Professional Documents
Culture Documents
4.4 Monitoring of Ethernetip Network Traffic
Uploaded by
Sam eagle goodOriginal Title
Copyright
Available Formats
Share this document
Did you find this document useful?
Is this content inappropriate?
Report this DocumentCopyright:
Available Formats
4.4 Monitoring of Ethernetip Network Traffic
Uploaded by
Sam eagle goodCopyright:
Available Formats
Module 5
4m. MONITORING OF ETHERNET/IP NETWORK TRAFFIC.
Wireshark (see Section 6) is a network packet analyser . It is used to:
• troubleshoot network problems,
• examine security problems,
• debug protocol implementations,
• learn network protocol internals.
Wireshark can capture traffic from many different network media types, including dial-up
connection, cable ethernet LAN and Wi-Fi LAN. It supports more than 900 types of
communication protocols. Wireshark is an open source software project, and is released
under the GNU General Public Licence (GPL).
The main goal of this exercise is to analyse Ethernet/IP network traffic on the Aero Lift
laboratory setup (see Chapter 5) by utilizing the Wireshark application described in
Chapter 6. A further aim is to assign the multicast addresses generated on the
Ethernet/IP network to the data packets sent by each network node.
The main window of Wireshark, filled with sample data gathered on the Ethernet/IP
network, is shown in Fig. 4m.1. Each line in the top panel of the Wireshark window
corresponds to a single packet seen on the Ethernet/IP network. The first column shows
the time of the packet (relative to the initiation of the capture), the next columns: source
and destination IP addresses, the Ethernet/IP protocol (ENIP) used and some additional
information about the packet. The user can drill down and obtain more information by
clicking on a row. This causes the bottom two window panels to fill with information.
Section 4m: Monitoring of the Ethernet/IP network traffic Page 1
Module 5
Fig. 4m.1. The main window of Wireshark
For real-time messaging, Ethernet/IP employs the UDP over IP, which allows a datagram
to be multicast to a group of destination addresses. This producer-consumer multicast
model is called “Implicit I/O Data connection” and provides I/O data sending at regular
time intervals. Hence, to properly analyse network traffic it is necessary to understand
the concept of multicast addressing which is used in the Ethernet/IP protocol. IP
multicast addresses (Layer 3 of the OSI) have been assigned to the old Class "D" address
space by the Internet Assigned Number Authority (IANA). Addresses in this space are
denoted with a binary "1110" prefix in the first four bits of the first octet, as shown in
Fig. 4m.2. This results in IP multicast addresses spanning a range from 224.0.0.0
through 239.255.255.255. The remaining 28 bits identify the multicast "Group" the
datagram is sent to.
Octet 1 Octet 2 Octet 3 Octet 4
1110xxxx xxxxxxxx xxxxxxxx xxxxxxxx
Fig. 4m.2. IP multicast address format
Section 4m: Monitoring of the Ethernet/IP network traffic Page 2
Module 5
IP multicast frames all use MAC layer addresses beginning with the 24-bit prefix of
0x0100.5Exx.xxxx. With only half of these MAC addresses available for use by IP
Multicast, 23 bits of MAC address space is available for mapping Layer 3 IP multicast
addresses onto Layer 2 MAC addresses. All Layer 3 IP multicast addresses have the first
four of the 32 bits set to 0x1110, leaving 28 bits of meaningful IP multicast address
information. These 28 bits must map onto only 23 bits of the available MAC address. This
mapping (for IP multicast equal to 239.192.1.65) is shown graphically in Fig. 4m.3.
Fig. 4m.3. Multicast MAC address mapping
As can be seen in Fig. 4m.3 all the 28 bits of a Layer 3 multicast address cannot be
mapped onto the available 23 bits of MAC address space. This means that each IP
multicast MAC address can represent 32 IP multicast addresses (32:1 address ambiguity
when a Layer 3 IP multicast address is mapped onto a Layer 2 MAC address). An
example of the ambiguity in the mapping process is shown in Fig. 4m.4.
