Professional Documents
Culture Documents
Information Technology
Uploaded by
PartTimeMusicianCopyright
Available Formats
Share this document
Did you find this document useful?
Is this content inappropriate?
Report this DocumentCopyright:
Available Formats
Information Technology
Uploaded by
PartTimeMusicianCopyright:
Available Formats
Information Technology MARVIN MINSKY
EASY 7. ______________is characterized by abusers repeatedly
1. As of July 2015, what number Windows became the most sending an identical email message to a particular address
recent version of Windows for personal computers? EMAIL BOMBING
10
2. What country has the two letter domain name 'cn'? 8. What gave rise to the 'second generation' of computers by
CHINA replacing vacuum tubes in computer designs?
TRANSISTORS
3. In computing there are 8 bits to a byte, what are 4 bits
called? 9. Who is known as the Father of Internet?
NIBBLE VINT CERF
4. What is Spam related to e-mails? 10. A______________ contains specific rules and words that
UNSOLICITED/UNWANTED EMAIL express the logical steps of an algorithm
SYNTAX
5. What is the capacity of a standard PC floppy?
a. 1. 2MB
b. 1.44K DIFFICULT
c. 1.44MB 1. What name was given to the series of computers used by
d. 120MB British codebreakers in World War Two to break the Lorenz
cipher?
6. Founder of the social networking website 'Facebook'. Give COLOSSUS
his full name
MARK ELLIOT ZUCKERBERG 2. What frequency range is the High Frequency band?
7. "Stored Program Concept" is postulated by: a. 100 kHz
JOHN VON NEUMANN b. 1 GHz
c. 30 to 300 MHz
8. What does the 'F' stand for in the acronym FORTRAN? d. 3 to 30 MHz
FORMULA
3. What is the binary equivalent of 29?
9. A device that connects to a computer network without the 10110
use of cables is said to be:
WIRELESS 4. What type of attack do hackers use to gain information from
10. " Don't be evil" is The Tagline Of? you without the use of specialized computer programs?
GOOGLE SOCIAL ENGINEERING
5. McAfee, the internet security company, became a subsidiary
AVERAGE of which of these in 2011?
1. When is Computer Literacy Day? a. Intel
DECEMBER 2 b. Microsoft
c. Dell
2. Who Is The Author Of "Weaving The Web"? d. IBM
TIM BERNERS-LEE
6. In the early 1990s, users were advised not to run their PCs
3. Which general-purpose high-level programming language on March 6, the activation date for a dormant computer virus.
was created by Guido van Rossum in the Netherlands? This virus came to be named after which famous Renaissance
PYTHON artist born on March 6?
MICHELANGELO
4. '.INI' extension refers usually to what kind of file?
SYSTEM FILE 7. In May 2000 this worm, which shares a name with a Disney
film, spread through e-mail. What was one of its names?
5. Why is the domain Symbolics.com famous? I LOVE YOU
FIRST DOMAIN NAME (March 5, 1985)
8. The Stuxnet worm, discovered in June 2010, primarily
6. Who is considered to be The Father of Artificial Intelligence? attacked computer systems in which country?
IRAN BROADWELL – New architecture of the new Intel processor
PASCAL – New Architecture of the New Nvidia GPU or 10’s
9. In February 2001, which tennis star was the supposed series
subject of an e-mail attachment which actually carried a virus? POLARIS – New Architecture of the new AMD Radeo RX480
FREDRIK IDESTAM, LEO MECHELIN – Founders of Nokia
a. Anna Kournikova POKEMON GO – developer: Niantic, Inc.; publisher: The
b. Maria Sharapova Pokemon Company; initial release date: July 6, 2016
c. Serena Williams (Australia, New Zealand, US); Genre: Augmented Reality
d. Jennifer Capriati LASER - Light Amplification by Stimulated Emission of
Radiation
10. In July 2001 the Code Red worm caused affected web sites MICROSOFT AUGMENTED REALITY – AR
to display which phrase? VR: HTC Vile VR, Oculus Rift, Google Cardboard (VR)
QUALCOMM – Mobile CPU
a. Hacked by Chinese! QUALCOMM SNAPDRAGON – GPU
b. Infection in progress! GPS – Global Positioning System
c. You've been schooled! ISP – Internet Service Provider
d. Gremlins got you! TELSTRA – Australia's largest telecommunications and media
company
CLINCHER GOOGLE GLASS – developed by Google X; Augmented Reality
1. Yes or No. In Microsoft Excel '97, if I hit CTRL+B in a cell LTE – Long-Term Evolution
before typing in it, the resultant type would be bold. PHYSX - a proprietary realtime physics engine middleware
YES SDK. PhysX was authored at NovodeX, an ETH Zurich spin-off.
