100% (1)
- Fairsure Impl DocumentDocument5 pagesFairsure Impl DocumentkevinakaluziaNo ratings yet
- Identity and Access Management PMI Westchester Quality SIG Presentation September 12 2017Document20 pagesIdentity and Access Management PMI Westchester Quality SIG Presentation September 12 2017venkatesh VRNo ratings yet
- SRM PASSPORT SYSTEMDocument327 pagesSRM PASSPORT SYSTEMtamilarasi87thulasiNo ratings yet
- SFAFINITY vs SalesForce comparisonDocument4 pagesSFAFINITY vs SalesForce comparisonAnonymous pmzOTxaNo ratings yet
- Registrasi, Login, Pembayaran Tagihan, Transfer dalam Aplikasi AgenDocument2 pagesRegistrasi, Login, Pembayaran Tagihan, Transfer dalam Aplikasi AgenWidyawan Widarto 闘志No ratings yet
- Building Microsoft Teams Integration and WorkflowsDocument310 pagesBuilding Microsoft Teams Integration and WorkflowsRafa MoscoteNo ratings yet
- Create Customer Record (PWM)Document1 pageCreate Customer Record (PWM)Ram Mohan MishraNo ratings yet
- RDP_DFIR_ADDocument1 pageRDP_DFIR_ADlekshmanp1No ratings yet
- Datasheet Password Reset ServerDocument2 pagesDatasheet Password Reset ServerRadu CostinNo ratings yet
- External User (Agent) Registration Use Case-Diagram: Create Online AccountDocument16 pagesExternal User (Agent) Registration Use Case-Diagram: Create Online AccountSawijamesNo ratings yet
- External User (Agent) Registration Use Case-Diagram: Create Online AccountDocument16 pagesExternal User (Agent) Registration Use Case-Diagram: Create Online AccountSawijamesNo ratings yet
- WeAccess Revised Exhibit 11 - Resetting of Password User ID Activation Unlocking v.2Document1 pageWeAccess Revised Exhibit 11 - Resetting of Password User ID Activation Unlocking v.2April Rose AlagosNo ratings yet
- Web Application Penetration Testing Checklist: More Than 200 Custom Testcases Prepared By: Tushar Verma Recon PhaseDocument13 pagesWeb Application Penetration Testing Checklist: More Than 200 Custom Testcases Prepared By: Tushar Verma Recon PhasehologNo ratings yet
- Identity-Centrify PAM in Action: A Step-by-Step ApproachDocument1 pageIdentity-Centrify PAM in Action: A Step-by-Step ApproachShahram SametNo ratings yet
- Web Application Penetration Testing Checklist: More Than 200 Custom Test Cases Prepared By: Tushar Verma Recon PhaseDocument13 pagesWeb Application Penetration Testing Checklist: More Than 200 Custom Test Cases Prepared By: Tushar Verma Recon PhaseHafa kaliNo ratings yet
- 5 SAP Cloud Identity Access Gov Access RequestDocument29 pages5 SAP Cloud Identity Access Gov Access RequestSasha BankNo ratings yet
- 2007-2008 NEW Electrical Engineering TitlesDocument40 pages2007-2008 NEW Electrical Engineering Titlesmeenakshi sharmaNo ratings yet
- Eoy - CS (Vi) 23-24Document3 pagesEoy - CS (Vi) 23-24www.shahbazhaider165No ratings yet
- Capcut UseDocument16 pagesCapcut UseDatu Donnavie100% (1)
- EstoqueDocument56 pagesEstoqueGustavo OliveiraNo ratings yet
- Super Mario Color by NumberDocument13 pagesSuper Mario Color by NumberAdriana CruzNo ratings yet
- SAP FMS - PlanningDocument38 pagesSAP FMS - PlanningPallavi RastogiNo ratings yet
- Global Master's in Blockchain Technologies: Master's Degree by The IL3-Universitat de BarcelonaDocument4 pagesGlobal Master's in Blockchain Technologies: Master's Degree by The IL3-Universitat de BarcelonaAungsinghla MarmaNo ratings yet
- MA8692 Supplement EU MLDocument4 pagesMA8692 Supplement EU MLMaxsilva85No ratings yet
- My Updated Resume - MQ AdministratorDocument4 pagesMy Updated Resume - MQ AdministratorChiranjeevi KNo ratings yet
- 11 Training and SupportDocument9 pages11 Training and Supportcarsan87No ratings yet
- Automatic Speed Control and Accident Avoidance of Vehicle UsingDocument34 pagesAutomatic Speed Control and Accident Avoidance of Vehicle UsingK HariNo ratings yet
- Unit 4 - PythonDocument10 pagesUnit 4 - PythonPrakash MNo ratings yet
- Lab 05 - Boolean Function ImplementationDocument10 pagesLab 05 - Boolean Function ImplementationNashowan Gamal AlhadrmiNo ratings yet
- Automate financial consolidation and reportingDocument2 pagesAutomate financial consolidation and reportingSarwar GolamNo ratings yet
- Computeractive - 27 September 2023Document76 pagesComputeractive - 27 September 20239stm1q96No ratings yet
- Adc 1Document29 pagesAdc 1A10-14Rajat KumarNo ratings yet
- Manual SigmaDocument2 pagesManual SigmaespartanotpmNo ratings yet
- Process Synchronization: Silberschatz, Galvin and Gagne ©2013 Operating System Concepts - 9 EditionDocument66 pagesProcess Synchronization: Silberschatz, Galvin and Gagne ©2013 Operating System Concepts - 9 EditionUtkarshNo ratings yet
- Leach Routing Protocol Implementation in ns2Document38 pagesLeach Routing Protocol Implementation in ns2regragui50% (2)
- PACOM 8003 Intelligent Controller DatasheetDocument4 pagesPACOM 8003 Intelligent Controller DatasheetADA100% (1)
- Jam Digital: Praktikum Komponen ListDocument11 pagesJam Digital: Praktikum Komponen ListMuhaimin HasanudinNo ratings yet
- Importance of The Management Information SystemDocument2 pagesImportance of The Management Information SystemKazim AzrulNo ratings yet
- San Gabriel Senior High School Poblacion, San Gabriel, La Union Formative Test Empowerement Technologies-11 (Quarter 4)Document2 pagesSan Gabriel Senior High School Poblacion, San Gabriel, La Union Formative Test Empowerement Technologies-11 (Quarter 4)Glenda AstodilloNo ratings yet
- Instruction 1115 Fuel Limit AdjustmentDocument9 pagesInstruction 1115 Fuel Limit AdjustmentSergei KurpishNo ratings yet
- Datasheet FLOWSIC600-XT p406745 enDocument22 pagesDatasheet FLOWSIC600-XT p406745 enMarco ApodacaNo ratings yet
- Security QuizDocument5 pagesSecurity QuizIanne Merh100% (1)
- Fas 22Document15 pagesFas 22sam tariqNo ratings yet
- Program 2Document8 pagesProgram 2api-515961562No ratings yet
- Etulink Product MapDocument30 pagesEtulink Product MapAlexander PischulinNo ratings yet
- Computer Fundamentals GuideDocument17 pagesComputer Fundamentals GuideMohit PacharNo ratings yet