Fig. 4m.4. Ambiguities in the address mapping process
Section 4m: Monitoring of the Ethernet/IP network traffic Page 3
Module 5
All the IP Multicast addresses are grouped and allocated by the IANA. Currently, these
addresses are divided into 10 blocks. The IANA has reserved the range of 239.0.0.0-
239.255.255.255 as “Administratively Scoped” addresses for use in private multicast
domains. This means that network administrators are free to use multicast addresses in
this range inside of their domain without fear of conflicting with others elsewhere on the
Internet. These addresses should be used by enterprise networks and should never be
forwarded outside the organisation.
For the users of Allen-Bradley systems this is the most important range of addresses. As
can be seen in Fig. 4m.1 the Ethernet/IP multicast addresses start from the same two
octets 239.192.xxx.xxx. In fact the all Ethernet/IP multicast addresses may be in the
range of 239.192.0.0 to 239.192.255.255.
All multicast addresses in our Ethernet/IP network are associated with standard, unicast
IP addresses of specific network nodes. In addition, one unicast IP address may generate
multiple multicast addresses. Typically a node (I/O module) multicasts its data every
specified RPI interval time. For example, an input module sends data to a controller at
the RPI that you assign to the module during the configuration process (see Chapter
3m).
The user can analyse the main parameters of the developed Ethernet/IP network by
highlighting the row he or she is interested in, in the top panel of Wireshark. This causes
the bottom two window panels to fill with information as shown in Fig. 4m.5. The most
important parameters are: multicast IP and MAC addresses assigned to existing network
nodes, unicast IP addresses of the nodes, the time interval (measured from the start of
data capturing), Internet Protocol and Ethernet/IP protocol parameters.
As an example, let's analyze the data frame numbered three in Fig. 4m.5. The source
unicast IP address 192.168.1.2 corresponds to the POINT_IO 1734-AENT (see Table 5.4
in Chapter 5). The assigned destination IP multicast address is equal to 239.192.1.65
and it is mapped onto the MAC multicast address 01:00:5E:40:01:41 (see Fig. 4m.3).
The Time To Live (TTL) parameter from the Internet Protocol tag shows, that the packet
is restricted to the same subnet and won't be forwarded by a router. The TTL controls the
live time of the datagram to avoid it being looped forever due to routing errors. Routers
decrement the TTL of every datagram as it traverses from one network to another, and
when its value reaches 0 the packet is dropped. The UDP over IP protocol is employed.
Source and destination addresses are typical for the Ethernet/IP protocol and in the
shown example adopt the same values equal to 2222.
Section 4m: Monitoring of the Ethernet/IP network traffic Page 4
Module 5
The Sequenced Address Item (0x8002), Connection ID (0x428e1a16), Connected Data
Item (0x00b1) and item data length are the same for this type of transaction. The Data
field length directly corresponds to the number of bytes transferred from the POINT_IO
1734-AENT.
Fig. 4m.5. Ethernet/IP network monitoring utilizing Wireshark
Below a two examples of exercises that can be carried out at the laboratory setup are
presented.
Exercise 1. Assignment of multicast addresses to a specific transaction data exchange.
The main goal of this exercise is to recognize of all multicast addresses assigned to the Ethernet/IP
network nodes and to analyse the tags of an Ethernet frames. All necessary data will be collected
using the Wireshark program.
1. First, you have to be aware that all components are connected in a proper way
(especially all Ethernet cables).
2. Run RSLinx Classic first and next RSLogix 5000.
Section 4m: Monitoring of the Ethernet/IP network traffic Page 5
Module 5
3. Open an exemplary project.
4. Check if the local and network configuration has been correctly carried out (see
Chapter 1m). The most important are the unicast IP addresses of each node and
data exchanging between all network nodes.
5. In the next step set the PLC to the Run mode and download program to the
program memory of the PLC. After downloading, if everything was setup correctly,
the “I/O OK” indicator is green.
