Professional Documents
Culture Documents
Sem 3
Sem 3
Uploaded by
gujjar262069Original Title
Copyright
Available Formats
Share this document
Did you find this document useful?
Is this content inappropriate?
Report this DocumentCopyright:
Available Formats
Sem 3
Sem 3
Uploaded by
gujjar262069Copyright:
Available Formats
SCHEME OF TEACHING AND EXAMINATION FOR M.TECH.
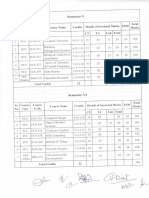
COMPUTER SCIENCE and ENGINEERING III Semester Subject Code 10SCS31 10SCS32x 10SCS33x 10SCS34 10SCS35 Name of the Subject Advances in VLSI Design and Algorithms Elective III Elective IV Project Phase - II Evaluation of Project Phase-I Total Hours per Week Field Work/ Lecture Practical Tutorials 04 04 04 --12 -----Elective IV 10SCS331 10SCS332 10SCS333 Duration of Exam in Hours 03 03 03 03 03 Marks for I.A. 50 50 50 50 200 Exam 100 100 100 -300 Total Marks 150 150 150 -50 500
09
Elective III 10SCS321 Wireless and Cellular Networks 10SCS322 10SCS323 Advances in Storage Area Networks Advances in Pattern Classification
Analysis of Computer Networks Advances in Compiler Design Information Security
Note:3 Days Course work and 3 Days for Project Work
Semester 3
Advances in VLSI Design and Algorithms Subject Code : 10SCS31 No of Lecture Hrs/Week : 4 Total No of Lecture Hours : 52 IA Marks : 50 Exam hours : 3 Exam Marks : 100
1. Introduction to Digital systems and VLSI: Why Design Integrated Circuits? Integrated Circuits manufacturing; Integrated Circuit Design Techniques; IP-Based Design. 2. Fabrication and Devices: Introduction; Fabrication processes; Fabrication theory and practice; Reliability. 3. Sequential Machines: Introduction; Latches and Flip-flops; Sequential systems and clocking disciplines; Performance analysis; Clock generators; Sequential systems design, Power optimization, Design validation, Sequential testing. 4. Subsystem Design: Introduction; Combinational shifters; Adders; ALUs; Multipliers; High-density memory; Image sensors; FPGAs; PLA; Buses and networks on chips; Data paths; Subsystems as IP. 5. Architecture Design: Introduction; Hardware description languages; Register Transfer design; Pipelining; High-level synthesis; Architecture for low power; GALS systems; Architecture testing; IP components; Design methodologies; Multiprocessor system-on-Chip design. 6. Simulations: General remarks; Gate-level modeling and simulations; Switch-level modeling and simulation.
TEXT BOOKS: 1. Wayne Wolf: Modern VLSI design, 3rd edition, Pearson Education, 2007. 2. Sabih H Gerez: Algorithms for VLSI Design Automation, Wiley India, 2007, Wireless and Cellular Networks Subject Code : 10SCS321 No of Lecture Hrs/Week : 4 Total No of Lecture Hours : 52 IA Marks : 50 Exam hours : 3 Exam Marks : 100
1. Introduction to Wireless Communication Systems: Evolution of Mobile Radio Communications Mobil Radio Systems around the world examples of Wireless Communication Systems, Paging System, Cordless Telephone System. Cellular Telephone Systems, Comparison of Common Wireless Communications Systems. 2. Modern Wireless Communications Systems: Second generation (2G), Cellular Networks, evolution of 2.5G, TDMA Standards, Third Generation (3G) Wireless Networks, Wireless Local Loop (WLL) and LMDS, Wireless Local Area Networks (WLANs), Bluetooth and Personal Area Networks (PANS) 3. The Cellular Concept: System Design Fundamentals, Introduction, Frequency reuse, channel assignment strategies, handoff strategies prioritizing handoffs, Practical Handoff considerations. Interference and system capacity, co-channel interference and system capacity, channel planning for wireless systems, adjacent channel interference, power control for reducing interference. 4. Mobile Radio Propagation: Introduction to radio wave propagation, Free space propagation model, Relating power to electric field, Reflection, Diffraction, Scattering. 