In 2004 NovodeX was acquired by Ageia, and in February 2008
2. What does SAN stand for? Ageia was acquired by Nvidia.
STORAGE AREA NETWORK ALAN TURING – AI
BJARNE STROUSTRUP – C++
3. In 1984, Apple Computer kicked off its campaign for the CHARLES BABBAGE – Difference Engine and Analytical
Macintosh computer in a $1.5 million Super Bowl ad. What was Engine, two punched-card controlled general purpose
the name of the $10,000 flop the Mac replaced? calculators
LISA GORDON MOORE – Intel
GEORGE BOOLE, ROBERT NOYCE – modern symbolic logic
4. What type of memory is used to temporarily store MARC ANDREESSEN – Netscape
information that the computer is currently working with? SHAWN FANNING – Napster
RAM CHARLES GOLDFARB – SGML
LINUS TORVALDS – Linux OS
5. True or False. In 1997, a computer named Deep Purple beat KONRAD ZUSE – first binary digit Z1
chess wizard Garry Kasparov. LARRY PAGE, SERGEY BRIN - GOOGLE
TRUE MARK ELLIOT ZUCKERBERG – FACEBOOK
STEVE JOBS, RONALD WAYNE, STEVE WOZNIAK – APPLE
6. This software programs' main function is typically to enable BILL GATES, PAUL ALLEN - MICROSOFT
an attacker to have a complete control of their victim's PC ADA LOVELACE – COMPUTER PROG MOTHER
TROJAN JERRY SANDERS - ADVANCED MICRO DEVICES (AMD)
LARRY ELLISON - ORACLE
7. What are the first six (6) letters that appear on the - AMERICA ONLINE
traditional computer keyboard? TED NELSON – FATHER OF HYPEETEXT
QWERTY RASMUS LERDORF – PHP
PHIL ZIMMERMANN – PGP/Pretty Good Privacy: data
8. What is the general term given for keys such as ALT, SHIFT, encryption and decryption computer program that provides
or CTRL? cryptographic privacy and authentication for data
MODIFIER KEYS communication
JAMES GOSLING – JAVA
9. What is the term used for a method of capturing and FRED COHEN – coined ‘virus’
recording a person's keystrokes when typing on a keyboard? HISTORY
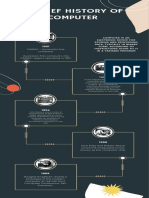
KEY LOGGING 1st Gen (1937-1946)
ABC (Atanasoff Berry Computer) – 1937, 1st electronic digital
10. What network operating system is Solaris a version of? computer by Dr. John V. Atanasoff and Clifford Berry
UNIX Colossus – electronic computer built for the military
ENIAC (Electronic Numerical Integrator and Computer) –
1946, first general-purpose digital computer
2nd Gen (1947-1962)
UNIVAC 1 (Universal Automatic Computer) – first computer
for commercial use, 1951
IBM (International Business Machine) 650 and 700 – 1953
3rd Gen (1963-Present)
Integrated circuit – invented
MS-DOS (Microsoft Disk Operating System) – 1980
PERSONAL COMPUTER (PC) – 1981, IBM
ABACUS – mathematical equations
PASCALINE – 1642, Blaise Pascal
JACQUARD’S LOOM – Joseph Marie Jacquard
DIFFERENCE ENGINE AND ANALYTIC ENGINE – Charles
Babbage 1822
ADA BYRON LOVELACE – mother of computer programming
COBOL – Rear Admiral Grace Hopper
The first hard disk drive was created in 1979 by Seagate. Its
capacity was a whopping (not) 5 MB.