6. Run the Wireshark program and set capture interface in accordance with Chapter
6. Click the Start button next to the name of the interface on which you wish to
capture traffic (or press the Capture -> Start option form the Main menu). The
capture process will start immediately.
7. After a several seconds a running capture session should be stopped by pressing
the Stop icon located on the toolbar or choosing the Capture -> Stop option
form the Main menu.
8. Now, you can view all captured Ethernet frames, assigning a multicast addresses
by reading source unicast IP addresses and analysing frame tags. It is important
that one unicast IP address can generate a few multicast addresses (each type of
data transaction occupies a different multicast address).
Exercise 2. Analysis of the Requested Packed Interval (RPI) time.
The main goal of this exercise is to experimentally analyse variation of the RPI, which decides about
refreshing of I/O data over the Ethernet/IP network. All necessary data will be collected using
the Wireshark program.
The exercise assumes that students carried out the configuration of the Ethernet/IP
network nodes (described in Section 1m) and can check and change the value of the RPI.
1. Repeat steps 1-3 from the Exercise 1.
2. Read RPI parameter set for each I/O module (open the Module Properties
window and select the Connection tag). For each RPI assign the unicast IP
address of the corresponding module.
3. Repeat steps 5-7 from the Exercise 1.
4. Locate and write down all type of transactions with the same source and
destination addresses, for example: 192.168.1.5 – 239.192.33.160,
192.168.1.182 – 239.192.23.193 etc.
Section 4m: Monitoring of the Ethernet/IP network traffic Page 6
Module 5
5. Order all of the frames according to the capturing time (the second column of the
main window of the Wireshark).
6. Read and write down times for the ten consecutive transactions of the same type.
7. Calculate the RPI by subtracting two consecutive capturing times wrote in step 6.
8. Compare the calculated values of the RPI with values set during the configuration
stage.
9. Repeat steps 6-8 for all transactions of the same type.
Bibliography
[1] CISCO Systems Inc., Guidelines for Enterprise IP Multicast Address Allocation,
http://www.cisco.com, 2004.
[2] RFC 3171, IANA Guidelines for IPv4 Multicast Address Assignments, Best Current
Practice, July 2001, http://tools.ietf.org/html/rfc3171, 2010. [2 dates???]
Author: M. Rosol
Section 4m: Monitoring of the Ethernet/IP network traffic Page 7
You might also like
- Network Design Assignment 1Document4 pagesNetwork Design Assignment 1Shulav PoudelNo ratings yet
- Lab Exercise - Ethernet: ObjectiveDocument11 pagesLab Exercise - Ethernet: ObjectiveTakaskiNo ratings yet
- 5.1.4.3 Lab - Using Wireshark To Examine Ethernet FramesDocument7 pages5.1.4.3 Lab - Using Wireshark To Examine Ethernet FramesBenjamin Gm100% (4)
- IPv4 Subnetting for Beginners: Your Complete Guide to Master IP Subnetting in 4 Simple Steps: Computer Networking, #1From EverandIPv4 Subnetting for Beginners: Your Complete Guide to Master IP Subnetting in 4 Simple Steps: Computer Networking, #1Rating: 5 out of 5 stars5/5 (3)