5. Modulation Techniques for Mobile Radio: Frequency modulation Vs amplitude modulation, Amplitude modulation, Angle modulation, Digital Modulation, Linear Modulation techniques Binary phases shift keying (BPSK), Differential Phase Shift Keying (DPSK), Quadrature Phase Shift Keying (QPSK), Constant envelope modulation Binary Frequency Shift Keying, Minimum Shift Keying (MSK), Gaussian Minimum Shift Keying (GMSK). 6. Multiple Access Techniques for Wireless Communications: Introduction to Multiple access, Frequency Division Multiple Access (FDMA), Time Division Multiple Access (TDMA), Spread Spectrum Multiple Access, Space Division Multiple Access (SDMA), Packet Radio. Protocols, Reservation Protocols Reservation ALOHA, Packet Reservation Multiple Access (PRMA), Capacity of cellular systems. 7. Wireless Networking: Introduction, Difference between Wireless and Fixed Telephone Networks, Development of Wireless Networks, First generation, second generation, third generation. TEXT BOOKS: 1. Theodore S Rappaport: Wireless Communications, Principles and Practice, 2nd Edition, Pearson Education Asia, 2002. REFERENCE BOOKS: 1. William C Y Lee: Mobile Communications Engineering Theory and Applications, 2nd Edition, McGraw Hill, 1998. 2. William Stallings: Wireless Communications and Networks, Pearson Education Asia, 2002. Advances in Storage Area Networks Subject Code : 10SCS322 No of Lecture Hrs/Week : 4 Total No of Lecture Hours : 52 IA Marks : 50 Exam hours : 3 Exam Marks : 100
1. Introduction: Server Centric IT Architecture and its Limitations; Storage Centric IT Architecture and its advantages. Case study: Replacing a server with Storage Networks The Data Storage and Data Access problem; The Battle for size and access. 2. Intelligent Disk Subsystems: Architecture of Intelligent Disk Subsystems; Hard disks and Internal I/O Channels; JBOD, Storage virtualization using RAID and different RAID levels; Caching: Acceleration of Hard Disk Access; Intelligent disk subsystems, Availability of disk subsystems. 3. I/O Techniques: The Physical I/O path from the CPU to the Storage System; SCSI; Fibre Channel Protocol Stack; Fibre Channel SAN; IP Storage. 4. Network Attached Storage: The NAS Architecture, The NAS hardware Architecture, The NAS Sotfware Architecture, Network connectivity, NAS as a storage system. 5. File System and NAS: Local File Systems; Network file Systems and file servers; Shared Disk file systems; Comparison of fibre Channel and NAS. 6. Storage Virtualization: Definition of Storage virtualization ; Implementation Considerations; Storage virtualization on Block or file level; Storage virtualization on various levels of the storage Network; Symmetric and Asymmetric storage virtualization in the Network. 7. SAN Architecture and Hardware devices: Overview, Creating a Network for storage; SAN Hardware devices; The fibre channel switch; Host Bus Adaptors; Putting the storage in SAN; Fabric operation from a Hardware perspective. 8. Software Components of SAN: The switchs Operating system; Device Drivers; Supporting the switchs components; Configuration options for SANs.
9. Management: Planning Business Continuity; Managing availability; Managing Serviceability; Capacity planning; Security considerations. Text Book: 1. Ulf Troppens, Rainer Erkens and Wolfgang Muller: Storage Networks Explained, Wiley India, 2007. Reference Books: 1. 2. 3. Marc Farley: Storage Networking Fundamentals An Introduction to Storage Devices, Subsystems, Applications, Management, and File Systems, Cisco Press, 2005. Robert Spalding: Storage Networks The Complete Reference, Tata McGraw-Hill, 2003. Richard Barker and Paul Massiglia: Storage Area Network Essentials A CompleteGuide to understanding and Implementing SANs, Wiley India, 2006.