“The Dirty Dozen” – codename of the 12 engineers at IBM that
developed the IBM PC
Intel 4004 – first microprocessor
Shakuntala Devi - Human computer
WIKI – What I Know Is
RICHARD MATHEW STALMAN – Open source program
DOUGLAS ENGELBART – computer mouse
CHRISTOPHER SHOLES - QWERTY type keyboard
JAMES RUSSELL - COMPACT DISC (CD)
VINT CERF – Father of Internet
TIM BERNERS-LEE - Father of WWW
PARAM – Super computer, India
ASCII - American Standard Code for Information Interchange
ALAN CURTIS KAY – GUI
INTERNET BACKBONE - main routes that data travels over the
internet
You might also like
- Raspberry Pi for Arduino Users: Building IoT and Network Applications and DevicesFrom EverandRaspberry Pi for Arduino Users: Building IoT and Network Applications and DevicesNo ratings yet
- Information Technology - Questions EasyDocument4 pagesInformation Technology - Questions EasyPartTimeMusicianNo ratings yet
- Quiz BeeDocument18 pagesQuiz BeeJazmyn AlegriaNo ratings yet
- Group 1 (Quiz)Document7 pagesGroup 1 (Quiz)Gabrielle Anne MagsanocNo ratings yet
- TCS It Quiz 2018Document63 pagesTCS It Quiz 2018cv bnmmksNo ratings yet
- Ict 7 Q1 Module 1Document12 pagesIct 7 Q1 Module 1LhanzTVNo ratings yet
- Vanik Iiu Lichevskaia SP Levitskaia Ms Molchan Ok English FoDocument150 pagesVanik Iiu Lichevskaia SP Levitskaia Ms Molchan Ok English FoSvitlana KovalNo ratings yet
- Namma - Kalvi - 11th - Computer - Science - Volume - 1 - Guide - em - 215024 (Dragged)Document1 pageNamma - Kalvi - 11th - Computer - Science - Volume - 1 - Guide - em - 215024 (Dragged)kingofpaladinsNo ratings yet
- 4th Generation of ComputerDocument20 pages4th Generation of ComputerPria VillalobosNo ratings yet
- Question Bank For Class XIIDocument30 pagesQuestion Bank For Class XIIRïshü SøñdhïNo ratings yet
- Information Age: Figure 2 Modern Days Figure 1 Before Modern DaysDocument6 pagesInformation Age: Figure 2 Modern Days Figure 1 Before Modern DaysDeony CaceresNo ratings yet
- Wordstar Language: Dev - Babloo Offline Send EmailDocument1 pageWordstar Language: Dev - Babloo Offline Send EmailRahul Girish KumarNo ratings yet
- Cambridge Year 8 Topical Test 1Document4 pagesCambridge Year 8 Topical Test 1Ice SyahNo ratings yet
- Ultimate ReviewerDocument12 pagesUltimate Reviewerjuraven12No ratings yet
- Computer Revision Booklet 2019-20Document8 pagesComputer Revision Booklet 2019-20Adhara MukherjeeNo ratings yet
- ACCS 211 (Assignment) Radeah M. Mokamad Bsa 2 5:30 - 7:00 PM M/WDocument4 pagesACCS 211 (Assignment) Radeah M. Mokamad Bsa 2 5:30 - 7:00 PM M/WRhanda BernardoNo ratings yet
- Pendon - Living in It Era - MidtermDocument3 pagesPendon - Living in It Era - MidtermLordelene PendonNo ratings yet
- Modul Bahasa Inggris 2 - Unit 3Document9 pagesModul Bahasa Inggris 2 - Unit 3anon_7405835630% (1)
- l1 Evolution-Of-computers Updated Edited 08062020Document15 pagesl1 Evolution-Of-computers Updated Edited 08062020Ella ViscayaNo ratings yet
- Technology QuizDocument1 pageTechnology Quizlizbet08No ratings yet
- ICT Related TRIVIASDocument10 pagesICT Related TRIVIASWowie J CruzatNo ratings yet
- Techně Logos: Law Formulated by Isaac Asimov Back in 1940'sDocument8 pagesTechně Logos: Law Formulated by Isaac Asimov Back in 1940'sSofia GadoyNo ratings yet
- Sai Wan Hong Kong Victoria HarbourDocument17 pagesSai Wan Hong Kong Victoria HarbourAiasha AgarwalNo ratings yet
- 11 CS Guide 2022 2023Document93 pages11 CS Guide 2022 2023venkateshss4123No ratings yet
- 1ST Quarter Exam in CSS IDocument2 pages1ST Quarter Exam in CSS IFrancis100% (1)
- TCS IT Wiz Book 2011Document31 pagesTCS IT Wiz Book 2011Vignesh VermaNo ratings yet