- Control Techniques Drives and Controls Handbook PDFDocument384 pagesControl Techniques Drives and Controls Handbook PDFbudak150% (2)
- LTE ENB CLI Tips&Tricks Mina Adel April-2014LTE ENB CLIDocument19 pagesLTE ENB CLI Tips&Tricks Mina Adel April-2014LTE ENB CLIYoucef BelhadiaNo ratings yet
- Mansoura University Faculty of Computers and Information Department TCP/IP CourseDocument20 pagesMansoura University Faculty of Computers and Information Department TCP/IP Coursesaher waleedNo ratings yet
- LabExercise1 EhternetDocument5 pagesLabExercise1 EhternetSyaiful Maulana AbbidinNo ratings yet
- S7 Ethernet-Local Area Network ConfigurationDocument47 pagesS7 Ethernet-Local Area Network ConfigurationByron Xavier Lima CedilloNo ratings yet
- Tcpi IpDocument97 pagesTcpi Ipcborn99100% (1)
- IP Router Software Reference GuideDocument189 pagesIP Router Software Reference Guideniko67No ratings yet
- CIR 209 (Lecture 4f) OSI - ModelDocument16 pagesCIR 209 (Lecture 4f) OSI - Modeldancanongori9No ratings yet
- CCNA Exam NotesDocument33 pagesCCNA Exam NotesMuhd IrfanNo ratings yet
- Course: Instructed byDocument21 pagesCourse: Instructed byanurag_0290No ratings yet
- The Internet NotesDocument91 pagesThe Internet NotesTejas Raghavendra Bhat MNo ratings yet
- Intro Computer Net Chapter 4Document12 pagesIntro Computer Net Chapter 4KhalifaNo ratings yet
- 17EC64 - Module4 - Network Layer Protocol and Unicast RoutingDocument52 pages17EC64 - Module4 - Network Layer Protocol and Unicast RoutingShashidhar krNo ratings yet
- Atmel - Embedded Web ServerDocument53 pagesAtmel - Embedded Web ServerNobodyXX66No ratings yet
- Unit 1Document54 pagesUnit 1AngayarkanniNo ratings yet
- Lecture 7Document5 pagesLecture 7owronrawan74No ratings yet
- 12.4 Multicasting: Multicast Group AddressesDocument3 pages12.4 Multicasting: Multicast Group AddressesRamandeep Singh LambaNo ratings yet
- CN Lab ManualDocument59 pagesCN Lab ManualNO 1No ratings yet
- IoT Module-2 NotesDocument11 pagesIoT Module-2 Notessachin mNo ratings yet
- Lab Ethernet HomeworkDocument8 pagesLab Ethernet HomeworklolzzzNo ratings yet
- CCNA Exam Notes: Key Concepts for Cisco Certified Network Associate 640-802 ExamDocument26 pagesCCNA Exam Notes: Key Concepts for Cisco Certified Network Associate 640-802 ExamDua ArsalanNo ratings yet
- Chapter Four: TCP/IP Network ManagementDocument57 pagesChapter Four: TCP/IP Network ManagementYomif NiguseNo ratings yet
- TCP vs UDP Sockets - Key DifferencesDocument26 pagesTCP vs UDP Sockets - Key DifferencesVaisa GanNo ratings yet
- Lecture 6 - Network Layer - Internet ProtocolDocument21 pagesLecture 6 - Network Layer - Internet ProtocolPrasad LoyalNo ratings yet
- IT Notes Unit 5Document14 pagesIT Notes Unit 5Deepankar Anil KumarNo ratings yet
- 4 Quarter Grade 9 TLE CSS (Computer System Servicing) Internet ProtocolsDocument8 pages4 Quarter Grade 9 TLE CSS (Computer System Servicing) Internet ProtocolsSERVEN GAMINGNo ratings yet
- Link Layer Overview of TCP/IP ProtocolsDocument6 pagesLink Layer Overview of TCP/IP Protocolsgani525No ratings yet
- Assignment Cs349 WiresharkDocument8 pagesAssignment Cs349 WiresharkRitvik SarafNo ratings yet