Advances in Pattern Classification Subject Code : 10SCS323 No of Lecture Hrs/Week : 4 Total No of Lecture Hours : 52 IA Marks : 50 Exam hours : 3 Exam Marks : 100
1. Introduction: Polynomial Curve Fitting, Probability Theory, Probability Distributions, Model Selection, Decision Theory, Information Theory 2. Linear Models for Regression: Linear Basis Function Models, The Bias Variance Decomposition, Bayesian Linear Regression, Bayesian Model Comparison, The Evidence Approximation, Limitations of Fixed Basis Functions 3. Linear Models for Classification: Discriminant Functions, Probabilistic Generative Models, Probabilistic Discriminative Models, The Laplace Approximation, Bayesian Logistic Regression 4. Kernel Methods: Dual Representations, Constructing Kernels, RBF Networks, Gaussian Processes, Sparse Kernel Machines: SVMs, Multiclass SVMs, Relevance Vector Machines 5. Unsupervised Learning: Introduction, Association Rules, Cluster Analysis, Self-Organizing Maps, Principal Components, Curves and Surfaces, Non-negative Matrix Factorization, Independent Component Analysis and Exploratory Projection Pursuit, Multidimensional Scaling, Nonlinear Dimension Reduction and Local Multidimensional Scaling, The Google PageRank Algorithm 6. Mixture Models and EM: Mixtures of Gaussians, An alternative view of EM, The EM Algorithm in general. 7. High-Dimensional Problems: The Curse of Dimensionality, Diagonal Linear Discriminant Analysis and Nearest Shrunken Centroids, Linear Classifiers with Quadratic Regularization, Linear Classifiers with L1 Regularization, Classification when Features are Unavailable, High-Dimensional Regression: Supervised Principal Components, Feature Assessment and the Multiple-Testing Problem.
Text Books: 1. Christopher M Bishop: Pattern Recognition and Machine Learning, Springer, 2006. 2. Trevor Hastie, Robert Tibshirani, and Jerome Friedman: The Elements of Statistical Learning, Springer, 2008.
Reference Books: 1. 2. R. O. Duda, P. E. Hart, and D. G. Stork: Pattern Classification by 2 nd edition, Wiley Interscience, 2001. Sergios Theodoridis and Konstantinos Koutroumbas: Pattern Recognition, 2nd Edition, Elsevier, 2003. Analysis of Computer Networks
Subject Code : 10SCS331 No of Lecture Hrs/Week : 4 Total No of Lecture Hours : 52
IA Marks : 50 Exam hours : 3 Exam Marks : 100
1. Introduction: Two examples of analysis: Efficient transport of packet voice calls, Achievable throughput in an input-queuing packet switch; The importance of quantitative modeling in the Engineering of Telecommunication Networks. 2. Multiplexing: Network performance and source characterization; Stream sessions in a packet network: Delay guarantees; Elastic transfers in a packet network; Packet multiplexing over Wireless networks. 3. Stream Sessions: Deterministic Network Analysis: Events and processes in packet multiplexer models: Universal concepts; Deterministic traffic models and Network Calculus; Scheduling; Application to a packet voice example; Connection setup: The RSVP approach; Scheduling (continued). 3. Stream Sessions: Stochastic Analysis: Deterministic analysis can yield loose bounds; Stochastic traffic models; Additional notation; Performance measures; Littles theorem, Brumelles theorem, and applications; Multiplexer analysis with stationary and ergodic traffic; The effective bandwidth approach for admission control; Application to the packet voice example; Stochastic analysis with shaped traffic; Multihop networks; Long-Range-Dependent traffic. 4. Adaptive Bandwidth Sharing for Elastic Traffic: Elastic transfers in a Network; Network parameters and performance objectives; Sharing a single link; Rate-Based Control; Window-Based Control: General Principles; TCP: The Internets Adaptive Window Protocol; Bandwidth sharing in a Network.
TEXT BOOKS: 1. Anurag Kumar, D. Manjunath, Joy Kuri: Communication Networking An Analytical Approach, Elsevier, 2004. REFERENCE BOOKS: 1. M. Schwartz: Broadband Integrated Networks, Prentice Hall PTR, 1996. 2. J. Walrand, P. Varaiya: High Performance Communication Networks, 2nd Edition, Morgan Kaufmann, 1999.