- Science, Technology & Society in The 20 Century: Prepared By: Sheena M. RositaDocument22 pagesScience, Technology & Society in The 20 Century: Prepared By: Sheena M. RositaEmgelle JalbuenaNo ratings yet
- DLP Network Interface CardDocument5 pagesDLP Network Interface CardAlfred Terre LlasosNo ratings yet
- A Level Computer Science Bridging Unit 2020Document11 pagesA Level Computer Science Bridging Unit 2020nunya78No ratings yet
- Lab 1Document2 pagesLab 1Diana Hull0% (2)
- Fallarcuna, Elhieza 02 Quiz 1 MITDocument2 pagesFallarcuna, Elhieza 02 Quiz 1 MITELHIEZA FALLARCUNANo ratings yet
- Computer Science Trivia QuestionsDocument5 pagesComputer Science Trivia Questionssolbert55No ratings yet
- Fourth Generation ComputersDocument3 pagesFourth Generation ComputersMohammad Umer Asgher100% (2)
- Quarter 4 - Lesson 1 Computer NetworkDocument83 pagesQuarter 4 - Lesson 1 Computer NetworkMELAIDA CASTANAR GARIBAYNo ratings yet
- Textual Learning Material - Module 1Document44 pagesTextual Learning Material - Module 1SaurabhChaudharyNo ratings yet
- PDF Uttam Second TermDocument7 pagesPDF Uttam Second TermUttam Lal RajbanshiNo ratings yet
- Reviewer Answers: The First Link On The ARPANETDocument1 pageReviewer Answers: The First Link On The ARPANETjhari aliparoNo ratings yet
- Quiz 1: Empowerment TechnologiesDocument1 pageQuiz 1: Empowerment TechnologiesJennalyn JavierNo ratings yet
- Cerebra Integrated Technologies LimitedDocument78 pagesCerebra Integrated Technologies LimitedPrashanth PBNo ratings yet
- Story Internet TN PDFDocument5 pagesStory Internet TN PDFSaleemNo ratings yet
- Technology Listening and VocabularyDocument2 pagesTechnology Listening and VocabularySofíaNo ratings yet
- Tech Quiz 8 MarchDocument2 pagesTech Quiz 8 MarchtansNo ratings yet
- Asistin Empotech ReviewerDocument5 pagesAsistin Empotech ReviewerJulie Ann Cabonce AsistinNo ratings yet
- Lesson PlanDocument23 pagesLesson PlanAbanes, Cherry ShaneNo ratings yet
- Emp Tech Pointers To Review 1Document4 pagesEmp Tech Pointers To Review 1Jm seNo ratings yet
- What I Have Learnd in Lesson 1-3 Not FinalDocument6 pagesWhat I Have Learnd in Lesson 1-3 Not FinalAshley PatricioNo ratings yet
- 1st COMP 9 MODULE 1-Week 1Document9 pages1st COMP 9 MODULE 1-Week 1Jasmine BalbinNo ratings yet
- IT ContinueDocument2 pagesIT ContinueLa JewelNo ratings yet
- Accenture Outlook It 2015Document5 pagesAccenture Outlook It 2015myscribd1209No ratings yet
- Aesthetic Charcoal Managing Brand Tips InfographicDocument4 pagesAesthetic Charcoal Managing Brand Tips InfographicJEZY LEI MANALANSANNo ratings yet
- Module - InternetDocument18 pagesModule - InternetNinerz LacsamanaNo ratings yet
- Activity in It Era (Prelim 2nd Sem)Document10 pagesActivity in It Era (Prelim 2nd Sem)BinggayNo ratings yet
- Generation of Computers: Camarines Sur National High School Icf 7 Learning Activity Sheet Quarter 1, Week 4Document9 pagesGeneration of Computers: Camarines Sur National High School Icf 7 Learning Activity Sheet Quarter 1, Week 4Houstine ErisareNo ratings yet
- Wa0001Document172 pagesWa0001Aniket LavandNo ratings yet
- Íngua Inglesa: Ead - Ita/ImeDocument3 pagesÍngua Inglesa: Ead - Ita/ImeLeonardo Silva KuligoskiNo ratings yet
- 3Document69 pages3KaleeswariNo ratings yet
- Unit 6Document3 pagesUnit 6Muhamad Farrel RizqullahNo ratings yet
- Activity 1: Caveman VS Computer: 1954 - Used Vacuum Tubes 2 GenerationDocument2 pagesActivity 1: Caveman VS Computer: 1954 - Used Vacuum Tubes 2 GenerationJaymark UrbanoNo ratings yet
- Week 4Document21 pagesWeek 4eljay9037No ratings yet
- The Melody Shop March: Tempo de MarchaDocument3 pagesThe Melody Shop March: Tempo de MarchaPartTimeMusicianNo ratings yet
- Rolling Thunder TubaDocument2 pagesRolling Thunder TubaPartTimeMusicianNo ratings yet