- Introd To Internet ProtocolDocument6 pagesIntrod To Internet ProtocolCamilo A. InfanteNo ratings yet
- How TCP-IP WorksDocument29 pagesHow TCP-IP WorksJames GeorgeNo ratings yet
- Computer NetworksDocument21 pagesComputer NetworksAran UtkarshNo ratings yet
- TCP/IP Protocol Suite & IP Addressing ExplainedDocument7 pagesTCP/IP Protocol Suite & IP Addressing ExplainedGrecu GianiNo ratings yet
- Ok LangDocument8 pagesOk LangCrislan D. VillalonNo ratings yet
- Network Layer/Internet Protocols: You Will Learn About The Following in This ChapterDocument28 pagesNetwork Layer/Internet Protocols: You Will Learn About The Following in This ChapterMarius PlesaNo ratings yet
- IPv4 and IPv6 Coexistence Seminar ReportDocument19 pagesIPv4 and IPv6 Coexistence Seminar ReportAnirban KunduNo ratings yet
- Using IP Multicasting With The TMS320C6000 Network Developer's Kit (NDK)Document12 pagesUsing IP Multicasting With The TMS320C6000 Network Developer's Kit (NDK)Rahim Ali QamarNo ratings yet
- Study of Network and Transport Layer Protocols Using WiresharkDocument10 pagesStudy of Network and Transport Layer Protocols Using WiresharkSALIM TADVINo ratings yet
- 5.1.4.3 Lab - Using Wireshark To Examine EthernetDocument7 pages5.1.4.3 Lab - Using Wireshark To Examine Ethernetjinzo10101No ratings yet
- History of Internet Protocol:: What Is IP?Document25 pagesHistory of Internet Protocol:: What Is IP?Amrit Razz ShresthaNo ratings yet
- Ccna1-Final 2 v4.0Document18 pagesCcna1-Final 2 v4.0rajnox100% (6)
- CCNA LabManual NewDocument142 pagesCCNA LabManual Newyashveer100% (1)
- I E N /IP T: Ntroduction To Ther ET EchnologyDocument9 pagesI E N /IP T: Ntroduction To Ther ET Echnologyshadi22No ratings yet
- Web NotesDocument37 pagesWeb NotesRayroy KaranjaNo ratings yet
- SummaryDocument14 pagesSummaryAbdullah MohammadNo ratings yet
- Assignment On NetworksDocument7 pagesAssignment On NetworksLimitless StatusNo ratings yet
- Fundamentals of Telecommunication ExcercisesDocument16 pagesFundamentals of Telecommunication ExcercisesPhan AnNo ratings yet
- Cisco QuizDocument2 pagesCisco QuizJatinder SinghNo ratings yet
- TCP/IP Fundamentals: Chapter ObjectivesDocument27 pagesTCP/IP Fundamentals: Chapter Objectiveschetana sidigeNo ratings yet
- Abhishek Pal - Project Report 2012Document34 pagesAbhishek Pal - Project Report 2012Ankit GuptaNo ratings yet
- TCP/IP Protocols Homework ExplainedDocument10 pagesTCP/IP Protocols Homework ExplainedJaspreet KaurNo ratings yet
- Ircse09 Submission 24Document8 pagesIrcse09 Submission 24mrwanzNo ratings yet
- Internet Protocols g10 Chs EdzDocument49 pagesInternet Protocols g10 Chs EdzJoan SarahanNo ratings yet
- Bosch - Networking Essentials and Basic ConceptsDocument10 pagesBosch - Networking Essentials and Basic ConceptsFábio Dos ReisNo ratings yet
- CSP 11 Block 03Document71 pagesCSP 11 Block 03BiswamitNo ratings yet
- CCNA Interview Questions You'll Most Likely Be Asked: Job Interview Questions SeriesFrom EverandCCNA Interview Questions You'll Most Likely Be Asked: Job Interview Questions SeriesNo ratings yet
- Computer Networking: An introductory guide for complete beginners: Computer Networking, #1From EverandComputer Networking: An introductory guide for complete beginners: Computer Networking, #1Rating: 4.5 out of 5 stars4.5/5 (2)