Advances in Compiler Design Subject Code : 10SCS332 No of Lecture Hrs/Week : 4 Total No of Lecture Hours : 52 IA Marks : 50 Exam hours : 3 Exam Marks : 100
1. Introduction and Review: Language processors; The structure of a Compiler; The evolution of programming languages; The science of building a compiler; Applications of Compiler technology; Programming language basics. 2. Topics in Code Generation: Issues in the design of Code Generator; Peephole optimization; Register allocation and assignment; Instruction selection by tree rewriting; Optimal code generation for expressions; Dynamic programming code generation. 3. Machine-Independent Optimizations: The principle sources of optimization; Introduction to data flow analysis; Foundations of data flow analysis; Constant propagation; Partial-redundancy elimination; Loops in flow graphs; Region-based analysis; Symbolic analysis. 4. Instruction-Level Parallelism: Process architectures; Code-scheduling constraints; Basic-block scheduling; Global code scheduling; Software pipelining. 5. Optimizing for Parallelism and Locality: Basic concepts; An example of matrix multiplication; Iteration spaces; Affine array indexes; Data reuse; Array data dependence analysis; Finding synchronization-free parallelism; Synchronization between parallel loops; Pipelining; Locality optimizations.
TEXT BOOKS: 1. Alfred V Aho, Monica S. Lam, Ravi Sethi, Jeffrey D Ullman: Compilers - Principles, Techniques and Tools, 2nd Edition, Pearson, 2007. REFERENCE BOOKS: 1. Charles N. Fischer, Richard J. leBlanc, Jr.: Crafting a Compiler with C, Pearson, 1991. 2. Andrew W Apple: Modern Compiler Implementation in C, Cambridge University Press, 1997. 3. Kenneth C Louden: Compiler Construction Principles & Practice, Cengage Learning, 1997. Information Security
Subject Code : 10SCS333 No of Lecture Hrs/Week : 4 Total No of Lecture Hours : 52
IA Marks : 50 Exam hours : 3 Exam Marks : 100
1. Introduction to Information Security: Introduction; What is security? Critical characteristics of information; NSTISSC security model; Approaches to information security implementation; The Security System Development Life Cycle; Information Security Terminology. 2. Planning for Security: Introduction; Information Security Policy, Standards, and Practices; The Information Security Blue Print. 3. Security Technology: Firewalls and VPNs: Introduction, Physical design, Firewalls, Protecting Remote Connections. Intrusion Detection, Access control and Other Security Tools: Introduction; Intrusion Detection Systems (IDS); Honey Pots, Honey Nets, and Padded cell systems; Scanning and Analysis Tools; Access Control Devices. 4. Information Security maintenance: Introduction; Security Management Models; The Maintenance Model. 5. Introduction to Network Security: Attacks, Services, and Mechanisms; Security Attacks; Security Services; A model for Internetwork Security; Internet Standards and RFCs; Wireless network security. 6. Cryptography: Conventional Encryption Principles and Algorithms; Cipher Block Modes of Operation; Location of encryption devices; Key distribution; Approaches to message authentication; Secure Hash functions and HMAC; Public Key Cryptography Principles and Algorithms; Digital Signatures; Key management. 7. Authentication Applications: Kerberos, X.509 Directory Authentication Service. 8. Electronic Mail Security: Pretty Good Privacy (PGP), S/MIME. 9. IP Security: IP Security Overview, IP Security Architecture, Authentication Header, Encapsulating Security Payload, Combining Security Associations, Key Management. 10. Web Security: Web security requirements, Secure Socket layer (SSL) and Transport layer Security (TLS), Secure Electronic Transaction (SET). 11. Software: Introduction; Software flaws; Malware; Software-based attacks; Digital Rights Management; TEXT BOOKS: 1. Michael E. Whitman and Herbert J. Mattord: Principles of Information Security, 2nd Edition, Cengage Learning, 2005. 2. William Stallings: Network Security Essentials Applications and Standards, Person, 2000. 3. Deven N. Shah: Information Security Principles and Practice, Wiley India, 2009. REFERENCE BOOKS: 1. Behrouz A. Forouzan: Cryptography and Network Security, Tata McGraw-Hill, 2007.