- Joyces71st Tousignant PDFDocument31 pagesJoyces71st Tousignant PDFPartTimeMusicianNo ratings yet
- 4 HorsemenDocument13 pages4 HorsemenPartTimeMusicianNo ratings yet
- 4 HorsemenDocument13 pages4 HorsemenPartTimeMusicianNo ratings yet
- Tec066 6700 PDFDocument2 pagesTec066 6700 PDFExclusivo VIPNo ratings yet
- Flight Data Recorder Rule ChangeDocument7 pagesFlight Data Recorder Rule ChangeIgnacio ZupaNo ratings yet
- 3) Uses and Gratification: 1) The Hypodermic Needle ModelDocument5 pages3) Uses and Gratification: 1) The Hypodermic Needle ModelMarikaMcCambridgeNo ratings yet
- 5045.CHUYÊN ĐỀDocument8 pages5045.CHUYÊN ĐỀThanh HuyềnNo ratings yet
- Population Second TermDocument2 pagesPopulation Second Termlubna imranNo ratings yet
- The Intel 8086 / 8088/ 80186 / 80286 / 80386 / 80486 Jump InstructionsDocument3 pagesThe Intel 8086 / 8088/ 80186 / 80286 / 80386 / 80486 Jump InstructionsalexiouconNo ratings yet
- SCIENCE 11 WEEK 6c - Endogenic ProcessDocument57 pagesSCIENCE 11 WEEK 6c - Endogenic ProcessChristine CayosaNo ratings yet
- 9701 Nos Ps 23Document5 pages9701 Nos Ps 23Hubbak KhanNo ratings yet
- Acceptable Use Policy 08 19 13 Tia HadleyDocument2 pagesAcceptable Use Policy 08 19 13 Tia Hadleyapi-238178689No ratings yet
- An Analysis of Students' Error in Using Possesive Adjective in Their Online Writing TasksDocument19 pagesAn Analysis of Students' Error in Using Possesive Adjective in Their Online Writing TasksKartika Dwi NurandaniNo ratings yet
- GrenTech Express Communication System Introduction 1.0Document30 pagesGrenTech Express Communication System Introduction 1.0Son NguyenNo ratings yet
- Auditing Principles and Practices-IDocument8 pagesAuditing Principles and Practices-IMoti BekeleNo ratings yet
- Acute Suppurative Otitis MediaDocument41 pagesAcute Suppurative Otitis Mediarani suwadjiNo ratings yet
- The DIRKS Methodology: A User GuideDocument285 pagesThe DIRKS Methodology: A User GuideJesus Frontera100% (2)
- Physiol Toric Calculator: With Abulafia-Koch Regression FormulaDocument1 pagePhysiol Toric Calculator: With Abulafia-Koch Regression FormuladeliNo ratings yet
- Emerging Technology SyllabusDocument6 pagesEmerging Technology Syllabussw dr100% (4)
- Cln4u Task Prisons RubricsDocument2 pagesCln4u Task Prisons RubricsJordiBdMNo ratings yet
- Worked Solution Paper5 A LevelDocument8 pagesWorked Solution Paper5 A LevelBhoosan AncharazNo ratings yet
- Makalah Bahasa Inggris TranslateDocument14 pagesMakalah Bahasa Inggris TranslatevikaseptideyaniNo ratings yet
- Chapter 5 - Principle of Marketing UpdateDocument58 pagesChapter 5 - Principle of Marketing UpdateKhaing HtooNo ratings yet
- JIMMA Electrical&ComputerEngDocument219 pagesJIMMA Electrical&ComputerEngTewodros71% (7)
- Power System Protection (Vol 3 - Application) PDFDocument479 pagesPower System Protection (Vol 3 - Application) PDFAdetunji TaiwoNo ratings yet
- Oil List: Audi Front Axle DriveDocument35 pagesOil List: Audi Front Axle DriveAska QianNo ratings yet
- Worksheet in Bio 102: Microbiology and Parasitology (WEEK 17)Document3 pagesWorksheet in Bio 102: Microbiology and Parasitology (WEEK 17)DELOS SANTOS JESSIECAHNo ratings yet
- Written Report SampleDocument16 pagesWritten Report Sampleallanposo3No ratings yet
- OB and Attendance PolicyDocument2 pagesOB and Attendance PolicyAshna MeiNo ratings yet
- Traffic Survey, Analysis, and ForecastDocument91 pagesTraffic Survey, Analysis, and Forecastsanthosh rajNo ratings yet
- Energy Production From Speed BreakerDocument44 pagesEnergy Production From Speed BreakerMuhammad Bilal67% (3)
- Pen Pal Lesson Plan 3Document3 pagesPen Pal Lesson Plan 3api-664582820No ratings yet
- Ticket: Fare DetailDocument1 pageTicket: Fare DetailSajal NahaNo ratings yet