- Introduction to Internet & Web Technology: Internet & Web TechnologyFrom EverandIntroduction to Internet & Web Technology: Internet & Web TechnologyNo ratings yet
- A03 StartupDocument48 pagesA03 StartupSam eagle goodNo ratings yet
- Deck BleDocument1 pageDeck BlenemoneoNo ratings yet
- Programação em Realtime SystemDocument26 pagesProgramação em Realtime SystemSam eagle goodNo ratings yet
- Siemens PLC Programming Example1 PDFDocument12 pagesSiemens PLC Programming Example1 PDFHani ErrachidNo ratings yet
- Deckble KO-7KFMSDocument1 pageDeckble KO-7KFMSSam eagle goodNo ratings yet
- Brochure Simatic-Wincc-Flexible enDocument28 pagesBrochure Simatic-Wincc-Flexible enSam eagle goodNo ratings yet
- Scan Flow ChartDocument2 pagesScan Flow ChartSam eagle goodNo ratings yet
- Dinamic BrakeDocument18 pagesDinamic BrakeSam eagle goodNo ratings yet
- Simatic Configuration Communication - 2Document18 pagesSimatic Configuration Communication - 2Sam eagle goodNo ratings yet
- Driver Gantry Rigid Control FunctionDocument22 pagesDriver Gantry Rigid Control FunctionSam eagle goodNo ratings yet
- SIMATIC NET Commissioning PC Stations - ManualDocument221 pagesSIMATIC NET Commissioning PC Stations - ManualSam eagle goodNo ratings yet
- S7-TCPIP Ethernet InterfaceDocument124 pagesS7-TCPIP Ethernet InterfaceSam eagle goodNo ratings yet
- FM 351 Positioning Function Installation and ParameterDocument170 pagesFM 351 Positioning Function Installation and ParameterSam eagle goodNo ratings yet
- Sink SourceDocument4 pagesSink SourceSam eagle goodNo ratings yet
- Brake DynamicDocument3 pagesBrake DynamicSam eagle goodNo ratings yet
- TF5200 Gantry Operation enDocument33 pagesTF5200 Gantry Operation enSam eagle goodNo ratings yet
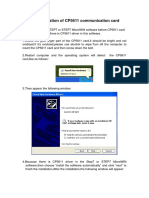
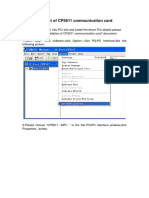
- The Installation of CP5611 Communication CardDocument4 pagesThe Installation of CP5611 Communication CardSam eagle goodNo ratings yet
- FM 351 Positioning With S7-300Document204 pagesFM 351 Positioning With S7-300Sam eagle goodNo ratings yet
- The Test of CP5611 Communication CardDocument8 pagesThe Test of CP5611 Communication CardSam eagle goodNo ratings yet
- Simatic FM 351: First Steps in CommissioningDocument6 pagesSimatic FM 351: First Steps in CommissioningSam eagle goodNo ratings yet
- SIMATIC NET Siemens PROFIBUS Controller 3 User DescriptionDocument106 pagesSIMATIC NET Siemens PROFIBUS Controller 3 User DescriptionSam eagle goodNo ratings yet
- FM 351 - Getting - StartedDocument20 pagesFM 351 - Getting - StartedSam eagle goodNo ratings yet
- PROFIBUS Servo Positioning Controller ARS 2000Document84 pagesPROFIBUS Servo Positioning Controller ARS 2000Sam eagle goodNo ratings yet
- CP5512E InstallationDocument12 pagesCP5512E InstallationSam eagle goodNo ratings yet
- CP5611 Card IntroductionDocument2 pagesCP5611 Card IntroductionSam eagle goodNo ratings yet
- PROFIBUS FMS-OLE-DDE S5 CP5431 and PC FMS-CP5412Document24 pagesPROFIBUS FMS-OLE-DDE S5 CP5431 and PC FMS-CP5412Sam eagle goodNo ratings yet
- SIMATIC NET Siemens PROFIBUS Controller 4 User DescriptionDocument96 pagesSIMATIC NET Siemens PROFIBUS Controller 4 User DescriptionSam eagle goodNo ratings yet