You might also like
- Quantum Communication, Quantum Networks, and Quantum SensingFrom EverandQuantum Communication, Quantum Networks, and Quantum SensingNo ratings yet
- 2013-2014 ADMITTED BATCH: Two Year Course StructureDocument41 pages2013-2014 ADMITTED BATCH: Two Year Course StructuremurthykalkiNo ratings yet
- Seventh SemDocument12 pagesSeventh SemHardik KanthariyaNo ratings yet
- 7 SemDocument8 pages7 Semraju rama raj kumarNo ratings yet
- Fifth Semester: BTCS 501 Computer Networks - IIDocument6 pagesFifth Semester: BTCS 501 Computer Networks - IIPrincess deepikaNo ratings yet
- 3rd CSE IT New Syllabus 2019 20Document19 pages3rd CSE IT New Syllabus 2019 20Harsh Vardhan HBTUNo ratings yet
- Seventh / Eightth SemesterDocument21 pagesSeventh / Eightth SemesterYashwant KumarNo ratings yet
- B.tech Cse 7th Sem SyllabusDocument6 pagesB.tech Cse 7th Sem SyllabusHarseerat SidhuNo ratings yet
- Viii Semester Wireless CommunicationDocument19 pagesViii Semester Wireless Communicationbharath18haiNo ratings yet
- Semester - 8 GTU SyllabusDocument9 pagesSemester - 8 GTU SyllabusPanchal Dhaval MNo ratings yet
- BTech ECE Syllabus PDFDocument67 pagesBTech ECE Syllabus PDFaveaNo ratings yet
- Semester - II Information Technology 2008 CourseDocument11 pagesSemester - II Information Technology 2008 CourseMikhail AdvaniNo ratings yet
- Unit No. Course Contents: Course Code: BCS601 Course Name: Introduction To Embedded System CreditsDocument7 pagesUnit No. Course Contents: Course Code: BCS601 Course Name: Introduction To Embedded System CreditsTanayyNo ratings yet
- SyllabusDocument10 pagesSyllabusShahid AsmarNo ratings yet
- ECE 6640 Digital CommunicationsDocument67 pagesECE 6640 Digital CommunicationsSanaullah KhanNo ratings yet
- EE6640 WmuDocument537 pagesEE6640 WmuMo LêNo ratings yet
- Preface: Dr. B. K. SridharaDocument49 pagesPreface: Dr. B. K. SridharaJeevith JeeviNo ratings yet
- Regulations - 2009Document14 pagesRegulations - 2009iamsabhereNo ratings yet
- 8th Sem ECE SyllabusDocument10 pages8th Sem ECE SyllabusSanjeev DesaiNo ratings yet
- Course Syllabus of IT PG PDFDocument39 pagesCourse Syllabus of IT PG PDFteklayNo ratings yet
- MCTA - 301 (A) Data Mining and Warehousing: Reference BooksDocument8 pagesMCTA - 301 (A) Data Mining and Warehousing: Reference BookssurajamitNo ratings yet
- 6 Bca 6th Sem Syllabus UemjDocument19 pages6 Bca 6th Sem Syllabus Uemjapi-351162654No ratings yet
- 18-M.Tech (VLSI Design and Embedded System) PDFDocument31 pages18-M.Tech (VLSI Design and Embedded System) PDFAhilan AppathuraiNo ratings yet
- Semester-6: Course Structure: Lectures: 2/labs: 1 Credit Hours: 3 ObjectivesDocument6 pagesSemester-6: Course Structure: Lectures: 2/labs: 1 Credit Hours: 3 ObjectivesAsghar AliNo ratings yet
- Syllabus 2nd SemDocument18 pagesSyllabus 2nd SemMithun PvNo ratings yet
- Syllabus CS-0000 V Sem All SubjectDocument11 pagesSyllabus CS-0000 V Sem All Subject12ashivangtiwariNo ratings yet
- Eighth Semester SyllabusDocument11 pagesEighth Semester SyllabustrishatdNo ratings yet