- SIMATIC NET Siemens PROFIBUS Controlle 3 Hardware DescriptionDocument68 pagesSIMATIC NET Siemens PROFIBUS Controlle 3 Hardware DescriptionSam eagle goodNo ratings yet
- C79000-G8976-C157-0 SIMATIC NET PROFIBUS Controller SPC 4-2Document126 pagesC79000-G8976-C157-0 SIMATIC NET PROFIBUS Controller SPC 4-2Sam eagle goodNo ratings yet
- Mikrotik Nstreme Protocol: Document Revision 1.6 (Tue Jun 1 19:59:00 GMT 2004)Document5 pagesMikrotik Nstreme Protocol: Document Revision 1.6 (Tue Jun 1 19:59:00 GMT 2004)Driton Emerllahu100% (1)
- Wireshark Analysis of Trace File-UtarDocument22 pagesWireshark Analysis of Trace File-UtarLam Chen RiangNo ratings yet
- How Many Packets Per Second Per Port Are Needed To Achieve Wire-Speed?Document4 pagesHow Many Packets Per Second Per Port Are Needed To Achieve Wire-Speed?y_m_algbaliNo ratings yet
- En300468 V1 8 1Document103 pagesEn300468 V1 8 1phamducnhonNo ratings yet
- Whats NewDocument32 pagesWhats NewSandro RodrigoNo ratings yet
- WestermoDirect Autumn2002Document6 pagesWestermoDirect Autumn2002cvidal_47No ratings yet
- Open Architecture Applied To Next-Generation WeaponsDocument11 pagesOpen Architecture Applied To Next-Generation Weaponsbring it onNo ratings yet
- NewtworkingDocument16 pagesNewtworkingAnum BakhtiarNo ratings yet
- CCNA Dump 2Document38 pagesCCNA Dump 2api-3754892100% (3)
- AX-18A/F Part Photo and SpecsDocument27 pagesAX-18A/F Part Photo and SpecsLUINo ratings yet
- Information SecurityDocument59 pagesInformation SecurityAshwin Charles ANo ratings yet
- Next Generation FirewallDocument6 pagesNext Generation FirewallFelippe CoelhoNo ratings yet
- CS610 Solved MCQSDocument13 pagesCS610 Solved MCQScool_eyezNo ratings yet
- ICCA Volume 6Document245 pagesICCA Volume 6kk3934No ratings yet
- TCP VS UdpDocument11 pagesTCP VS UdpMk BdNo ratings yet
- Ethernet Frame Types PDFDocument2 pagesEthernet Frame Types PDFMarcoNo ratings yet
- CC Notes Lecture 03Document39 pagesCC Notes Lecture 03Ghulam ShabbirNo ratings yet
- WAP PresentationDocument43 pagesWAP PresentationAkshay PhadkeNo ratings yet
- Ipt NotesDocument4 pagesIpt NotesDavid PhanNo ratings yet
- ZTE UMTS Services and Radio Access Bearers Feature Guide V1 10 PDFDocument66 pagesZTE UMTS Services and Radio Access Bearers Feature Guide V1 10 PDFMayra Garrett100% (1)
- ColeDocument236 pagesColeJason PittmanNo ratings yet
- TCP and UDP protocols explainedDocument4 pagesTCP and UDP protocols explainedGowri Shankar S JNo ratings yet
- Model Answer - Task 2Document11 pagesModel Answer - Task 2Shahid ImranNo ratings yet
- Solaris 10 Overview: ObjectivesDocument61 pagesSolaris 10 Overview: ObjectivesRattnakishore NandamuriNo ratings yet
- GT300 ProtocolDocument51 pagesGT300 Protocolpranay kambleNo ratings yet
- ECSS E 50 04A (14november2007) PDFDocument139 pagesECSS E 50 04A (14november2007) PDFAndreeNo ratings yet
- Basics of HartDocument59 pagesBasics of Hartjmathew_984887No ratings yet
- Performance Analysis of RLC/MAC and LLC Layers in A GPRS Protocol StackDocument16 pagesPerformance Analysis of RLC/MAC and LLC Layers in A GPRS Protocol Stacksrinivasa shettigarNo ratings yet