- Advance Computer Architecture & Peripherals: Duration 3 Hours 3 1 2 6 70 22Document7 pagesAdvance Computer Architecture & Peripherals: Duration 3 Hours 3 1 2 6 70 22Yogendra AgnihotriNo ratings yet
- M. Tech 1st Year 2nd SemDocument7 pagesM. Tech 1st Year 2nd Sem9866726771No ratings yet
- Semester 1: 1. Course Structure and Scheme of Evaluation (Semester-Wise, Along With Curriculum Details)Document19 pagesSemester 1: 1. Course Structure and Scheme of Evaluation (Semester-Wise, Along With Curriculum Details)Sneha NargundkarNo ratings yet
- Rajasthan Technical University, Kota Detailed Syllabus For B.Tech.Document21 pagesRajasthan Technical University, Kota Detailed Syllabus For B.Tech.Dolly HussainNo ratings yet
- SyllabusDocument13 pagesSyllabusKartikey KatyalNo ratings yet
- Digital Electronics and CommunicationDocument25 pagesDigital Electronics and CommunicationShreyasKamatNo ratings yet
- CSE - 5th Semester NotesDocument5 pagesCSE - 5th Semester NotesShubham ChoudharyNo ratings yet
- (Applicable From The Academic Session 2018-2019) : Syllabus For B. Tech in Computer Science & EngineeringDocument24 pages(Applicable From The Academic Session 2018-2019) : Syllabus For B. Tech in Computer Science & EngineeringAdhara MukherjeeNo ratings yet
- Semester I 32creditsDocument11 pagesSemester I 32creditsAkshayRMishraNo ratings yet
- M. Tech. - 2018Document46 pagesM. Tech. - 2018hyuNo ratings yet
- Sem 6Document23 pagesSem 6Soumya BeraNo ratings yet
- CSVTU BE VII Semester IT Fault Tolerant Systems SyllabusDocument7 pagesCSVTU BE VII Semester IT Fault Tolerant Systems SyllabusBaswamy CseNo ratings yet
- Wireless Sensor NetworksDocument2 pagesWireless Sensor NetworkspratheepNo ratings yet
- (Formerly West Bengal University of Technology) : (Applicable From The Academic Session 2018-2019)Document28 pages(Formerly West Bengal University of Technology) : (Applicable From The Academic Session 2018-2019)nitish kumarNo ratings yet
- ECE Elective SyllabusDocument34 pagesECE Elective SyllabusPratyush ChauhanNo ratings yet
- Distributed SystemsDocument7 pagesDistributed SystemsMurari NayuduNo ratings yet
- Describe The Courses You Have Taught by Summarizing The Course Content and Assignments Required. Subjects I Will Be Comfortable To TeachDocument15 pagesDescribe The Courses You Have Taught by Summarizing The Course Content and Assignments Required. Subjects I Will Be Comfortable To TeachPushan Kumar DattaNo ratings yet
- WSN SyllabusDocument2 pagesWSN SyllabusAnil V. WalkeNo ratings yet
- SylabiiDocument6 pagesSylabiiashit kumarNo ratings yet
- M.E-CSE Anna UniversityDocument25 pagesM.E-CSE Anna UniversityPushparaj KaruNo ratings yet
- Eee Study Material at UTSADocument9 pagesEee Study Material at UTSAShreyas KamathNo ratings yet
- Academic Regulations Course Structure AND Detailed Syllabus: Computer Science and EngineeringDocument20 pagesAcademic Regulations Course Structure AND Detailed Syllabus: Computer Science and EngineeringneczuberbashaNo ratings yet
- 3rd Year Elective CoursesDocument5 pages3rd Year Elective CoursesRicharrdNo ratings yet
- 3 Semester Mtce 701 A Knowledge Based System Design: ReferencesDocument8 pages3 Semester Mtce 701 A Knowledge Based System Design: ReferencesZeeshan KhursheedNo ratings yet
- BE ETC Syllabus 2012 Course Revised SyllabusDocument61 pagesBE ETC Syllabus 2012 Course Revised Syllabusaniket5941No ratings yet
- Network Coding: Fundamentals and ApplicationsFrom EverandNetwork Coding: Fundamentals and ApplicationsMuriel MedardNo ratings yet
- Cognitive Radio Communication and Networking: Principles and PracticeFrom EverandCognitive Radio Communication and Networking: Principles and PracticeNo ratings yet
- Energy Management in Wireless Sensor NetworksFrom EverandEnergy Management in Wireless Sensor NetworksRating: 4 out of 5 stars4/5 (1)
- Multihop Wireless Networks: Opportunistic RoutingFrom EverandMultihop Wireless Networks: Opportunistic RoutingRating: 4 out of 5 stars4/5 (1)
- Top-Down Digital VLSI Design: From Architectures to Gate-Level Circuits and FPGAsFrom EverandTop-Down Digital VLSI Design: From Architectures to Gate-Level Circuits and FPGAsNo ratings yet
- Problem-Solving Through Programming: First/Second Semester B.E. Degree ExaminationDocument2 pagesProblem-Solving Through Programming: First/Second Semester B.E. Degree ExaminationAnser PashaNo ratings yet
- Problem-Solving Through Programming: First/Second Semester B.E. Degree ExaminationDocument2 pagesProblem-Solving Through Programming: First/Second Semester B.E. Degree ExaminationAnser PashaNo ratings yet
- 2.3 Starting Activities With Implicit IntentsDocument35 pages2.3 Starting Activities With Implicit IntentsAnser PashaNo ratings yet
- 1.3 Text and Scrolling ViewsDocument19 pages1.3 Text and Scrolling ViewsAnser PashaNo ratings yet
- 3.3 Using The Android Support LibrariesDocument25 pages3.3 Using The Android Support LibrariesAnser PashaNo ratings yet
- 2.2 The Activity Lifecycle and Managing StateDocument38 pages2.2 The Activity Lifecycle and Managing StateAnser PashaNo ratings yet
- DMS - Imp Questions - VTU ExamDocument10 pagesDMS - Imp Questions - VTU ExamAnser PashaNo ratings yet
- Lab4 F12Document8 pagesLab4 F12Anser PashaNo ratings yet
- Cssyll18-19 DMSDocument2 pagesCssyll18-19 DMSAnser PashaNo ratings yet
- Lab 1Document10 pagesLab 1Anser PashaNo ratings yet
- Lab 1Document10 pagesLab 1Anser PashaNo ratings yet
- MAHE PHD Guidelines - Oct 2019Document14 pagesMAHE PHD Guidelines - Oct 2019Anser PashaNo ratings yet
- Unit7-NAN 2Document38 pagesUnit7-NAN 2Anser PashaNo ratings yet
- Is SchemeDocument6 pagesIs SchemeAnser PashaNo ratings yet
- Aed Unit3Document68 pagesAed Unit3Anser Pasha100% (1)
- Computer Concepts and C ProgrammingDocument2 pagesComputer Concepts and C ProgrammingAnser Pasha50% (2)
- Data Structure MCQ 1Document5 pagesData Structure MCQ 1Anser PashaNo ratings yet
- SDH Training Part3 NCP IP ConfigDocument9 pagesSDH Training Part3 NCP IP ConfignazilaNo ratings yet
- Assignment-Cn: Syeda Pakiza ImranDocument5 pagesAssignment-Cn: Syeda Pakiza Imrannauman tariqNo ratings yet
- HG6543C - Data Sheet&Product ManualDocument104 pagesHG6543C - Data Sheet&Product ManualAdan CastilloNo ratings yet
- Huawei E5331 Specs PDFDocument18 pagesHuawei E5331 Specs PDFjohnrey_lidresNo ratings yet
- 323-1851-101 (6500 R12.6 Datacomms Planning Procedures) Issue1 PDFDocument634 pages323-1851-101 (6500 R12.6 Datacomms Planning Procedures) Issue1 PDFtnhphuongNo ratings yet
- rv120w AdminDocument163 pagesrv120w AdminOswaldo Diaz NievesNo ratings yet
- Altai C1An Super Wifi Cpe/Ap Control Traffic Throughput FlexiblyDocument2 pagesAltai C1An Super Wifi Cpe/Ap Control Traffic Throughput FlexiblyRoyer Casaverde DiazNo ratings yet
- Hillstone E-1000 Series Next-Generation Firewall: E1100W / E1100WG3w / E1600 / E1606 / E1700Document4 pagesHillstone E-1000 Series Next-Generation Firewall: E1100W / E1100WG3w / E1600 / E1606 / E1700Isabél CampoverdeNo ratings yet
- H12 221 Enu V18.02 1Document126 pagesH12 221 Enu V18.02 1Bă ĶŕNo ratings yet
- Application Layer ProtocolsDocument33 pagesApplication Layer ProtocolsSarah AliNo ratings yet
- MTera SONET SDH Migration 0012 An RevB 0422Document9 pagesMTera SONET SDH Migration 0012 An RevB 0422manhhaibcvtNo ratings yet
- Public Inventory39Document16 pagesPublic Inventory39Giovanny LeonNo ratings yet
- Protecciones ABB - RET620 - PG - 757846 - ENe - Transformer Protection and ControlDocument76 pagesProtecciones ABB - RET620 - PG - 757846 - ENe - Transformer Protection and ControlJorge Antonio GonzálezNo ratings yet
- Document 1614134.1Document2 pagesDocument 1614134.1Joseph LeeNo ratings yet
- Assignment Cap275 Data CommunicationDocument4 pagesAssignment Cap275 Data CommunicationSantosh KumarNo ratings yet
- Avaya IX Desktop Phones: J100 SeriesDocument7 pagesAvaya IX Desktop Phones: J100 SeriesOmingo KingiNo ratings yet
- Ccna Lab Manual Version 5.0Document720 pagesCcna Lab Manual Version 5.0kev_aulakhNo ratings yet
- Cisco Application Centric Infrastructure Design GuideDocument217 pagesCisco Application Centric Infrastructure Design GuideA.A.No ratings yet
- Ex2300 Ethernet Switch DatasheetDocument12 pagesEx2300 Ethernet Switch Datasheetnaufal irfanNo ratings yet
- Mikrotik SecurityDocument54 pagesMikrotik Securitydpsguard-buy8922100% (2)
- Computer Networks Lab FileDocument35 pagesComputer Networks Lab FileRamendra ChaudharyNo ratings yet
- Digital EPABX Systems ADX 600 (N) : The Next GenerationDocument4 pagesDigital EPABX Systems ADX 600 (N) : The Next GenerationSumit BhallaNo ratings yet
- 00 MP IntroDocument29 pages00 MP IntroAlejandraNo ratings yet
- Computer Networks - Lecture NotesDocument42 pagesComputer Networks - Lecture NotesMehran Mustafa88% (17)
- Vlans 9800 DSLAMDocument8 pagesVlans 9800 DSLAMMuhammad DanyalNo ratings yet
- 11.5.5 Packet Tracer - Subnet An IPv4 NetworkDocument7 pages11.5.5 Packet Tracer - Subnet An IPv4 NetworkKrystelle Ungria TimtimNo ratings yet
- DIR-819 A1 Datasheet 01 (HQ)Document3 pagesDIR-819 A1 Datasheet 01 (HQ)Christián RojasNo ratings yet
- Lab 8.5.3: Troubleshooting Enterprise Networks 3: Topology DiagramDocument11 pagesLab 8.5.3: Troubleshooting Enterprise Networks 3: Topology DiagrambusmaniakNo ratings yet
- User'S Guide: Dell™ Powerconnect™ 27Xx SystemsDocument84 pagesUser'S Guide: Dell™ Powerconnect™ 27Xx SystemsChris SmithNo ratings yet
- Internet of Things (Iot 540) : L-T-P - (C) 4-0-0Document50 pagesInternet of Things (Iot 540) : L-T-P - (C) 4-0-0deva dattaNo ratings yet